- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: SFR Module NTP Traffic Blocked
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
SFR Module NTP Traffic Blocked
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-18-2019 01:58 PM - edited 02-21-2020 09:42 AM
Hello,
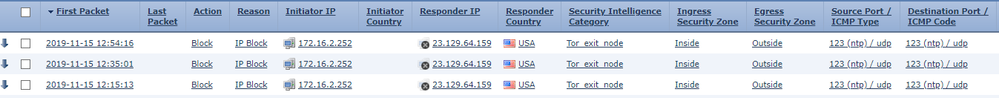
Looking at my blocked traffic I see some TOR exit node IP (23.129.64.159). Strange thing is, the initiator IP is my SFR module. It's NTP traffic. What's going on here? Why is my SFR module looking at a TOR node for time? I looked at my FMC and the IP isn't listed in the time configuration.
- Labels:
-
Other Network Security Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2019 05:13 AM
The time server could have been set on the module during the initial setup. You can rerun that using the script:
/etc/sysconfig/configure-network
...from cli on your module. (you may need to "sudo su -" first)
What (if anything) do you have set on FMC under System > Local > System Policy?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2019 09:14 AM
Hi Marvin,
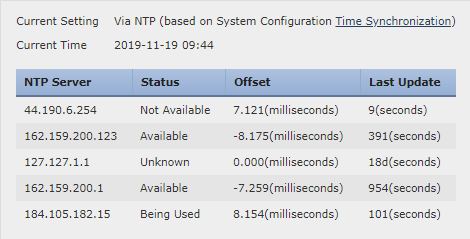
I don't have any option in my FMC for System > Local > System Policy but I do have System > Configuration > Time which displays this:
The blocked IP isn't listed there.
I ran the
/etc/sysconfig/configure-network
But there wasn't an option for a NTP server there before it completed.
After I ran the configure-network this error popped up in the FMC but it cleared itself up after a few min:
I ran the initial setup a couple of weeks ago when I re-imaged the SFR module, but I don't recall if I saw a setting for NTP there. If it was there it may not have been configured at that time.
Thank you for your help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2019 04:36 AM
Hello,
I have the same events and most of the devices that initiate this traffic, belong to voice vlan (voip phones).
I haven's also configured this IP, i have left the default servers.
Did you find why this kind of traffic is being initiated from inside?
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2019 07:12 AM
@anousakisioannis wrote:Hello,
I have the same events and most of the devices that initiate this traffic, belong to voice vlan (voip phones).
I haven's also configured this IP, i have left the default servers.
Did you find why this kind of traffic is being initiated from inside?
Thank you
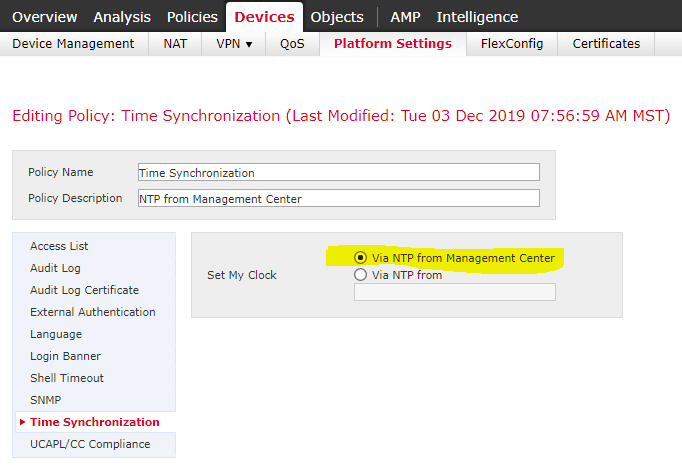
It was never clear as to why our SFR module was looking at that IP for time. I raised a ticket with TAC and the engineer had me create a platform setting policy configured to synchronize time with the FMC. Since I set up that platform setting policy I haven't seen the SFR trying to access the TOR IP.
In my case it was only the SFR module that was doing this. I hadn't seen any other devices touching that TOR IP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2019 07:54 AM
In my case it was only the SFR module that was doing this. I hadn't seen any other devices touching that TOR IP.
I take that back... I just logged in and saw that a one of our field office Xerox printers and our BitDefender appliance tried to access the IP yesterday and the day before. Three occurrences, All port 123 NTP traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2019 08:32 AM
It appears from my research using Cisco Umbrella Investigate that the suspect Emerald Onion-registered address is "squatting" on numerous NTP server DNS records. I'm not sure how this has come to pass but I suspect we may see more from Talos Intelligence on this eventually.
In any case, they include 0.sourcefire.pool.ntp.org (and 1., 2. and 3.)
Known domains hosted by 23.129.64.159
- 1.sophos.pool.ntp.org
- 1.resinio.pool.ntp.org
- 1.coreos.pool.ntp.org
- 1.leeo.pool.ntp.org
- 1.freebsd.pool.ntp.org
- 1.yoctopuce.pool.ntp.org
- 1.boot2docker.pool.ntp.org
- 1.nixos.pool.ntp.org
- 1.arch.pool.ntp.org
- 1.formlabs.pool.ntp.org
- 1.americantime.pool.ntp.org
- 1.scientific.pool.ntp.org
- 1.colubris.pool.ntp.org
- 1.anki.pool.ntp.org
- 1.north-america.pool.ntp.org
- 3.ovcirrus.pool.ntp.org
- 3.digium.pool.ntp.org
- 3.vmware.pool.ntp.org
- 0.android.pool.ntp.org
- 3.inovonicsinc.pool.ntp.org
- 0.bose.pool.ntp.org
- 0.pepwave.pool.ntp.org
- 0.boot2docker.pool.ntp.org
- 3.daktronics.pool.ntp.org
- 3.avaya.pool.ntp.org
- 0.ubnt.pool.ntp.org
- 0.sourcefire.pool.ntp.org
- 3.riverbed.pool.ntp.org
- 3.zscaler.pool.ntp.org
- 3.coreos.pool.ntp.org
- 3.purestorage.pool.ntp.org
- 3.resinio.pool.ntp.org
- 0.debian.pool.ntp.org
- 3.ooma.pool.ntp.org
- 3.americantime.pool.ntp.org
- 0.aerohive.pool.ntp.org
- 0.ciscome.pool.ntp.org
- 3.nixos.pool.ntp.org
- 3.boot2docker.pool.ntp.org
- 0.ciscosb.pool.ntp.org
- 1.exigent.pool.ntp.org
- 1.ipfire.pool.ntp.org
- 1.vmware.pool.ntp.org
- 1.logitech.pool.ntp.org
- 1.vizio.pool.ntp.org
- 1.bctelectronic.pool.ntp.org
- 1.savantsystems.pool.ntp.org
- 1.pfsense.pool.ntp.org
- 1.daktronics.pool.ntp.org
- 1.viking.pool.ntp.org
- 1.purestorage.pool.ntp.org
- 1.echo360.pool.ntp.org
- 1.ooma.pool.ntp.org
- 1.vornexl.pool.ntp.org
- 1.endian.pool.ntp.org
- 1.mitel.pool.ntp.org
- 3.echo360.pool.ntp.org
- 3.north-america.pool.ntp.org
- 2.opnsense.pool.ntp.org
- 3.sophos.pool.ntp.org
- 3.insignia.pool.ntp.org
- 3.leeo.pool.ntp.org
- 3.vizio.pool.ntp.org
- 3.logitech.pool.ntp.org
- 3.manjaro.pool.ntp.org
- 2.boot2docker.pool.ntp.org
- 3.opensuse.pool.ntp.org
- 2.m0n0wall.pool.ntp.org
- 2.nettime.pool.ntp.org
- 3.planefinder.pool.ntp.org
- 3.aastra.pool.ntp.org
- 3.control4.pool.ntp.org
- 3.rhel.pool.ntp.org
- 2.ooma.pool.ntp.org
- 2.coreos.pool.ntp.org
- 3.nettime.pool.ntp.org
- 3.fedora.pool.ntp.org
- 2.gentoo.pool.ntp.org
- 3.gentoo.pool.ntp.org
- 3.irobot.pool.ntp.org
- 3.ubnt.pool.ntp.org
- 3.cloudgenix.pool.ntp.org
- 2.vornexl.pool.ntp.org
- 3.android.pool.ntp.org
- 3.centos.pool.ntp.org
- 3.ciscosb.pool.ntp.org
- 2.control4.pool.ntp.org
- 2.fedora.pool.ntp.org
- 2.sonostime.pool.ntp.org
- us.pool.ntp.org
- 2.vmware.pool.ntp.org
- 2.vizio.pool.ntp.org
- 2.opensuse.pool.ntp.org
- 1.siuslawbb.pool.ntp.org
- 1.digium.pool.ntp.org
- 1.gentoo.pool.ntp.org
- 1.insignia.pool.ntp.org
- 2.americantime.pool.ntp.org
- 2.north-america.pool.ntp.org
- 1.aolt.pool.ntp.org
- 0.pfsense.pool.ntp.org
- 1.opensuse.pool.ntp.org
- 0.nettime.pool.ntp.org
- 1.incanetworks.pool.ntp.org
- 3.lede.pool.ntp.org
- 1.zscaler.pool.ntp.org
- 1.drbsystems.pool.ntp.org
- 159.emeraldonion.org
- 1.planefinder.pool.ntp.org
- 1.android.pool.ntp.org
- pool.ntp.org
- 3.vernier.pool.ntp.org
- 3.amazon.pool.ntp.org
- 2.insignia.pool.ntp.org
- 2.sophos.pool.ntp.org
- 1.fedora.pool.ntp.org
- 1.nettime.pool.ntp.org
- 1.lede.pool.ntp.org
- 2.arch.pool.ntp.org
- 2.leeo.pool.ntp.org
- 1.aastra.pool.ntp.org
- 1.cloudgenix.pool.ntp.org
- 1.servertech.pool.ntp.org
- 2.freebsd.pool.ntp.org
- 0.netcomm.pool.ntp.org
- 0.linksys.pool.ntp.org
- 1.control4.pool.ntp.org
- 1.ciscosb.pool.ntp.org
- 2.drbsystems.pool.ntp.org
- 0.vizio.pool.ntp.org
- 1.bose.pool.ntp.org
- 1.openwrt.pool.ntp.org
- 1.sonostime.pool.ntp.org
- 1.datadog.pool.ntp.org
- 1.netcomm.pool.ntp.org
- 1.shor.pool.ntp.org
- 1.amazon.pool.ntp.org
- 1.ubnt.pool.ntp.org
- 1.us.pool.ntp.org
- 1.aerohive.pool.ntp.org
- 0.sonostime.pool.ntp.org
- 2.mitel.pool.ntp.org
- 2.logitech.pool.ntp.org
- 0.fedora.pool.ntp.org
- 0.rhel.pool.ntp.org
- 2.inovonicsinc.pool.ntp.org
- 2.echo360.pool.ntp.org
- 1.debian.pool.ntp.org
- 0.openwrt.pool.ntp.org
- 0.peplink.pool.ntp.org
- 2.lede.pool.ntp.org
- 2.daktronics.pool.ntp.org
- 2.siuslawbb.pool.ntp.org
- 2.rgnets.pool.ntp.org
- 2.ciscosb.pool.ntp.org
- 2.cloudgenix.pool.ntp.org
- 0.datadog.pool.ntp.org
- 0.shor.pool.ntp.org
- 2.manjaro.pool.ntp.org
- 2.ipaccess.pool.ntp.org
- 1.sourcefire.pool.ntp.org
- 2.riverbed.pool.ntp.org
- 2.aastra.pool.ntp.org
- 2.viking.pool.ntp.org
- 2.irobot.pool.ntp.org
- 0.digium.pool.ntp.org
- 2.servertech.pool.ntp.org
- 3.tosibox.pool.ntp.org
- 3.savantsystems.pool.ntp.org
- 1.rhel.pool.ntp.org
- 1.irobot.pool.ntp.org
- 3.endian.pool.ntp.org
- 0.ubuntu.pool.ntp.org
- 1.centos.pool.ntp.org
- 3.drbsystems.pool.ntp.org
- 3.cctv.pool.ntp.org
- 1.ubuntu.pool.ntp.org
- 3.cumulusnetworks.pool.ntp.org
- 3.sourcefire.pool.ntp.org
- 3.arch.pool.ntp.org
- 3.sonostime.pool.ntp.org
- 3.openwrt.pool.ntp.org
- 3.shor.pool.ntp.org
- 3.us.pool.ntp.org
- 2.anki.pool.ntp.org
- 2.resinio.pool.ntp.org
- 2.idigi.pool.ntp.org
- 2.barix.pool.ntp.org
- 2.pfsense.pool.ntp.org
- 2.planefinder.pool.ntp.org
- 2.inovonics.pool.ntp.org
- 2.kerio.pool.ntp.org
- 2.digium.pool.ntp.org
- 2.formlabs.pool.ntp.org
- 0.daktronics.pool.ntp.org
- 2.centos.pool.ntp.org
- 2.us.pool.ntp.org
- 0.coreos.pool.ntp.org
- 2.rhel.pool.ntp.org
- 0.formlabs.pool.ntp.org
- 2.ubuntu.pool.ntp.org
- 0.north-america.pool.ntp.org
- 0.americantime.pool.ntp.org
- 0.ubiquita.pool.ntp.org
- 0.riverbed.pool.ntp.org
- 0.siuslawbb.pool.ntp.org
- 0.viking.pool.ntp.org
- 0.patton.pool.ntp.org
- 0.arch.pool.ntp.org
- 0.vmware.pool.ntp.org
- 0.leeo.pool.ntp.org
- 0.unicoi.pool.ntp.org
- 0.gentoo.pool.ntp.org
- 0.opensuse.pool.ntp.org
- 0.insignia.pool.ntp.org
- 0.lede.pool.ntp.org
- 0.ooma.pool.ntp.org
- 0.vornexl.pool.ntp.org
- 0.endian.pool.ntp.org
- 0.scientific.pool.ntp.org
- 0.savantsystems.pool.ntp.org
- 0.freebsd.pool.ntp.org
- 1.ipaccess.pool.ntp.org
- 2.cctv.pool.ntp.org
- 1.barix.pool.ntp.org
- 1.trafsys.pool.ntp.org
- 0.irrigationcaddy.pool.ntp.org
- 0.honeywell.pool.ntp.org
- 0.qumulo.pool.ntp.org
- 0.colubris.pool.ntp.org
- 0.xenserver.pool.ntp.org
- 2.openwrt.pool.ntp.org
- 0.logitech.pool.ntp.org
- 0.comrex.pool.ntp.org
- 2.shor.pool.ntp.org
- 0.ipaccess.pool.ntp.org
- 0.axis.pool.ntp.org
- 0.tandberg.pool.ntp.org
- 0.amazon.pool.ntp.org
- 0.weatherflow.pool.ntp.org
- 0.control4.pool.ntp.org
- 0.sophos.pool.ntp.org
- 0.anetd.pool.ntp.org
- 0.cloudgenix.pool.ntp.org
- 0.us.pool.ntp.org
- 0.irobot.pool.ntp.org
- 0.wahsega.pool.ntp.org
- 0.centos.pool.ntp.org
- 0.pool.ntp.org
- 2.aerohive.pool.ntp.org
- 3.inovonics.pool.ntp.org
- 2.datadog.pool.ntp.org
- 3.oaklabs.pool.ntp.org
- 3.exigent.pool.ntp.org
- 2.amazon.pool.ntp.org
- 2.sourcefire.pool.ntp.org
- 3.pfsense.pool.ntp.org
- 3.mitydsp.pool.ntp.org
- 1.manjaro.pool.ntp.org
- 1.ciscome.pool.ntp.org
- north-america.pool.ntp.org
- 3.anki.pool.ntp.org
- 3.catapult.pool.ntp.org
- 3.datadog.pool.ntp.org
- 3.ubuntu.pool.ntp.org
- 3.debian.pool.ntp.org
- 3.aerohive.pool.ntp.org
- 2.zscaler.pool.ntp.org
- 2.nixos.pool.ntp.org
- 2.purestorage.pool.ntp.org
- 3.lenbrook.pool.ntp.org
- 3.viking.pool.ntp.org
- 3.mitel.pool.ntp.org
- 0.echo360.pool.ntp.org
- 0.avaya.pool.ntp.org
- 1.riverbed.pool.ntp.org
- 0.drbsystems.pool.ntp.org
- 3.pool.ntp.org
- 0.ovcirrus.pool.ntp.org
- 0.nti1.pool.ntp.org
- 0.bigswitch.pool.ntp.org
- 0.manjaro.pool.ntp.org
- 0.angstrom.pool.ntp.org
- 0.resinio.pool.ntp.org
- 2.endian.pool.ntp.org
- 0.ipfire.pool.ntp.org
- 1.flatcar.pool.ntp.org
- 1.tandberg.pool.ntp.org
- 1.qumulo.pool.ntp.org
- 1.cumulusnetworks.pool.ntp.org
- 0.mitydsp.pool.ntp.org
- 0.sqst.pool.ntp.org
- 0.planefinder.pool.ntp.org
- 0.sinefa.pool.ntp.org
- 0.lima.pool.ntp.org
- 0.philips.pool.ntp.org
- 2.aolt.pool.ntp.org
- 1.inovonicsinc.pool.ntp.org
- 2.avaya.pool.ntp.org
- 2.gtantp.pool.ntp.org
- 3.xenserver.pool.ntp.org
- 1.angstrom.pool.ntp.org
- 1.vernier.pool.ntp.org
- 1.roamingtrek.pool.ntp.org
- 2.fireeye.pool.ntp.org
- 1.cambridge-audio.pool.ntp.org
- 2.ubnt.pool.ntp.org
- 2.ciscome.pool.ntp.org
- 2.debian.pool.ntp.org
- 3.flatcar.pool.ntp.org
- 0.nixos.pool.ntp.org
- 1.lenbrook.pool.ntp.org
- 1.cloudlinux.pool.ntp.org
- 1.kerio.pool.ntp.org
- 1.avaya.pool.ntp.org
- 1.idigi.pool.ntp.org
- 1.ovcirrus.pool.ntp.org
- 0.wivalley.pool.ntp.org
- 2.tandberg.pool.ntp.org
- 1.ubiquita.pool.ntp.org
- 2.ocedo.pool.ntp.org
- 2.xenserver.pool.ntp.org
- 1.bdrthermea.pool.ntp.org
- 0.bctelectronic.pool.ntp.org
- 0.anki.pool.ntp.org
- 1.sqst.pool.ntp.org
- 3.opnsense.pool.ntp.org
- 1.glooko.pool.ntp.org
- 1.github.pool.ntp.org
- 0.flatcar.pool.ntp.org
- 0.datataker.pool.ntp.org
- 0.aolt.pool.ntp.org
- 0.glooko.pool.ntp.org
- 1.ocedo.pool.ntp.org
- 1.pool.ntp.org
- 0.incanetworks.pool.ntp.org
- 1.lima.pool.ntp.org
- 1.sinefa.pool.ntp.org
- 3.bctelectronic.pool.ntp.org
- 0.zscaler.pool.ntp.org
- 0.kerio.pool.ntp.org
- 2.incanetworks.pool.ntp.org
- 2.flatcar.pool.ntp.org
- 2.vernier.pool.ntp.org
- 2.cumulusnetworks.pool.ntp.org
- 0.digitallumens.pool.ntp.org
- 0.openembedded.pool.ntp.org
- 0.github.pool.ntp.org
- 3.ocedo.pool.ntp.org
- 1.catapult.pool.ntp.org
- 0.vernier.pool.ntp.org
- 0.cloudlinux.pool.ntp.org
- 2.scientific.pool.ntp.org
- 0.zymation.pool.ntp.org
- 0.ocedo.pool.ntp.org
- 2.pool.ntp.org
- 0.nimblestorage.pool.ntp.org
- 1.inovonics.pool.ntp.org
- 1.remarkable.pool.ntp.org
- 2.android.pool.ntp.org
- 0.domiq.pool.ntp.org
- 3.ipaccess.pool.ntp.org
- 3.schneider.pool.ntp.org
- 3.barix.pool.ntp.org
- 1.opnsense.pool.ntp.org
- 1.bigswitch.pool.ntp.org
- 0.inovonicsinc.pool.ntp.org
- 0.cumulusnetworks.pool.ntp.org
- 0.cctv.pool.ntp.org
- 0.wled.pool.ntp.org
- 2.ovcirrus.pool.ntp.org
- 0.inovonics.pool.ntp.org
- 1.patton.pool.ntp.org
- 3.clearlinux.pool.ntp.org
- 0.idigi.pool.ntp.org
- 0.nodemcu.pool.ntp.org
- 0.clearlinux.pool.ntp.org
- 2.develooper.pool.ntp.org
- 2.lima.pool.ntp.org
- 2.sinefa.pool.ntp.org
- 2.novell.pool.ntp.org
- 2.clearlinux.pool.ntp.org
- 0.vobfs.pool.ntp.org
- 0.siemens.pool.ntp.org
- 1.clearlinux.pool.ntp.org
- 1.nodemcu.pool.ntp.org
- 0.beevik-ntp.pool.ntp.org
- 0.exigent.pool.ntp.org
- 3.kerio.pool.ntp.org
- 0.opnsense.pool.ntp.org
- 1.weatherflow.pool.ntp.org
- 2.netbsd.pool.ntp.org
- 2.weatherflow.pool.ntp.org
- 1.rgnets.pool.ntp.org
- 3.gtantp.pool.ntp.org
- 1.xenserver.pool.ntp.org
- 3.incanetworks.pool.ntp.org
- 3.cloudlinux.pool.ntp.org
- 0.sailfishos.pool.ntp.org
- 2.bctelectronic.pool.ntp.org
- 3.glooko.pool.ntp.org
- 0.bdrthermea.pool.ntp.org
- 3.scientific.pool.ntp.org
- 0.espclock.pool.ntp.org
- 3.sqst.pool.ntp.org
- 2.savantsystems.pool.ntp.org
- 0.powerschool.pool.ntp.org
- 1.thesimple.pool.ntp.org
- 0.avizia.pool.ntp.org
- 0.askozia.pool.ntp.org
- 2.lenbrook.pool.ntp.org
- 0.canary.pool.ntp.org
- 3.bdrthermea.pool.ntp.org
- 0.cambridge-audio.pool.ntp.org
- 3.weatherflow.pool.ntp.org
- 3.avc1.pool.ntp.org
- 3.lima.pool.ntp.org
- 0.dakim.pool.ntp.org
- 1.oaklabs.pool.ntp.org
- 0.youview.pool.ntp.org
- 2.cloudlinux.pool.ntp.org
- 2.oaklabs.pool.ntp.org
- 0.lenbrook.pool.ntp.org
- 0.natinst.pool.ntp.org
- 3.tandberg.pool.ntp.org
- 1.gtantp.pool.ntp.org
- 2.invoxia.pool.ntp.org
- 2.bigswitch.pool.ntp.org
- 1.serverdensity.pool.ntp.org
- 3.extrahop.pool.ntp.org
- 3.thesimple.pool.ntp.org
- 1.netbsd.pool.ntp.org
- 2.cambridge-audio.pool.ntp.org
- 2.exigent.pool.ntp.org
- 0.thesimple.pool.ntp.org
- 2.linksys.pool.ntp.org
- 3.bigswitch.pool.ntp.org
- 1.tradfri.pool.ntp.org
- 3.cambridge-audio.pool.ntp.org
- 2.tosibox.pool.ntp.org
- 2.dragonmint.pool.ntp.org
- 2.avc1.pool.ntp.org
- 0.serverdensity.pool.ntp.org
- 3.honeywell.pool.ntp.org
- 0.schneider.pool.ntp.org
- 0.roamingtrek.pool.ntp.org
- 2.angstrom.pool.ntp.org
- 1.extrahop.pool.ntp.org
- 1.cctv.pool.ntp.org
- 2.natinst.pool.ntp.org
- 2.canary.pool.ntp.org
- 1.linksys.pool.ntp.org
- 3.trafsys.pool.ntp.org
- 0.openmandriva.pool.ntp.org
- 2.thesimple.pool.ntp.org
- 1.novell.pool.ntp.org
- 0.rhino.pool.ntp.org
- 2.roamingtrek.pool.ntp.org
- 3.vtech.pool.ntp.org
- 3.forcepoint.pool.ntp.org
- 1.powerschool.pool.ntp.org
- 0.vyatta.pool.ntp.org
- 1.natinst.pool.ntp.org
- 1.kodakalaris.pool.ntp.org
- 0.omnios.pool.ntp.org
- 0.epic.pool.ntp.org
- 1.robin.pool.ntp.org
- 3.progress.pool.ntp.org
- 2.extron.pool.ntp.org
- 1.fireeye.pool.ntp.org
- 2.glooko.pool.ntp.org
- 0.vasco.pool.ntp.org
- 2.sqst.pool.ntp.org
- 0.cbrx.pool.ntp.org
- 3.rgnets.pool.ntp.org
- 0.rgnets.pool.ntp.org
- 1.connecteddata.pool.ntp.org
- 1.clearswift.pool.ntp.org
- 0.pokercopilot.pool.ntp.org
- 0.ubilinux.pool.ntp.org
- 0.fetchtv.pool.ntp.org
- 2.nodemcu.pool.ntp.org
- 3.roamingtrek.pool.ntp.org
- 0.guix.pool.ntp.org
- 3.guix.pool.ntp.org
- 3.linksys.pool.ntp.org
- 2.schneider.pool.ntp.org
- 0.ipcop.pool.ntp.org
- 2.guix.pool.ntp.org
- 3.youview.pool.ntp.org
- 1.guix.pool.ntp.org
- 1.attvdna.pool.ntp.org
- 3.nodemcu.pool.ntp.org
- 2.honeywell.pool.ntp.org
- 2.bdrthermea.pool.ntp.org
- 1.jaxcontrols.pool.ntp.org
- 2.homewizard.pool.ntp.org
- 1.vasco.pool.ntp.org
- 2.tradfri.pool.ntp.org
- 0.extron.pool.ntp.org
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2019 12:44 AM
How can we report it to Talos?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2019 04:12 AM
You can make a report to Talos using the following URL:
https://talosintelligence.com/reputation_center/support#reputation_center_support_ticket
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: