- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- Evaluating Cisco SDWAN Cloud onRamp for IaaS with dCloud
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
03-18-2019 10:07 AM - edited 03-31-2019 11:40 AM
Note: This lab utilizes the dCloud SD-WAN platform. You must schedule this ahead of time before proceeding below!
Cloud onRamp for IaaS extends the fabric of the Cisco SDWAN overlay network into public cloud instances, allowing branches with cEdge/vEdge routers to connect directly to public-cloud application providers. By eliminating the need for a physical Data Center, Cloud onRamp for IaaS improves the performance of SaaS applications.
Step 1: Configure Pre-requisites
The connection between the SDWAN overlay network and a public-cloud application is provided by two redundant vEdge Cloud or cEdge routers, which act together as a transit between the overlay network and the application. Using two routers to form the transit offers path resiliency to the public cloud. In addition, having redundant routers assists in brownout protection to improve the availability of public-cloud applications. Together, the two routers can remediate link degradation that might occur during brownouts. Cloud OnRamp for IaaS discovers any existing private cloud instances in cloud regions and allows you to select which of them to make available for the overlay network. In such a brownfield scenario, Cloud OnRamp for IaaS allows simple integration between legacy public-cloud connections and the Cisco SDWAN overlay network. You configure and manage Cloud OnRamp for IaaS through the vManage NMS server. A configuration wizard in the vManage NMS automates the provisioning and connections between public-cloud applications and the users of those applications at branches in the overlay network. Cloud OnRamp for IaaS works in conjunction with AWS virtual private clouds (VPCs) and Azure virtual networks (VNets).
All Cisco SD-WAN devices configured for the Cloud onRamp for IaaS service must meet these requirements:
- You must have at least two available vEdge Cloud or cEdge devices in the vManage device listing with generated bootstrap parameters (these will be used in the gateway VPC/VNET).
- You must create a configuration template (to be defined below) to attach to the two vEdge Cloud/cEdge devices. This template can be a CLI or Feature Template.
- The above template must define at least one Service Side VPN.
- In the case of Microsoft Azure, the host VNet Default Subnet and VNet Gateway Subnet must be part of host VNet Address Block. For example:
- Host VNet Address Block – 192.168.1.0/24
- Default Subnet – 192.168.1.240/28
- VNet Gateway Subnet – 192.168.1.0/28
- Each gateway VPC/VNet can accommodate 16 host VPCs/VNets (considering an IKE-IPsec limit of 64 sessions per vEdge Cloud)
- This feature is currently only supported on vEdges (cEdge support for AWS will come in March, 2019 with Azure and GCP support following in July, 2019 on CSR1KV).
1. We first need to create a template to attach to our new IaaS routers. Navigate to Configuration, Templates.
2. Click the Feature tab at the top of your screen, followed by the Add Template button:
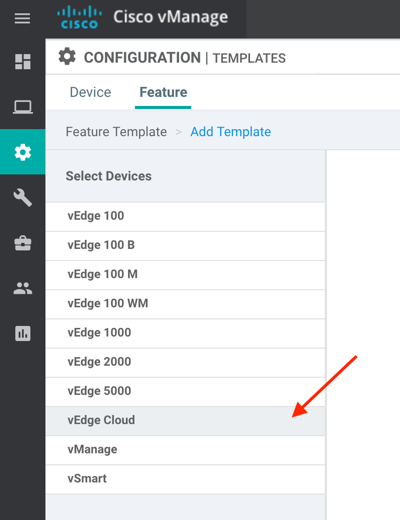
3. Click on vEdge Cloud:
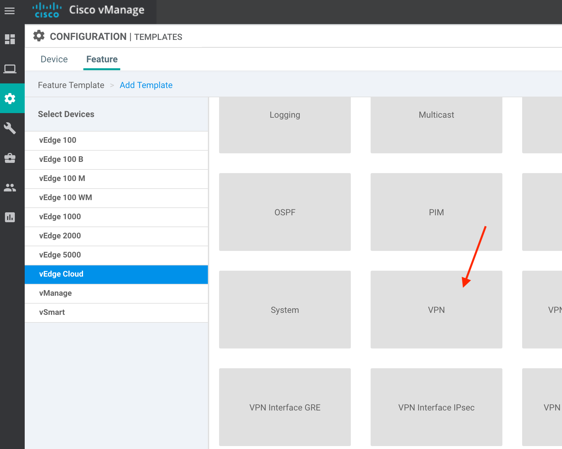
4. Click on the VPN button:
5. First, specify a name for your new Feature Template. In our case, since this template will define the parameters for our WAN VRF/VPN, we’ll use WAN-VPN0.
6. Next, specify a description for your template. We will use WAN – VPN0 Configuration.
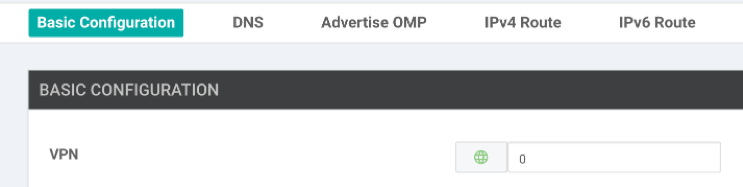
7. Modify the VPN field under the Basic Configuration heading. Set this field to Global and its value to 0:
8. At the bottom of the page, click the Save button to save the template.
9. Next, we will create an Interface Feature Template to define interface parameters (IP Addressing, NAT, speed, duplex, etc.). 10. Click the Add Template button.
11. Click on vEdge Cloud as the device type.
12. Click the VPN Interface Ethernet button.
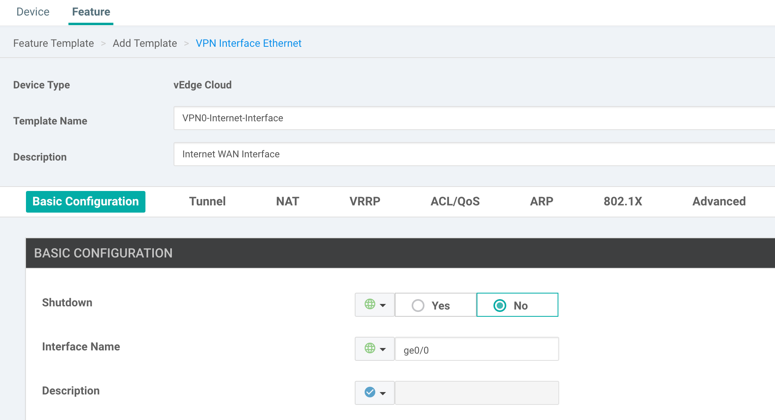
13. Provide a name for your interface template. This template will define parameters for the Internet-facing interface of the vEdge (ge0/0). Hence, we will name our template VPN0-Internet-Interface.
14. Provide a description for the template. We will use Internet WAN Interface.
15. Under the Basic Configuration heading, set the Shutdown option to Global and its value to No. This will ensure that the interface is physically enabled.
16. Set the Interface Name option to Global as well and its value to ge0/0. This value will ensure that the configuration push selects the correct interface to apply the configuration (note that this is case sensitive):
17. Under IPv4 Configuration, change the radio button to Dynamic.
18. Next, scroll down to the Tunnel section.
19. Set the Tunnel Interface option to Global and its value to On.
20. Set the Color option to Global and select biz-internet for the value.
21. Set the Restrict option to Global and its value to On.
22. Set the Control Connection option to Global and its value to On.
23. Click the Save button.
24. We have now finished configuring the WAN side templates of the router. Next, we will focus on the LAN side. Start by clicking on Add Template.
25. Choose vEdge Cloud as the device type.
26. Click the VPN button.
27. Name your template. Since this template will refer to Service VPN 10, we will use LAN-VPN10.
28. Provide a description for your template. We will use LAN – VPN10 Configuration.
29. Under Basic Configuration set the VPN parameter to Global and its value to 10.
30. Click on the Save button.
31. In the Feature Templates listing, click the Add Template button.
32. Choose vEdge Cloud as the device type.
33. Click the VPN Interface Ethernet button.
34. Provide a name for your template. This template will address the physical interface properties for our Service VPN 10 interface, so we will name ours VPN10-LAN-Interface.
35. Provide a description for your template. We will use VPN 10 LAN Interface Configuration.
36. Under Basic Configuration set the Shutdown parameter to Global and the value to No.
37. Set the Interface Name parameter to Global and the value to ge0/2.
38. Under IPv4 Configuration, change the radio button to Dynamic.
39. Click the Save button at the bottom.
40. Now it’s time to build your parent template. Click the Device tab in the upper left corner, or simply navigate to Configuration, Templates.
41. Click the Create Template button, followed by From Feature Template.
42. Choose vEdge Cloud as the Device Model.
43. Provide a name for your template. Here, we will use AWS-vEdge-Template.
44. Provide a description for your template. Here, we will use AWS Device Template.
45. Next, we need to fill in the blanks with the templates we created previously along with a few that were created for you.
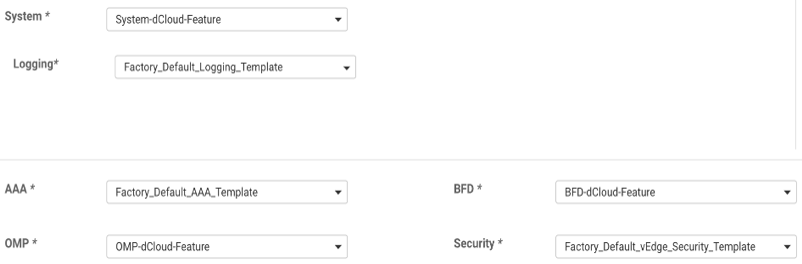
46. Under the Basic Information section, click the down arrow next to each parameter and set the following:
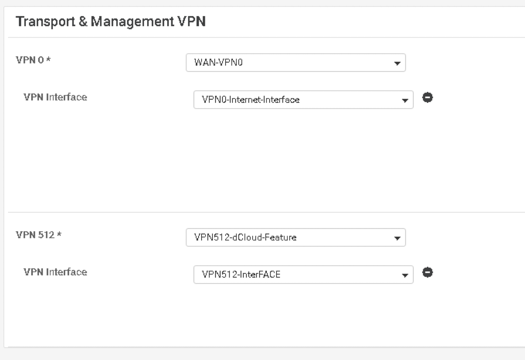
47. Scroll down to the Transport & Management VPN section and set the following parameters. You will likely need to click the icon to the right of the VPN512 Management VPN section:
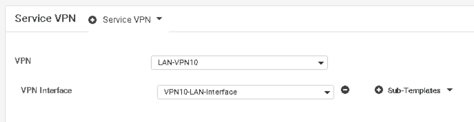
48. In the Service VPN section, click the plus sign to add a new Service VPN.
49. For your new Service VPN, click the button on the right to add a new VPN interface.
50. Configure your Service VPN as follows:
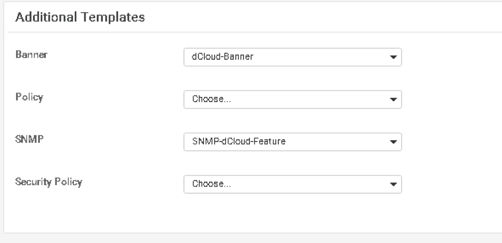
51. Lastly, under the Additional Templates section, set the following parameters:
52. Click the Create button.
53. Navigate to Configuration, Templates.
54. Click the ellipsis (three dots) to the right of your new AWS template, followed by the Attach button.
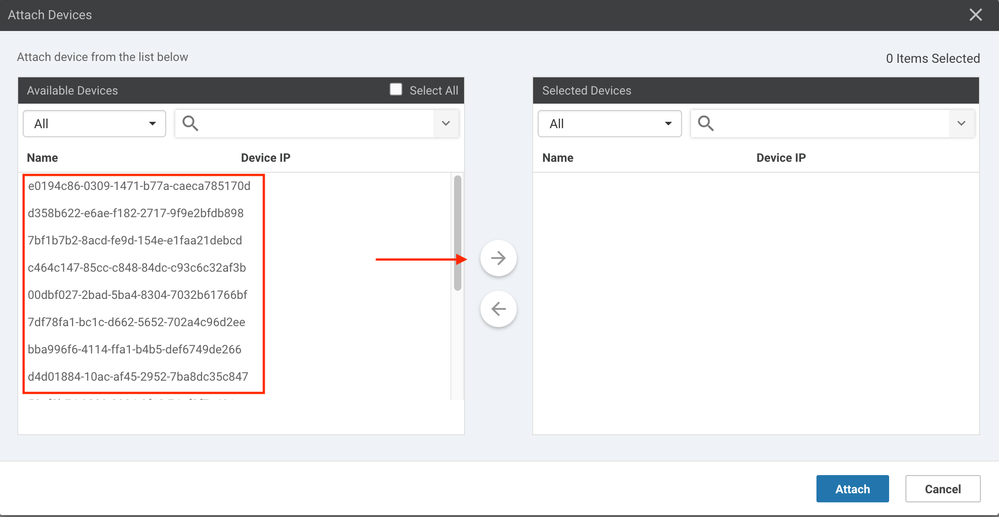
55. Select two available vEdge Cloud Chassis IDs from the window that appears and click the right arrow:
56. Click the Attach button.
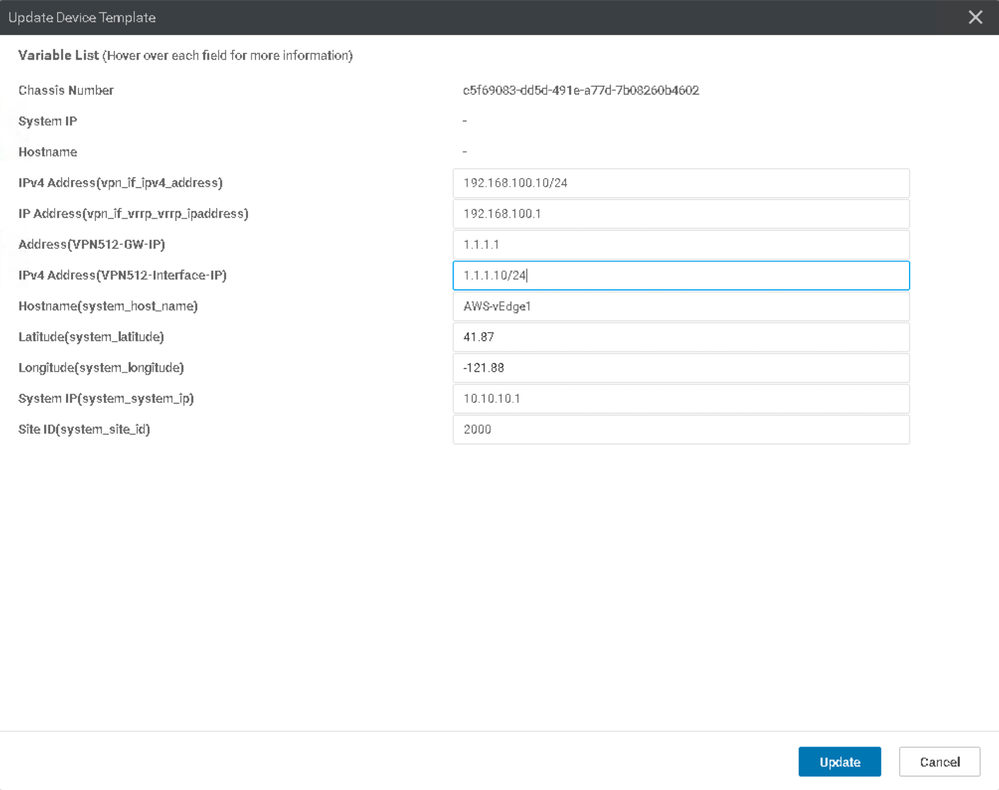
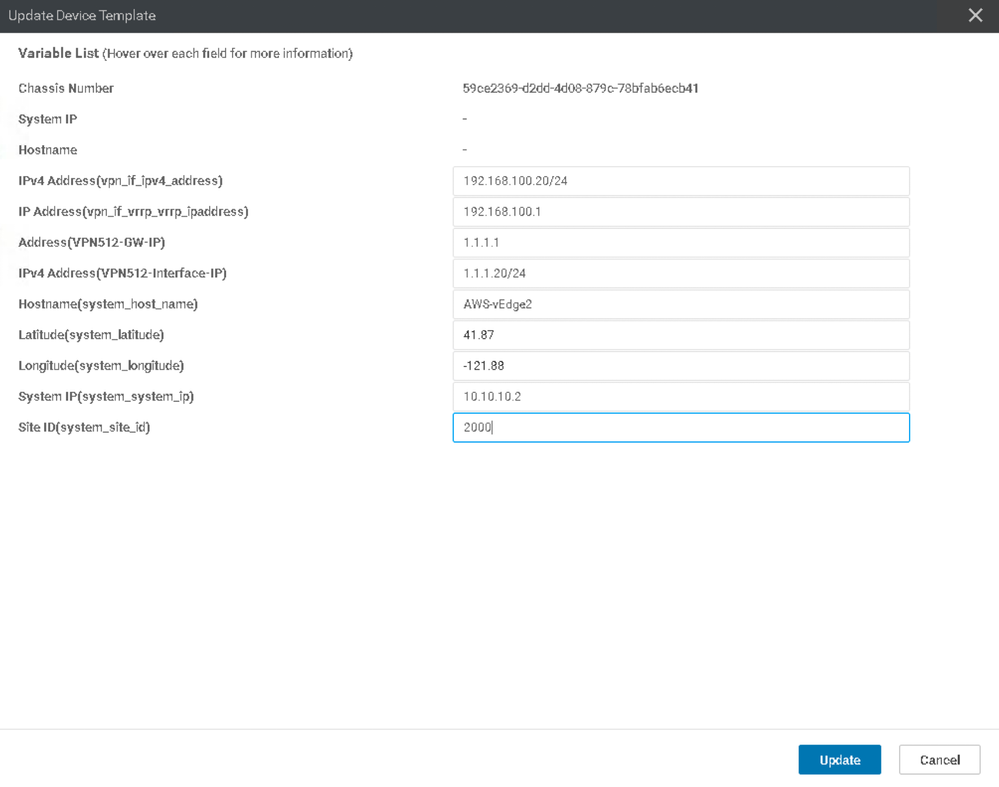
57. Since several components of the Device Template were set to Device Specific, we need to input these variables here. Click the ellipsis on the far right of each vEdge Cloud and input the following:
58. Click the Next button.
59. Click the Configure Devices button.
60. Click the Confirm checkbox, followed by the OK button.
Step 2: Enable Cloud onRamp for IaaS
1. Navigate to Configuration, Cloud onRamp.
2. Click the Add New Cloud Instance button.
3. Choose the AWS radio button.
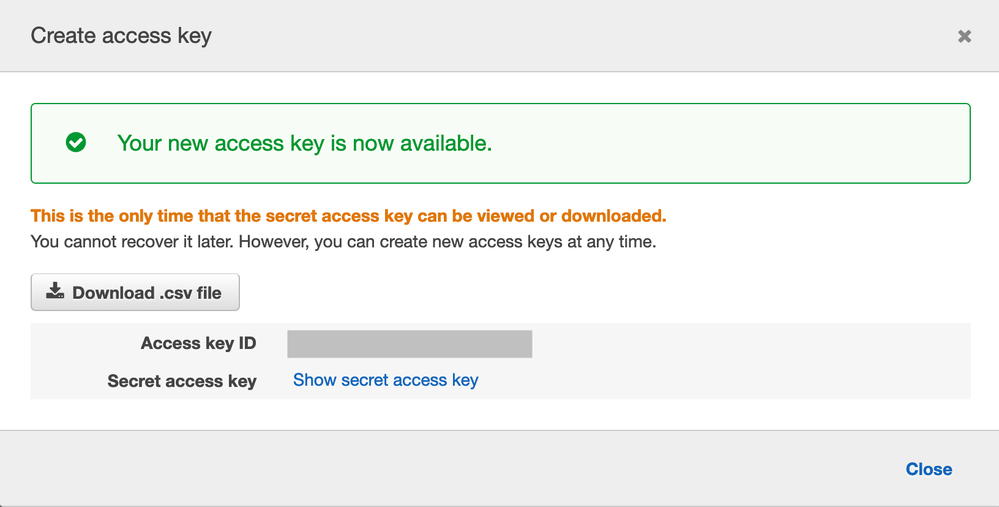
4. Enter the API Key and Secret Key obtained from your lab instructor. In a real-world deployment, you can obtain these items from the AWS Dashboard under the My Security menu. In this menu, click the Create Access Key button to generate a new API Key and Security Key:
5. Click the Login button.
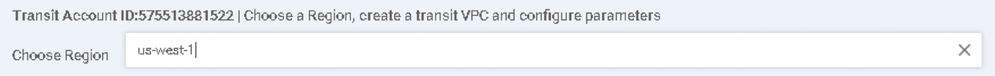
6. In the Choose Region dropdown, enter us-west-1:
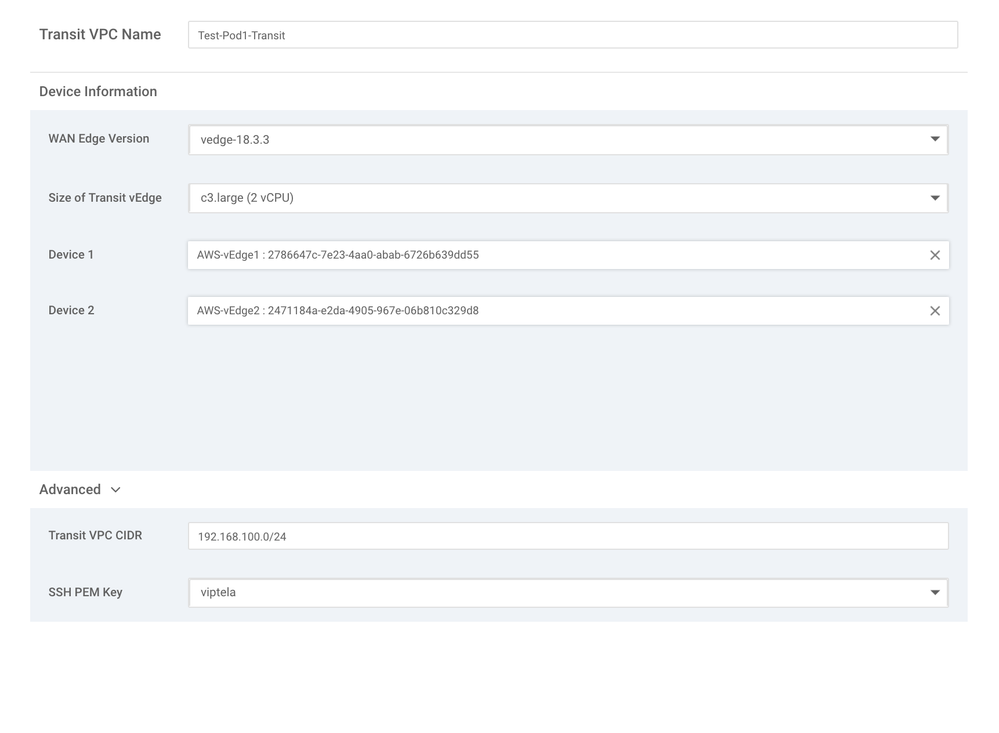
7. Name your Transit VPC. Here, we will use Test-Pod1-Transit.
8. Select the version of code to run on the device from the WAN Edge Version dropdown box. We will use vedge-18.3.3.
9. Select the CPU allocation for the vEdge(s) in the Size of Transit vEdge dropdown. We will use c3.large (2 vCPU) since our deployment is rather small.
10. For the Device 1 and Device 2 dropdown menus, select each of your vEdges allocated in the preceding steps.
11. (Optional) Under Advanced Options, set the Transit VPC CIDR value (the IP Range that will be used on the LAN interface of your vEdge) and select your PEM key (generated and uploaded to AWS).
12. Click the Proceed to Discovery and Mapping button to allow vManage to auto-discover the AWS Host VPCs.
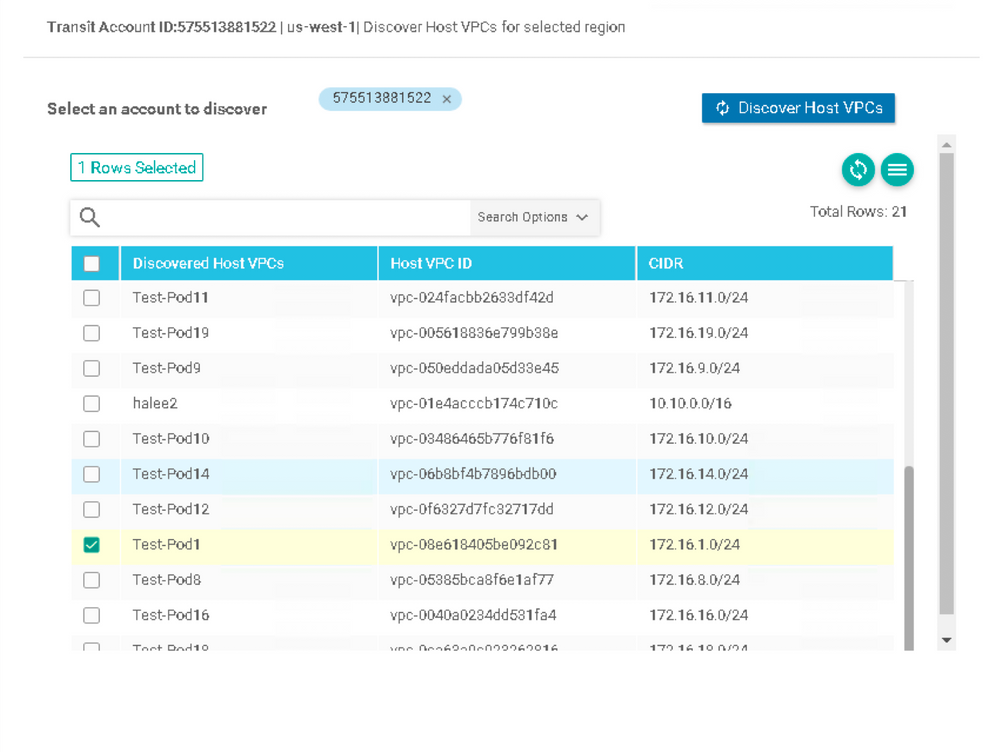
13. Choose an account from the dropdown menu (there should only be one in this lab) and click the Discovery Host VPCs button.
14. You will notice several "Test-PodX" VPCs in the output that follows. Choose the VPC that corresponds to your pod, as dictated by the instructor. Do not choose any other VPCs:
15. Click the Next button.
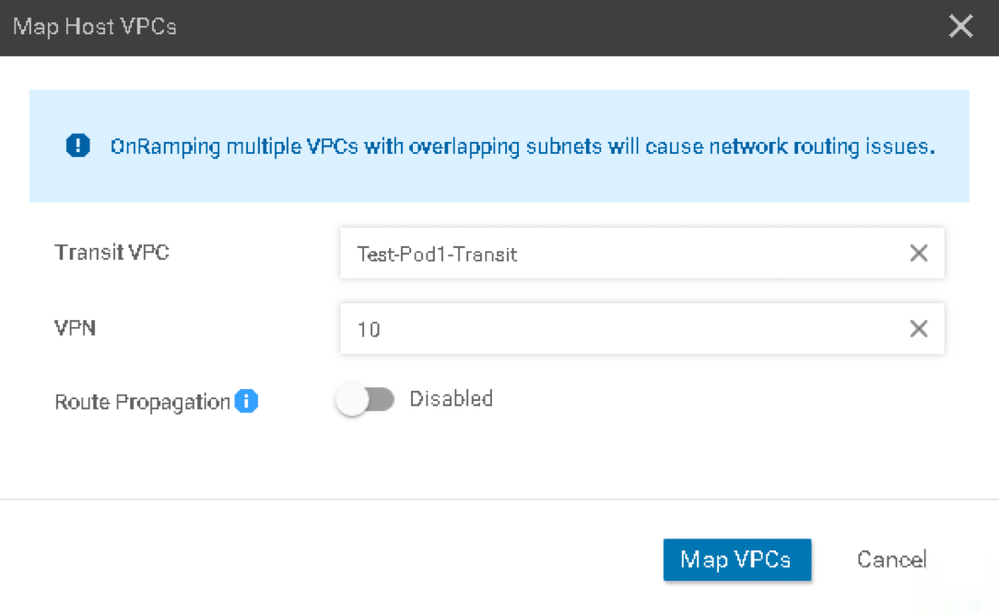
16. In the proceeding screen, ensure that your pod's VPC is still selected and click the Map VPCs button.
17. In the window that appears, your Transit VPC and VPN should be set for you. Review for correctness and click the Map VPCs button.
18. Click the Save and Complete button.
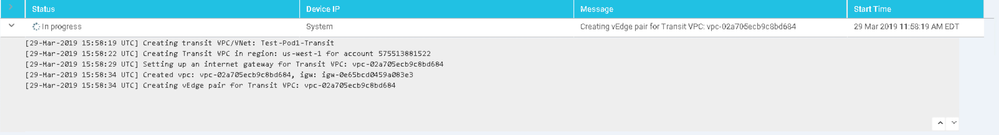
19. The task manager window will appear showing the status of the build. This process may take up to 45 minutes to complete!
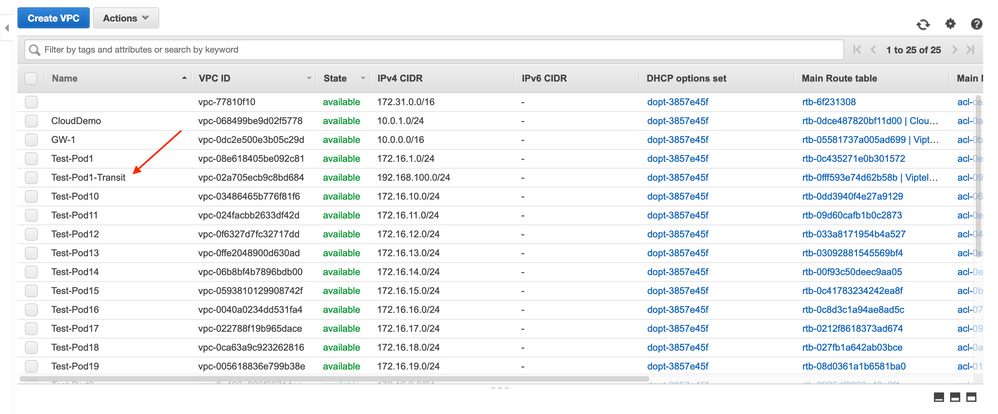
20. (AWS Dashboard access required) You can review the progress from the AWS dashboard in several places. To see the new Transit VPC that's being built, navigate to the Services menu, followed by VPCs. Click on the VPCs link in the window that appears.
21. The VPCs window should show your new Transit VPC being created:
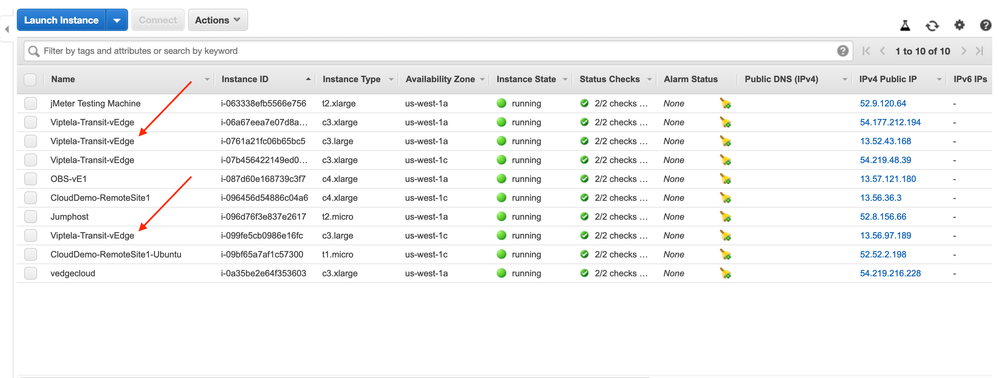
22. Your vEdge Clouds will be instantiated within this VPC and automatically begin route propagation with the VPCs that you mapped to (in this case, Test-Pod1 VPC - 172.16.1.0/24). To view the status of these vEdge Clouds, navigate to Services, followed by EC2. Click on the Running Instances link:
23. Once this process completes, you should be able to see your VPC routes (172.16.x.x/24) within the VPN10 routing table:
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: