Dear community,
I have problems with a simply preshared key based IPsec tunnel. Basically it actually runs perfect for 36 hours, well 2 times 64800 seconds and not only for 86400 as I assumed before. Afterwards it goes down.
Reloading the router is the fastest way to get the tunnel up again.
(I currently playing with e.g. lifetimes, keepalives and currently "set security-association lifetime seconds 64800" have been added for testing on both sites after testing with default values.)
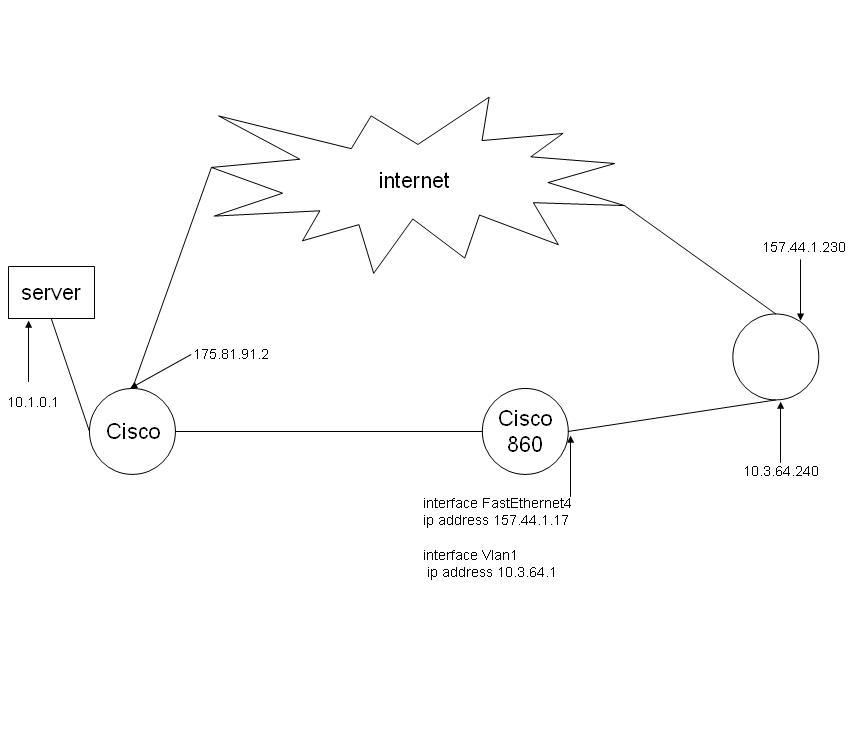
boot system flash c860-universalk9-mz.152-3.T1.bin
!
no ip cef
!
crypto isakmp policy 10
encr aes
group 14
!
crypto isakmp policy 50
encr 3des
hash md5
authentication pre-share
crypto isakmp key PASSWORD address 175.81.91.2
crypto isakmp identity dn
crypto isakmp invalid-spi-recovery
!
!
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
!
!
!
crypto map SDM_CMAP_1 1 ipsec-isakmp
set peer 175.81.91.2
set security-association lifetime seconds 64800
set transform-set ESP-3DES-SHA
match address 100
!
interface FastEthernet4
ip address 157.44.1.17 255.255.254.0
duplex auto
speed auto
crypto map SDM_CMAP_1
!
interface Vlan1
ip address 10.3.64.1 255.255.255.0
no ip redirects
ip tcp adjust-mss 1452
!
ip route 0.0.0.0 0.0.0.0 157.44.1.230 //to public/internet
ip route 10.3.64.0 255.255.192.0 10.3.64.240 //internal network which should is connected to the tunnel
!
access-list 100 permit ip 10.3.64.0 0.0.63.255 10.1.0.0 0.0.255.255
no cdp run
- So, as I already told, the tunnel is up and running for as long as the lifetime is > 0:
# show crypto session detail
Crypto session current status
Code: C - IKE Configuration mode, D - Dead Peer Detection
K - Keepalives, N - NAT-traversal, T - cTCP encapsulation
X - IKE Extended Authentication, F - IKE Fragmentation
Interface: FastEthernet4
Uptime: 00:02:54
Session status: UP-ACTIVE
Peer: 175.81.91.2 port 500 fvrf: (none) ivrf: (none)
Phase1_id: 175.81.91.2
Desc: (none)
IKEv1 SA: local 157.44.1.17/500 remote 175.81.91.2/500 Active
Capabilities:(none) connid:2001 lifetime:23:56:52
IPSEC FLOW: permit ip 10.3.64.0/255.255.192.0 10.1.0.0/255.255.0.0
Active SAs: 2, origin: crypto map
Inbound: #pkts dec'ed 32 drop 0 life (KB/Sec) 4167467/64625
Outbound: #pkts enc'ed 31 drop 0 life (KB/Sec) 4167468/64625
- I can happily ping server on the other site of the tunnel:
# ping 10.1.0.1 source Vlan 1
#show crypto session detail
Crypto session current status
Code: C - IKE Configuration mode, D - Dead Peer Detection
K - Keepalives, N - NAT-traversal, T - cTCP encapsulation
X - IKE Extended Authentication, F - IKE Fragmentation
Interface: FastEthernet4
Session status: UP-NO-IKE
Peer: 175.81.91.2 port 500 fvrf: (none) ivrf: (none)
Desc: (none)
Phase1_id: (none)
IPSEC FLOW: permit ip 10.3.64.0/255.255.192.0 10.1.0.0/255.255.0.0
Active SAs: 2, origin: crypto map
Inbound: #pkts dec'ed 12195 drop 0 life (KB/Sec) 4324875/35554
Outbound: #pkts enc'ed 12193 drop 0 life (KB/Sec) 4324875/35554
- After 2 x 64800 seconds, tunnel is down:
show crypto session detail
Crypto session current status
Code: C - IKE Configuration mode, D - Dead Peer Detection
K - Keepalives, N - NAT-traversal, T - cTCP encapsulation
X - IKE Extended Authentication, F - IKE Fragmentation
Interface: FastEthernet4
Session status: DOWN-NEGOTIATING
Peer: 175.81.91.2 port 500 fvrf: (none) ivrf: (none)#
Desc: (none)
Phase1_id: (none)
IKEv1 SA: local 157.44.1.17/500 remote 175.81.91.2/500 Inactive
Capabilities:D connid:2069 lifetime:0
IPSEC FLOW: permit ip 10.3.64.0/255.255.192.0 10.1.0.0/255.255.0.0
Active SAs: 0, origin: crypto map
Inbound: #pkts dec'ed 16687 drop 0 life (KB/Sec) 0/0
Outbound: #pkts enc'ed 16686 drop 0 life (KB/Sec) 0/0
show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
157.44.1.17 175.81.91.2 MM_KEY_EXCH 2069 ACTIVE
IPv6 Crypto ISAKMP SA
After that, I actually have to do a "reload" after which everything is working fine again, for the next 2x 64800 seconds