- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Site to Site Cisco ASA, 1 of 3 LAN is not Working
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2020 09:30 AM
Hello,
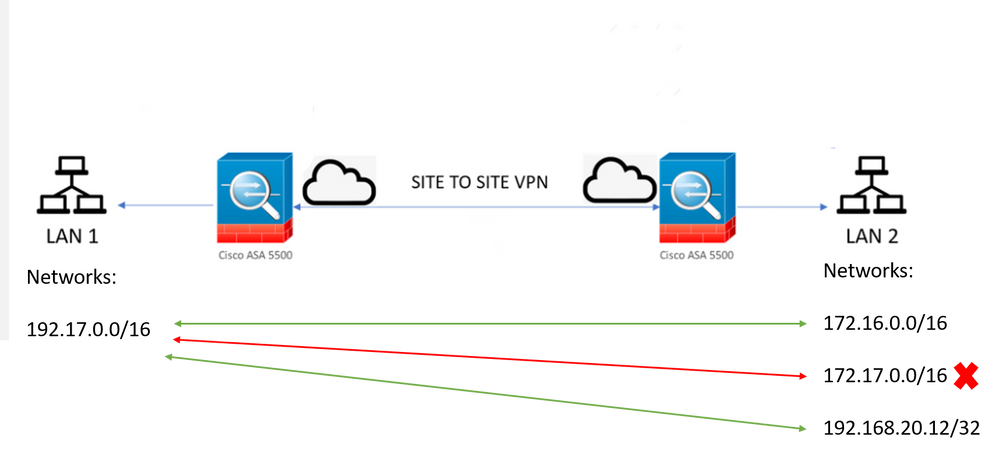
I have a Site to Site VPN Tunnel Between 2 Cisco ASAs, my isse is that I added 2 Networks, but just one is working, I cheked both sides config, both routers have routes to the FWs, but I cannot reach it, the strange is that I added a new network (it was juts one hots) and it worked. So I do not know what else to do.
I will add configs pointing to the Site to Site part.
Here is my config on the LAN1:
object-group network DM_INLINE_NETWORK_5
network-object 172.16.0.0 255.255.0.0
network-object 172.17.0.0 255.255.0.0
network-object object MarVMHost
object-group network DM_INLINE_NETWORK_8
network-object 172.16.0.0 255.255.0.0
network-object 172.17.0.0 255.255.0.0
object-group network DM_INLINE_NETWORK_10
network-object 172.16.0.0 255.255.0.0
network-object 172.17.0.0 255.255.0.0
network-object object Mar_VPN_SubNET
network-object object MarVMHost
network-object object 172.17.20.0
object-group network DM_INLINE_NETWORK_6
network-object 172.16.0.0 255.255.0.0
network-object 172.17.0.0 255.255.0.0
network-object object MarVMHost
object-group network DM_INLINE_NETWORK_7
network-object 172.17.0.0 255.255.0.0
network-object 172.16.0.0 255.255.0.0
network-object object MarVMHost
object-group network DM_INLINE_NETWORK_11
network-object object 172.17.20.0
network-object object NETWORK_OBJ_172.16.0.0_16
access-list outside.acl.in extended permit icmp any any echo-reply
access-list outside.acl.in extended permit icmp any any time-exceeded
access-list outside.acl.in extended permit tcp any object obj-Video.Conf.Private range 3230 3241
access-list outside.acl.in extended permit udp any object obj-Video.Conf.Private range 3230 3291
access-list outside.acl.in extended permit tcp any object obj-Video.Conf.Private eq h323
access-list outside.acl.in extended permit ip any any log disable inactive
access-list split.tunnel.acl standard permit 192.17.0.0 255.255.0.0
access-list split.tunnel.acl standard permit 172.28.0.0 255.255.0.0
access-list split.tunnel.acl standard permit 172.29.0.0 255.255.0.0
access-list split.tunnel.acl standard permit 172.16.0.0 255.255.0.0
access-list split.tunnel.acl standard permit 172.17.0.0 255.255.0.0
access-list vpn.to.m extended permit ip object-group DM_INLINE_NETWORK_4 object-group grp-M.Subnets
access-list vpn.to.p extended permit ip object-group DM_INLINE_NETWORK_1 object-group grp-P.Subnets
access-list sfr.acl extended permit ip any any
access-list net.to.vzt extended permit ip any object-group DM_INLINE_NETWORK_2
access-list net.to.vzt extended permit ip object-group DM_INLINE_NETWORK_3 any
access-list AnyConnect_Client_Local_Print extended deny ip any4 any4
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq lpd
access-list AnyConnect_Client_Local_Print remark IPP: Internet Printing Protocol
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 631
access-list AnyConnect_Client_Local_Print remark Windows' printing port
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 9100
access-list AnyConnect_Client_Local_Print remark mDNS: multicast DNS protocol
access-list AnyConnect_Client_Local_Print extended permit udp any4 host 224.0.0.251 eq 5353
access-list AnyConnect_Client_Local_Print remark LLMNR: Link Local Multicast Name Resolution protocol
access-list AnyConnect_Client_Local_Print extended permit udp any4 host 224.0.0.252 eq 5355
access-list AnyConnect_Client_Local_Print remark TCP/NetBIOS protocol
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 137
access-list AnyConnect_Client_Local_Print extended permit udp any4 any4 eq netbios-ns
access-list vpn.to.mar extended permit ip 192.17.0.0 255.255.0.0 object-group DM_INLINE_NETWORK_10
access-list vpn.to.mar extended permit ip object-group DM_INLINE_NETWORK_5 any
access-list net.to.mar extended permit ip any object-group DM_INLINE_NETWORK_6
access-list net.to.mar extended permit ip object-group DM_INLINE_NETWORK_7 any
nat (inside,outside) source static 192.17.17.0 192.17.17.0 destination static DM_INLINE_NETWORK_9 DM_INLINE_NETWORK_9 no-proxy-arp route-lookup
nat (inside,outside) source static obj-192.17.0.0 obj-192.17.0.0 destination static obj-192.17.0.0 obj-192.17.0.0 no-proxy-arp route-lookup
nat (inside,outside2) source static obj-192.17.0.0-2 obj-192.17.0.0-2 destination static obj-192.17.0.0-2 obj-192.17.0.0-2 no-proxy-arp route-lookup
nat (inside,outside) source static NETWORK_OBJ_192.17.0.0_16 NETWORK_OBJ_192.17.0.0_16 destination static DM_INLINE_NETWORK_8 DM_INLINE_NETWORK_8 no-proxy-arp route-lookup
nat (inside,outside) source static NETWORK_OBJ_192.17.0.0_16 NETWORK_OBJ_192.17.0.0_16 destination static DM_INLINE_NETWORK_10 DM_INLINE_NETWORK_10 no-proxy-arp route-lookup
nat (inside,outside) source static 192.17.17.0 192.17.17.0 destination static DM_INLINE_NETWORK_11 DM_INLINE_NETWORK_11 no-proxy-arp route-lookup
Here is my config on the LAN1:
object-group network DM_INLINE_NETWORK_11
network-object host 172.16.0.1
network-object object obj-172.16.0.0
network-object 172.17.0.0 255.255.0.0
network-object object MarVMHost
network-object Net-RedZone 255.255.255.0
network-object Net-WiFi 255.255.255.0
object-group network DM_INLINE_NETWORK_13
network-object host 192.17.10.134
network-object object Jenkins
object-group network DM_INLINE_NETWORK_14
network-object 172.16.0.0 255.255.0.0
network-object 172.17.0.0 255.255.0.0
network-object object obj-172.16.101.0
network-object object MarVMHost
network-object 172.17.19.0 255.255.255.0
network-object Net-RedZone 255.255.255.0
network-object Net-WiFi 255.255.255.0
object-group network DM_INLINE_NETWORK_15
network-object 172.16.0.0 255.255.0.0
network-object 172.17.0.0 255.255.0.0
object-group network DM_INLINE_NETWORK_16
network-object object obj-172.16.0.0
network-object object obj-172.16.101.0
network-object object MarVMHost
network-object object Mar17
object-group network MarNet17
network-object Net-RedZone 255.255.255.0
network-object Net-WiFi 255.255.255.0
network-object object Mar17
network-object object Net-AP_Mgmt
access-list Split-Tunnel-ACL standard permit 172.16.0.0 255.255.0.0
access-list Split-Tunnel-ACL standard permit 192.17.0.0 255.255.0.0
access-list Split-Tunnel-ACL standard permit 172.28.0.0 255.255.0.0
access-list Split-Tunnel-ACL standard permit 172.29.0.0 255.255.0.0
access-list Split-Tunnel-ACL standard permit 172.17.20.0 255.255.255.0
access-list Split-Tunnel-ACL standard permit 172.17.21.0 255.255.255.0
access-list Split-Tunnel-ACL standard permit 192.168.0.0 255.255.255.0
access-list Split-Tunnel-ACL standard permit 172.17.19.0 255.255.255.0
access-list ACL-SNMP extended permit ip object-group DM_INLINE_NETWORK_13 object-group DM_INLINE_NETWORK_11
access-list outside_cryptomap extended permit ip object-group DM_INLINE_NETWORK_14 192.17.0.0 255.255.0.0
access-list outside_cryptomap extended permit ip object-group DM_INLINE_NETWORK_16 192.17.0.0 255.255.0.0
access-list net.to.n extended permit ip any 192.17.0.0 255.255.0.0
access-list net.to.n extended permit ip 192.17.0.0 255.255.0.0 any
nat (inside,outside) source static obj-172.17.20.0 obj-172.17.20.0 destination static obj-172.16.101.0 obj-172.16.101.0 no-proxy-arp route-lookup
nat (inside,outside) source static obj-172.17.21.0 obj-172.17.21.0 destination static obj-172.16.101.0 obj-172.16.101.0 no-proxy-arp route-lookup
nat (inside,outside) source static obj-172.16.0.0 obj-172.16.0.0 destination static obj-172.16.101.0 obj-172.16.101.0 no-proxy-arp route-lookup
nat (inside,outside) source static any any destination static NETWORK_OBJ_172.18.0.0_24 NETWORK_OBJ_172.18.0.0_24 no-proxy-arp route-lookup
nat (inside,outside) source static DM_INLINE_NETWORK_15 DM_INLINE_NETWORK_15 destination static NETWORK_OBJ_192.17.0.0_16 NETWORK_OBJ_192.17.0.0_16 no-proxy-arp route-lookup
nat (inside,outside) source static DM_INLINE_NETWORK_16 DM_INLINE_NETWORK_16 destination static NETWORK_OBJ_192.17.0.0_16 NETWORK_OBJ_192.17.0.0_16 no-proxy-arp route-lookup
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2020 10:46 AM
Sometimes, the FW did not take all the Subnets on the Phase 2, so try this:
Move the Subnets that are not working to the Top of the ACL od the CryptoMap
And validate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2020 11:37 AM
please upload all the configuration. the provided one are not enough.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2020 12:09 PM
LAN 1
N-HQ-FW1/sec/act# sh run
: Saved
:
: Serial Number:
: Hardware: ASA5506, 4096 MB RAM, CPU Atom C2000 series 1250 MHz, 1 CPU (4 cores)
:
ASA Version 9.6(3)1
!
hostname N-HQ-FW1
domain-name N.com
enable password
names
ip local pool vpn.pool 192.17.17.11-192.17.17.250 mask 255.255.255.0
!
interface GigabitEthernet1/1
nameif inside
security-level 100
ip address 192.17.14.21 255.255.255.0 standby 192.17.14.22
!
interface GigabitEthernet1/2
description Windstream (primary)
nameif outside
security-level 0
ip address 40.141.230.226 255.255.255.248 standby 40.141.230.228
!
interface GigabitEthernet1/3
description Comcast (backup)
nameif outside2
security-level 0
ip address 173.9.221.41 255.255.255.248 standby 173.9.221.42
!
interface GigabitEthernet1/4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/5
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/6
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/7
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/8
description LAN/STATE Failover Interface
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
boot system disk0:/asa963-1-lfbff-k8.SPA
ftp mode passive
clock timezone CST -6
clock summer-time CDT recurring
dns domain-lookup inside
dns domain-lookup outside
dns domain-lookup outside2
dns server-group DefaultDNS
domain-name N.com
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network obj-192.17.0.0
subnet 192.17.0.0 255.255.0.0
object network obj-192.17.0.0-2
subnet 192.17.0.0 255.255.0.0
object network obj-SheetLine.Private
host 192.17.10.172
object network obj-Video.Conf.Private
host 192.17.12.199
object network obj-TS.Private
host 192.17.10.127
object network obj-Dameware.MiniRemote
host 192.17.10.190
description "Dameware Mini Remote Control external"
object network DCVZT
subnet 172.28.100.0 255.255.255.0
object network StaVG
subnet 172.28.120.0 255.255.255.0
description StaVG
object network VZT
host 192.17.12.170
description RouterAlestraLevel3
object network cisco9k
host 192.17.10.53
object network Cisco9K1
host 192.17.14.1
object network StaAmerica
subnet 172.29.0.0 255.255.0.0
description StaAmerica
object network PolycomStaGarcia
host 172.28.120.14
object network PolycomVZT
host 172.28.127.15
object network PolycomIMP
host 172.28.129.15
object network PolycomStaTlalne
host 172.28.123.16
object network PolycomN
host 192.17.12.199
object network Santi
host 192.17.10.230
description Santi
object network NET-MARCalifornia
subnet 192.168.1.0 255.255.255.0
object network NETWORK_OBJ_192.17.10.0_24
subnet 192.17.10.0 255.255.255.0
object network Jira_N
host 192.17.10.72
object network TestVPNMAR
host 172.16.1.22
object network NETWORK_OBJ_172.16.0.0_16
subnet 172.16.0.0 255.255.0.0
object network TS01_N
host 192.17.10.127
object network DC1_MAR
host 172.16.1.22
object network DC2_MAR
host 172.16.1.77
object network Flori
host 192.17.12.92
object network NPDC
host 192.17.10.102
object network NDC01
host 192.17.10.194
object network N_Confluence
host 192.17.10.71
object network N_Nagios
host 192.17.10.134
object network 192.17.17.0
subnet 192.17.17.0 255.255.255.0
object network UTL1_MAR
host 172.16.10.155
object network UTL01_N
host 192.17.10.124
object network NETWORK_OBJ_192.17.0.0_16
subnet 192.17.0.0 255.255.0.0
object network MAR_VPN_SubNET
subnet 172.16.101.0 255.255.255.0
object network MARVMHost
host 192.168.20.12
description MARVMHost
object network 172.17.20.0
subnet 172.17.20.0 255.255.254.0
object-group network grp-HQ.LAN.Subnets
network-object 192.17.10.0 255.255.255.0
network-object 192.17.12.0 255.255.255.0
network-object object 192.17.17.0
object-group network grp-Pri.Subnets
network-object 192.17.30.0 255.255.255.0
network-object 192.17.31.0 255.255.255.0
object-group network grp-MW.Subnets
network-object 192.17.20.0 255.255.255.0
network-object 192.17.21.0 255.255.255.0
object-group network obj-Dameware.ProxyServer
network-object host 192.17.10.190
object-group service grp-Dameware.Ports tcp
port-object eq https
port-object range 6130 6133
object-group network DM_INLINE_NETWORK_1
network-object object DCVZT
network-object object StaVG
group-object grp-HQ.LAN.Subnets
network-object object StaAmerica
object-group network DM_INLINE_NETWORK_2
network-object object DCVZT
network-object object StaVG
network-object object StaAmerica
object-group network DM_INLINE_NETWORK_3
network-object object DCVZT
network-object object StaVG
network-object object StaAmerica
object-group network DM_INLINE_NETWORK_4
network-object object DCVZT
network-object object StaVG
group-object grp-HQ.LAN.Subnets
network-object object StaAmerica
object-group network PolycomsVZT
network-object object PolycomIMP
network-object object PolycomStaGarcia
network-object object PolycomStaTlalne
network-object object PolycomVZT
object-group network DM_INLINE_NETWORK_5
network-object 172.16.0.0 255.255.0.0
network-object 172.17.0.0 255.255.0.0
network-object object MARVMHost
object-group network DM_INLINE_NETWORK_8
network-object 172.16.0.0 255.255.0.0
network-object 172.17.0.0 255.255.0.0
object-group network DM_INLINE_NETWORK_9
group-object grp-MW.Subnets
group-object grp-Pri.Subnets
object-group network DM_INLINE_NETWORK_10
network-object 172.16.0.0 255.255.0.0
network-object 172.17.0.0 255.255.0.0
network-object object MAR_VPN_SubNET
network-object object MARVMHost
network-object object 172.17.20.0
object-group network DM_INLINE_NETWORK_6
network-object 172.16.0.0 255.255.0.0
network-object 172.17.0.0 255.255.0.0
network-object object MARVMHost
object-group network DM_INLINE_NETWORK_7
network-object 172.17.0.0 255.255.0.0
network-object 172.16.0.0 255.255.0.0
network-object object MARVMHost
object-group network DM_INLINE_NETWORK_11
network-object object 172.17.20.0
network-object object NETWORK_OBJ_172.16.0.0_16
access-list outside.acl.in extended permit icmp any any echo-reply
access-list outside.acl.in extended permit icmp any any time-exceeded
access-list outside.acl.in extended permit tcp any object obj-Video.Conf.Private range 3230 3241
access-list outside.acl.in extended permit udp any object obj-Video.Conf.Private range 3230 3291
access-list outside.acl.in extended permit tcp any object obj-Video.Conf.Private eq h323
access-list outside.acl.in extended permit ip any any log disable inactive
access-list split.tunnel.acl standard permit 192.17.0.0 255.255.0.0
access-list split.tunnel.acl standard permit 172.28.0.0 255.255.0.0
access-list split.tunnel.acl standard permit 172.29.0.0 255.255.0.0
access-list split.tunnel.acl standard permit 172.16.0.0 255.255.0.0
access-list split.tunnel.acl standard permit 172.17.0.0 255.255.0.0
access-list vpn.to.MW extended permit ip object-group DM_INLINE_NETWORK_4 object-group grp-MW.Subnets
access-list vpn.to.Pri extended permit ip object-group DM_INLINE_NETWORK_1 object-group grp-Pri.Subnets
access-list sfr.acl extended permit ip any any
access-list net.to.vzt extended permit ip any object-group DM_INLINE_NETWORK_2
access-list net.to.vzt extended permit ip object-group DM_INLINE_NETWORK_3 any
access-list AnyConnect_Client_Local_Print extended deny ip any4 any4
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq lpd
access-list AnyConnect_Client_Local_Print remark IPP: Internet Printing Protocol
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 631
access-list AnyConnect_Client_Local_Print remark Windows' printing port
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 9100
access-list AnyConnect_Client_Local_Print remark mDNS: multicast DNS protocol
access-list AnyConnect_Client_Local_Print extended permit udp any4 host 224.0.0.251 eq 5353
access-list AnyConnect_Client_Local_Print remark LLMNR: Link Local Multicast Name Resolution protocol
access-list AnyConnect_Client_Local_Print extended permit udp any4 host 224.0.0.252 eq 5355
access-list AnyConnect_Client_Local_Print remark TCP/NetBIOS protocol
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 137
access-list AnyConnect_Client_Local_Print extended permit udp any4 any4 eq netbios-ns
access-list vpn.to.MAR extended permit ip 192.17.0.0 255.255.0.0 object-group DM_INLINE_NETWORK_10
access-list vpn.to.MAR extended permit ip object-group DM_INLINE_NETWORK_5 any
access-list net.to.MAR extended permit ip any object-group DM_INLINE_NETWORK_6
access-list net.to.MAR extended permit ip object-group DM_INLINE_NETWORK_7 any
pager lines 24
logging enable
logging asdm informational
mtu inside 1500
mtu outside 1500
mtu outside2 1500
failover
failover lan interface folink GigabitEthernet1/8
failover key *****
failover replication http
failover mac address GigabitEthernet1/1 0000.aaaa.0001 0000.aaaa.0002
failover mac address GigabitEthernet1/2 0000.aaaa.1111 0000.aaaa.1112
failover mac address GigabitEthernet1/3 0000.aaaa.2221 0000.aaaa.2222
failover link folink GigabitEthernet1/8
failover interface ip folink 169.254.254.1 255.255.255.252 standby 169.254.254.2
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-771-150.bin
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 16384
nat (inside,outside) source static 192.17.17.0 192.17.17.0 destination static DM_INLINE_NETWORK_9 DM_INLINE_NETWORK_9 no-proxy-arp route-lookup
nat (inside,outside) source static obj-192.17.0.0 obj-192.17.0.0 destination static obj-192.17.0.0 obj-192.17.0.0 no-proxy-arp route-lookup
nat (inside,outside2) source static obj-192.17.0.0-2 obj-192.17.0.0-2 destination static obj-192.17.0.0-2 obj-192.17.0.0-2 no-proxy-arp route-lookup
nat (inside,outside) source static NETWORK_OBJ_192.17.0.0_16 NETWORK_OBJ_192.17.0.0_16 destination static DM_INLINE_NETWORK_8 DM_INLINE_NETWORK_8 no-proxy-arp route-lookup
nat (inside,outside) source static NETWORK_OBJ_192.17.0.0_16 NETWORK_OBJ_192.17.0.0_16 destination static DM_INLINE_NETWORK_10 DM_INLINE_NETWORK_10 no-proxy-arp route-lookup
nat (inside,outside) source static 192.17.17.0 192.17.17.0 destination static DM_INLINE_NETWORK_11 DM_INLINE_NETWORK_11 no-proxy-arp route-lookup
!
object network obj-192.17.0.0
nat (inside,outside) dynamic interface
object network obj-192.17.0.0-2
nat (inside,outside2) dynamic interface
object network obj-Video.Conf.Private
nat (inside,outside) static 40.141.230.227
access-group outside.acl.in in interface outside
access-group outside.acl.in in interface outside2
route outside 0.0.0.0 0.0.0.0 40.141.230.225 1 track 1
route outside2 0.0.0.0 0.0.0.0 173.9.221.46 250
route outside 8.8.8.8 255.255.255.255 40.141.230.225 1
route inside 172.28.0.0 255.255.0.0 192.17.14.1 1
route inside 172.29.0.0 255.255.0.0 192.17.14.1 1
route inside 192.17.0.0 255.255.0.0 192.17.14.1 1
route outside 192.17.20.0 255.255.255.0 40.141.230.225 1
route outside 192.17.21.0 255.255.255.0 40.141.230.225 1
route outside 192.17.30.0 255.255.255.0 40.141.230.225 1
route outside 192.17.31.0 255.255.255.0 40.141.230.225 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
aaa-server AD protocol ldap
max-failed-attempts 5
aaa-server AD (inside) host 192.17.10.102
timeout 20
server-port 389
ldap-base-dn DC=N,DC=local
ldap-scope subtree
ldap-login-password *****
ldap-login-dn CN=Administrator,CN=Users,DC=N,DC=local
server-type microsoft
user-identity default-domain LOCAL
aaa authentication http console LOCAL
aaa authentication serial console LOCAL
aaa authentication ssh console LOCAL
aaa authentication telnet console LOCAL
aaa authentication enable console LOCAL
aaa authentication secure-http-client
http server enable
http 0.0.0.0 0.0.0.0 inside
no snmp-server location
no snmp-server contact
sysopt connection preserve-vpn-flows
sla monitor 1
type echo protocol ipIcmpEcho 8.8.8.8 interface outside
num-packets 3
timeout 2000
frequency 3
sla monitor schedule 1 life forever start-time now
service sw-reset-button
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS mode transport
crypto ipsec ikev2 ipsec-proposal ESP-AES128-SHA
protocol esp encryption aes
protocol esp integrity sha-1
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal 3DES
protocol esp encryption 3des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal DES
protocol esp encryption des
protocol esp integrity sha-1 md5
crypto ipsec security-association pmtu-aging infinite
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map l2l 1 match address vpn.to.MAR
crypto map l2l 1 set peer 198.30.101.70
crypto map l2l 1 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map l2l 1 set ikev2 ipsec-proposal DES 3DES AES AES192 AES256 ESP-AES128-SHA
crypto map l2l 10 match address vpn.to.MW
crypto map l2l 10 set peer 107.209.3.121
crypto map l2l 10 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map l2l 10 set ikev2 ipsec-proposal ESP-AES128-SHA
crypto map l2l 20 match address vpn.to.Pri
crypto map l2l 20 set peer 50.79.62.201
crypto map l2l 20 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map l2l 20 set ikev2 ipsec-proposal ESP-AES128-SHA
crypto map l2l 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map l2l interface outside
crypto ca trustpool policy
crypto ikev2 policy 10
encryption aes
integrity sha
group 2
prf sha
lifetime seconds 28800
crypto ikev2 enable outside
crypto ikev1 enable outside
crypto ikev1 policy 20
authentication rsa-sig
encryption aes-256
hash sha
group 2
lifetime 86400
crypto ikev1 policy 30
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 86400
crypto ikev1 policy 50
authentication rsa-sig
encryption aes-192
hash sha
group 2
lifetime 86400
crypto ikev1 policy 60
authentication pre-share
encryption aes-192
hash sha
group 2
lifetime 86400
crypto ikev1 policy 80
authentication rsa-sig
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 policy 90
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 policy 110
authentication rsa-sig
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 120
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 140
authentication rsa-sig
encryption des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 150
authentication pre-share
encryption des
hash sha
group 2
lifetime 86400
!
track 1 rtr 1 reachability
telnet timeout 5
ssh stricthostkeycheck
ssh 0.0.0.0 0.0.0.0 inside
ssh timeout 5
ssh version 2
ssh key-exchange group dh-group14-sha1
console timeout 0
management-access inside
vpn-sessiondb max-anyconnect-premium-or-essentials-limit 10
priority-queue outside
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ntp server 64.113.32.5
ntp server 129.6.15.30
ntp server 24.56.178.140
webvpn
enable outside
enable outside2
anyconnect image disk0:/anyconnect-win-4.3.05017-k9.pkg 1
anyconnect image disk0:/anyconnect-macosx-i386-4.3.05017-k9.pkg 2
anyconnect enable
tunnel-group-list enable
cache
disable
error-recovery disable
group-policy GroupPolicy_198.30.101.70 internal
group-policy GroupPolicy_198.30.101.70 attributes
vpn-tunnel-protocol ikev1 ikev2
group-policy AnyConnect internal
group-policy AnyConnect attributes
dns-server value 192.17.10.102
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value split.tunnel.acl
address-pools value vpn.pool
dynamic-access-policy-record DfltAccessPolicy
tunnel-group AnyConnect type remote-access
tunnel-group AnyConnect general-attributes
authentication-server-group AD
default-group-policy AnyConnect
tunnel-group AnyConnect webvpn-attributes
group-alias AnyConnect enable
tunnel-group tsupport type remote-access
tunnel-group tsupport general-attributes
default-group-policy AnyConnect
tunnel-group tsupport webvpn-attributes
group-url https://173.9.221.41/tsupport enable
group-url https://40.141.230.226/tsupport enable
group-url https://vpn.N.com/tsupport enable
tunnel-group 107.209.3.121 type ipsec-l2l
tunnel-group 107.209.3.121 ipsec-attributes
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
tunnel-group 50.79.62.201 type ipsec-l2l
tunnel-group 50.79.62.201 ipsec-attributes
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
tunnel-group 198.30.101.70 type ipsec-l2l
tunnel-group 198.30.101.70 general-attributes
default-group-policy GroupPolicy_198.30.101.70
tunnel-group 198.30.101.70 ipsec-attributes
ikev1 pre-shared-key *****
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
!
class-map VPN-MAR-RDP
match port tcp eq 3389
match tunnel-group 198.30.101.70
class-map VPN-MAR-HTTPS
match port tcp eq https
match tunnel-group 198.30.101.70
class-map VPN-MAR-SQL
match port tcp eq 1433
match tunnel-group 198.30.101.70
class-map VPN-MAR-HTTP
match port tcp eq www
match tunnel-group 198.30.101.70
class-map sfr
match access-list sfr.acl
class-map VPN-MAR-HTTP2
match port tcp eq 8080
match tunnel-group 198.30.101.70
class-map inspection_default
match default-inspection-traffic
class-map VPN-MAR-RDP2
match port udp eq 3389
match tunnel-group 198.30.101.70
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map VPN-MAR-PRIORITY
class VPN-MAR-RDP
priority
class VPN-MAR-RDP2
priority
class VPN-MAR-HTTP
priority
class VPN-MAR-HTTP2
priority
class VPN-MAR-HTTPS
priority
class VPN-MAR-SQL
priority
policy-map global_policy
class inspection_default
inspect ftp
inspect h323 h225
inspect h323 ras
inspect ip-options
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
inspect xdmcp
inspect dns preset_dns_map
class sfr
sfr fail-open
!
service-policy global_policy global
service-policy VPN-MAR-PRIORITY interface outside
prompt hostname priority state
no call-home reporting anonymous
Cryptochecksum:6df49de9e2f339f0a16bcf2254ba2858
: end
N-HQ-FW1/sec/act#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2020 12:23 PM
LAN 2
vpn# sh run
: Saved
:
: Serial Number:
: Hardware: ASA5505, 512 MB RAM, CPU Geode 500 MHz
:
ASA Version 9.2(3)
!
hostname vpn
domain-name mar.com
xlate per-session deny tcp any4 any4
xlate per-session deny tcp any4 any6
xlate per-session deny tcp any6 any4
xlate per-session deny tcp any6 any6
xlate per-session deny udp any4 any4 eq domain
xlate per-session deny udp any4 any6 eq domain
xlate per-session deny udp any6 any4 eq domain
xlate per-session deny udp any6 any6 eq domain
passwd ZhT07TejNEHLesjr encrypted
names
name 172.16.1.30 Server-Appsvr1
name 172.16.1.5 Server-Briefcase1
name 172.16.1.7 Server-CyBlock
name 172.16.1.38 Server-EDI1
name 172.16.1.8 Server-IceWarp
name 172.16.1.9 Server-Remote
name 172.16.1.35 Server-Remote1
name 198.30.101.66 OUTSIDE_198.30.101.66
name 198.30.101.67 OUTSIDE_198.30.101.67
name 198.30.101.68 OUTSIDE_198.30.101.68
name 198.30.101.69 OUTSIDE_198.30.101.69
name 198.30.101.72 OUTSIDE_198.30.101.72
name 198.30.101.73 OUTSIDE_198.30.101.73
name 198.30.101.74 OUTSIDE_198.30.101.74
name 12.28.215.206 Server-EDIPartner1
name 209.95.232.130 Server-EDIPartner2
name 172.16.5.0 Network_NAT_16.5
name 172.16.1.166 PC-J-GARNER-VISTA
name 172.16.1.160 PC-K-BECKLEY-XP
name 172.16.1.220 PC-N-COUTIS-XP
name 172.16.1.135 PC-R-COLVIN-W7
name 172.16.1.144 PC-V-MOSLEY-W7
name 172.16.1.12 Server-HyperV2
name 172.16.1.10 Server-Hyperv1
name 172.16.1.20 Server-Symantec
name 172.16.1.36 Server-Util-2
name 65.196.53.194 Server-EDIPartner3
name 172.16.1.44 Server-TS1
name 172.16.250.101 DEV-GANSAW
name 192.168.0.0 Network-TX
name 50.194.86.245 OUTSIDE_50.194.86.245 description Temporary rule for VVICINI
name 172.16.250.102 D-Grid-Sa description HD Ticket 71868 - Add RDP Via PAT Outside to Inside
name 173.24.96.0 Net-173.24.96.0
name 184.164.128.0 Net-184.164.128.0
name 173.246.96.0 Net-173.246.96.0
name 185.26.124.0 Net-185.26.124.0
name 217.70.176.0 Net-217.70.176.0
name 46.226.104.0 Net-46.226.104.0
name 92.243.0.0 Net-92.243.0.0
name 95.142.160.0 Net-95.142.160.0
name 108.170.0.0 Net-108.170.0.0
name 162.213.252.0 Net-162.213.252.0
name 162.213.254.0 Net-162.213.254.0
name 174.138.160.0 Net-174.138.160.0
name 184.171.160.0 Net-184.171.160.0
name 184.95.32.0 Net-184.95.32.0
name 192.198.192.0 Net-192.198.192.0
name 192.198.200.0 Net-192.198.200.0
name 198.15.64.0 Net-198.15.64.0
name 198.24.128.0 Net-198.24.128.0
name 199.48.165.0 Net-199.48.165.0
name 209.188.0.0 Net-209.188.0.0
name 66.85.128.0 Net-66.85.128.0
name 69.194.224.0 Net-69.194.224.0
name 69.194.226.0 Net-69.194.226.0
name 172.16.102.84 Operations-PC description EDI Operations PC
name 172.16.102.119 PC_ML-TTOM-W7-WS description T Thompson Maint PC No Internet
name 172.16.1.62 Inside-172.16.1.62-MLOSM description NetOps OSM
name 192.168.1.0 Network-LAX
name 172.16.1.26 SyteL1-172.16.1.26
name 112.160.0.0 Korean-Spam-IPs
name 3.0.0.0 US-Block-1
name 109.0.0.0 Non-Us1
name 118.0.0.0 Non-Us10
name 119.0.0.0 Non-Us11
name 120.0.0.0 Non-Us12
name 121.0.0.0 Non-Us13
name 122.0.0.0 Non-Us14
name 123.0.0.0 Non-Us15
name 124.0.0.0 Non-Us16
name 125.0.0.0 Non-Us17
name 126.0.0.0 Non-Us18
name 110.0.0.0 Non-Us2
name 111.0.0.0 Non-Us3
name 112.0.0.0 Non-Us4
name 113.0.0.0 Non-Us5
name 114.0.0.0 Non-Us6
name 115.0.0.0 Non-Us7
name 116.0.0.0 Non-Us8
name 117.0.0.0 Non-Us9
name 133.0.0.0 Non-Us19
name 186.0.0.0 Non-Us20
name 187.0.0.0 Non-Us21
name 188.0.0.0 Non-Us22
name 189.0.0.0 Non-Us23
name 190.0.0.0 Non-Us24
name 191.0.0.0 Non-Us25
name 176.125.0.0 Non-Us26
name 195.0.0.0 Non-Us27
name 177.0.0.0 Non-Us28
name 178.0.0.0 Non-Us29
name 180.0.0.0 Non-Us30
name 182.0.0.0 Non-Us31
name 183.0.0.0 Non-Us32
name 31.0.0.0 Non-Us33
name 5.0.0.0 Non-Us34
name 92.0.0.0 Non-Us35
name 90.0.0.0 Non-Us36
name 94.0.0.0 Non-Us37
name 95.0.0.0 Non-Us38
name 102.0.0.0 Non-Us39
name 103.0.0.0 Non-Us40
name 104.0.0.0 Non-Us41
name 105.0.0.0 Non-Us42
name 106.0.0.0 Non-Us43
name 93.0.0.0 Non-Us44
name 88.0.0.0 Non-Us45
name 89.0.0.0 Non-Us46
name 222.0.0.0 Non-Us47
name 172.16.102.40 ML-VM-Test-W7-1 description Test VM for PRTG server
name 172.17.22.0 Net-Guest description Network for Guest WiFi
name 172.17.20.0 Net-RedZone description Network for RedZone Training Center
name 172.17.21.0 Net-WiFi description Network for Employee WiFi
name 198.30.101.78 OUTSIDE_198.30.101.78 description Service Ticket #176820 - New External Access to Server PCM - for Web and SSL & New FQDN TBD
name 172.16.10.31 Server-PCM2 description Service Ticket #176820 - New External Access to Server PCM - for Web and SSL & New FQDN TBD
ip local pool 172.18.0.1 172.18.0.2-172.18.0.253 mask 255.255.255.0
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
switchport access vlan 3
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan1
description Ether 0/1 Uplink to ML-SW-DataCenter-1 Port 48
mac-address 0003.e300.67c5
nameif inside
security-level 100
ip address 172.16.0.1 255.255.0.0
!
interface Vlan2
mac-address 0003.e300.67c4
nameif outside
security-level 0
ip address 198.30.101.70 255.255.255.240
!
interface Vlan3
description Ether 0/2 Uplink to ML-SW-DataCenter-1 Port 47
no forward interface Vlan1
nameif GuestWireless
security-level 50
ip address 172.17.22.1 255.255.255.0
!
boot system disk0:/asa923-k8.bin
ftp mode passive
clock timezone EST -5
clock summer-time EDT recurring
dns domain-lookup inside
dns domain-lookup outside
dns domain-lookup GuestWireless
dns server-group DefaultDNS
domain-name mar.com
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network Server-EDIPartner1
host 12.28.215.206
description Created during name migration
object network Server-EDIPartner2
host 209.95.232.130
description Created during name migration
object network Server-EDIPartner3
host 65.196.53.194
description Created during name migration
object network Net-108.170.0.0
subnet 108.170.0.0 255.255.192.0
description Created during name migration
object network Net-162.213.252.0
subnet 162.213.252.0 255.255.255.0
description Created during name migration
object network Net-162.213.254.0
subnet 162.213.254.0 255.255.254.0
description Created during name migration
object network Net-174.138.160.0
subnet 174.138.160.0 255.255.240.0
description Created during name migration
object network Net-184.164.128.0
subnet 184.164.128.0 255.255.224.0
description Created during name migration
object network Net-184.171.160.0
subnet 184.171.160.0 255.255.240.0
description Created during name migration
object network Net-184.95.32.0
subnet 184.95.32.0 255.255.224.0
description Created during name migration
object network Net-192.198.192.0
subnet 192.198.192.0 255.255.248.0
description Created during name migration
object network Net-192.198.200.0
subnet 192.198.200.0 255.255.252.0
description Created during name migration
object network Net-198.15.64.0
subnet 198.15.64.0 255.255.192.0
description Created during name migration
object network Net-198.24.128.0
subnet 198.24.128.0 255.255.224.0
description Created during name migration
object network Net-199.48.165.0
subnet 199.48.165.0 255.255.255.0
description Created during name migration
object network Net-209.188.0.0
subnet 209.188.0.0 255.255.224.0
description Created during name migration
object network Net-66.85.128.0
subnet 66.85.128.0 255.255.192.0
description Created during name migration
object network Net-69.194.224.0
subnet 69.194.224.0 255.255.255.0
description Created during name migration
object network Net-69.194.226.0
subnet 69.194.226.0 255.255.255.0
description Created during name migration
object network Net-173.246.96.0
subnet 173.246.96.0 255.255.240.0
description Created during name migration
object network Net-185.26.124.0
subnet 185.26.124.0 255.255.252.0
description Created during name migration
object network Net-217.70.176.0
subnet 217.70.176.0 255.255.240.0
description Created during name migration
object network Net-46.226.104.0
subnet 46.226.104.0 255.255.248.0
description Created during name migration
object network Net-92.243.0.0
subnet 92.243.0.0 255.255.224.0
description Created during name migration
object network Net-95.142.160.0
subnet 95.142.160.0 255.255.240.0
description Created during name migration
object network OUTSIDE_50.194.86.245
host 50.194.86.245
description Created during name migration
object network Non-Us1
subnet 109.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us2
subnet 110.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us3
subnet 111.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us4
subnet 112.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us5
subnet 113.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us6
subnet 114.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us7
subnet 115.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us8
subnet 116.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us9
subnet 117.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us10
subnet 118.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us11
subnet 119.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us12
subnet 120.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us13
subnet 121.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us14
subnet 122.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us15
subnet 123.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us16
subnet 124.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us17
subnet 125.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us18
subnet 126.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us39
subnet 102.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us40
subnet 103.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us41
subnet 104.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us42
subnet 105.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us43
subnet 106.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us19
subnet 133.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us26
subnet 176.125.0.0 255.255.0.0
description Created during name migration
object network Non-Us28
subnet 177.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us29
subnet 178.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us30
subnet 180.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us31
subnet 182.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us32
subnet 183.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us20
subnet 186.0.0.0 255.255.255.0
description Created during name migration
object network Non-Us21
subnet 187.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us22
subnet 188.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us23
subnet 189.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us24
subnet 190.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us25
subnet 191.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us27
subnet 195.0.0.0 255.128.0.0
description Created during name migration
object network Non-Us33
subnet 31.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us34
subnet 5.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us36
subnet 90.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us35
subnet 92.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us37
subnet 94.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us38
subnet 95.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us47
subnet 222.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us45
subnet 88.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us46
subnet 89.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us44
subnet 93.0.0.0 255.0.0.0
description Created during name migration
object network US-Block-1
subnet 3.0.0.0 255.0.0.0
description Created during name migration
object network Server-IceWarp
host 172.16.1.8
description Created during name migration
object network Server-NM1
host 172.16.1.130
description Old name = ML-VM-Test-W7-1
object network obj-172.16.0.0
subnet 172.16.0.0 255.255.0.0
object network Network-TX
subnet 192.168.0.0 255.255.255.0
object network Network-LAX
subnet 192.168.1.0 255.255.255.0
object network Server-Appsvr1
host 172.16.1.30
object network OUTSIDE_198.30.101.73
host 198.30.101.73
object network DEV-GANSAW
host 172.16.250.101
object network Doucet-Grid-Saw
host 172.16.250.102
object network SL1-172.16.1.26
host 172.16.1.26
object network Server-PCM2
host 172.16.10.31
object network OUTSIDE_198.30.101.78
host 198.30.101.78
object network Server-PCM2-01
host 172.16.10.31
object network OUTSIDE_198.30.101.66
host 198.30.101.66
object network Server-Briefcase1
host 172.16.1.5
object network OUTSIDE_198.30.101.67
host 198.30.101.67
object network Server-Remote1
host 172.16.1.35
object network OUTSIDE_198.30.101.68
host 198.30.101.68
object network Server-EDI1
host 172.16.1.38
object network OUTSIDE_198.30.101.72
host 198.30.101.72
object network Server-TS1
host 172.16.1.44
object network OUTSIDE_198.30.101.74
host 198.30.101.74
object network obj_any
subnet 0.0.0.0 0.0.0.0
object network obj-172.17.0.0
subnet 172.17.0.0 255.255.0.0
object network Operations-PC
host 172.16.102.84
description Created during name migration
object network PC_ML-TTOM-W7-WS
host 172.16.102.119
description Created during name migration
object network NETWORK_OBJ_172.18.0.0_24
subnet 172.18.0.0 255.255.255.0
object network PRT-IP-172.16.1.85
host 172.16.1.85
description Printer
object network PRT-IP-172.16.1.87
host 172.16.1.87
description Printer
object network PRT-IP-172.16.1.88
host 172.16.1.88
description Printer
object network PRT-IP-172.16.1.90
host 172.16.1.90
description Printer
object network PRT-IP-172.16.1.93
host 172.16.1.93
description Printer
object network PRT-IP-172.16.11.17
host 172.16.11.17
description Printer
object network PRT-IP-172.16.11.19
host 172.16.11.19
description Printer
object network Server-VideoConf
host 172.16.0.210
object network OUTSIDE_198.30.101.71
host 198.30.101.71
object network Net-97.0.0.0
subnet 97.0.0.0 255.0.0.0
description N - Darry Home Office Public Range
object network OUTSIDE_173.9.221.41
host 173.9.221.41
description N Secondary WAN
object network OUTSIDE_40.141.230.226
host 40.141.230.226
description N Primary WAN
object network OUTSIDE_40.141.230.227
host 40.141.230.227
description N Polycom
object network Range-vzt_Public_IPs
range 200.76.17.14 200.76.17.18
description Range of vzt Public IPs
object network Net-76.0.0.0
subnet 76.0.0.0 255.0.0.0
object network Net-73.221.0.0
subnet 73.221.0.0 255.255.0.0
object network NET-vzt-172.28.0.0
subnet 172.28.0.0 255.255.0.0
object network NET-vzt-172.29.0.0
subnet 172.29.0.0 255.255.0.0
object network Dover-Gateway
host 172.16.3.60
object network Net-73.225.0.0
subnet 73.225.0.0 255.255.0.0
object network obj-172.16.101.0
subnet 172.16.101.0 255.255.255.0
object network obj-172.17.21.0
subnet 172.17.21.0 255.255.255.0
object network obj-172.17.20.0
subnet 172.17.20.0 255.255.255.0
object network Net-AP_Mgmt
subnet 172.17.19.0 255.255.255.0
description AP Management
object network Net-Guest-Wireless
subnet 172.17.22.0 255.255.255.0
description Guest Wireless
object network Printer-Line
host 172.16.102.141
description Block access to Internet
object network NAS-2
host 172.16.10.38
object network TestVPNmar
host 172.16.1.22
object network Jira_N
host 192.17.10.72
object network Santillan
host 192.17.10.230
object network NETWORK_OBJ_172.16.0.0_16
subnet 172.16.0.0 255.255.0.0
object network DC1_mar
host 172.16.1.22
object network DC2_mar
host 172.16.1.77
object network TS01_N
host 192.17.10.127
object network Flori
host 192.17.12.92
object network NDC01
host 192.17.10.194
object network NPDC
host 192.17.10.102
object network N_Confluence
host 192.17.10.71
object network N_Nagios
host 192.17.10.134
object network UTL1_mar
host 172.16.10.155
object network UTL01_N
host 192.17.10.124
object network NETWORK_OBJ_192.17.0.0_16
subnet 192.17.0.0 255.255.0.0
object network TestOutside
host 173.9.221.46
object network mar17
subnet 172.17.0.0 255.255.0.0
object network marVMHost
host 192.168.20.12
description marVMHost
object network Jenkins
host 192.17.10.120
object-group service SVG-ICEWARP tcp
description ICEWARP Email Access
port-object eq 32000
port-object eq 32001
port-object eq 366
port-object eq imap4
port-object eq pop3
port-object eq smtp
port-object eq 465
port-object eq 5229
port-object eq 993
port-object eq 995
port-object eq www
port-object eq https
port-object eq ldaps
object-group service SVG-BRIEFCASE tcp
port-object eq ftp
port-object eq ftp-data
port-object eq www
object-group network DM_INLINE_NETWORK_2
network-object object Server-EDIPartner1
network-object object Server-EDIPartner2
network-object object Server-EDIPartner3
object-group service SRV-GANGSAW tcp
port-object eq 9600
object-group service SRV-Doucet-Grid-Saw tcp
description HD Ticket 71868 External Access on port 9602 for Doucet Grid Saw
port-object eq 9602
object-group network BGPAS20454-HIGHHO
description www.bc.net
network-object object Net-108.170.0.0
network-object object Net-162.213.252.0
network-object object Net-162.213.254.0
network-object object Net-174.138.160.0
network-object object Net-184.164.128.0
network-object object Net-184.171.160.0
network-object object Net-184.95.32.0
network-object object Net-192.198.192.0
network-object object Net-192.198.200.0
network-object object Net-198.15.64.0
network-object object Net-198.24.128.0
network-object object Net-199.48.165.0
network-object object Net-209.188.0.0
network-object object Net-66.85.128.0
network-object object Net-69.194.224.0
network-object object Net-69.194.226.0
object-group network BGPAS29169-GANDI
description GANDI Registrar
network-object object Net-173.246.96.0
network-object object Net-185.26.124.0
network-object object Net-217.70.176.0
network-object object Net-46.226.104.0
network-object object Net-92.243.0.0
network-object object Net-95.142.160.0
object-group network DM_INLINE_NETWORK_1
group-object BGPAS20454-HIGHHO
group-object BGPAS29169-GANDI
object-group service Web-Services
service-object tcp destination eq ftp
service-object tcp destination eq ftp-data
service-object tcp destination eq www
service-object tcp destination eq https
object-group service RDP tcp
port-object eq 3389
object-group network Blocked-IPs
network-object object OUTSIDE_50.194.86.245
network-object object Non-Us1
network-object object Non-Us2
network-object object Non-Us3
network-object object Non-Us4
network-object object Non-Us5
network-object object Non-Us6
network-object object Non-Us7
network-object object Non-Us8
network-object object Non-Us9
network-object object Non-Us10
network-object object Non-Us11
network-object object Non-Us12
network-object object Non-Us13
network-object object Non-Us14
network-object object Non-Us15
network-object object Non-Us16
network-object object Non-Us17
network-object object Non-Us18
network-object object Non-Us39
network-object object Non-Us40
network-object object Non-Us41
network-object object Non-Us42
network-object object Non-Us43
network-object object Non-Us19
network-object object Non-Us26
network-object object Non-Us28
network-object object Non-Us29
network-object object Non-Us30
network-object object Non-Us31
network-object object Non-Us32
network-object object Non-Us20
network-object object Non-Us21
network-object object Non-Us22
network-object object Non-Us23
network-object object Non-Us24
network-object object Non-Us25
network-object object Non-Us27
network-object object Non-Us33
network-object object Non-Us34
network-object object Non-Us36
network-object object Non-Us35
network-object object Non-Us37
network-object object Non-Us38
network-object object Non-Us47
network-object object Non-Us45
network-object object Non-Us46
network-object object Non-Us44
object-group network USIPAddreses
network-object object US-Block-1
object-group network DM_INLINE_NETWORK_3
network-object object Server-IceWarp
network-object object Server-NM1
object-group network mar-Printers
description All Printer IP addresses to allow SMTP outbound for scan to email.
network-object object PRT-IP-172.16.1.85
network-object object PRT-IP-172.16.1.87
network-object object PRT-IP-172.16.1.88
network-object object PRT-IP-172.16.1.90
network-object object PRT-IP-172.16.1.93
network-object object PRT-IP-172.16.11.17
network-object object PRT-IP-172.16.11.19
object-group network Polycom-Allowed-IPs
description IP addresses allowed to access the Polycom video conferencing system
network-object object Net-97.0.0.0
network-object object OUTSIDE_173.9.221.41
network-object object OUTSIDE_40.141.230.226
network-object object OUTSIDE_40.141.230.227
network-object object Range-vzt_Public_IPs
network-object object Net-76.0.0.0
network-object object Net-73.221.0.0
network-object object Net-73.225.0.0
object-group service Polycom-TCP-(3230-3241) tcp
port-object range 3230 3241
object-group service Polycom-UDP-(3230-3291) udp
port-object range 3230 3291
object-group service DM_INLINE_TCP_1 tcp
group-object Polycom-TCP-(3230-3241)
port-object eq h323
object-group network vzt-Networks
network-object object NET-vzt-172.28.0.0
network-object object NET-vzt-172.29.0.0
object-group network DM_INLINE_NETWORK_4
network-object 172.16.0.0 255.255.0.0
group-object vzt-Networks
object-group network DM_INLINE_NETWORK_5
network-object 172.16.0.0 255.255.0.0
group-object vzt-Networks
object-group network DM_INLINE_NETWORK_6
network-object 172.16.0.0 255.255.0.0
group-object vzt-Networks
object-group network DM_INLINE_NETWORK_7
network-object 172.16.0.0 255.255.0.0
group-object vzt-Networks
object-group protocol TCPUDP
protocol-object udp
protocol-object tcp
object-group service DM_INLINE_SERVICE_1
service-object ip
service-object tcp-udp destination eq 3389
object-group network DM_INLINE_NETWORK_8
network-object 172.16.0.0 255.255.0.0
network-object 172.16.102.0 255.255.255.0
object-group network DM_INLINE_NETWORK_9
network-object 172.16.0.0 255.255.0.0
network-object 172.16.102.0 255.255.255.0
object-group service DM_INLINE_SERVICE_4
service-object ip
service-object tcp-udp destination eq 3389
object-group network DM_INLINE_NETWORK_10
network-object Net-RedZone 255.255.255.0
network-object Net-WiFi 255.255.255.0
object-group network DM_INLINE_NETWORK_12
network-object Net-RedZone 255.255.255.0
network-object Net-WiFi 255.255.255.0
object-group service DM_INLINE_SERVICE_2
service-object ip
service-object tcp-udp destination eq 3389
object-group service DM_INLINE_SERVICE_3
service-object ip
service-object tcp-udp destination eq 3389
object-group service DM_INLINE_SERVICE_5
service-object ip
service-object tcp-udp destination eq 5080
object-group network DM_INLINE_NETWORK_11
network-object host 172.16.0.1
network-object object obj-172.16.0.0
network-object 172.17.0.0 255.255.0.0
network-object object marVMHost
network-object Net-RedZone 255.255.255.0
network-object Net-WiFi 255.255.255.0
object-group network DM_INLINE_NETWORK_13
network-object host 192.17.10.134
network-object object Jenkins
object-group network DM_INLINE_NETWORK_14
network-object 172.16.0.0 255.255.0.0
network-object 172.17.0.0 255.255.0.0
network-object object obj-172.16.101.0
network-object object marVMHost
network-object 172.17.19.0 255.255.255.0
network-object Net-RedZone 255.255.255.0
network-object Net-WiFi 255.255.255.0
object-group network DM_INLINE_NETWORK_15
network-object 172.16.0.0 255.255.0.0
network-object 172.17.0.0 255.255.0.0
object-group network DM_INLINE_NETWORK_16
network-object object obj-172.16.0.0
network-object object obj-172.16.101.0
network-object object marVMHost
network-object object mar17
object-group network marNet17
network-object Net-RedZone 255.255.255.0
network-object Net-WiFi 255.255.255.0
network-object object mar17
network-object object Net-AP_Mgmt
access-list Split-Tunnel-ACL standard permit 172.16.0.0 255.255.0.0
access-list Split-Tunnel-ACL standard permit 192.17.0.0 255.255.0.0
access-list Split-Tunnel-ACL standard permit 172.28.0.0 255.255.0.0
access-list Split-Tunnel-ACL standard permit 172.29.0.0 255.255.0.0
access-list Split-Tunnel-ACL standard permit 172.17.20.0 255.255.255.0
access-list Split-Tunnel-ACL standard permit 172.17.21.0 255.255.255.0
access-list Split-Tunnel-ACL standard permit 192.168.0.0 255.255.255.0
access-list Split-Tunnel-ACL standard permit 172.17.19.0 255.255.255.0
access-list inside_nat0_outbound extended permit object-group DM_INLINE_SERVICE_4 object-group DM_INLINE_NETWORK_6 object Network-TX
access-list inside_nat0_outbound extended permit object-group DM_INLINE_SERVICE_1 object-group DM_INLINE_NETWORK_7 object Network-LAX
access-list outside_2_cryptomap extended permit ip object-group DM_INLINE_NETWORK_4 object Network-LAX
access-list outside_1_cryptomap extended permit ip object-group DM_INLINE_NETWORK_5 object Network-TX
access-list inside_access_in remark Deny Access to ASNs hosting CryptoBlocker.
access-list inside_access_in extended deny ip any4 object-group DM_INLINE_NETWORK_1
access-list inside_access_in remark Allow Outbound Email for ICE WARP, Per Schuster Request 4/23/13 added by NetOps (dpetika)
access-list inside_access_in extended permit tcp object-group DM_INLINE_NETWORK_3 any4 eq smtp
access-list inside_access_in remark Remote Desktop
access-list inside_access_in extended permit object-group TCPUDP any any eq 3389
access-list inside_access_in extended permit object-group DM_INLINE_SERVICE_2 object-group DM_INLINE_NETWORK_9 object-group DM_INLINE_NETWORK_12
access-list inside_access_in extended permit object-group DM_INLINE_SERVICE_3 object-group DM_INLINE_NETWORK_10 object-group DM_INLINE_NETWORK_8
access-list inside_access_in remark Required for EDI - NetOps Ticket# 93603
access-list inside_access_in extended permit tcp object Operations-PC any4 eq smtp
access-list inside_access_in extended permit tcp object-group mar-Printers any eq smtp
access-list inside_access_in remark Deny SMTP outbound except for Email Server, Per Schuster Request 4/23/13 added by NetOps (dpetika)
access-list inside_access_in extended deny tcp any4 any4 eq smtp inactive
access-list inside_access_in extended deny ip object PC_ML-TTOM-W7-WS any4 inactive
access-list inside_access_in extended deny ip 172.17.22.0 255.255.255.0 172.16.0.0 255.255.0.0
access-list inside_access_in extended permit ip object Printer-Line object NAS-2
access-list inside_access_in extended deny ip object Printer-Line any
access-list inside_access_in remark Implicit Rule
access-list inside_access_in extended permit ip any4 any4
access-list outside_access_in extended permit icmp any any unreachable
access-list outside_access_in extended permit tcp object-group Polycom-Allowed-IPs host 172.16.0.210 object-group DM_INLINE_TCP_1
access-list outside_access_in extended permit udp object-group Polycom-Allowed-IPs host 172.16.0.210 object-group Polycom-UDP-(3230-3291)
access-list outside_access_in extended deny ip any4 object PC_ML-TTOM-W7-WS inactive
access-list outside_access_in remark Remote ICEWARP Access
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq www inactive
access-list outside_access_in remark RDP Access from Outside
access-list outside_access_in extended permit tcp any4 object Server-Remote1 eq 3389 inactive
access-list outside_access_in remark External Access for EDI Partners Port 5080
access-list outside_access_in extended permit object-group DM_INLINE_SERVICE_5 object-group DM_INLINE_NETWORK_2 object Server-EDI1
access-list outside_access_in remark Deny RDP Access From INTERNET
access-list outside_access_in extended deny object-group TCPUDP any object Server-EDI1 eq 3389
access-list outside_access_in remark Allow Remote RDP Access
access-list outside_access_in extended permit tcp any4 object Server-TS1 eq 3389 inactive
access-list outside_access_in extended deny ip object-group Blocked-IPs object Server-IceWarp inactive
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq smtp inactive
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq 32000 inactive
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq 32001 inactive
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq 366 inactive
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq 465 inactive
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq 5229 inactive
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq 993 inactive
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq 995 inactive
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq https inactive
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq imap4 inactive
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq ldaps inactive
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq pop3 inactive
access-list outside_access_in extended permit tcp any4 object Server-Briefcase1 eq ftp inactive
access-list outside_access_in extended permit tcp any4 object Server-Briefcase1 eq www inactive
access-list outside_access_in extended permit tcp any4 object Server-Briefcase1 eq ftp-data inactive
access-list outside_access_in extended permit udp any4 object Server-Appsvr1 eq ntp inactive
access-list outside_access_in remark Migration, ACE (line 30) expanded: permit tcp any4 host OUTSIDE_198.30.101.73
access-list outside_access_in extended permit tcp any4 object DEV-GANSAW eq 9600 inactive
access-list outside_access_in remark Migration: End of expansion
access-list outside_access_in remark Ticket 71868 External Access on port 9602 for Doucet Grid Saw
access-list outside_access_in remark Migration, ACE (line 32) expanded: permit tcp any4 host OUTSIDE_198.30.101.73
access-list outside_access_in extended permit tcp any4 object Doucet-Grid-Saw eq 9602 inactive
access-list outside_access_in remark Migration: End of expansion
access-list outside_access_in remark Ticket 99868
access-list outside_access_in remark Migration, ACE (line 28) expanded: permit tcp any4 host OUTSIDE_198.30.101.73 object-group RDP
access-list outside_access_in remark Migration: End of expansion
access-list outside_access_in extended permit tcp any4 object Server-PCM2 eq https
access-list outside_access_in extended permit tcp any4 object Server-PCM2 eq www inactive
access-list outside_access_in remark RDP
access-list outside_access_in extended permit object-group TCPUDP any any eq 3389
access-list ACL-SNMP remark Used to allow access from SNMP server for Nagios checks
access-list ACL-SNMP extended permit ip object-group DM_INLINE_NETWORK_13 object-group DM_INLINE_NETWORK_11
access-list outside_cryptomap extended permit ip object-group DM_INLINE_NETWORK_14 192.17.0.0 255.255.0.0
access-list outside_cryptomap extended permit ip object-group DM_INLINE_NETWORK_16 192.17.0.0 255.255.0.0
access-list net.to.N extended permit ip any 192.17.0.0 255.255.0.0
access-list net.to.N extended permit ip 192.17.0.0 255.255.0.0 any
pager lines 24
logging enable
logging asdm-buffer-size 512
logging monitor debugging
logging buffered debugging
logging asdm informational
flow-export destination inside 172.16.1.130 5022
flow-export template timeout-rate 1
mtu inside 1500
mtu outside 1500
mtu GuestWireless 1500
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-743.bin
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
nat (inside,outside) source static obj-172.17.20.0 obj-172.17.20.0 destination static obj-172.16.101.0 obj-172.16.101.0 no-proxy-arp route-lookup
nat (inside,outside) source static obj-172.17.21.0 obj-172.17.21.0 destination static obj-172.16.101.0 obj-172.16.101.0 no-proxy-arp route-lookup
nat (inside,outside) source static NET-vzt-172.28.0.0 NET-vzt-172.28.0.0 destination static obj-172.16.101.0 obj-172.16.101.0 no-proxy-arp route-lookup
nat (inside,outside) source static NET-vzt-172.29.0.0 NET-vzt-172.29.0.0 destination static obj-172.16.101.0 obj-172.16.101.0 no-proxy-arp route-lookup
nat (inside,outside) source static obj-172.16.0.0 obj-172.16.0.0 destination static obj-172.16.101.0 obj-172.16.101.0 no-proxy-arp route-lookup
nat (any,outside) source static DM_INLINE_NETWORK_4 DM_INLINE_NETWORK_4 destination static Network-LAX Network-LAX no-proxy-arp route-lookup
nat (inside,any) source static obj-172.16.0.0 obj-172.16.0.0 destination static Network-TX Network-TX no-proxy-arp route-lookup
nat (inside,any) source static obj-172.16.0.0 obj-172.16.0.0 destination static Network-LAX Network-LAX no-proxy-arp route-lookup
nat (inside,outside) source static any any destination static NETWORK_OBJ_172.18.0.0_24 NETWORK_OBJ_172.18.0.0_24 no-proxy-arp route-lookup
nat (inside,outside) source static Server-VideoConf OUTSIDE_198.30.101.71
nat (inside,outside) source static DM_INLINE_NETWORK_15 DM_INLINE_NETWORK_15 destination static NETWORK_OBJ_192.17.0.0_16 NETWORK_OBJ_192.17.0.0_16 no-proxy-arp route-lookup
nat (inside,outside) source static DM_INLINE_NETWORK_16 DM_INLINE_NETWORK_16 destination static NETWORK_OBJ_192.17.0.0_16 NETWORK_OBJ_192.17.0.0_16 no-proxy-arp route-lookup
!
object network Server-PCM2
nat (inside,outside) static OUTSIDE_198.30.101.78 service tcp https https
object network Server-PCM2-01
nat (inside,outside) static OUTSIDE_198.30.101.78 service tcp www www
object network Server-EDI1
nat (inside,outside) static OUTSIDE_198.30.101.72
object network obj_any
nat (inside,outside) dynamic interface
object network Net-Guest-Wireless
nat (GuestWireless,outside) dynamic interface
access-group inside_access_in in interface inside
access-group outside_access_in in interface outside
route outside 0.0.0.0 0.0.0.0 198.30.101.65 1
route inside 172.17.19.0 255.255.255.0 172.16.3.60 1
route inside Net-RedZone 255.255.254.0 172.16.3.60 1
route inside Net-Guest 255.255.255.0 172.16.3.60 1
route inside 172.28.0.0 255.255.0.0 172.16.3.60 1
route inside 172.29.0.0 255.255.0.0 172.16.3.60 1
route inside 192.168.20.0 255.255.255.0 172.16.3.60 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
webvpn
svc ask none default svc
aaa-server mar-LDAP protocol ldap
aaa-server mar-LDAP (inside) host 172.16.1.22
ldap-base-dn DC=mar2k,DC=com
ldap-group-base-dn CN=VPN-Users,OU=ML Groups,DC=mar2k,DC=com
ldap-scope subtree
ldap-naming-attribute sAMAccountName
ldap-login-password *****
ldap-login-dn CN=asa admin,CN=Users,DC=mar2k,DC=com
server-type microsoft
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
aaa authentication enable console LOCAL
http server enable 8443
http server idle-timeout 60
http 0.0.0.0 0.0.0.0 inside
http 69.54.56.242 255.255.255.255 outside
http 63.157.106.146 255.255.255.255 outside
http 63.110.89.234 255.255.255.255 outside
http 74.3.106.174 255.255.255.255 outside
http Network-TX 255.255.255.0 inside
http Network-LAX 255.255.255.0 inside
http redirect outside 80
snmp-server host inside 192.17.10.134 community ***** version 2c
snmp-server location mar HQ, Dover OH
snmp-server contact IT HelpDesk (tickets@mar.com)
snmp-server community *****
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS mode transport
crypto ipsec ikev2 ipsec-proposal DES
protocol esp encryption des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal 3DES
protocol esp encryption 3des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto ipsec security-association pmtu-aging infinite
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
crypto map outside_map 1 match address outside_1_cryptomap
crypto map outside_map 1 set peer 74.3.106.174
crypto map outside_map 1 set ikev1 transform-set ESP-3DES-SHA
crypto map outside_map 2 match address outside_2_cryptomap
crypto map outside_map 2 set peer 63.110.89.234
crypto map outside_map 2 set ikev1 transform-set ESP-3DES-SHA
crypto map outside_map 2 set ikev2 ipsec-proposal DES 3DES AES AES192 AES256
crypto map outside_map 3 match address outside_cryptomap
crypto map outside_map 3 set peer 40.141.230.226
crypto map outside_map 3 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 3 set ikev2 ipsec-proposal DES 3DES AES AES192 AES256
crypto map outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map outside_map interface outside
crypto ca trustpoint ASDM_TrustPoint0
enrollment terminal
fqdn vpn.mar.com
subject-name CN=vpn.mar.com,OU=IT,O=mar Inc,St=Ohio,L=Dover
keypair vpn.mar.com
crl configure
crypto ca trustpoint GoDaddy
enrollment terminal
crl configure
crypto ca trustpoint _SmartCallHome_ServerCA
no validation-usage
crl configure
crypto ca trustpoint ASDM_TrustPoint1
enrollment terminal
crl configure
crypto ca trustpoint ASDM_TrustPoint2
enrollment terminal
subject-name CN=vpn.mar.com,OU=IT,O=mar Inc,C=US,St=Ohio,L=Dover
keypair vpn.mar.com
crl configure
crypto ca trustpoint ASDM_TrustPoint3
enrollment terminal
fqdn none
subject-name CN=vpn.mar.com,OU=Domain Control Validated
keypair vpn.mar.com
crl configure
crypto ca trustpoint ASDM_TrustPoint4
keypair ASDM_TrustPoint4
no validation-usage
crl configure
crypto ca trustpool policy
crypto ca certificate chain _SmartCallHome_ServerCA
certificate ca 6ecc7aa5a7032009b8cebcf4e952d491
308205ec 308204d4 a0030201 0202106e cc7aa5a7 032009b8 cebcf4e9 52d49130
0d06092a 864886f7 0d010105 05003081 ca310b30 09060355 04061302 55533117
30150603 55040a13 0e566572 69536967 6e2c2049 6e632e31 1f301d06 0355040b
13165665 72695369 676e2054 72757374 204e6574 776f726b 313a3038 06035504
0b133128 63292032 30303620 56657269 5369676e 2c20496e 632e202d 20466f72
20617574 686f7269 7a656420 75736520 6f6e6c79 31453043 06035504 03133c56
65726953 69676e20 436c6173 73203320 5075626c 69632050 72696d61 72792043
65727469 66696361 74696f6e 20417574 686f7269 7479202d 20473530 1e170d31
30303230 38303030 3030305a 170d3230 30323037 32333539 35395a30 81b5310b
30090603 55040613 02555331 17301506 0355040a 130e5665 72695369 676e2c20
496e632e 311f301d 06035504 0b131656 65726953 69676e20 54727573 74204e65
74776f72 6b313b30 39060355 040b1332 5465726d 73206f66 20757365 20617420
68747470 733a2f2f 7777772e 76657269 7369676e 2e636f6d 2f727061 20286329
3130312f 302d0603 55040313 26566572 69536967 6e20436c 61737320 33205365
63757265 20536572 76657220 4341202d 20473330 82012230 0d06092a 864886f7
0d010101 05000382 010f0030 82010a02 82010100 b187841f c20c45f5 bcab2597
a7ada23e 9cbaf6c1 39b88bca c2ac56c6 e5bb658e 444f4dce 6fed094a d4af4e10
9c688b2e 957b899b 13cae234 34c1f35b f3497b62 83488174 d188786c 0253f9bc
7f432657 5833833b 330a17b0 d04e9124 ad867d64 12dc744a 34a11d0a ea961d0b
15fca34b 3bce6388 d0f82d0c 948610ca b69a3dca eb379c00 48358629 5078e845
63cd1941 4ff595ec 7b98d4c4 71b350be 28b38fa0 b9539cf5 ca2c23a9 fd1406e8
18b49ae8 3c6e81fd e4cd3536 b351d369 ec12ba56 6e6f9b57 c58b14e7 0ec79ced
4a546ac9 4dc5bf11 b1ae1c67 81cb4455 33997f24 9b3f5345 7f861af3 3cfa6d7f
81f5b84a d3f58537 1cb5a6d0 09e4187b 384efa0f 02030100 01a38201 df308201
db303406 082b0601 05050701 01042830 26302406 082b0601 05050730 01861868
7474703a 2f2f6f63 73702e76 65726973 69676e2e 636f6d30 12060355 1d130101
ff040830 060101ff 02010030 70060355 1d200469 30673065 060b6086 480186f8
45010717 03305630 2806082b 06010505 07020116 1c687474 70733a2f 2f777777
2e766572 69736967 6e2e636f 6d2f6370 73302a06 082b0601 05050702 02301e1a
1c687474 70733a2f 2f777777 2e766572 69736967 6e2e636f 6d2f7270 61303406
03551d1f 042d302b 3029a027 a0258623 68747470 3a2f2f63 726c2e76 65726973
69676e2e 636f6d2f 70636133 2d67352e 63726c30 0e060355 1d0f0101 ff040403
02010630 6d06082b 06010505 07010c04 61305fa1 5da05b30 59305730 55160969
6d616765 2f676966 3021301f 30070605 2b0e0302 1a04148f e5d31a86 ac8d8e6b
c3cf806a d448182c 7b192e30 25162368 7474703a 2f2f6c6f 676f2e76 65726973
69676e2e 636f6d2f 76736c6f 676f2e67 69663028 0603551d 11042130 1fa41d30
1b311930 17060355 04031310 56657269 5369676e 4d504b49 2d322d36 301d0603
551d0e04 1604140d 445c1653 44c1827e 1d20ab25 f40163d8 be79a530 1f060355
1d230418 30168014 7fd365a7 c2ddecbb f03009f3 4339fa02 af333133 300d0609
2a864886 f70d0101 05050003 82010100 0c8324ef ddc30cd9 589cfe36 b6eb8a80
4bd1a3f7 9df3cc53 ef829ea3 a1e697c1 589d756c e01d1b4c fad1c12d 05c0ea6e
b2227055 d9203340 3307c265 83fa8f43 379bea0e 9a6c70ee f69c803b d937f47a
6decd018 7d494aca 99c71928 a2bed877 24f78526 866d8705 404167d1 273aeddc
481d22cd 0b0b8bbc f4b17bfd b499a8e9 762ae11a 2d876e74 d388dd1e 22c6df16
b62b8214 0a945cf2 50ecafce ff62370d ad65d306 4153ed02 14c8b558 28a1ace0
5becb37f 954afb03 c8ad26db e6667812 4ad99f42 fbe198e6 42839b8f 8f6724e8
6119b5dd cdb50b26 058ec36e c4c875b8 46cfe218 065ea9ae a8819a47 16de0c28
6c2527b9 deb78458 c61f381e a4c4cb66
quit
crypto ca certificate chain ASDM_TrustPoint1
certificate ca 07
308204d0 308203b8 a0030201 02020107 300d0609 2a864886 f70d0101 0b050030
8183310b 30090603 55040613 02555331 10300e06 03550408 13074172 697a6f6e
61311330 11060355 0407130a 53636f74 74736461 6c65311a 30180603 55040a13
11476f44 61646479 2e636f6d 2c20496e 632e3131 302f0603 55040313 28476f20
44616464 7920526f 6f742043 65727469 66696361 74652041 7574686f 72697479
202d2047 32301e17 0d313130 35303330 37303030 305a170d 33313035 30333037
30303030 5a3081b4 310b3009 06035504 06130255 53311030 0e060355 04081307
4172697a 6f6e6131 13301106 03550407 130a5363 6f747473 64616c65 311a3018
06035504 0a131147 6f446164 64792e63 6f6d2c20 496e632e 312d302b 06035504
0b132468 7474703a 2f2f6365 7274732e 676f6461 6464792e 636f6d2f 7265706f
7369746f 72792f31 33303106 03550403 132a476f 20446164 64792053 65637572
65204365 72746966 69636174 65204175 74686f72 69747920 2d204732 30820122
300d0609 2a864886 f70d0101 01050003 82010f00 3082010a 02820101 00b9e0cb
10d4af76 bdd49362 eb3064b8 81086cc3 04d96217 8e2fff3e 65cf8fce 62e63c52
1cda1645 4b55ab78 6b638362 90ce0f69 6c99c81a 148b4ccc 4533ea88 dc9ea3af
2bfe8061 9d7957c4 cf2ef43f 303c5d47 fc9a16bc c3379641 518e114b 54f828be
d08cbef0 30381ef3 b026f866 47636dde 7126478f 384753d1 461db4e3 dc00ea45
acbdbc71 d9aa6f00 dbdbcd30 3a794f5f 4c47f81d ef5bc2c4 9d603bb1 b24391d8
a4334eea b3d6274f ad258aa5 c6f4d5d0 a6ae7405 645788b5 4455d42d 2a3a3ef8
b8bde932 0a029464 c4163a50 f14aaee7 7933af0c 20077fe8 df0439c2 69026c63
52fa77c1 1bc87487 c8b99318 5054354b 694ebc3b d3492e1f dcc1d252 fb020301
0001a382 011a3082 0116300f 0603551d 130101ff 04053003 0101ff30 0e060355
1d0f0101 ff040403 02010630 1d060355 1d0e0416 041440c2 bd278ecc 348330a2
33d7fb6c b3f0b42c 80ce301f 0603551d 23041830 1680143a 9a850710 6728b6ef
f6bd0541 6e20c194 da0fde30 3406082b 06010505 07010104 28302630 2406082b
06010505 07300186 18687474 703a2f2f 6f637370 2e676f64 61646479 2e636f6d
2f303506 03551d1f 042e302c 302aa028 a0268624 68747470 3a2f2f63 726c2e67
6f646164 64792e63 6f6d2f67 64726f6f 742d6732 2e63726c 30460603 551d2004
3f303d30 3b060455 1d200030 33303106 082b0601 05050702 01162568 74747073
3a2f2f63 65727473 2e676f64 61646479 2e636f6d 2f726570 6f736974 6f72792f
300d0609 2a864886 f70d0101 0b050003 82010100 087e6c93 10c838b8 96a9904b
ffa15f4f 04ef6c3e 9c8806c9 508fa673 f757311b bebce42f dbf8bad3 5be0b4e7
e679620e 0ca2d76a 637331b5 f5a848a4 3b082da2 5d90d7b4 7c254f11 5630c4b6
449d7b2c 9de55ee6 ef0c61aa bfe42a1b ee849eb8 837dc143 ce44a713 700d911f
f4c813ad 8360d9d8 72a87324 1eb5ac22 0eca1789 6258441b ab892501 000fcdc4
1b62db51 b4d30f51 2a9bf4bc 73fc76ce 36a4cdd9 d82ceaae 9bf52ab2 90d14d75
188a3f8a 4190237d 5b4bfea4 03589b46 b2c36060 83f87d50 41cec2a1 90c3bbef
022fd215 54ee4415 d90aaea7 8a33edb1 2d763626 dc04eb9f f7611f15 dc876fee
469628ad a1267d0a 09a72e04 a38dbcf8 bc043001
quit
crypto ca certificate chain ASDM_TrustPoint2
certificate 6888ad29a3d8f4ae
3082052d 30820415 a0030201 02020868 88ad29a3 d8f4ae30 0d06092a 864886f7
0d01010b 05003081 b4310b30 09060355 04061302 55533110 300e0603 55040813
07417269 7a6f6e61 31133011 06035504 07130a53 636f7474 7364616c 65311a30
18060355 040a1311 476f4461 6464792e 636f6d2c 20496e63 2e312d30 2b060355
040b1324 68747470 3a2f2f63 65727473 2e676f64 61646479 2e636f6d 2f726570
6f736974 6f72792f 31333031 06035504 03132a47 6f204461 64647920 53656375
72652043 65727469 66696361 74652041 7574686f 72697479 202d2047 32301e17
0d313530 36333030 30333434 305a170d 31363036 32393138 31363430 5a303d31
21301f06 0355040b 1318446f 6d61696e 20436f6e 74726f6c 2056616c 69646174
65643118 30160603 55040313 0f76706e 2e6d6172 6c697465 2e636f6d 30820122
300d0609 2a864886 f70d0101 01050003 82010f00 3082010a 02820101 00a7e649
5c447f15 977bc02f f529f68a d3a0f751 c830b090 ed4f543b 8dd522db 4d877a23
bf979bc7 35dada74 2d1e2e5b 217cfd12 eec0b6eb b8bc010a ab44a279 e2e2eba2
ca4649fb 2aa63235 249f1246 b2a6238c 8c806be0 b9eb9b26 2de97011 da46e14b
c4695cc2 dca5abd6 fa8fe1a1 93d295c7 0032471d f536d24b 540c3fa7 554ee0a7
822c693a 1fd8c502 0461e9a8 256531ae 38fc1bc1 09fdc5fb 50e5ff46 ae84c02f
e3bf94ef f42f4a13 e0a6c96a 6339d6f1 3c985277 eb4d5098 40b0eccd f9101df4
45c67e0b 83a7e32e 00fb5242 cd2bc717 a04f0ecd d3408f3a 3b020193 0c2b14e0
62da2666 4d668188 521e00e3 9556eb2c 9d9592f0 27f03081 f02d8bae 75020301
0001a382 01b73082 01b3300c 0603551d 130101ff 04023000 301d0603 551d2504
16301406 082b0601 05050703 0106082b 06010505 07030230 0e060355 1d0f0101
ff040403 0205a030 36060355 1d1f042f 302d302b a029a027 86256874 74703a2f
2f63726c 2e676f64 61646479 2e636f6d 2f676469 67327331 2d38372e 63726c30
53060355 1d20044c 304a3048 060b6086 480186fd 6d010717 01303930 3706082b
06010505 07020116 2b687474 703a2f2f 63657274 69666963 61746573 2e676f64
61646479 2e636f6d 2f726570 6f736974 6f72792f 30760608 2b060105 05070101
046a3068 30240608 2b060105 05073001 86186874 74703a2f 2f6f6373 702e676f
64616464 792e636f 6d2f3040 06082b06 01050507 30028634 68747470 3a2f2f63
65727469 66696361 7465732e 676f6461 6464792e 636f6d2f 7265706f 7369746f
72792f67 64696732 2e637274 301f0603 551d2304 18301680 1440c2bd 278ecc34
8330a233 d7fb6cb3 f0b42c80 ce302f06 03551d11 04283026 820f7670 6e2e6d61
726c6974 652e636f 6d821377 77772e76 706e2e6d 61726c69 74652e63 6f6d301d
0603551d 0e041604 142f2c7e 73c8cb07 562982e0 47c02653 e7778dbe fd300d06
092a8648 86f70d01 010b0500 03820101 003a34da 0d96b4b1 80a62baf 611e023b
5dd22fe2 eeadc432 c7a8d010 231405c1 12fe9ad6 78c3d663 852db88f bafa8a4c
1e5d89fa 7e6eb93a 3ea8c9fa 6672d439 0f32b0a2 b934bc1f 40914482 b0951f83
faa65080 48aa15f7 871b0acf dd23a6d7 c139b7b6 295d6069 e3bf8249 6c33b089
98bd4024 6e9fca4b 55b24bfe ecdee073 ad14057e e7667fef fafb6f8a bd177ca0
8a5d5659 10a79ca3 d6fa69e5 1260be58 583de6c6 b92bc7aa eeacd0be 1be188bd
9de6f532 93eb3851 6864e963 74034133 1ef5ccad 29609d61 815a32fa 6498e98c
a5231f04 bba8763d 6a8dfe9a 823632c6 239df261 f12c0e9e fe4be11d 1768d5e1
7f311a91 f9b6d4b3 b3ef25d0 b1f8b974 65
quit
crypto ca certificate chain ASDM_TrustPoint3
certificate 00e995a76562d68bb2
30820539 30820421 a0030201 02020900 e995a765 62d68bb2 300d0609 2a864886
f70d0101 0b050030 81b4310b 30090603 55040613 02555331 10300e06 03550408
13074172 697a6f6e 61311330 11060355 0407130a 53636f74 74736461 6c65311a
30180603 55040a13 11476f44 61646479 2e636f6d 2c20496e 632e312d 302b0603
55040b13 24687474 703a2f2f 63657274 732e676f 64616464 792e636f 6d2f7265
706f7369 746f7279 2f313330 31060355 0403132a 476f2044 61646479 20536563
75726520 43657274 69666963 61746520 41757468 6f726974 79202d20 4732301e
170d3136 30353230 31383437 33395a17 0d313930 36323931 38313634 305a303d
3121301f 06035504 0b131844 6f6d6169 6e20436f 6e74726f 6c205661 6c696461
74656431 18301606 03550403 130f7670 6e2e6d61 726c6974 652e636f 6d308201
22300d06 092a8648 86f70d01 01010500 0382010f 00308201 0a028201 0100a7e6
495c447f 15977bc0 2ff529f6 8ad3a0f7 51c830b0 90ed4f54 3b8dd522 db4d877a
23bf979b c735dada 742d1e2e 5b217cfd 12eec0b6 ebb8bc01 0aab44a2 79e2e2eb
a2ca4649 fb2aa632 35249f12 46b2a623 8c8c806b e0b9eb9b 262de970 11da46e1
4bc4695c c2dca5ab d6fa8fe1 a193d295 c7003247 1df536d2 4b540c3f a7554ee0
a7822c69 3a1fd8c5 020461e9 a8256531 ae38fc1b c109fdc5 fb50e5ff 46ae84c0
2fe3bf94 eff42f4a 13e0a6c9 6a6339d6 f13c9852 77eb4d50 9840b0ec cdf9101d
f445c67e 0b83a7e3 2e00fb52 42cd2bc7 17a04f0e cdd3408f 3a3b0201 930c2b14
e062da26 664d6681 88521e00 e39556eb 2c9d9592 f027f030 81f02d8b ae750203
010001a3 8201c230 8201be30 0c060355 1d130101 ff040230 00301d06 03551d25
04163014 06082b06 01050507 03010608 2b060105 05070302 300e0603 551d0f01
01ff0404 030205a0 30370603 551d1f04 30302e30 2ca02aa0 28862668 7474703a
2f2f6372 6c2e676f 64616464 792e636f 6d2f6764 69673273 312d3234 312e6372
6c305d06 03551d20 04563054 3048060b 60864801 86fd6d01 07170130 39303706
082b0601 05050702 01162b68 7474703a 2f2f6365 72746966 69636174 65732e67
6f646164 64792e63 6f6d2f72 65706f73 69746f72 792f3008 06066781 0c010201
30760608 2b060105 05070101 046a3068 30240608 2b060105 05073001 86186874
74703a2f 2f6f6373 702e676f 64616464 792e636f 6d2f3040 06082b06 01050507
30028634 68747470 3a2f2f63 65727469 66696361 7465732e 676f6461 6464792e
636f6d2f 7265706f 7369746f 72792f67 64696732 2e637274 301f0603 551d2304
18301680 1440c2bd 278ecc34 8330a233 d7fb6cb3 f0b42c80 ce302f06 03551d11
04283026 820f7670 6e2e6d61 726c6974 652e636f 6d821377 77772e76 706e2e6d
61726c69 74652e63 6f6d301d 0603551d 0e041604 142f2c7e 73c8cb07 562982e0
47c02653 e7778dbe fd300d06 092a8648 86f70d01 010b0500 03820101 002781ab
9fc36e65 9b7e0f7f aa6e5226 99dfb367 b3e0bfac 619dc653 f747c130 62e54ec3
41ba3d16 4477f5de a1b29599 8a8556ce 7eec8bf8 d2d2bcb5 87dde7b2 be0fd308
e81f5413 228f03bc b5158436 0ad71ec1 be313afd 19106174 87e49f91 e2645a7e
9314acfa ab802e60 bb9ebeed 69d0a662 4ab8122e df3f61fc 2c28f9e9 44e03abb
8af3b1a8 52b9640b 3bd37430 2a0ca2bc b91aa822 1e0f2558 0e906477 04354890
b4d8f020 e9f8873a 4c4e7dc5 de37ad3c 1b67f24e 8510dffb eb5a369b deadeb77
85bdba2c 9423d1d8 bc1276a0 a29e6ad6 12d25065 d23946f2 fe38fb1a 49be6bb8
c873ab28 24b19dfa 7fed1112 e315e0c9 8c44a478 ff861325 83d6f7b6 43
quit
crypto ca certificate chain ASDM_TrustPoint4
certificate 00b54c41fa1578a9e7
308206ce 308205b6 a0030201 02020900 b54c41fa 1578a9e7 300d0609 2a864886
f70d0101 0b050030 81b4310b 30090603 55040613 02555331 10300e06 03550408
13074172 697a6f6e 61311330 11060355 0407130a 53636f74 74736461 6c65311a
30180603 55040a13 11476f44 61646479 2e636f6d 2c20496e 632e312d 302b0603
55040b13 24687474 703a2f2f 63657274 732e676f 64616464 792e636f 6d2f7265
706f7369 746f7279 2f313330 31060355 0403132a 476f2044 61646479 20536563
75726520 43657274 69666963 61746520 41757468 6f726974 79202d20 4732301e
170d3139 30373232 31353135 35385a17 0d323130 37323231 35313535 385a305b
310b3009 06035504 06130255 53310d30 0b060355 04081304 4f68696f 310e300c
06035504 07130544 6f766572 31153013 06035504 0a130c4d 61726c69 74652c20
496e6331 16301406 03550403 0c0d2a2e 6d61726c 6974652e 636f6d30 82012230
0d06092a 864886f7 0d010101 05000382 010f0030 82010a02 82010100 b5041358
b938c6f0 7eaec7a6 968ec195 8cd0179f e5e6d869 20bd2376 9f2c4e4f cd38e32a
c8678e7e 585b00ad a02dd82a 3f0b4c67 824fdfa6 1694a073 6e360420 062c9b02
c082559f 9ac20404 35818e88 6d2d8877 382e3c0a 282002af d33b84b1 1d3b823e
0e6a53dd de82455e fdd5bf76 32b3fcf0 b6885e62 17bf7f70 58253610 5472c152
1d317f05 3e2334af cd3a2591 d483bd53 dd6fb647 0b19c725 1ff6083c abcd1d90
6f7f11c2 311406e5 4bcbdfa1 c1fd31e5 ac8274fa 775106eb bbccd1c2 5088bb02
f3d0922e 83f41ad6 11374540 e149c6f4 b1994e16 1b5da92f 22bb9a7d 3ec2c8c2
3240a33c 14360107 fe3a804e 4c6c1c15 aa75633f 41943bfd f3c632a3 02030100
01a38203 39308203 35300c06 03551d13 0101ff04 02300030 1d060355 1d250416
30140608 2b060105 05070301 06082b06 01050507 0302300e 0603551d 0f0101ff
04040302 05a03036 0603551d 1f042f30 2d302ba0 29a02786 25687474 703a2f2f
63726c2e 676f6461 6464792e 636f6d2f 67646967 3273322d 31332e63 726c305d
0603551d 20045630 54304806 0b608648 0186fd6d 01071702 30393037 06082b06
01050507 0201162b 68747470 3a2f2f63 65727469 66696361 7465732e 676f6461
6464792e 636f6d2f 7265706f 7369746f 72792f30 08060667 810c0102 02307606
082b0601 05050701 01046a30 68302406 082b0601 05050730 01861868 7474703a
2f2f6f63 73702e67 6f646164 64792e63 6f6d2f30 4006082b 06010505 07300286
34687474 703a2f2f 63657274 69666963 61746573 2e676f64 61646479 2e636f6d
2f726570 6f736974 6f72792f 67646967 322e6372 74301f06 03551d23 04183016
801440c2 bd278ecc 348330a2 33d7fb6c b3f0b42c 80ce3025 0603551d 11041e30
1c820d2a 2e6d6172 6c697465 2e636f6d 820b6d61 726c6974 652e636f 6d301d06
03551d0e 04160414 ae5a2621 96567295 ae130727 a0b76397 ba04c4ce 3082017e
060a2b06 010401d6 79020402 0482016e 0482016a 01680076 00a4b909 90b41858
1487bb13 a2cc6770 0a3c3598 04f91bdf b8e377cd 0ec80ddc 10000001 6c1a40ef
38000004 03004730 45022100 9626aa24 3998ff30 2814ddd8 fe75566a eb8fe1c5
b107580d 28ea642e ce1397bf 02206492 96f61198 10c01933 84eb5287 2716ce84
828f5c05 9c831bf6 e47886a4 29a20077 00ee4bbd b775ce60 bae14269 1fabe19e
66a30f7e 5fb072d8 8300c47b 897aa8fd cb000001 6c1a40f4 fe000004 03004830
46022100 856a585c b076a6c9 4a6274df e6781b2f 3cd6c584 a50c1891 80b8a41c
4e53f70d 02210092 74025b41 056266e7 ba8338e2 d5795829 1bbbdc75 743a811f
5b7f8150 34d1bd00 75004494 652eb0ee ceafc440 07d8a8fe 28c0dae6 82bed8cb
31b53fd3 3396b5b6 81a80000 016c1a40 fa800000 04030046 30440220 30b597e4
09add3cc 9cd5f02f 8999412b 277968f2 631e5a90 a9e3a504 5d7c9b10 022045d7
ed38e138 75d1d49e bc1fd3bc d6674782 6efc0be7 77e5acfe e4fb450c f512300d
06092a86 4886f70d 01010b05 00038201 0100b811 5877525d cf79cd7e abd3de28
7eebfa94 9aa05da5 b000fbc7 01929c7a b436a245 7e429785 383226d4 7a5bc39d
cbdeffb6 b1e3863c 4e0f5ad6 7b88119e ffed0594 636f2fbb 77ea4900 679bf420
28e86091 3becb49e 5b6b309b ba481c3c be239442 836e120a e0a5c004 0528803e
2f098fba 5cd43cf7 e134a5c2 3111dce7 8598a3a3 70638633 2a2905e3 9f956275
ac516de7 f22ee8df c443f257 f4d897a0 0efef09f fab05911 d5a99313 4a219521
ef93ad96 3551db60 a8b35826 83a44a32 a57c48dd 037b2c71 454b4a9f 5a1920b9
51fc3e90 3ed51322 4b5d0995 d70aa5cc 03eb4440 a9b0d71d 4a4da85c e36d3a42
fd0b3684 597ca8cf b3ec4172 6e1d7ff1 25d7
quit
certificate ca 07
308204d0 308203b8 a0030201 02020107 300d0609 2a864886 f70d0101 0b050030
8183310b 30090603 55040613 02555331 10300e06 03550408 13074172 697a6f6e
61311330 11060355 0407130a 53636f74 74736461 6c65311a 30180603 55040a13
11476f44 61646479 2e636f6d 2c20496e 632e3131 302f0603 55040313 28476f20
44616464 7920526f 6f742043 65727469 66696361 74652041 7574686f 72697479
202d2047 32301e17 0d313130 35303330 37303030 305a170d 33313035 30333037
30303030 5a3081b4 310b3009 06035504 06130255 53311030 0e060355 04081307
4172697a 6f6e6131 13301106 03550407 130a5363 6f747473 64616c65 311a3018
06035504 0a131147 6f446164 64792e63 6f6d2c20 496e632e 312d302b 06035504
0b132468 7474703a 2f2f6365 7274732e 676f6461 6464792e 636f6d2f 7265706f
7369746f 72792f31 33303106 03550403 132a476f 20446164 64792053 65637572
65204365 72746966 69636174 65204175 74686f72 69747920 2d204732 30820122
300d0609 2a864886 f70d0101 01050003 82010f00 3082010a 02820101 00b9e0cb
10d4af76 bdd49362 eb3064b8 81086cc3 04d96217 8e2fff3e 65cf8fce 62e63c52
1cda1645 4b55ab78 6b638362 90ce0f69 6c99c81a 148b4ccc 4533ea88 dc9ea3af
2bfe8061 9d7957c4 cf2ef43f 303c5d47 fc9a16bc c3379641 518e114b 54f828be
d08cbef0 30381ef3 b026f866 47636dde 7126478f 384753d1 461db4e3 dc00ea45
acbdbc71 d9aa6f00 dbdbcd30 3a794f5f 4c47f81d ef5bc2c4 9d603bb1 b24391d8
a4334eea b3d6274f ad258aa5 c6f4d5d0 a6ae7405 645788b5 4455d42d 2a3a3ef8
b8bde932 0a029464 c4163a50 f14aaee7 7933af0c 20077fe8 df0439c2 69026c63
52fa77c1 1bc87487 c8b99318 5054354b 694ebc3b d3492e1f dcc1d252 fb020301
0001a382 011a3082 0116300f 0603551d 130101ff 04053003 0101ff30 0e060355
1d0f0101 ff040403 02010630 1d060355 1d0e0416 041440c2 bd278ecc 348330a2
33d7fb6c b3f0b42c 80ce301f 0603551d 23041830 1680143a 9a850710 6728b6ef
f6bd0541 6e20c194 da0fde30 3406082b 06010505 07010104 28302630 2406082b
06010505 07300186 18687474 703a2f2f 6f637370 2e676f64 61646479 2e636f6d
2f303506 03551d1f 042e302c 302aa028 a0268624 68747470 3a2f2f63 726c2e67
6f646164 64792e63 6f6d2f67 64726f6f 742d6732 2e63726c 30460603 551d2004
3f303d30 3b060455 1d200030 33303106 082b0601 05050702 01162568 74747073
3a2f2f63 65727473 2e676f64 61646479 2e636f6d 2f726570 6f736974 6f72792f
300d0609 2a864886 f70d0101 0b050003 82010100 087e6c93 10c838b8 96a9904b
ffa15f4f 04ef6c3e 9c8806c9 508fa673 f757311b bebce42f dbf8bad3 5be0b4e7
e679620e 0ca2d76a 637331b5 f5a848a4 3b082da2 5d90d7b4 7c254f11 5630c4b6
449d7b2c 9de55ee6 ef0c61aa bfe42a1b ee849eb8 837dc143 ce44a713 700d911f
f4c813ad 8360d9d8 72a87324 1eb5ac22 0eca1789 6258441b ab892501 000fcdc4
1b62db51 b4d30f51 2a9bf4bc 73fc76ce 36a4cdd9 d82ceaae 9bf52ab2 90d14d75
188a3f8a 4190237d 5b4bfea4 03589b46 b2c36060 83f87d50 41cec2a1 90c3bbef
022fd215 54ee4415 d90aaea7 8a33edb1 2d763626 dc04eb9f f7611f15 dc876fee
469628ad a1267d0a 09a72e04 a38dbcf8 bc043001
quit
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 10
encryption aes-192
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 30
encryption 3des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 40
encryption des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 enable outside client-services port 443
crypto ikev2 remote-access trustpoint ASDM_TrustPoint4
crypto ikev1 enable outside
crypto ikev1 policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
telnet 172.16.0.0 255.255.0.0 inside
telnet timeout 5
ssh stricthostkeycheck
ssh 172.16.0.0 255.255.0.0 inside
ssh Network-LAX 255.255.255.0 inside
ssh Network-TX 255.255.255.0 inside
ssh 69.54.56.242 255.255.255.255 outside
ssh 63.157.106.146 255.255.255.255 outside
ssh 74.3.106.174 255.255.255.255 outside
ssh 63.110.89.234 255.255.255.255 outside
ssh timeout 20
ssh key-exchange group dh-group14-sha1
console timeout 0
management-access inside
dhcpd auto_config outside
!
dhcpd address 172.17.22.100-172.17.22.200 GuestWireless
dhcpd dns 8.8.8.8 8.8.4.4 interface GuestWireless
dhcpd lease 7200 interface GuestWireless
dhcpd enable GuestWireless
!
priority-queue outside
threat-detection basic-threat
threat-detection statistics port
threat-detection statistics protocol
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ntp server 207.150.168.70 source outside
ntp server 172.16.1.22 source inside prefer
ssl trust-point ASDM_TrustPoint4 outside
ssl trust-point ASDM_TrustPoint4 inside
webvpn
enable outside
anyconnect image disk0:/anyconnect-win-4.7.04056-webdeploy-k9.pkg 1
anyconnect profiles vpn.mar.com2 disk0:/vpn.mar.com2.xml
anyconnect profiles vpn.mar.com_client_profile disk0:/vpn.mar.com_client_profile.xml
anyconnect enable
tunnel-group-list enable
group-policy GroupPolicy_vpn.mar.com internal
group-policy GroupPolicy_vpn.mar.com attributes
wins-server value 172.16.1.22 172.16.1.77
dns-server value 172.16.1.22 172.16.1.77
dhcp-network-scope 172.16.101.2
vpn-tunnel-protocol ikev2
split-tunnel-policy tunnelspecified
split-tunnel-network-list value Split-Tunnel-ACL
default-domain value mar2k.com
webvpn
anyconnect profiles value vpn.mar.com2 type user
group-policy GroupPolicy_40.141.230.226 internal
group-policy GroupPolicy_40.141.230.226 attributes
wins-server value 172.16.1.22 172.16.1.77
dns-server value 172.16.1.22 172.16.1.77
vpn-tunnel-protocol ikev1 ikev2
default-domain value mar2k.com
tunnel-group 63.110.89.234 type ipsec-l2l
tunnel-group 63.110.89.234 ipsec-attributes
ikev1 pre-shared-key *****
tunnel-group 74.3.106.174 type ipsec-l2l
tunnel-group 74.3.106.174 ipsec-attributes
ikev1 pre-shared-key *****
tunnel-group 108.69.100.226 type ipsec-l2l
tunnel-group 108.69.100.226 ipsec-attributes
ikev1 pre-shared-key *****
tunnel-group vpn.mar.com type remote-access
tunnel-group vpn.mar.com general-attributes
authentication-server-group mar-LDAP
default-group-policy GroupPolicy_vpn.mar.com
dhcp-server link-selection 172.16.1.22
tunnel-group vpn.mar.com webvpn-attributes
group-alias vpn.mar.com enable
tunnel-group 40.141.230.226 type ipsec-l2l
tunnel-group 40.141.230.226 general-attributes
default-group-policy GroupPolicy_40.141.230.226
tunnel-group 40.141.230.226 ipsec-attributes
ikev1 pre-shared-key *****
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
!
class-map VPN-N-HTTP
match port tcp eq www
match tunnel-group 40.141.230.226
class-map VPN-N-HTTPS
match port tcp eq https
match tunnel-group 40.141.230.226
class-map VPN-N-SQL
match port tcp eq 1433
match tunnel-group 40.141.230.226
class-map VPN-N-RDP
match port tcp eq 3389
match tunnel-group 40.141.230.226
class-map inspection_default
match default-inspection-traffic
class-map VPN-N-RDP2
match port udp eq 3389
match tunnel-group 40.141.230.226
class-map VPN-N-HTTP2
match port tcp eq 8080
match tunnel-group 40.141.230.226
!
!
policy-map VPN-N-PRIORITY
class VPN-N-RDP
priority
class VPN-N-RDP2
priority
class VPN-N-HTTP
priority
class VPN-N-HTTP2
priority
class VPN-N-HTTPS
priority
class VPN-N-SQL
priority
policy-map global-policy
class inspection_default
inspect icmp
class class-default
flow-export event-type all destination 172.16.1.130
!
service-policy global-policy global
service-policy VPN-N-PRIORITY interface outside
prompt hostname context
call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
Cryptochecksum:7133ee7bfeb1f5c0180b8d64f984d16b
: end
vpn#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2020 11:52 AM
Hi,
If your tunnel is up and running, only have issues with some reachability, post the following outputs from with devices: "show run access-list", "show run access-group", "show run nat","show run object", "show run object-group". Your configuration needs a lot of cleaning anyways....
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2020 12:47 PM
LAN 1:
N-HQ-FW1/sec/act# show run access-list
access-list outside.acl.in extended permit icmp any any echo-reply
access-list outside.acl.in extended permit icmp any any time-exceeded
access-list outside.acl.in extended permit tcp any object obj-Video.Conf.Private range 3230 3241
access-list outside.acl.in extended permit udp any object obj-Video.Conf.Private range 3230 3291
access-list outside.acl.in extended permit tcp any object obj-Video.Conf.Private eq h323
access-list outside.acl.in extended permit ip any any log disable inactive
access-list split.tunnel.acl standard permit 192.17.0.0 255.255.0.0
access-list split.tunnel.acl standard permit 172.28.0.0 255.255.0.0
access-list split.tunnel.acl standard permit 172.29.0.0 255.255.0.0
access-list split.tunnel.acl standard permit 172.16.0.0 255.255.0.0
access-list split.tunnel.acl standard permit 172.17.0.0 255.255.0.0
access-list vpn.to.mid extended permit ip object-group DM_INLINE_NETWORK_4 object-group grp-Midwest.Subnets
access-list vpn.to.pr extended permit ip object-group DM_INLINE_NETWORK_1 object-group grp-Prime.Subnets
access-list sfr.acl extended permit ip any any
access-list net.to.vzt extended permit ip any object-group DM_INLINE_NETWORK_2
access-list net.to.vzt extended permit ip object-group DM_INLINE_NETWORK_3 any
access-list AnyConnect_Client_Local_Print extended deny ip any4 any4
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq lpd
access-list AnyConnect_Client_Local_Print remark IPP: Internet Printing Protocol
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 631
access-list AnyConnect_Client_Local_Print remark Windows' printing port
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 9100
access-list AnyConnect_Client_Local_Print remark mDNS: multicast DNS protocol
access-list AnyConnect_Client_Local_Print extended permit udp any4 host 224.0.0.251 eq 5353
access-list AnyConnect_Client_Local_Print remark LLMNR: Link Local Multicast Name Resolution protocol
access-list AnyConnect_Client_Local_Print extended permit udp any4 host 224.0.0.252 eq 5355
access-list AnyConnect_Client_Local_Print remark TCP/NetBIOS protocol
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 137
access-list AnyConnect_Client_Local_Print extended permit udp any4 any4 eq netbios-ns
access-list vpn.to.N extended permit ip 192.17.0.0 255.255.0.0 object-group DM_INLINE_NETWORK_10
access-list vpn.to.N extended permit ip object-group DM_INLINE_NETWORK_5 any
access-list net.to.N extended permit ip any object-group DM_INLINE_NETWORK_6
access-list net.to.N extended permit ip object-group DM_INLINE_NETWORK_7 any
N-HQ-FW1/sec/act#
N-HQ-FW1/sec/act# show run access-group
access-group outside.acl.in in interface outside
access-group outside.acl.in in interface outside2
N-HQ-FW1/sec/act#
N-HQ-FW1/sec/act# sh run nat
nat (inside,outside) source static 192.17.17.0 192.17.17.0 destination static DM_INLINE_NETWORK_9 DM_INLINE_NETWORK_9 no-proxy-arp route-lookup
nat (inside,outside) source static obj-192.17.0.0 obj-192.17.0.0 destination static obj-192.17.0.0 obj-192.17.0.0 no-proxy-arp route-lookup
nat (inside,outside2) source static obj-192.17.0.0-2 obj-192.17.0.0-2 destination static obj-192.17.0.0-2 obj-192.17.0.0-2 no-proxy-arp route-lookup
nat (inside,outside) source static NETWORK_OBJ_192.17.0.0_16 NETWORK_OBJ_192.17.0.0_16 destination static DM_INLINE_NETWORK_8 DM_INLINE_NETWORK_8 no-proxy-arp route-lookup
nat (inside,outside) source static NETWORK_OBJ_192.17.0.0_16 NETWORK_OBJ_192.17.0.0_16 destination static DM_INLINE_NETWORK_10 DM_INLINE_NETWORK_10 no-proxy-arp route-lookup
nat (inside,outside) source static 192.17.17.0 192.17.17.0 destination static DM_INLINE_NETWORK_11 DM_INLINE_NETWORK_11 no-proxy-arp route-lookup
!
object network obj-192.17.0.0
nat (inside,outside) dynamic interface
object network obj-192.17.0.0-2
nat (inside,outside2) dynamic interface
object network obj-Video.Conf.Private
nat (inside,outside) static 40.141.230.227
N-HQ-FW1/sec/act#
N-HQ-FW1/sec/act#
N-HQ-FW1/sec/act#
N-HQ-FW1/sec/act# sh run obj
N-HQ-FW1/sec/act# sh run object
object network obj-192.17.0.0
subnet 192.17.0.0 255.255.0.0
object network obj-192.17.0.0-2
subnet 192.17.0.0 255.255.0.0
object network obj-SheetLine.Private
host 192.17.10.172
object network obj-Video.Conf.Private
host 192.17.12.199
object network obj-TS.Private
host 192.17.10.127
object network obj-Dameware.MiniRemote
host 192.17.10.190
description "Dameware Mini Remote Control external"
object network DCVZT
subnet 172.28.100.0 255.255.255.0
object network StaVG
subnet 172.28.120.0 255.255.255.0
description StaVG
object network VZT
host 192.17.12.170
description RouterAlestraLevel3
object network cisco9k
host 192.17.10.53
object network Cisco9K1
host 192.17.14.1
object network StaAmerica
subnet 172.29.0.0 255.255.0.0
description StaAmerica
object network PolycomStaGarcia
host 172.28.120.14
object network PolycomVZT
host 172.28.127.15
object network PolycomIMSAPlastics
host 172.28.129.15
object network PolycomStaTlalne
host 172.28.123.16
object network PolycomN
host 192.17.12.199
object network Santillan
host 192.17.10.230
description Santillan
object network NET-NCalifornia
subnet 192.168.1.0 255.255.255.0
object network NETWORK_OBJ_192.17.10.0_24
subnet 192.17.10.0 255.255.255.0
object network Jira_N
host 192.17.10.72
object network TestVPNN
host 172.16.1.22
object network NETWORK_OBJ_172.16.0.0_16
subnet 172.16.0.0 255.255.0.0
object network TS01_N
host 192.17.10.127
object network DC1_N
host 172.16.1.22
object network DC2_N
host 172.16.1.77
object network Flori
host 192.17.12.92
object network NPDC
host 192.17.10.102
object network NDC01
host 192.17.10.194
object network N_Confluence
host 192.17.10.71
object network N_Nagios
host 192.17.10.134
object network 192.17.17.0
subnet 192.17.17.0 255.255.255.0
object network UTL1_N
host 172.16.10.155
object network UTL01_N
host 192.17.10.124
object network NETWORK_OBJ_192.17.0.0_16
subnet 192.17.0.0 255.255.0.0
object network N_VPN_SubNET
subnet 172.16.101.0 255.255.255.0
object network NVMHost
host 192.168.20.12
description NVMHost
object network 172.17.20.0
subnet 172.17.20.0 255.255.254.0
N-HQ-FW1/sec/act#
N-HQ-FW1/sec/act#
N-HQ-FW1/sec/act# sh run object-g
N-HQ-FW1/sec/act# sh run object-group
object-group network grp-HQ.LAN.Subnets
network-object 192.17.10.0 255.255.255.0
network-object 192.17.12.0 255.255.255.0
network-object object 192.17.17.0
object-group network grp-Prime.Subnets
network-object 192.17.30.0 255.255.255.0
network-object 192.17.31.0 255.255.255.0
object-group network grp-Midwest.Subnets
network-object 192.17.20.0 255.255.255.0
network-object 192.17.21.0 255.255.255.0
object-group network obj-Dameware.ProxyServer
network-object host 192.17.10.190
object-group service grp-Dameware.Ports tcp
port-object eq https
port-object range 6130 6133
object-group network DM_INLINE_NETWORK_1
network-object object DCVZT
network-object object StaVG
group-object grp-HQ.LAN.Subnets
network-object object StaAmerica
object-group network DM_INLINE_NETWORK_2
network-object object DCVZT
network-object object StaVG
network-object object StaAmerica
object-group network DM_INLINE_NETWORK_3
network-object object DCVZT
network-object object StaVG
network-object object StaAmerica
object-group network DM_INLINE_NETWORK_4
network-object object DCVZT
network-object object StaVG
group-object grp-HQ.LAN.Subnets
network-object object StaAmerica
object-group network PolycomsVZT
network-object object PolycomIMSAPlastics
network-object object PolycomStaGarcia
network-object object PolycomStaTlalne
network-object object PolycomVZT
object-group network DM_INLINE_NETWORK_5
network-object 172.16.0.0 255.255.0.0
network-object 172.17.0.0 255.255.0.0
network-object object NVMHost
object-group network DM_INLINE_NETWORK_8
network-object 172.16.0.0 255.255.0.0
network-object 172.17.0.0 255.255.0.0
object-group network DM_INLINE_NETWORK_9
group-object grp-Midwest.Subnets
group-object grp-Prime.Subnets
object-group network DM_INLINE_NETWORK_10
network-object 172.16.0.0 255.255.0.0
network-object 172.17.0.0 255.255.0.0
network-object object N_VPN_SubNET
network-object object NVMHost
network-object object 172.17.20.0
object-group network DM_INLINE_NETWORK_6
network-object 172.16.0.0 255.255.0.0
network-object 172.17.0.0 255.255.0.0
network-object object NVMHost
object-group network DM_INLINE_NETWORK_7
network-object 172.17.0.0 255.255.0.0
network-object 172.16.0.0 255.255.0.0
network-object object NVMHost
object-group network DM_INLINE_NETWORK_11
network-object object 172.17.20.0
network-object object NETWORK_OBJ_172.16.0.0_16
N-HQ-FW1/sec/act#
N-HQ-FW1/sec/act#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2020 12:52 PM
LAN 2:
vpn# sh run access-list
access-list Split-Tunnel-ACL standard permit 172.16.0.0 255.255.0.0
access-list Split-Tunnel-ACL standard permit 192.17.0.0 255.255.0.0
access-list Split-Tunnel-ACL standard permit 172.28.0.0 255.255.0.0
access-list Split-Tunnel-ACL standard permit 172.29.0.0 255.255.0.0
access-list Split-Tunnel-ACL standard permit 172.17.20.0 255.255.255.0
access-list Split-Tunnel-ACL standard permit 172.17.21.0 255.255.255.0
access-list Split-Tunnel-ACL standard permit 192.168.0.0 255.255.255.0
access-list Split-Tunnel-ACL standard permit 172.17.19.0 255.255.255.0
access-list inside_nat0_outbound extended permit object-group DM_INLINE_SERVICE_4 object-group DM_INLINE_NETWORK_6 object Network-TX
access-list inside_nat0_outbound extended permit object-group DM_INLINE_SERVICE_1 object-group DM_INLINE_NETWORK_7 object Network-LAX
access-list outside_2_cryptomap extended permit ip object-group DM_INLINE_NETWORK_4 object Network-LAX
access-list outside_1_cryptomap extended permit ip object-group DM_INLINE_NETWORK_5 object Network-TX
access-list inside_access_in remark Deny Access to ASNs hosting CryptoBlocker.
access-list inside_access_in extended deny ip any4 object-group DM_INLINE_NETWORK_1
access-list inside_access_in remark Allow Outbound Email for ICE WARP, Per Schuster Request 4/23/13 added by NetOps (dpetika)
access-list inside_access_in extended permit tcp object-group DM_INLINE_NETWORK_3 any4 eq smtp
access-list inside_access_in remark Remote Desktop
access-list inside_access_in extended permit object-group TCPUDP any any eq 3389
access-list inside_access_in extended permit object-group DM_INLINE_SERVICE_2 object-group DM_INLINE_NETWORK_9 object-group DM_INLINE_NETWORK_12
access-list inside_access_in extended permit object-group DM_INLINE_SERVICE_3 object-group DM_INLINE_NETWORK_10 object-group DM_INLINE_NETWORK_8
access-list inside_access_in remark Required for EDI - NetOps Ticket# 93603
access-list inside_access_in extended permit tcp object Operations-PC any4 eq smtp
access-list inside_access_in extended permit tcp object-group Mar-Printers any eq smtp
access-list inside_access_in remark Deny SMTP outbound except for Email Server, Per Schuster Request 4/23/13 added by NetOps (dpetika)
access-list inside_access_in extended deny tcp any4 any4 eq smtp inactive
access-list inside_access_in extended deny ip object PC_ML-TTOM-W7-WS any4 inactive
access-list inside_access_in extended deny ip 172.17.22.0 255.255.255.0 172.16.0.0 255.255.0.0
access-list inside_access_in extended permit ip object Printer-Line object NAS-2
access-list inside_access_in extended deny ip object Printer-Line any
access-list inside_access_in remark Implicit Rule
access-list inside_access_in extended permit ip any4 any4
access-list outside_access_in extended permit icmp any any unreachable
access-list outside_access_in extended permit tcp object-group Polycom-Allowed-IPs host 172.16.0.210 object-group DM_INLINE_TCP_1
access-list outside_access_in extended permit udp object-group Polycom-Allowed-IPs host 172.16.0.210 object-group Polycom-UDP-(3230-3291)
access-list outside_access_in extended deny ip any4 object PC_ML-TTOM-W7-WS inactive
access-list outside_access_in remark Remote ICEWARP Access
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq www inactive
access-list outside_access_in remark RDP Access from Outside
access-list outside_access_in extended permit tcp any4 object Server-Remote1 eq 3389 inactive
access-list outside_access_in remark External Access for EDI Partners Port 5080
access-list outside_access_in extended permit object-group DM_INLINE_SERVICE_5 object-group DM_INLINE_NETWORK_2 object Server-EDI1
access-list outside_access_in remark Deny RDP Access From INTERNET
access-list outside_access_in extended deny object-group TCPUDP any object Server-EDI1 eq 3389
access-list outside_access_in remark Allow Remote RDP Access
access-list outside_access_in extended permit tcp any4 object Server-TS1 eq 3389 inactive
access-list outside_access_in extended deny ip object-group Blocked-IPs object Server-IceWarp inactive
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq smtp inactive
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq 32000 inactive
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq 32001 inactive
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq 366 inactive
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq 465 inactive
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq 5229 inactive
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq 993 inactive
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq 995 inactive
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq https inactive
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq imap4 inactive
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq ldaps inactive
access-list outside_access_in extended permit tcp any4 object Server-IceWarp eq pop3 inactive
access-list outside_access_in extended permit tcp any4 object Server-Briefcase1 eq ftp inactive
access-list outside_access_in extended permit tcp any4 object Server-Briefcase1 eq www inactive
access-list outside_access_in extended permit tcp any4 object Server-Briefcase1 eq ftp-data inactive
access-list outside_access_in extended permit udp any4 object Server-Appsvr1 eq ntp inactive
access-list outside_access_in remark Migration, ACE (line 30) expanded: permit tcp any4 host OUTSIDE_198.30.101.73
access-list outside_access_in extended permit tcp any4 object DEV-GANSAW eq 9600 inactive
access-list outside_access_in remark Migration: End of expansion
access-list outside_access_in remark Ticket 71868 External Access on port 9602 for Doucet Grid Saw
access-list outside_access_in remark Migration, ACE (line 32) expanded: permit tcp any4 host OUTSIDE_198.30.101.73
access-list outside_access_in extended permit tcp any4 object Doucet-Grid-Saw eq 9602 inactive
access-list outside_access_in remark Migration: End of expansion
access-list outside_access_in remark Ticket 99868
access-list outside_access_in remark Migration, ACE (line 28) expanded: permit tcp any4 host OUTSIDE_198.30.101.73 object-group RDP
access-list outside_access_in remark Migration: End of expansion
access-list outside_access_in extended permit tcp any4 object Server-PCM2 eq https
access-list outside_access_in extended permit tcp any4 object Server-PCM2 eq www inactive
access-list outside_access_in remark RDP
access-list outside_access_in extended permit object-group TCPUDP any any eq 3389
access-list ACL-SNMP remark Used to allow access from SNMP server for Nagios checks
access-list ACL-SNMP extended permit ip object-group DM_INLINE_NETWORK_13 object-group DM_INLINE_NETWORK_11
access-list outside_cryptomap extended permit ip object-group DM_INLINE_NETWORK_14 192.17.0.0 255.255.0.0
access-list outside_cryptomap extended permit ip object-group DM_INLINE_NETWORK_16 192.17.0.0 255.255.0.0
access-list net.to.N extended permit ip any 192.17.0.0 255.255.0.0
access-list net.to.N extended permit ip 192.17.0.0 255.255.0.0 any
vpn#
vpn# sh run acc
vpn# sh run access-gr
vpn# sh run access-group
access-group inside_access_in in interface inside
access-group outside_access_in in interface outside
vpn#
vpn# sh run nat
vpn# sh run nat
nat (inside,outside) source static obj-172.17.20.0 obj-172.17.20.0 destination static obj-172.16.101.0 obj-172.16.101.0 no-proxy-arp route-lookup
nat (inside,outside) source static obj-172.17.21.0 obj-172.17.21.0 destination static obj-172.16.101.0 obj-172.16.101.0 no-proxy-arp route-lookup
nat (inside,outside) source static NET-VZT-172.28.0.0 NET-VZT-172.28.0.0 destination static obj-172.16.101.0 obj-172.16.101.0 no-proxy-arp route-lookup
nat (inside,outside) source static NET-VZT-172.29.0.0 NET-VZT-172.29.0.0 destination static obj-172.16.101.0 obj-172.16.101.0 no-proxy-arp route-lookup
nat (inside,outside) source static obj-172.16.0.0 obj-172.16.0.0 destination static obj-172.16.101.0 obj-172.16.101.0 no-proxy-arp route-lookup
nat (any,outside) source static DM_INLINE_NETWORK_4 DM_INLINE_NETWORK_4 destination static Network-LAX Network-LAX no-proxy-arp route-lookup
nat (inside,any) source static obj-172.16.0.0 obj-172.16.0.0 destination static Network-TX Network-TX no-proxy-arp route-lookup
nat (inside,any) source static obj-172.16.0.0 obj-172.16.0.0 destination static Network-LAX Network-LAX no-proxy-arp route-lookup
nat (inside,outside) source static any any destination static NETWORK_OBJ_172.18.0.0_24 NETWORK_OBJ_172.18.0.0_24 no-proxy-arp route-lookup
nat (inside,outside) source static Server-VideoConf OUTSIDE_198.30.101.71
nat (inside,outside) source static DM_INLINE_NETWORK_15 DM_INLINE_NETWORK_15 destination static NETWORK_OBJ_192.17.0.0_16 NETWORK_OBJ_192.17.0.0_16 no-proxy-arp route-lookup
nat (inside,outside) source static DM_INLINE_NETWORK_16 DM_INLINE_NETWORK_16 destination static NETWORK_OBJ_192.17.0.0_16 NETWORK_OBJ_192.17.0.0_16 no-proxy-arp route-lookup
!
object network Server-PCM2
nat (inside,outside) static OUTSIDE_198.30.101.78 service tcp https https
object network Server-PCM2-01
nat (inside,outside) static OUTSIDE_198.30.101.78 service tcp www www
object network Server-EDI1
nat (inside,outside) static OUTSIDE_198.30.101.72
object network obj_any
nat (inside,outside) dynamic interface
object network Net-Guest-Wireless
nat (GuestWireless,outside) dynamic interface
vpn#
vpn#
vpn# sh run obje
vpn# sh run object
object network Server-EDIPartner1
host 12.28.215.206
description Created during name migration
object network Server-EDIPartner2
host 209.95.232.130
description Created during name migration
object network Server-EDIPartner3
host 65.196.53.194
description Created during name migration
object network Net-108.170.0.0
subnet 108.170.0.0 255.255.192.0
description Created during name migration
object network Net-162.213.252.0
subnet 162.213.252.0 255.255.255.0
description Created during name migration
object network Net-162.213.254.0
subnet 162.213.254.0 255.255.254.0
description Created during name migration
object network Net-174.138.160.0
subnet 174.138.160.0 255.255.240.0
description Created during name migration
object network Net-184.164.128.0
subnet 184.164.128.0 255.255.224.0
description Created during name migration
object network Net-184.171.160.0
subnet 184.171.160.0 255.255.240.0
description Created during name migration
object network Net-184.95.32.0
subnet 184.95.32.0 255.255.224.0
description Created during name migration
object network Net-192.198.192.0
subnet 192.198.192.0 255.255.248.0
description Created during name migration
object network Net-192.198.200.0
subnet 192.198.200.0 255.255.252.0
description Created during name migration
object network Net-198.15.64.0
subnet 198.15.64.0 255.255.192.0
description Created during name migration
object network Net-198.24.128.0
subnet 198.24.128.0 255.255.224.0
description Created during name migration
object network Net-199.48.165.0
subnet 199.48.165.0 255.255.255.0
description Created during name migration
object network Net-209.188.0.0
subnet 209.188.0.0 255.255.224.0
description Created during name migration
object network Net-66.85.128.0
subnet 66.85.128.0 255.255.192.0
description Created during name migration
object network Net-69.194.224.0
subnet 69.194.224.0 255.255.255.0
description Created during name migration
object network Net-69.194.226.0
subnet 69.194.226.0 255.255.255.0
description Created during name migration
object network Net-173.246.96.0
subnet 173.246.96.0 255.255.240.0
description Created during name migration
object network Net-185.26.124.0
subnet 185.26.124.0 255.255.252.0
description Created during name migration
object network Net-217.70.176.0
subnet 217.70.176.0 255.255.240.0
description Created during name migration
object network Net-46.226.104.0
subnet 46.226.104.0 255.255.248.0
description Created during name migration
object network Net-92.243.0.0
subnet 92.243.0.0 255.255.224.0
description Created during name migration
object network Net-95.142.160.0
subnet 95.142.160.0 255.255.240.0
description Created during name migration
object network OUTSIDE_50.194.86.245
host 50.194.86.245
description Created during name migration
object network Non-Us1
subnet 109.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us2
subnet 110.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us3
subnet 111.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us4
subnet 112.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us5
subnet 113.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us6
subnet 114.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us7
subnet 115.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us8
subnet 116.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us9
subnet 117.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us10
subnet 118.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us11
subnet 119.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us12
subnet 120.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us13
subnet 121.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us14
subnet 122.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us15
subnet 123.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us16
subnet 124.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us17
subnet 125.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us18
subnet 126.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us39
subnet 102.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us40
subnet 103.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us41
subnet 104.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us42
subnet 105.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us43
subnet 106.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us19
subnet 133.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us26
subnet 176.125.0.0 255.255.0.0
description Created during name migration
object network Non-Us28
subnet 177.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us29
subnet 178.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us30
subnet 180.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us31
subnet 182.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us32
subnet 183.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us20
subnet 186.0.0.0 255.255.255.0
description Created during name migration
object network Non-Us21
subnet 187.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us22
subnet 188.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us23
subnet 189.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us24
subnet 190.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us25
subnet 191.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us27
subnet 195.0.0.0 255.128.0.0
description Created during name migration
object network Non-Us33
subnet 31.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us34
subnet 5.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us36
subnet 90.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us35
subnet 92.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us37
subnet 94.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us38
subnet 95.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us47
subnet 222.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us45
subnet 88.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us46
subnet 89.0.0.0 255.0.0.0
description Created during name migration
object network Non-Us44
subnet 93.0.0.0 255.0.0.0
description Created during name migration
object network US-Block-1
subnet 3.0.0.0 255.0.0.0
description Created during name migration
object network Server-IceWarp
host 172.16.1.8
description Created during name migration
object network Server-NM1
host 172.16.1.130
description Old name = ML-VM-Test-W7-1
object network obj-172.16.0.0
subnet 172.16.0.0 255.255.0.0
object network Network-TX
subnet 192.168.0.0 255.255.255.0
object network Network-LAX
subnet 192.168.1.0 255.255.255.0
object network Server-Appsvr1
host 172.16.1.30
object network OUTSIDE_198.30.101.73
host 198.30.101.73
object network DEV-GANSAW
host 172.16.250.101
object network Doucet-Grid-Saw
host 172.16.250.102
object network Syteline1-172.16.1.26
host 172.16.1.26
object network Server-PCM2
host 172.16.10.31
object network OUTSIDE_198.30.101.78
host 198.30.101.78
object network Server-PCM2-01
host 172.16.10.31
object network OUTSIDE_198.30.101.66
host 198.30.101.66
object network Server-Briefcase1
host 172.16.1.5
object network OUTSIDE_198.30.101.67
host 198.30.101.67
object network Server-Remote1
host 172.16.1.35
object network OUTSIDE_198.30.101.68
host 198.30.101.68
object network Server-EDI1
host 172.16.1.38
object network OUTSIDE_198.30.101.72
host 198.30.101.72
object network Server-TS1
host 172.16.1.44
object network OUTSIDE_198.30.101.74
host 198.30.101.74
object network obj_any
subnet 0.0.0.0 0.0.0.0
object network obj-172.17.0.0
subnet 172.17.0.0 255.255.0.0
object network Operations-PC
host 172.16.102.84
description Created during name migration
object network PC_ML-TTOM-W7-WS
host 172.16.102.119
description Created during name migration
object network NETWORK_OBJ_172.18.0.0_24
subnet 172.18.0.0 255.255.255.0
object network PRT-IP-172.16.1.85
host 172.16.1.85
description Printer
object network PRT-IP-172.16.1.87
host 172.16.1.87
description Printer
object network PRT-IP-172.16.1.88
host 172.16.1.88
description Printer
object network PRT-IP-172.16.1.90
host 172.16.1.90
description Printer
object network PRT-IP-172.16.1.93
host 172.16.1.93
description Printer
object network PRT-IP-172.16.11.17
host 172.16.11.17
description Printer
object network PRT-IP-172.16.11.19
host 172.16.11.19
description Printer
object network Server-VideoConf
host 172.16.0.210
object network OUTSIDE_198.30.101.71
host 198.30.101.71
object network Net-97.0.0.0
subnet 97.0.0.0 255.0.0.0
description N - Darry Home Office Public Range
object network OUTSIDE_173.9.221.41
host 173.9.221.41
description N Secondary WAN
object network OUTSIDE_40.141.230.226
host 40.141.230.226
description N Primary WAN
object network OUTSIDE_40.141.230.227
host 40.141.230.227
description N Polycom
object network Range-VZT_Public_IPs
range 200.76.17.14 200.76.17.18
description Range of VZT Public IPs
object network Net-76.0.0.0
subnet 76.0.0.0 255.0.0.0
object network Net-73.221.0.0
subnet 73.221.0.0 255.255.0.0
object network NET-VZT-172.28.0.0
subnet 172.28.0.0 255.255.0.0
object network NET-VZT-172.29.0.0
subnet 172.29.0.0 255.255.0.0
object network Dover-Gateway
host 172.16.3.60
object network Net-73.225.0.0
subnet 73.225.0.0 255.255.0.0
object network obj-172.16.101.0
subnet 172.16.101.0 255.255.255.0
object network obj-172.17.21.0
subnet 172.17.21.0 255.255.255.0
object network obj-172.17.20.0
subnet 172.17.20.0 255.255.255.0
object network Net-AP_Mgmt
subnet 172.17.19.0 255.255.255.0
description AP Management
object network Net-Guest-Wireless
subnet 172.17.22.0 255.255.255.0
description Guest Wireless
object network Printer-Line
host 172.16.102.141
description Block access to Internet
object network NAS-2
host 172.16.10.38
object network TestVPNMar
host 172.16.1.22
object network Jira_N
host 192.17.10.72
object network Santi
host 192.17.10.230
object network NETWORK_OBJ_172.16.0.0_16
subnet 172.16.0.0 255.255.0.0
object network DC1_Mar
host 172.16.1.22
object network DC2_Mar
host 172.16.1.77
object network TS01_N
host 192.17.10.127
object network Flori
host 192.17.12.92
object network NDC01
host 192.17.10.194
object network NPDC
host 192.17.10.102
object network N_Confluence
host 192.17.10.71
object network N_Nagios
host 192.17.10.134
object network UTL1_Mar
host 172.16.10.155
object network UTL01_N
host 192.17.10.124
object network NETWORK_OBJ_192.17.0.0_16
subnet 192.17.0.0 255.255.0.0
object network TestOutside
host 173.9.221.46
object network Mar17
subnet 172.17.0.0 255.255.0.0
object network MarVMHost
host 192.168.20.12
description MarVMHost
object network Jenkins
host 192.17.10.120
vpn# sh run object-gr
vpn# sh run object-group
object-group service SVG-ICEWARP tcp
description ICEWARP Email Access
port-object eq 32000
port-object eq 32001
port-object eq 366
port-object eq imap4
port-object eq pop3
port-object eq smtp
port-object eq 465
port-object eq 5229
port-object eq 993
port-object eq 995
port-object eq www
port-object eq https
port-object eq ldaps
object-group service SVG-BRIEFCASE tcp
port-object eq ftp
port-object eq ftp-data
port-object eq www
object-group network DM_INLINE_NETWORK_2
network-object object Server-EDIPartner1
network-object object Server-EDIPartner2
network-object object Server-EDIPartner3
object-group service SRV-GANGSAW tcp
port-object eq 9600
object-group service SRV-Doucet-Grid-Saw tcp
description HD Ticket 71868 External Access on port 9602 for Doucet Grid Saw
port-object eq 9602
object-group network BGPAS20454-HIGHHO
description www.bc.net
network-object object Net-108.170.0.0
network-object object Net-162.213.252.0
network-object object Net-162.213.254.0
network-object object Net-174.138.160.0
network-object object Net-184.164.128.0
network-object object Net-184.171.160.0
network-object object Net-184.95.32.0
network-object object Net-192.198.192.0
network-object object Net-192.198.200.0
network-object object Net-198.15.64.0
network-object object Net-198.24.128.0
network-object object Net-199.48.165.0
network-object object Net-209.188.0.0
network-object object Net-66.85.128.0
network-object object Net-69.194.224.0
network-object object Net-69.194.226.0
object-group network BGPAS29169-GANDI
description GANDI Registrar
network-object object Net-173.246.96.0
network-object object Net-185.26.124.0
network-object object Net-217.70.176.0
network-object object Net-46.226.104.0
network-object object Net-92.243.0.0
network-object object Net-95.142.160.0
object-group network DM_INLINE_NETWORK_1
group-object BGPAS20454-HIGHHO
group-object BGPAS29169-GANDI
object-group service Web-Services
service-object tcp destination eq ftp
service-object tcp destination eq ftp-data
service-object tcp destination eq www
service-object tcp destination eq https
object-group service RDP tcp
port-object eq 3389
object-group network Blocked-IPs
network-object object OUTSIDE_50.194.86.245
network-object object Non-Us1
network-object object Non-Us2
network-object object Non-Us3
network-object object Non-Us4
network-object object Non-Us5
network-object object Non-Us6
network-object object Non-Us7
network-object object Non-Us8
network-object object Non-Us9
network-object object Non-Us10
network-object object Non-Us11
network-object object Non-Us12
network-object object Non-Us13
network-object object Non-Us14
network-object object Non-Us15
network-object object Non-Us16
network-object object Non-Us17
network-object object Non-Us18
network-object object Non-Us39
network-object object Non-Us40
network-object object Non-Us41
network-object object Non-Us42
network-object object Non-Us43
network-object object Non-Us19
network-object object Non-Us26
network-object object Non-Us28
network-object object Non-Us29
network-object object Non-Us30
network-object object Non-Us31
network-object object Non-Us32
network-object object Non-Us20
network-object object Non-Us21
network-object object Non-Us22
network-object object Non-Us23
network-object object Non-Us24
network-object object Non-Us25
network-object object Non-Us27
network-object object Non-Us33
network-object object Non-Us34
network-object object Non-Us36
network-object object Non-Us35
network-object object Non-Us37
network-object object Non-Us38
network-object object Non-Us47
network-object object Non-Us45
network-object object Non-Us46
network-object object Non-Us44
object-group network USIPAddreses
network-object object US-Block-1
object-group network DM_INLINE_NETWORK_3
network-object object Server-IceWarp
network-object object Server-NM1
object-group network Mar-Printers
description All Printer IP addresses to allow SMTP outbound for scan to email.
network-object object PRT-IP-172.16.1.85
network-object object PRT-IP-172.16.1.87
network-object object PRT-IP-172.16.1.88
network-object object PRT-IP-172.16.1.90
network-object object PRT-IP-172.16.1.93
network-object object PRT-IP-172.16.11.17
network-object object PRT-IP-172.16.11.19
object-group network Polycom-Allowed-IPs
description IP addresses allowed to access the Polycom video conferencing system
network-object object Net-97.0.0.0
network-object object OUTSIDE_173.9.221.41
network-object object OUTSIDE_40.141.230.226
network-object object OUTSIDE_40.141.230.227
network-object object Range-VZT_Public_IPs
network-object object Net-76.0.0.0
network-object object Net-73.221.0.0
network-object object Net-73.225.0.0
object-group service Polycom-TCP-(3230-3241) tcp
port-object range 3230 3241
object-group service Polycom-UDP-(3230-3291) udp
port-object range 3230 3291
object-group service DM_INLINE_TCP_1 tcp
group-object Polycom-TCP-(3230-3241)
port-object eq h323
object-group network VZT-Networks
network-object object NET-VZT-172.28.0.0
network-object object NET-VZT-172.29.0.0
object-group network DM_INLINE_NETWORK_4
network-object 172.16.0.0 255.255.0.0
group-object VZT-Networks
object-group network DM_INLINE_NETWORK_5
network-object 172.16.0.0 255.255.0.0
group-object VZT-Networks
object-group network DM_INLINE_NETWORK_6
network-object 172.16.0.0 255.255.0.0
group-object VZT-Networks
object-group network DM_INLINE_NETWORK_7
network-object 172.16.0.0 255.255.0.0
group-object VZT-Networks
object-group protocol TCPUDP
protocol-object udp
protocol-object tcp
object-group service DM_INLINE_SERVICE_1
service-object ip
service-object tcp-udp destination eq 3389
object-group network DM_INLINE_NETWORK_8
network-object 172.16.0.0 255.255.0.0
network-object 172.16.102.0 255.255.255.0
object-group network DM_INLINE_NETWORK_9
network-object 172.16.0.0 255.255.0.0
network-object 172.16.102.0 255.255.255.0
object-group service DM_INLINE_SERVICE_4
service-object ip
service-object tcp-udp destination eq 3389
object-group network DM_INLINE_NETWORK_10
network-object Net-RedZone 255.255.255.0
network-object Net-WiFi 255.255.255.0
object-group network DM_INLINE_NETWORK_12
network-object Net-RedZone 255.255.255.0
network-object Net-WiFi 255.255.255.0
object-group service DM_INLINE_SERVICE_2
service-object ip
service-object tcp-udp destination eq 3389
object-group service DM_INLINE_SERVICE_3
service-object ip
service-object tcp-udp destination eq 3389
object-group service DM_INLINE_SERVICE_5
service-object ip
service-object tcp-udp destination eq 5080
object-group network DM_INLINE_NETWORK_11
network-object host 172.16.0.1
network-object object obj-172.16.0.0
network-object 172.17.0.0 255.255.0.0
network-object object MarVMHost
network-object Net-RedZone 255.255.255.0
network-object Net-WiFi 255.255.255.0
object-group network DM_INLINE_NETWORK_13
network-object host 192.17.10.134
network-object object Jenkins
object-group network DM_INLINE_NETWORK_14
network-object 172.16.0.0 255.255.0.0
network-object 172.17.0.0 255.255.0.0
network-object object obj-172.16.101.0
network-object object MarVMHost
network-object 172.17.19.0 255.255.255.0
network-object Net-RedZone 255.255.255.0
network-object Net-WiFi 255.255.255.0
object-group network DM_INLINE_NETWORK_15
network-object 172.16.0.0 255.255.0.0
network-object 172.17.0.0 255.255.0.0
object-group network DM_INLINE_NETWORK_16
network-object object obj-172.16.0.0
network-object object obj-172.16.101.0
network-object object MarVMHost
network-object object Mar17
object-group network MarNet17
network-object Net-RedZone 255.255.255.0
network-object Net-WiFi 255.255.255.0
network-object object Mar17
network-object object Net-AP_Mgmt
vpn#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2020 07:57 AM
Hi,
Did you find anything? I already remove the Networks and started from 0, but again, only 2 of that networks are working, I have no idea why if everything is as same.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2020 10:46 AM
Sometimes, the FW did not take all the Subnets on the Phase 2, so try this:
Move the Subnets that are not working to the Top of the ACL od the CryptoMap
And validate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2020 10:48 AM
Thanks that worked!
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: