- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: VPN deployment failed Config Error -- nat (inside,any) dynamic Out
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2021 12:43 PM
First VPN config. Missing something simple.
ERROR: Address X.X.X.X overlaps with outside interface address.
ERROR: NAT Policy is not downloaded.
Firepower 2100 series using FDM for configuration. I have configured the VPN for inside network object X.X.X.0/24 > Dynamic PAT > Outside facing public IP address (configured as HOST object)
From the config error called out in the failed deployment log, I know that I have messed up NAT policy somehow, but can't figure out how. Any help would be greatly appreciated.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2021 12:08 AM
The FDM should take care of exempting the VPN traffic without you to have to create any manual rules. However, if you still need to create a NAT exemption rule for the VPN traffic then that should be a manual static NAT rule where you specify the source in both the original packet and translated packet section as the endpoint source or the whole subnet where those endpoints are located. The same will be for the destination IP/subnet, you will set the same destination address in both the original packet and the translated packet.
Regarding the error you are seeing when you tried to apply the dynamic rule, I think it is simply because you can't use the same IP assigned to an interface in a NAT rule with a custom object. In your case it seems that the public IP 65.140.69.98 is assigned already to the outside interface. It would be enough to use a different public IP address associated to the object OutsidePublicIP and specify the destination interface as outside. That NAT rule will translate the traffic sourcing from the WHH-PACS-Network to the public IP 65.140.69.89.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2021 02:11 PM - edited 08-31-2021 02:37 PM
Hello @jreynolds4 ,
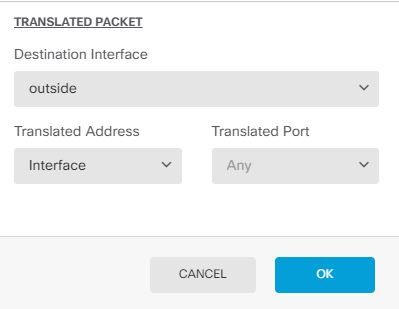
If you want to configure Dynamic PAT, use the Option Interface Instead of specifying an object contains outside interface IP.
Hope that helps!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2021 02:29 PM
i will try outside interface (instead of any)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2021 05:26 PM
Thank you so much for the response. My post was incorrect. Although the deploy error lead me to thinking there is an error in "NAT" rules that is incorrect. I have exempted this site to site VPN from NAT. With this in mind I am even more confused as to the config error.
ERROR: Address X.X.X.X overlaps with outside interface address.
ERROR: NAT Policy is not downloaded
Config Error -- nat (inside,any) dynamic OutsidePublicIP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2021 05:43 PM - edited 08-31-2021 05:43 PM
Hello @jreynolds4 ,
The PAT you should specifiy the outside to nat with, like this :
nat (inside,outside) dynamic OutsidePublicIP or nat (inside,outside) dynamic interface (Check the capture i have shared above for the example)
I'm assuming you want to "Any traffic from the inside zone going outside to be PAT", with the NAT Exempt checkbox enabled the local networks and remote networks configured under S2S VPN are going to be exempt from the PAT Policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2021 06:17 PM
Because I am so new to this I think it best to describe the purpose of the site to site VPN. This is to accommodate connections from individual workstations to our Electronic Health Records vendor. The connections are interactive and bi-directional. For this reason the individual IP addresses from the inside network object need to be visible to the vendor and, therefore, need to be exempt from NAT rules.
I hope this explanation makes sense. I am losing my mind a bit on this. I have opened a ticket with Cisco support. Hopefully they can walk me through. Fast learner, but starting at 0 here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2021 12:02 AM
The FDM should take care of exempting the VPN traffic without you to have to create any manual rules. However, if you still need to create a NAT exemption rule for the VPN traffic then that should be a manual static NAT rule where you specify the source in both the original packet and translated packet section as the endpoint source or the whole subnet where those endpoints are located. The same will be for the destination IP/subnet, you will set the same destination address in both the original packet and the translated packet.
Regarding the error you are seeing when you tried to apply the dynamic rule, I think it is simply because you can't use the same IP assigned to an interface in a NAT rule with a custom object. In your case it seems that the public IP 65.140.69.98 is assigned already to the outside interface. It would be enough to use a different public IP address associated to the object OutsidePublicIP and specify the destination interface as outside. That NAT rule will translate the traffic sourcing from the WHH-PACS-Network to the public IP 65.140.69.89.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2021 12:08 AM
The FDM should take care of exempting the VPN traffic without you to have to create any manual rules. However, if you still need to create a NAT exemption rule for the VPN traffic then that should be a manual static NAT rule where you specify the source in both the original packet and translated packet section as the endpoint source or the whole subnet where those endpoints are located. The same will be for the destination IP/subnet, you will set the same destination address in both the original packet and the translated packet.
Regarding the error you are seeing when you tried to apply the dynamic rule, I think it is simply because you can't use the same IP assigned to an interface in a NAT rule with a custom object. In your case it seems that the public IP 65.140.69.98 is assigned already to the outside interface. It would be enough to use a different public IP address associated to the object OutsidePublicIP and specify the destination interface as outside. That NAT rule will translate the traffic sourcing from the WHH-PACS-Network to the public IP 65.140.69.89.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide