- Cisco Community
- Technology and Support
- DevNet Hub
- DevNet Networking
- Networking Blogs
- Prime Infrastructure 3.6 API Preview: PSK support in WLAN templates
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Hey Folks! In Prime Infrastructure 3.6 we are going to extend WLAN provisioning API resources with basic support of PSK configuration. I prepared preview of the changes and couple of examples for you.
1. API Resources Preview
There are following API resources that allow to manage and retrieve WLAN template details:
- GET data/WlanTemplates - provides information about WLAN templates stored on the Prime Infrastructure instance
- POST op/wlanProvisioning/wlanTemplate - creates new WLAN template on the Prime Infrastructure instance
- PUT op/wlanProvisioning/wlanTemplate - modifies existing WLAN template
- DELETE op/wlanProvisioning/wlanTemplate - removes existing WLAN template
- PUT op/wlanProvisioning/deployTemplate - schedules a job to deploy a WLAN template onto a WLAN controller
GET data/WlanTemplates
data/WlanTemplates API contains number of attributes related to PSK configuration.
- wpaSecurityEnabled - Is WPA layer 2 security enabled?
- wpaEnabled - When wpaSecurityEnabled is true, this denotes whether the WPA1 policy is enabled
- wpaEncryptionProtocolAes - When wpaSecurityEnabled and wpaEnabled are both true, this denotes whether AES encryption is supported for the WPA1 policy
- wpaEncryptionProtocolTkip - When wpaSecurityEnabled and wpaEnabled are both true, this denotes whether TKIP encryption is supported for the WPA1 policy
- wpa2Enabled - When wpaSecurityEnabled is true, this denotes whether the WPA2 policy is enabled
- wpa2EncryptionProtocolAes - When wpaSecurityEnabled and wpa2Enabled are both true, this denotes whether AES encryption is supported for the WPA2 policy
- wpa2EncryptionProtocolTkip - When wpaSecurityEnabled and wpa2Enabled are both true, this denotes whether TKIP encryption is supported for the WPA2 policy
- wpaAuthenticationKeyManagement8021x - When wpaSecurityEnabled is true, this denotes whether 802.1X key management is enabled
- wpaAuthenticationKeyManagementCckm - When wpaSecurityEnabled is true, this denotes whether Cisco Centralized Key Management (CCKM) is enabled
- wpaAuthenticationKeyManagementPsk - When wpaSecurityEnabled is true, this denotes whether preshared key management is enabled
- wpaControllerSpecificPresharedKeyEnabled - When wpaSecurityEnabled and wpaAuthenticationKeyManagementPsk are both enabled, this denotes if the pre-shared key is controller specific
- wpaPresharedKey - When wpaSecurityEnabled and wpaAuthenticationKeyManagementPsk are both enabled, this denotes pre-shared key in ASCII or HEX format
- wpaPresharedKeyFormat - When wpaSecurityEnabled and wpaAuthenticationKeyManagementPsk are both enabled, this denotes pre-shared key format, ASCII or HEX
API response example
Below you can find an example of the data/WlanTemplates API response. Attributes that are not related to PSK configuration are omitted.
{
"queryResponse" : {
...
"entity" : {
...
"wlanTemplatesDTO" : {
...,
"templateName" : "PSK Template Example",
"wpaSecurityEnabled" : true,
"wpaEnabled" : true,
"wpaEncryptionProtocolAes" : true,
"wpaEncryptionProtocolTkip" : false,
"wpa2Enabled" : false,
"wpa2EncryptionProtocolAes" : false,
"wpa2EncryptionProtocolTkip" : false,
"wpaAuthenticationKeyManagement8021x" : false,
"wpaAuthenticationKeyManagementCckm" : false,
"wpaAuthenticationKeyManagementPsk" : true,
"wpaPresharedKey" : "Pre-shared key",
"wpaPresharedKeyFormat" : "ASCII"
}
}
}
POST op/wlanProvisioning/wlanTemplate and PUT op/wlanProvisioning/wlanTemplate
Both POST op/wlanProvisioning/wlanTemplate and PUT op/wlanProvisioning/wlanTemplate API resources use the same payload to create or modify WLAN templates.
There are following attributes that are related to PSK configuration:
- layer2Security - contains Layer 2 security configuration
- securityMode - Layer 2 security mode, NONE or WPAWPA2
- wpaEnabled - When securityMode is WPAWPA2, this denotes whether the WPA1 policy is enabled
- wpaEncryptionProtocolAes - When securityMode is WPAWPA2 and wpaEnabled is true, this denotes whether AES encryption is supported for the WPA1 policy
- wpaEncryptionProtocolTkip - When securityMode is WPAWPA2 and wpaEnabled is true, this denotes whether TKIP encryption is supported for the WPA1 policy
- wpa2Enabled - When securityMode is WPAWPA2, this denotes whether the WPA2 policy is enabled
- wpa2EncryptionProtocolAes - When securityMode is WPAWPA2 and wpaEnabled is true, this denotes whether AES encryption is supported for the WPA2 policy
- wpa2EncryptionProtocolTkip - When securityMode is WPAWPA2 and wpaEnabled is true, this denotes whether TKIP encryption is supported for the WPA2 policy
- wpaAuthenticationKeyManagement8021x - When securityMode is WPAWPA2, this denotes whether 802.1X key management is enabled
- wpaAuthenticationKeyManagementCckm - When securityMode is WPAWPA2, this denotes whether Cisco Centralized Key Management (CCKM) is enabled
- wpaAuthenticationKeyManagementPsk - When securityMode is WPAWPA2 this denotes whether preshared key management is enabled
- wpaControllerSpecificPresharedKeyEnabled - When securityMode is WPAWPA2 and wpaAuthenticationKeyManagementPsk is enabled, this denotes if the pre-shared key is controller specific
- wpaPresharedKey - When securityMode is WPAWPA2 and wpaAuthenticationKeyManagementPsk is enabled, this denotes pre-shared key in ASCII or HEX format
- wpaPresharedKeyFormat - When securityMode is WPAWPA2 and wpaAuthenticationKeyManagementPsk is enabled, this denotes pre-shared key format, ASCII or HEX
API request payload examples
To create a WLAN template without layer 2 security config:
{
"wlanTemplate" : {
"interfaceName" : "Dot11Radio0",
"interfaceType" : "INTERFACE",
"lanType" : "WIRELESS",
"profileName" : "psk",
"ssid" : "psk",
"templateName" : "example",
"layer2Security" : {
"securityMode" : "NONE"
}
}
}
Or even more simple:
{
"wlanTemplate" : {
"interfaceName" : "Dot11Radio0",
"interfaceType" : "INTERFACE",
"lanType" : "WIRELESS",
"profileName" : "psk",
"ssid" : "psk",
"templateName" : "psk_example",
}
}
To create a WLAN template with WPA, AES cipher, and a pre-shared key:
{
"wlanTemplate" : {
"interfaceName" : "Dot11Radio0",
"interfaceType" : "INTERFACE",
"lanType" : "WIRELESS",
"profileName" : "psk",
"ssid" : "psk",
"templateName" : "psk_example",
"layer2Security" : {
"securityMode" : "WPAWPA2",
"wpaEnabled" : true,
"wpaEncryptionProtocolAes" : true,
"wpaAuthenticationKeyManagementPsk" : true,
"wpaPresharedKey" : "MySharedKey",
"wpaPresharedKeyFormat" : "ASCII"
}
}
}
PUT op/wlanProvisioning/deployTemplate
The API is used to schedule a job to deploy a WLAN template onto a WLAN controller. There are following payload attributes that are related to PSK configuration:
- controllerConfig - contains controller speficic parameters applied to the deployed WLAN template
- wpaPresharedKey - when WLAN template is configured with controller-specific preshared key this should contain pre-shared key in ASCII or HEX format
- wpaPresharedKeyFormat - when WLAN template is configured with controller-specific preshared key this should contain pre-shared key formatt, ASCII or HEX
API request payload example
{
"deployWlanTemplateDTO" : {
"controllerName" : "WLC-10.1.1.1",
"templateName" : "psk_example",
"controllerConfig" : {
"wpaPresharedKey" : "MySharedKey",
"wpaPresharedKeyFormat" : "ASCII"
}
}
}
2. Step-by-Step Tutorial
Let's try it out and go through all the steps to provision a WLAN template to a controller.
Scenario 1: WLAN profile with pre-shared key
In this scenario we will create a WLAN template with a pre-shared key.
-
First we need to create a new WLAN template:
In this example I apply WLAN template to an interface group (it should already exist on the WLAN controller).
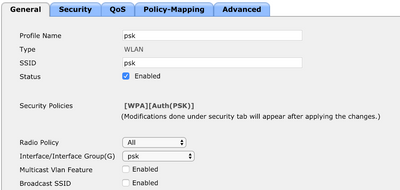
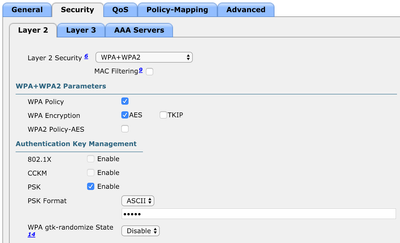
curl -X POST https://my_server/webacs/api/v4/op/wlanProvisioning/wlanTemplate \ -u user:password -H 'Content-Type: application/json' \ -d '{ "wlanTemplate" : { "adminStatus" : true, "interfaceName" : "psk", "interfaceType" : "INTERFACE", "lanType" : "WIRELESS", "profileName" : "psk", "ssid" : "psk", "templateName" : "psk_example", "layer2Security" : { "securityMode" : "WPAWPA2", "wpaEnabled" : true, "wpaEncryptionProtocolAes" : true, "wpaAuthenticationKeyManagementPsk" : true, "wpaControllerSpecificPresharedKeyEnabled" : false, "wpaPresharedKey" : "Pre-Shared Key", "wpaPresharedKeyFormat" : "ASCII" } } }'This creates the following WLAN templare on the Prime Infrastructure:
General tab:
And Layer 2 Security tab:
-
Then we deploy the WLAN template to a WLAN controller:
curl -X PUT https://my_server/api/v4/op/wlanProvisioning/deployTemplate \ -u user:password -H 'Content-Type: application/json' \ -d '{ "deployWlanTemplateDTO" : { "templateName" : "psk_example", "controllerName" : "my_controller" } }'API will reply with 200 OK and a job name in the response body:
{ "mgmtResponse": { "@requestUrl": "https://my_server/webacs/api/v4/op/wlanProvisioning/deployTemplate", "@responseType": "operation", "@rootUrl": "https://my_server/webacs/api/v4/op", "jobInformation": [ { "jobName": "NBI_DeployWlanTemplate_1548855452229_2", "jobType": "NBI_DeployWlanTemplate" } ] } }Status of the job can be tracked in the Job Dashboard in UI or via NBI API.
-
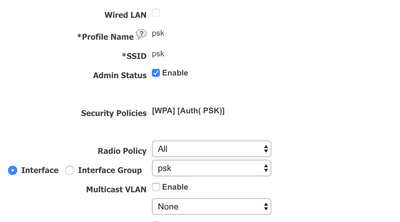
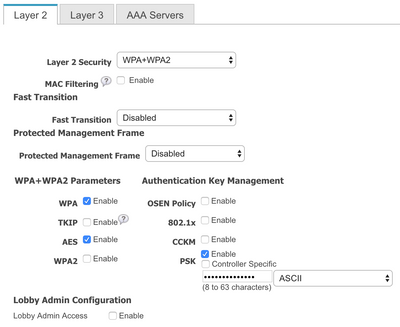
Check created WLAN on the controller
If the job is success then the WLAN profile should be provisioned to the controller:
General tab:
And Layer 2 Security tab:
Scenario 2: WLAN profile with controller specific pre-shared key
The only difference from the previous scenario is that the pre-shared key is specified per-controller at deploy time.
-
First we need to create a new WLAN template:
curl -X POST https://my_server/webacs/api/v4/op/wlanProvisioning/wlanTemplate \ -u user:password -H 'Content-Type: application/json' \ -d '{ "wlanTemplate" : { "adminStatus" : true, "interfaceName" : "psk", "interfaceType" : "INTERFACE", "lanType" : "WIRELESS", "profileName" : "psk", "ssid" : "psk", "templateName" : "psk_example", "layer2Security" : { "securityMode" : "WPAWPA2", "wpaEnabled" : true, "wpaEncryptionProtocolAes" : true, "wpaAuthenticationKeyManagementPsk" : true, "wpaControllerSpecificPresharedKeyEnabled" : true } } }' -
When we deploy the WLAN template to a WLAN controller it is required to provide controller-specific pre-shared key:
curl -X PUT https://my_server/api/v4/op/wlanProvisioning/deployTemplate \ -u user:password -H 'Content-Type: application/json' \ -d '{ "deployWlanTemplateDTO" : { "templateName" : "psk_example", "controllerName" : "my_controller", "controllerConfig" : { "wpaPresharedKey" : "0aafe7c7ec7e98e745d76b516e210248179890e7ca9f30c44f19b8ee9542afcf", "wpaPresharedKeyFormat" : "HEX" } } }'The pre-shared key and key format have to be passed for each controller where the WLAN template is provisioned to.
If you have any questions regarding this please leave a comment!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: