- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- How to discover devices in SD-Access ( SDA )
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
10-15-2019 05:04 PM - edited 10-18-2019 02:11 AM
- Before you Begin - Verify the Install
- Pre-requisite
- New Device Discovery
- Discovery Profile
- Viewing the Topology
In Cisco DNA Center, the Discovery tool is used to find existing underlay devices using CDP or IP address ranges. When defining a discovery profile, users will use ssh and snmp credentials.
Before you Begin - Verify the Install
Use a web browser to DNAC GUI IP Address. Create an exception and accept the certificate to connect to the GUI.
- Step 1. Log into DNA Center using the “admin” user and the administrative passphrase provided during install to successfully log into DNA Center.
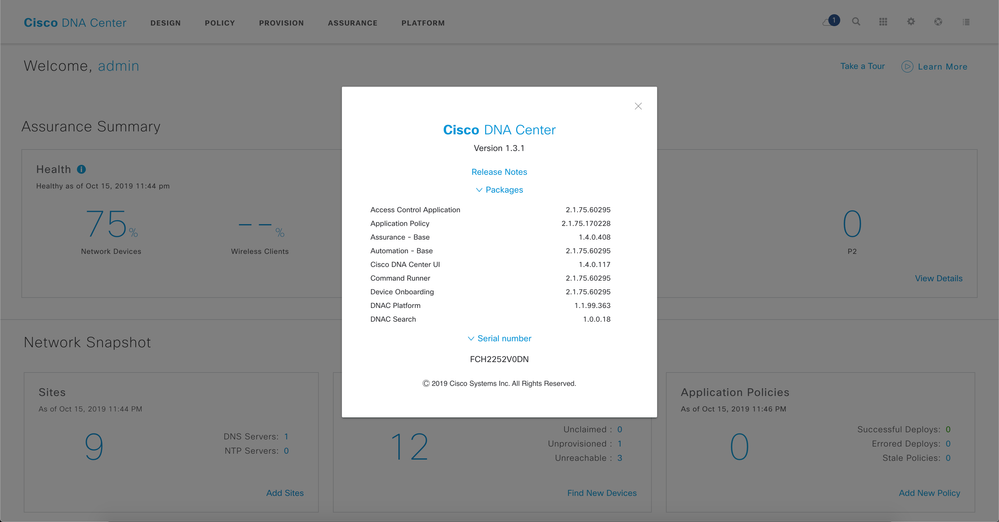
- Step 2. Upon logging in you will see the DNA Center dashboard. Click on the Globe and click on About.
Pre-requisite
Before creating a Discovery profile and running it, please take a moment to verify the underlay configuration of all your Catalyst switches and connectivity from Cisco DNAC CLI.
- There should not be any VRF (aside from Mgmt-vrf) or LISP configuration as this is pushed from Cisco DNAC to the devices while provisioning, after discovery and design.
- IP Addresses of loopbacks of all the switches
- Ping connectivity from Cisco DNAC CLI to loopback IP’s
- Verify if SSH is enabled on all the devices
- Verify if SNMP RW is configured
Verify VRF and LISP on all devices:
border-cp-3850#sh vrf
Name Default RD Protocols Interfaces
Mgmt-vrf <not set> ipv4,ipv6 Gi0/0
FE1-9300-03#sh vrf
Name Default RD Protocols Interfaces
Mgmt-vrf <not set> ipv4,ipv6 Gi0/0
FE1-9300-03#
FE2-9300-04#sh vrf
Name Default RD Protocols Interfaces
Mgmt-vrf <not set> ipv4,ipv6 Gi0/0
border-cp-3850#sho run | sec lisp
border-cp-3850#
FE1-9300-03#sho run | sec lisp
FE1-9300-03#
FE2-9300-04#sho run | sec lisp
FE2-9300-04#
Verify Loopback IP’s on all devices:
border-cp-3850#sh ip int brief | i Loopback0
Loopback0 3.3.3.5 YES manual up up
border-cp-3850#
FE1-9300-03#sh ip int brief | i Loopback0
Loopback0 3.3.3.9 YES manual up up
FE1-9300-03#
FE2-9300-04#sh ip int brief | i Loopback0
Loopback0 3.3.3.13 YES manual up up
FE2-9300-04#
Check Connectivity to all the loopbacks from Cisco DNAC.
root@maglev-master-10-195-180-191:~# ping -c 2 3.3.3.5
PING 3.3.3.5 (3.3.3.5) 56(84) bytes of data.
64 bytes from 3.3.3.5: icmp_seq=1 ttl=254 time=2.64 ms
64 bytes from 3.3.3.5: icmp_seq=2 ttl=254 time=1.34 ms
--- 3.3.3.5 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 1.344/1.993/2.642/0.649 ms
root@maglev-master-10-195-180-191:~# ping -c 2 3.3.3.9
PING 3.3.3.9 (3.3.3.9) 56(84) bytes of data.
64 bytes from 3.3.3.9: icmp_seq=1 ttl=252 time=0.523 ms
64 bytes from 3.3.3.9: icmp_seq=2 ttl=252 time=0.726 ms
--- 3.3.3.9 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1014ms
rtt min/avg/max/mdev = 0.523/0.624/0.726/0.104 ms
root@maglev-master-10-195-180-191:~# ping -c 2 3.3.3.13
PING 3.3.3.13 (3.3.3.13) 56(84) bytes of data.
64 bytes from 3.3.3.13: icmp_seq=1 ttl=252 time=0.668 ms
64 bytes from 3.3.3.13: icmp_seq=2 ttl=252 time=0.495 ms
--- 3.3.3.13 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1019ms
rtt min/avg/max/mdev = 0.495/0.581/0.668/0.089 ms
Verify if SSH is enabled on all the devices
border-cp-3850#sh run | i ssh
ip ssh time-out 90
ip ssh authentication-retries 4
ip ssh version 2
border-cp-3850#sh run | b vty
line vty 0 4
password lab
login local
transport input all
transport output all
line vty 5 15
password lab
login local
transport input all
transport output all
Verify if SNMP is enabled on all the devices
border-cp-3850#sh run | i snmp
snmp-server community pbagga RW
FE1-9300-03#sh run | i snmp
snmp-server community pbagga RW
FE2-9300-04#sh run | i snmp
snmp-server community pbagga RW
New Device Discovery
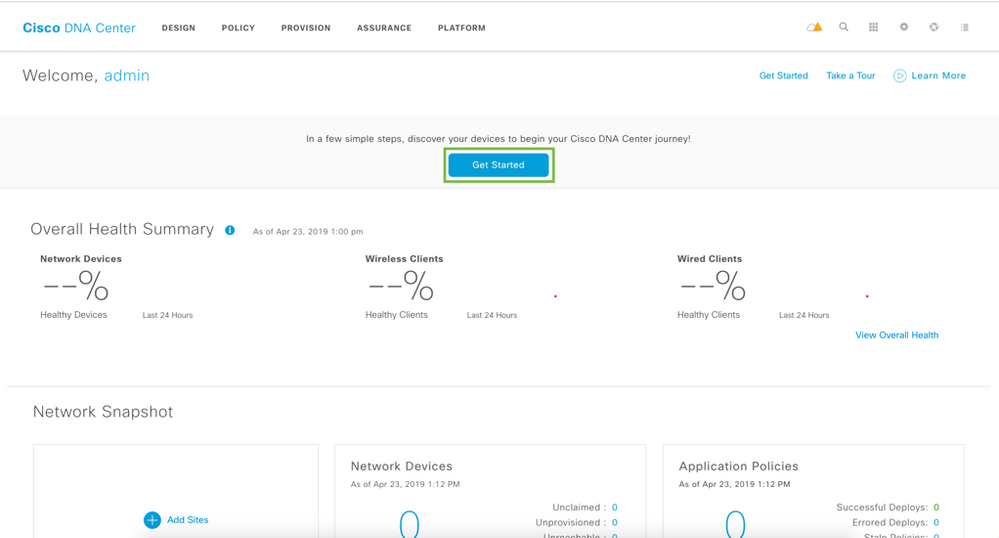
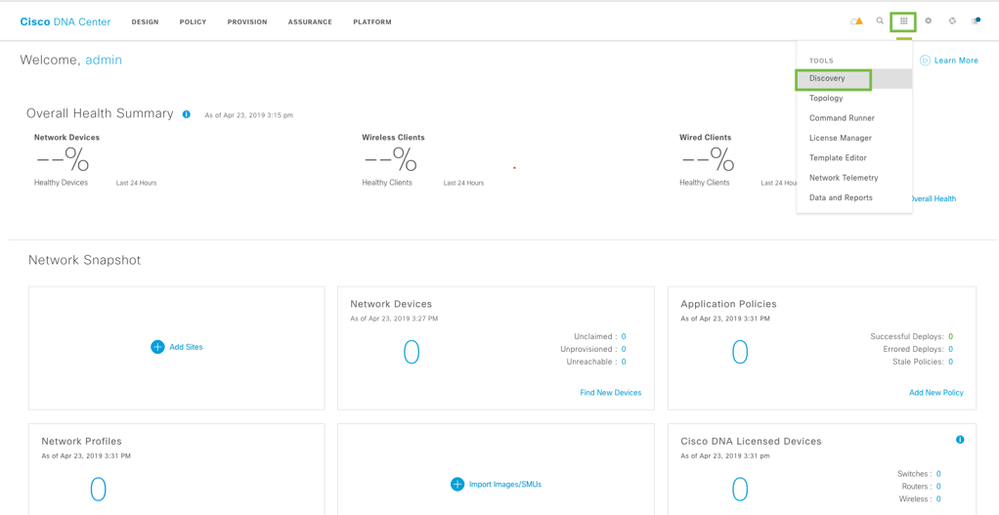
Please click on “Get Started” from the home page by accessing the tools from the home page. Or click on the Tools on the top right > Discovery to go to Discovery Dashboard.
You will be taken to the next step. Click on Get Started again.
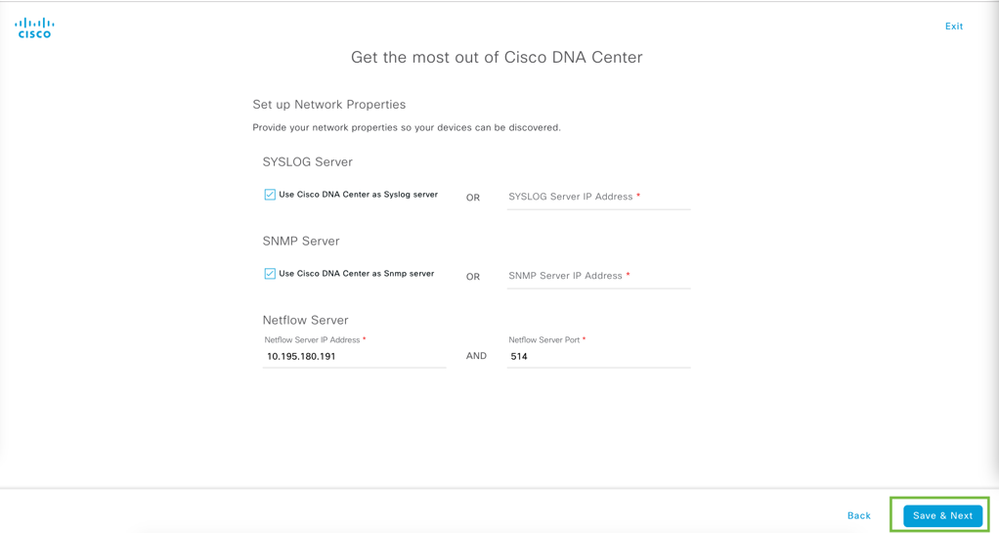
Configure syslog, snmp, and Netflow Server. By Default Cisco DNAC is your syslog and SNMP server. You can either select an external server for Netflow or Cisco DNAC IP for that too. The port for Netflow server is 514.
Once completed, click Save & Next on bottom right.
Click on the Tools on the top right > Discovery to go to Discovery Dashboard.
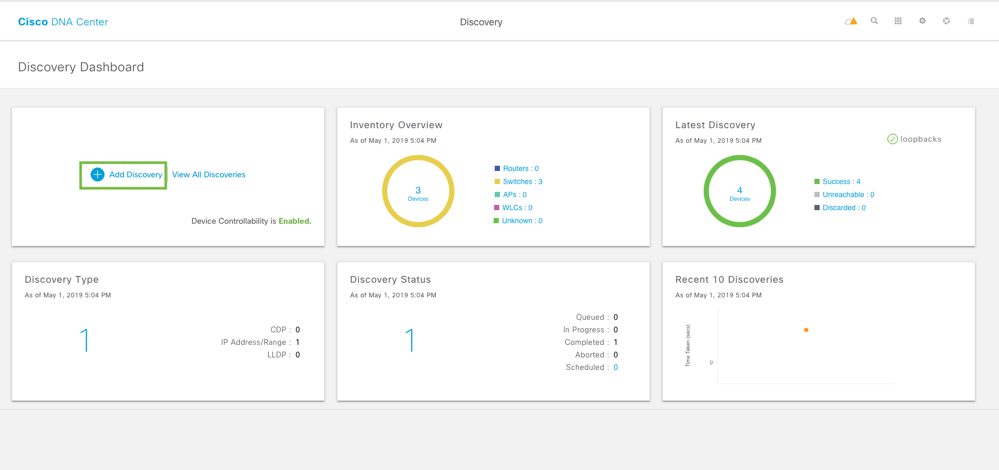
In the discovery dashboard, click on Add Discovery on top left.
Discovery Profile
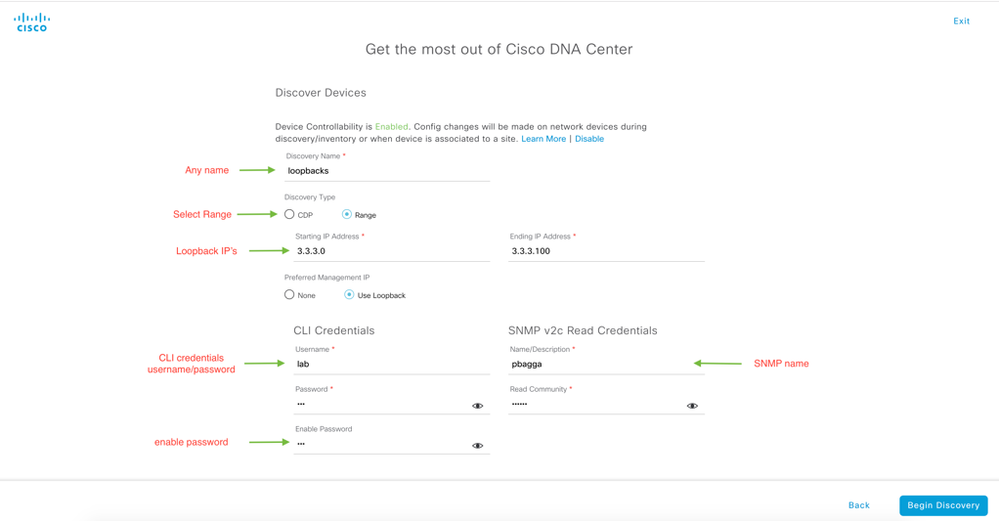
In the New Discovery Profile, provide the name of discover, IP Address Range, CLI Credentials, Enable Password, SNMP Credentials and click on Begin Discovery on the bottom right.
NOTE: If you do not select Range, then you will discover all devices. Please be sure to select Range.
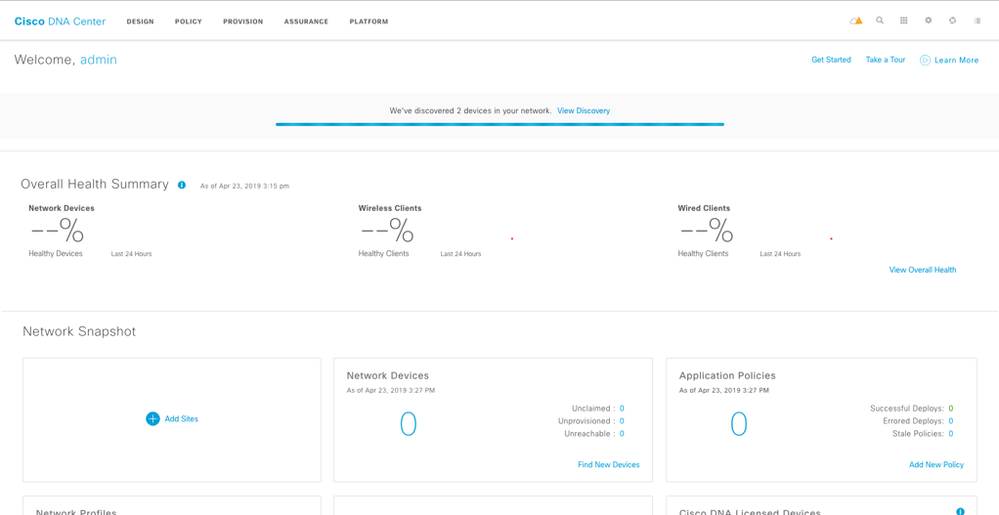
Cisco DNAC starts discovery and mentions how many devices it has discovered.
To go to discovery, click on Tools on top right and go to Discovery.
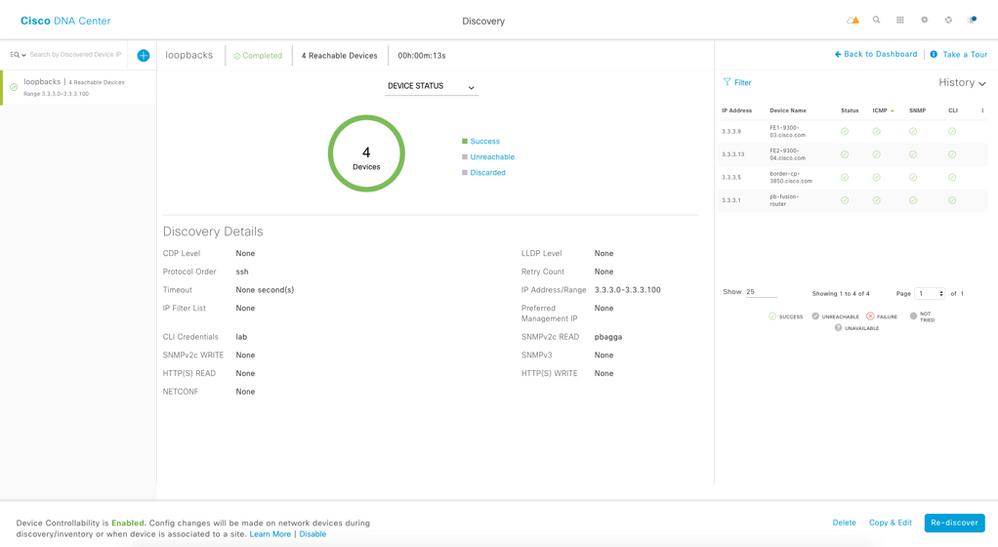
This will take us to the Discovery dashboard where overview of discovered devices can be seen. All the switches should be in healthy state and successful.
NOTE: At this point you can proceed to the Design section.
- Step 3. By default, Cisco DNA Center will make a few changes to the discovered devices. Please have another look at one of the access switch configurations to see the changes made.
FE1-9300-03#sh run | b IPDT
IPDT (IP Device Tracking) is used to keep track of connected hosts. |
device-tracking policy IPDT_MAX_10
limit address-count 10
no protocol udp
tracking enable
!
!
crypto pki trustpoint SLA-TrustPoint
enrollment pkcs12
revocation-check crl
!
crypto pki trustpoint TP-self-signed-312368764
enrollment selfsigned
Secure connection to Cisco DNA Center |
subject-name cn=IOS-Self-Signed-Certificate-312368764
revocation-check none
rsakeypair TP-self-signed-312368764
!
crypto pki trustpoint DNAC-CA
enrollment mode ra
enrollment terminal
usage ssl-client
revocation-check crl none
!
!
crypto pki certificate chain SLA-TrustPoint
certificate ca 01
30820321 30820209 A0030201 02020101 300D0609 2A864886 F70D0101 0B050030
32310E30 0C060355 040A1305 43697363 6F312030 1E060355 04031317 43697363
6F204C69 63656E73 696E6720 526F6F74 20434130 1E170D31 33303533 30313934
3834375A 170D3338 30353330 31393438 34375A30 32310E30 0C060355 040A1305
43697363 6F312030 1E060355 04031317 43697363 6F204C69 63656E73 696E6720
526F6F74 20434130 82012230 0D06092A 864886F7 0D010101 05000382 010F00
IPDT (IP Device Tracking) is used to keep track of connected hosts. This is done through a unicasted ARP probe. This is used for multiple services. For SD-Access, this is used for Cisco TrustSec, MAB and 802.1x session manager.
NOTE: Device tracking is not added to ports with end hosts physically attached. Here, port G1/0/1 and G1/0/11 have hosts connected to them.
- Step 4. Please save the Border, Control Plane, and Edge node configurations.
border-cp-3850#copy running-config startup-config
Destination filename [startup-config]?
Building configuration...
[OK]
FE1-9300-03#copy running-config startup-config
Destination filename [startup-config]?
Building configuration...
[OK]
FE2-9300-04#copy running-config startup-config
Destination filename [startup-config]?
Building configuration...
[OK]
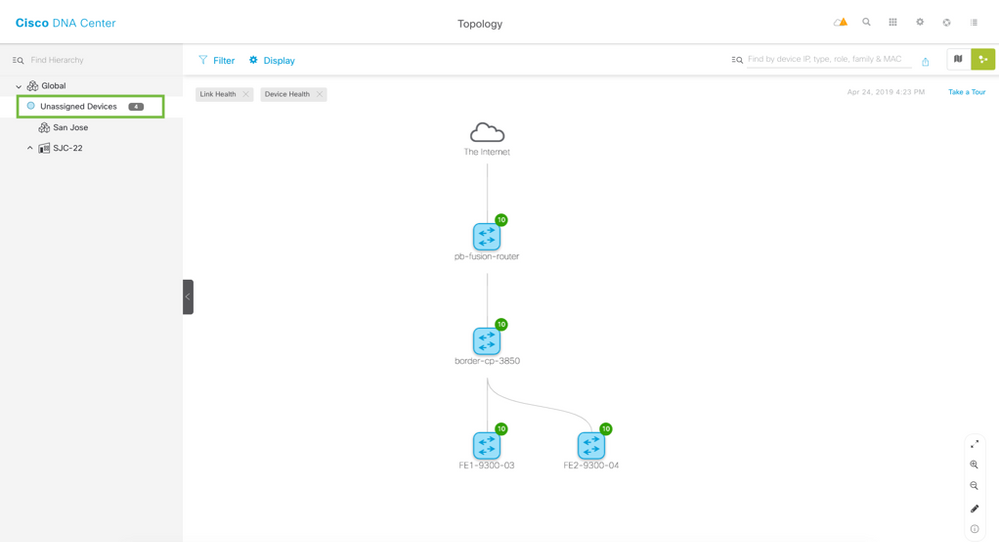
Viewing the Topology
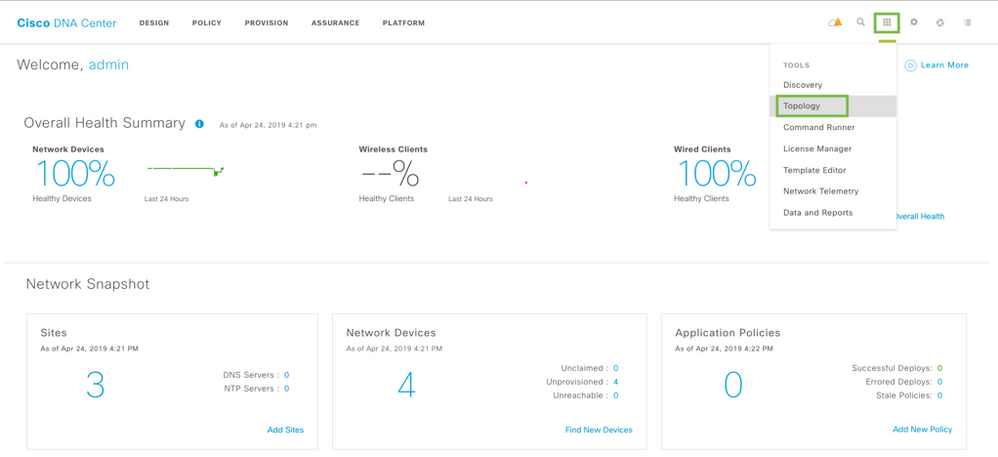
Once you have verified the Device Roles are correct use the Topology application to view the network.
Use the Apps button to open the Topology app to view the devices. You can use the zoom feature in the lower right to zoom in on the map. Feel free to interact with the Topology map further to get a feel for it. Once done please continue to the Design section.
Click on Unassigned Devices on the top left to check the Topology.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: