- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- Teleworker and Microbranch Solutions - IOS-XE
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
03-24-2020 11:18 AM - edited 07-08-2020 05:52 AM
- Goal
- Supported Platforms
- Supported Router Models and Required Licenses
- Documentation
- Prerequisites
- Use Case#1 (Site-to-Site and DMVPN tunnel)
- Step-By-Step Configuration
- SIM Installation and Verification
- Option1: Site-to-Site VPN (with routable public IP)
- Verification
- Option 2: Dynamic Multipoint VPN (with private IP from Service Provider)
- Verification
- WiFi Configuration1: Using router CLI (ME Mode)
- Verification
- Use Case #2 (using PnP server)
- Step-By-Step Configuration
- Add Devices to Smart Account
- NSO Server Requirements
- WiFi Configuration 2: Zero-Touch Deployment (ME Mode)
- Use Case #3 (boot strap using USB/bootflash)
- WiFi Configuration 3: Zero-Touch Deployment - External WLC (CAPWAP Mode)
Goal
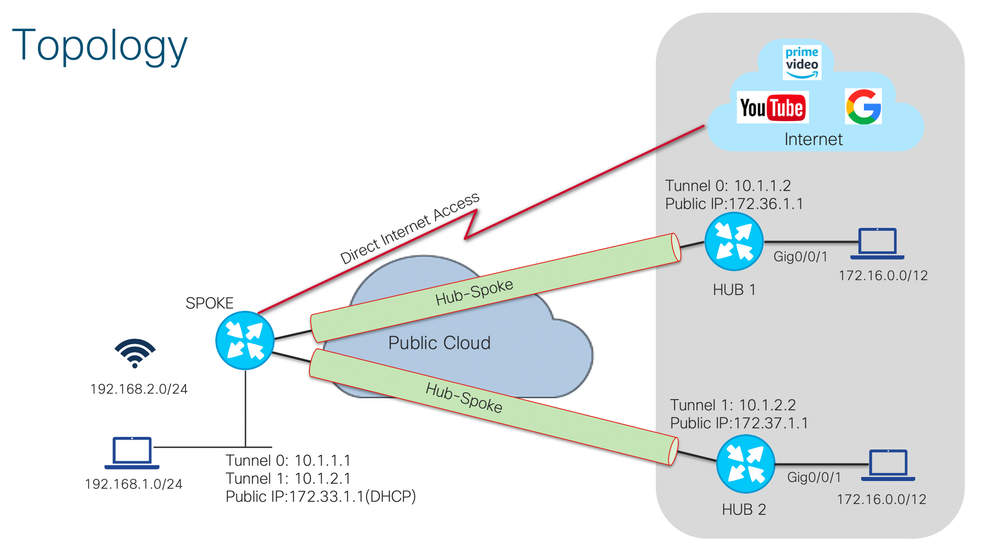
To provide a solution to quickly setup a pop-up site that supports WiFi and provides instant internet access using LTE as a transport.
Supported Platforms
ISR 1K series routers with LTE and WiFi capability.
Supported Router Models and Required Licenses
| PID | License Requirements |
Image Required |
| C1121X-8PLTEPWY* with P-LTEAP18-GL** | SL-1K-8P-SEC-SV, FL-1K-8P-HSEC-SV, FL-VPERF-8P200-SV | 16.12 |
| C1109-4PLTE2PW*** with 2x P-LTEA | SL-1100-4P-SEC, FL-VPERF-4P-100 | 16.12 |
| C1117-4PW | FL-1100-4P-HSEC, SL-1100-4P-SEC | 17.4 (Nov) |
| C1111-4PW | FL-1100-4P-HSEC, SL-1100-4P-SEC | 17.4 (Nov) |
| C1111-8PW | SL-1100-8P-SEC, FL-1100-8P-HSEC | 17.4 (Nov) |
Documentation
ISR 1K datasheet: https://www.cisco.com/c/en/us/products/collateral/routers/1000-series-integrated-services-routers-isr/datasheet-c78-739512.html
ISR LTE configuration guide: https://www.cisco.com/c/en/us/td/docs/routers/access/interfaces/NIM/software/configuration/guide/4GLTENIM_SW.html
ISR ME configuration guide: https://www.cisco.com/c/en/us/td/docs/routers/access/1100/software/configuration/xe-16-6/cisco_1100_series_swcfg_xe_16_6_x/cisco_1100_series_swcfg_chapter_01010.html
Prerequisites
ISR using CAT18 LTE PIM must be running IOS-XE version 16.12.1 or above. ISR using built in LTE must be running IOS-XE version 16.6.1 or above
ISR - https://software.cisco.com/download/home/286315006/type/282046477/release
CAT18 LTE PIM - https://software.cisco.com/download/home/286288566
Use Case#1 (Site-to-Site and DMVPN tunnel)
Step-By-Step Configuration
SIM Installation and Verification
Insert the SIM card in slot 0 of CAT18 LTE PIM or directly into the integrated SIM slot on the C1111/1109 routers.Router#show cellular 0/2/0 hardware //check for Carrier information Modem Firmware Version = 32.00.114 Host Firmware Version = 32.00.004_2 Device Model ID = LM960A18 International Mobile Subscriber Identity (IMSI) = 310260154954279 International Mobile Equipment Identity (IMEI) = 358347100003170 Integrated Circuit Card ID (ICCID) = 8901260151749542798 Mobile Subscriber Integrated Services Digital Network-Number (MSISDN) = 18574157134 Modem Status = Modem Online Current Modem Temperature = 30 deg C PRI version = 1023, Carrier = Generic OEM PRI version = 32101006
Check signal strength (RSSI) and Radio Access Technology (RAT). The RSSI is based on various factors (i.e., range from cellular tower, usage density in location, etc.) and can range from -30dBm (Excellent quality) to -90dBm (Unusable). Check to see if the RAT matches the data plan purchased from your cellular carrier.
Router#show cellular 0/2/0 radio Radio power mode = Online LTE Rx Channel Number(PCC) = 926 LTE Tx Channel Number(PCC) = 18926 LTE Band = 66 LTE Bandwidth = 5 MHz Current RSSI = -82 dBm Current RSRP = -112 dBm Current RSRQ = -16 dB Current SNR = -1.5 dB Physical Cell Id = 55 Number of nearby cells = 2 Idx PCI (Physical Cell Id) -------------------------------- 1 55 2 57 Radio Access Technology(RAT) Preference = AUTO Radio Access Technology(RAT) Selected = LTE
Option1: Site-to-Site VPN (with routable public IP)
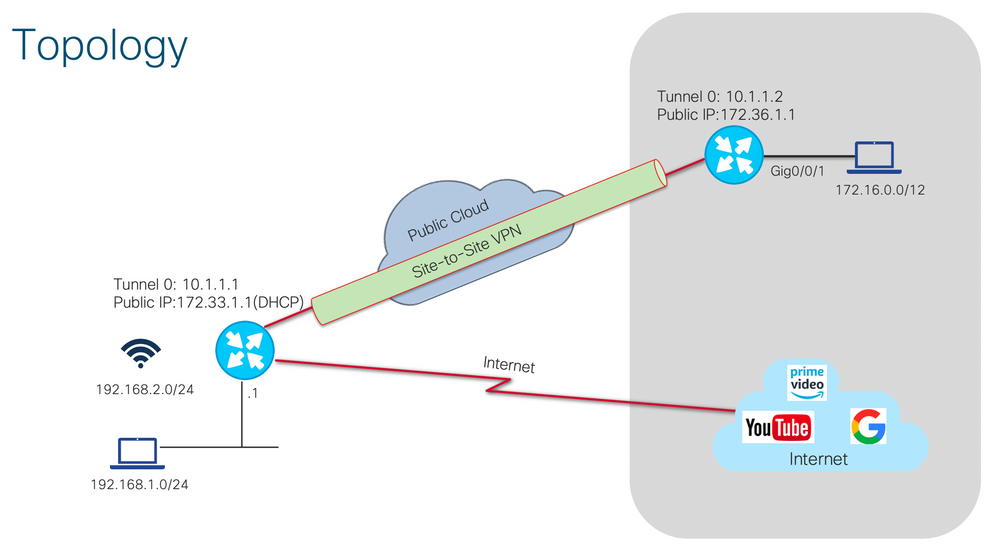
PSK Tunnel Configuration
The procedure in this section describes how to use a pre-shared key (PSK) in order to configure the tunnels in this network environment.
Left-Router
1. Configure the Internet Key Exchange version 2 (IKEv2) keyring:
crypto ikev2 keyring mykeys peer Right-Router address 172.36.1.1 pre-shared-key Cisco123
2. Configure IKEv2 proposal and policy
crypto ikev2 proposal S2S_Proposal encryption aes-cbc-256 integrity sha256 group 15 crypto ikev2 policy S2S-Policy proposal S2S_Proposal
3.Reconfigure the IKEv2 profile in order to:
- match on the IKE ID
- set the authentication methods for local and remote
- reference the keyring listed in the previous step
crypto ikev2 profile S2S_IKEv2_PROFILE match identity remote address 172.36.1.1 255.255.255.255 authentication remote pre-share authentication local pre-share keyring local mykeys dpd 60 2 on-demand
4. Configure IPsec Transform Set
crypto ipsec transform-set S2S_Set esp-aes 256 esp-sha256-hmac mode tunnel
5. Reconfigure the IPsec profile in order to reference the default IKEv2 profile:
crypto ipsec profile S2S_IPSEC_Profile set transform-set S2S_Set set ikev2-profile S2S_IKEv2_PROFILE ! interface Tunnel0 ip address 10.1.1.1 255.255.255.0 tunnel source <cellular slot/sub-slot/port> tunnel destination 172.36.1.1 tunnel protection ipsec profile S2S_IPSEC_Profile !
6. Configure the LAN and WAN interfaces:
interface <cellular slot/sub-slot/port> description WAN ip address dhcp ip nat outside ! interface GigabitEthernet0/0/0 description LAN ip address 192.168.1.1 255.255.255.0 ip nat inside vlan 2 name Wireless ! interface Wlan-GigabitEthernet0/1/8 description AP switchport mode access switchport access vlan 2 no shut ! interface Vlan 2 description Wireless ip address 192.168.2.1 255.255.255.0 ip nat inside ! ip route 172.16.0.0 255.240.0.0 10.1.1.2 name DC_Subnets ip route 0.0.0.0 0.0.0.0 <cellular slot/sub-slot/port> dhcp ip access-list extended NAT deny ip 192.168.1.0 0.0.0.255 172.16.0.0 0.15.255.255 deny ip 192.168.2.0 0.0.0.255 172.16.0.0 0.15.255.255 permit ip any any ip nat inside source list NAT interface GigabitEthernet0/0/2 overload
Right-Router
Repeat the steps from the Left-Router configuration, but with these necessary changes:
crypto ikev2 keyring mykeys peer Left-Router address 172.33.1.1 pre-shared-key Cisco123 ! crypto ikev2 proposal S2S_Proposal encryption aes-cbc-256 integrity sha256 group 15 crypto ikev2 policy S2S-Policy proposal S2S_Proposal ! crypto ikev2 profile S2S_IKEv2_PROFILE match identity remote address 172.33.1.1 255.255.255.255 authentication remote pre-share authentication local pre-share keyring local mykeys dpd 60 2 on-demand ! interface Tunnel0 ip address 10.1.1.1 255.255.255.0 tunnel source GigabitEthernet0/0/0 tunnel destination 172.33.1.1 tunnel protection ipsec profile S2S_IPSEC_Profile ! interface GigabitEthernet0/0/0 description WAN ip address 172.36.1.1 255.255.255.252 ! interface GigabitEthernet0/0/1 description LAN ip address 172.16.0.1 255.240.0.0 ! ip route 0.0.0.0 0.0.0.0 172.33.1.2 name route_to_internet ip route 192.168.1.0 255.255.255.0 10.1.1.1 name branch_wired_subnet ip route 192.168.2.0 255.255.255.0 10.1.1.1 name branch_wireless_subnet
Verification
Enter the following command on the Left-Router to verify connections
Router#show crypto ikev2 sa IPv4 Crypto IKEv2 SA Tunnel-id Local Remote fvrf/ivrf Status 1 172.33.1.1/500 172.36.1.1/500 none/none READY Encr: AES-CBC, keysize: 256, PRF: SHA256, Hash: SHA256, DH Grp:15, Auth sign: PSK, Auth verify: PSK Life/Active Time: 86400/10830 sec IPv6 Crypto IKEv2 SA
Router#show crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 172.33.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (172.33.1.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (172.36.1.1/255.255.255.255/47/0)
current_peer 172.36.1.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 15, #pkts encrypt: 15, #pkts digest: 15
#pkts decaps: 15, #pkts decrypt: 15, #pkts verify: 15#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 172.33.1.1, remote crypto endpt.: 172.36.1.1
plaintext mtu 1438, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/0/0.10
current outbound spi: 0xAAC9EE2A(2865360426)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x6F946636(1871996470)
transform: esp-256-aes esp-sha256-hmac ,
in use settings ={Tunnel, }
conn id: 2051, flow_id: ESG:51, sibling_flags FFFFFFFF80000048, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4608000/2485)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xAAC9EE2A(2865360426)
transform: esp-256-aes esp-sha256-hmac ,
in use settings ={Tunnel, }
conn id: 2052, flow_id: ESG:52, sibling_flags FFFFFFFF80000048, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4608000/2485)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
Option 2: Dynamic Multipoint VPN (with private IP from Service Provider)
Example Hub 1 Configuration for DMVPN
In the following example, which configures the hub router for multipoint GRE and IPsec integration, no explicit configuration lines are needed for each spoke; that is, the hub is configured with a global IPsec policy template that all spoke routers can talk to. In this example, EIGRP is configured to run over the private physical interface and the tunnel interface.
1. Configure IKE Policy
crypto isakmp policy 1 encryption aes 256 authentication pre-share group 15 crypto isakmp key cisco47 address 0.0.0.0
2. Configure IPsec Transform Set
crypto ipsec transform-set trans2 esp-aes 256 esp-sha256-hmac mode transport
3. Configure an IPsec Profile
crypto ipsec profile vpnprof set transform-set trans2 !
4. Configure the Tunnel Interface for DMVPN
interface Tunnel0 bandwidth 1000 ip address 10.1.1.2 255.255.255.0 ip mtu 1400 ip nhrp authentication donttell ip nhrp map multicast dynamic ip nhrp network-id 99 ip nhrp holdtime 300 no ip split-horizon eigrp 1 no ip next-hop-self eigrp 1 ip tcp adjust-mss 1360 delay 1000 tunnel source Gigabitethernet0/0/0 tunnel mode gre multipoint tunnel key 100000 tunnel protection ipsec profile vpnprof
5. Configure the Physical Interfaces
interface Gigabitethernet0/0/0 ip address 172.36.1.1 255.255.255.0 ! interface Gigabitethernet0/0/1 ip address 172.16.0.1 255.240.0.0 !
6. Configure the Dynamic Protocol
router eigrp 1 network 172.16.0.0 0.15.255.255 network 10.1.1.0 0.0.0.255
For information about defining and configuring ISAKMP profiles, see the “ Certificate to ISAKMP Profile Mapping ” module in the Cisco IOS XE Security Configuration Guide: Secure Connectivity .
Example Hub 2 Configuration for DMVPN
Repeat the steps from Hub1 configuration, but with these necessary changes:
crypto isakmp policy 1 encryption aes 256 authentication pre-share group 15 crypto isakmp key cisco47 address 0.0.0.0 ! crypto ipsec transform-set trans2 esp-aes 256 esp-sha256-hmac mode transport ! crypto ipsec profile vpnprof set transform-set trans2 ! interface Tunnel1 bandwidth 1000 ip address 10.1.2.2 255.255.255.0 ip mtu 1400 ip nhrp authentication donttell ip nhrp map multicast dynamic ip nhrp network-id 100 ip nhrp holdtime 300 no ip split-horizon eigrp 1 no ip next-hop-self eigrp 1 ip tcp adjust-mss 1360 delay 1000 tunnel source Gigabitethernet0/0/0 tunnel mode gre multipoint tunnel key 100001 tunnel protection ipsec profile vpnprof ! interface Gigabitethernet0/0/0 ip address 172.37.1.1 255.255.255.0 ! interface Gigabitethernet0/0/1 ip address 172.16.0.2 255.240.0.0 ! router eigrp 1 network 172.16.0.0 0.15.255.255 network 10.1.2.0 0.0.0.255
Example Spoke Configuration for DMVPN
In the following example, all spokes are configured the same except for tunnel and local interface address, thereby reducing necessary configurations for the user:
crypto isakmp policy 1 encryption aes 256 authentication pre-share group 15 crypto isakmp key cisco47 address 0.0.0.0 ! crypto ipsec transform-set trans2 esp-aes 256 esp-sha256-hmac mode transport ! crypto ipsec profile vpnprof set transform-set trans2 ! crypto ipsec profile vpnprof1 set transform-set trans2 ! interface Tunnel0 bandwidth 1000 ip address 10.1.1.1 255.255.255.0 ip mtu 1400 ip nhrp authentication donttell ip nhrp map 10.1.1.2 172.36.1.1 ip nhrp map multicast 172.36.1.1 ip nhrp network-id 99 ip nhrp holdtime 300 ip nhrp nhs 10.1.1.2 ip tcp adjust-mss 1360 delay 1000 tunnel source <Cellular Slot/sub-slot/port> tunnel mode gre multipoint tunnel key 100000 tunnel protection ipsec profile vpnprof ! interface Tunnel1 bandwidth 1000 ip address 10.1.2.1 255.255.255.0 ip mtu 1400 ip nhrp authentication donttell ip nhrp map 10.1.2.2 172.37.1.1 ip nhrp map multicast 172.37.1.1 ip nhrp network-id 100 ip nhrp holdtime 300 ip nhrp nhs 10.1.2.2 ip tcp adjust-mss 1360 delay 1000 tunnel source <Cellular Slot/sub-slot/port> tunnel mode gre multipoint tunnel key 100001 tunnel protection ipsec profile vpnprof1 ! router eigrp 1 network 192.168.1.0 0.0.0.255 network 192.168.2.0 0.0.0.255 network 10.1.1.0 0.0.0.255 network 10.1.2.0 0.0.0.255Configure the physical interfaces to perform Network Address Translation in order to access the internet
interface <Cellular Slot/sub-slot/port> description WAN ip address dhcp hostname Spoke1 ip nat outside ! interface GigabitEthernet0/0/1 description Wired LAN ip address 192.168.1.1 255.255.255.0 ip nat inside ! interface vlan 2 description Wireless LAN ip address 192.168.2.1 255.255.255.0 ip nat inside ! interface Wlan-GigabitEthernet0/1/8 switchport access vlan 2 switchport mode access ! ip access-list extended NAT deny ip 192.168.1.0 0.0.0.255 172.16.0.0 0.15.255.255 deny ip 192.168.2.0 0.0.0.255 172.16.0.0 0.15.255.255 permit ip any any ip nat inside source list NAT interface GigabitEthernet0/0/2 overload !
Verification
Enter the following command on the Spoke to verify connections
Router#show ip eigrp neighbors EIGRP-IPv4 Neighbors for AS(1) H Address Interface Hold Uptime SRTT RTO Q Seq (sec) (ms) Cnt Num 1 10.1.2.2 Tu1 14 00:29:36 1 132 0 34 0 10.1.1.2 Tu0 13 00:29:45 1 1398 0 77
Router#show ip route eigrp | include D D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA o - ODR, P - periodic downloaded static route, l - LISP D 172.17.0.0 [90/25984000] via 10.1.1.2, 00:01:58, Tunnel0 D 172.18.0.0 [90/2944000] via 10.1.2.2, 00:31:28, Tunnel1
Router#ping 172.17.0.1 source 192.168.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.17.0.1, timeout is 2 seconds: Packet sent with a source address of 192.168.1.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms Router#ping 172.17.0.1 source 192.168.2.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.17.0.1, timeout is 2 seconds: Packet sent with a source address of 192.168.2.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/4 ms Router#ping 172.18.0.1 source 192.168.2.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.18.0.1, timeout is 2 seconds: Packet sent with a source address of 192.168.2.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/4 ms Router#ping 172.18.0.1 source 192.168.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.18.0.1, timeout is 2 seconds: Packet sent with a source address of 192.168.1.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/4 ms
Router#show crypto isakmp sa IPv4 Crypto ISAKMP SA dst src state conn-id status 172.36.1.1 172.33.1.1 QM_IDLE 1071 ACTIVE 172.37.1.1 172.33.1.1 QM_IDLE 1068 ACTIVE
Router#show crypto sa
interface: Tunnel0 Crypto map tag: Tunnel0-head-0, local addr 172.33.1.1 protected vrf: (none) local ident (addr/mask/prot/port): (172.33.1.1/255.255.255.255/47/0) remote ident (addr/mask/prot/port): (172.37.1.1/255.255.255.255/47/0) current_peer 172.37.1.1 port 500 PERMIT, flags={origin_is_acl,} #pkts encaps: 1036, #pkts encrypt: 1036, #pkts digest: 1036 #pkts decaps: 1053, #pkts decrypt: 1053, #pkts verify: 1053 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 0 local crypto endpt.: 172.33.1.1, remote crypto endpt.: 172.37.1.1 plaintext mtu 1458, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/0/0.10 current outbound spi: 0x7895BF85(2023079813) PFS (Y/N): N, DH group: none inbound esp sas: spi: 0x32F70777(855050103) transform: esp-256-aes esp-sha256-hmac , in use settings ={Transport, } conn id: 2053, flow_id: ESG:53, sibling_flags FFFFFFFF80004008, crypto map: Tunnel1000-head-0 sa timing: remaining key lifetime (k/sec): (4607964/2449) IV size: 16 bytes replay detection support: Y Status: ACTIVE(ACTIVE) inbound ah sas: inbound pcp sas: outbound esp sas: spi: 0x7895BF85(2023079813) transform: esp-256-aes esp-sha256-hmac , in use settings ={Transport, } conn id: 2054, flow_id: ESG:54, sibling_flags FFFFFFFF80004008, crypto map: Tunnel1000-head-0 sa timing: remaining key lifetime (k/sec): (4607979/2449) IV size: 16 bytes replay detection support: Y Status: ACTIVE(ACTIVE) outbound ah sas: outbound pcp sas: interface: Tunnel1 Crypto map tag: Tunnel1-head-0, local addr 172.33.1.1 protected vrf: (none) local ident (addr/mask/prot/port): (172.33.1.1/255.255.255.255/47/0) remote ident (addr/mask/prot/port): (172.36.1.1/255.255.255.255/47/0) current_peer 172.36.1.1 port 500 PERMIT, flags={origin_is_acl,} #pkts encaps: 552, #pkts encrypt: 552, #pkts digest: 552 #pkts decaps: 557, #pkts decrypt: 557, #pkts verify: 557 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 0 local crypto endpt.: 172.33.1.1, remote crypto endpt.: 172.36.1.1 plaintext mtu 1458, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/0/0.10 current outbound spi: 0x75D7D3A2(1977078690) PFS (Y/N): N, DH group: none inbound esp sas: spi: 0x881AC24(142715940) transform: esp-256-aes esp-sha256-hmac , in use settings ={Transport, } conn id: 2049, flow_id: ESG:49, sibling_flags FFFFFFFF80004008, crypto map: Tunnel1001-head-0 sa timing: remaining key lifetime (k/sec): (4607932/1270) IV size: 16 bytes replay detection support: Y Status: ACTIVE(ACTIVE) inbound ah sas: inbound pcp sas: outbound esp sas: spi: 0x75D7D3A2(1977078690) transform: esp-256-aes esp-sha256-hmac , in use settings ={Transport, } conn id: 2050, flow_id: ESG:50, sibling_flags FFFFFFFF80004008, crypto map: Tunnel1001-head-0 sa timing: remaining key lifetime (k/sec): (4607961/1270) IV size: 16 bytes replay detection support: Y Status: ACTIVE(ACTIVE) outbound ah sas:
WiFi Configuration 1: Using router CLI (ME Mode)
There are multiple ways in which we can configure the WiFi Module on the router. The first one method we will discuss is manual CLI commands being inserted to bring up the Mobility Express controller present in the ISR 1K router.
Identify the Wireless AP slot on the router, by using a show platform command
Router#sh platform Chassis type: C1121X-8PLTEPWB Slot Type State Insert time (ago) --------- ------------------- --------------------- ----------------- 0 C1121X-8PLTEPWB ok 00:27:23 0/0 C1121X-2x1GE ok 00:25:01 0/1 C1121X-ES-8 ok 00:25:01 0/2 P-LTEAP18-GL ok 00:25:01 0/3 ISR-AP1101AC-B ok 00:25:01 R0 C1121X-8PLTEPWB ok, active 00:27:23 F0 C1121X-8PLTEPWB ok, active 00:27:23 P0 PWR-12V ok 00:26:48 Slot CPLD Version Firmware Version --------- ------------------- --------------------------------------- 0 18103101 16.12(1r) R0 18103101 16.12(1r) F0 18103101 16.12(1r)
Open a session to your module using the hw-module session command in privileged EXEC mode on the router :
Router#hw-module session 0/3 Establishing session connect to subslot 0/3 To exit, type ^a^q picocom v2.2 port is : /dev/ttyS3 flowcontrol : none baudrate is : 9600 parity is : none databits are : 8 stopbits are : 1 escape is : C-a local echo is : no noinit is : no noreset is : no nolock is : yes send_cmd is : sz -vv receive_cmd is : rz -vv -E imap is : omap is : emap is : crcrlf,delbs, logfile is : none Type [C-a] [C-h] to see available commands Terminal ready
When prompted to terminate the auto-install process (the CLI Initial Configuration Wizard), wait for 30 seconds. The CLI Initial Configuration Wizard begins after 30 seconds. Enter the Administrative Username and Administrative password to be assigned to this controller :
Enter Administrative User Name (24 characters max): admin Enter Administrative Password (3 to 127 characters): ******** Re-enter Administrative Password : ********
Enter the System Name, which is the name that you want to assign to the controller :
System Name [Cisco-4001.7ac0.8ba0] (24 characters max): Cisco-4001.7ac0.8ba0
Enter the code for the country in which the Mobility Express network is located. In case you are not aware of your country code, you can enter "help" and then type the appropriate country code :
Enter Country Code list (enter 'help' for a list of countries) [US]: help Enter the country code list (e.g. US,CA,MX) max=30. Supported Country Codes: AE, AL, AR, AT, AU, BA, BB, BE, BG, BH, BM, BN, BO, BR, BY, CA, CH, CL, CM, CN, CO, CR, CY, CZ, DE, DK, DO, DZ, EC, EE, EG, EL, ES, FI, FJ, FR, GB, GH, GI, GR, HK, HR, HU, ID, IE, IL, IO, IN, IQ, IS, IT, J4, JM, JO, KE, KN, KW, KZ, LB, LI, LK, LT, LU, LV, LY, MA, MC, ME, MK, MN, MO, MT, MX, MY, NG, NL, NO, NZ, OM, PA, PE, PH, PK, PL, PR, PT, PY, QA, RO, RS, RU, SA, SE, SG, SI, SK, TH, TI, TN, TR, TW, UA, US, UY, VE, VN, ZA Enter Country Code list (enter 'help' for a list of countries) [US]: IN
If you want the controller to receive its time setting from an external Network Time Protocol (NTP) server when it powers up, enter YES to configure an NTP server. For this lab purpose, we would be skipping this step. When you select "No", then it would ask the user to manually enter the date and time. This step can also be skipped :
Configure a NTP server now? [YES][no]: no Configure the system time now? [YES][no]: no Note! Default NTP servers will be used
Enter the IP address of the management interface. The management interface is the default interface for in-band management of the controller and connectivity to enterprise services. Also enter the IP address and subnet mask of the management interface and the default gateway router address :
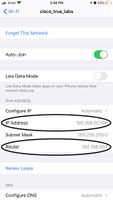
Management Interface IP Address Configuration [STATIC][dhcp]: STATIC Management Interface IP Address: 192.168.50.254 Management Interface Netmask: 255.255.255.0 Management Interface Default Router: 192.168.50.1
Now it will ask if you want to configure the DHCP scope to manage the address allocation for the clients connecting to the SSID (Yet to be configured). Please provide the relevant details such as pool, mask, Domain Name, DNS :
Create Management DHCP Scope? [yes][NO]: yes DHCP Network : 192.168.50.0 DHCP Netmask : 255.255.255.0 Router IP: 192.168.50.1 Start DHCP IP address: 192.168.50.11 Stop DHCP IP address: 192.168.50.253 DomainName : cisco.com DNS Server : [OPENDNS][user DNS]
Now it asks to configure the Employee Network ID (SSID) for the wireless controller and its security/authentication type and respective paraphrase :
Employee Network Name (SSID)?: cisco_true_labs Employee Network Security? [PSK][enterprise]: PSK Employee PSK Passphrase (8-63 characters)?: ******** Re-enter Employee PSK Passphrase: *********
To enable RF Parameter Optimization, enter YES. Enter the Client Density. You can enter TYPICAL, Low, or High, as per your requirement. Then it will confirm the changes made so far, and would reset the controller with the configured settings :
Enable RF Parameter Optimization? [YES][no]: YES Client Density [TYPICAL][Low][High]: Low Configuration correct? If yes, system will save it and reset. [yes][NO]: yes Configuration saved! Resetting system with new configuration...
After this step, wait till the controller comes back up and the AP is given the management address and the AP comes online. You can verify if the AP is online using the "show ap summary" command from the controller mode :
(Cisco Controller) >show ap sum Number of APs.................................... 1 Global AP User Name.............................. admin Global AP Dot1x User Name........................ Not Configured Global AP Dot1x EAP Method....................... EAP-FAST * prefix indicates Cisco Internal AP AP Name Slots AP Model Ethernet MAC IP Address Clients ----------------- ----- --------------- -------------- ---------- ----------- *AP4001.7AC0.8BA0 2 ISR-AP1101AC-D 40:01:7a:c0:8b:a0 192.168.50.97 1
Verification
Now, you should be able to see this SSID being advertised by the AP, and using any mobile device try to login to the SSID.
Then, you can verify the client which had joined the AP using "show dhcp lease" from the controller mode :
(Cisco Controller) >show dhcp lease Total Leases: 2 Host Name MAC IP Lease Time Remaining ABCDEs-iPhone aa:bb:cc:dd:ee:ff 192.168.50.198 23 hours 57 minutes 10 seconds AP4001-7AC0-8BA0 40:01:7a:c0:8b:a0 192.168.50.97 23 hours 52 minutes 39 seconds
You can validate if the SSID is active using "show wlan summary" from the controller mode :
(Cisco Controller) >show wlan summary Number of WLANs..................... 1 WLAN ID WLAN Profile Name / SSID Status Interface Name ------- ------------------------------------- -------- -------------------- 1 cisco_true_labs / cisco_true_labs Enabled management
Use Case #2 (using PnP server)
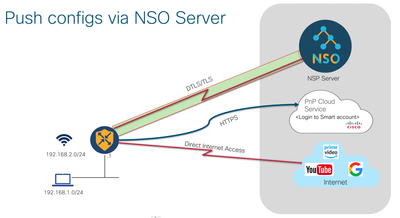
Step-By-Step Configuration
Add Devices to Smart Account
1. Navigate to software.cisco.com
2. Under Network Plug and Play, click on Plug and Play Connect
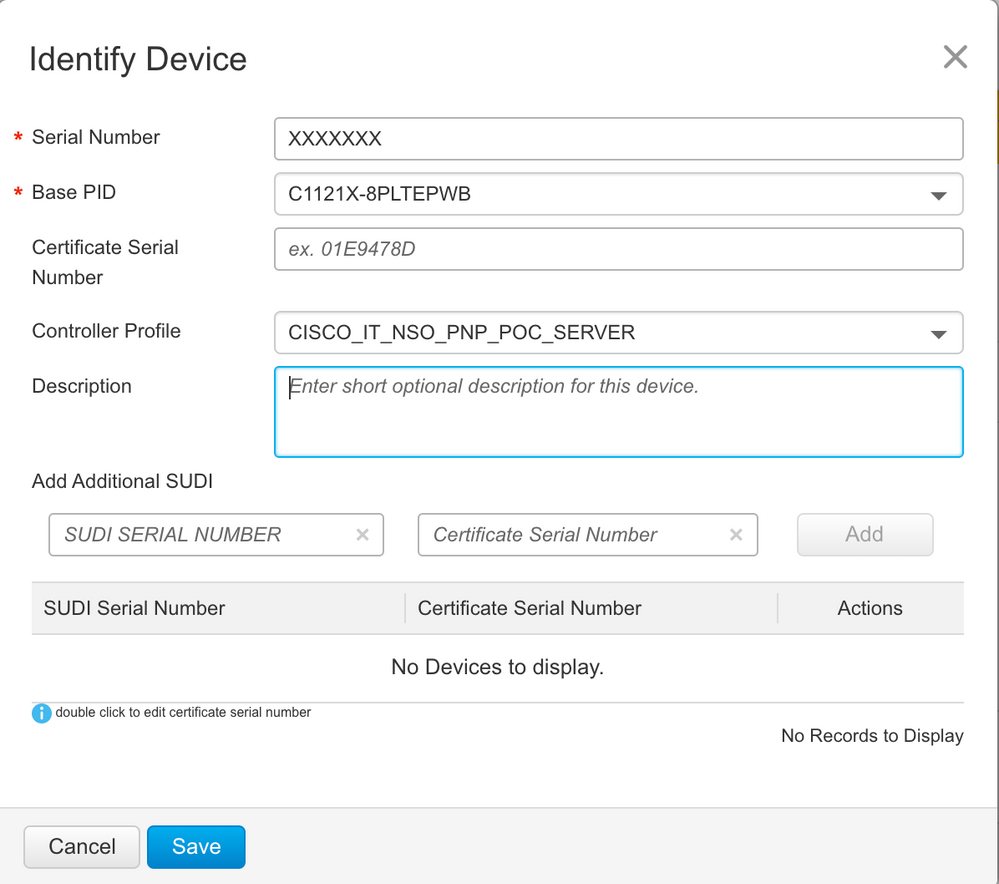
3. Click on Identify Device
4. Enter Serial Number, select Base PID (C1121X-8PLTEPWB) from the drop down menu and add Controller Profile (VIPTELA-CLOUD-HOSTED-PROFILE) from the drop down menu. Click Save and advance to the next step by clicking Next
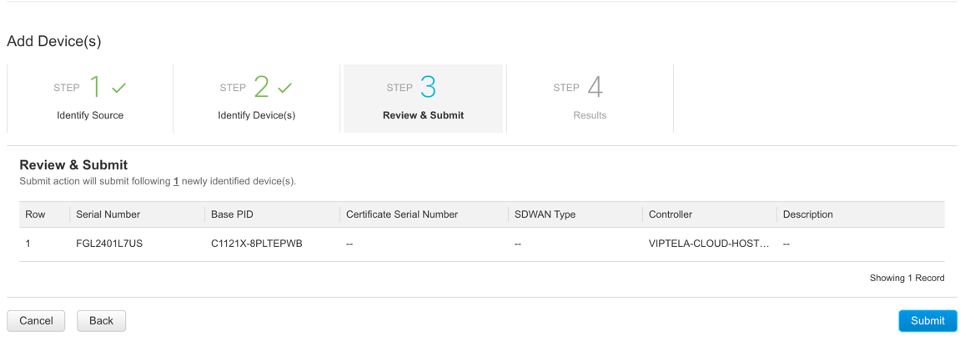
5. Verify the credentials and click Submit
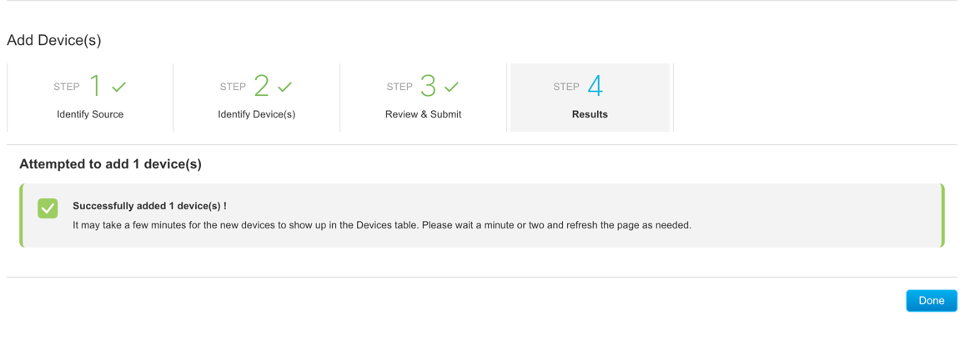
6. If device is added correctly, you should see a success message (such as shown below):
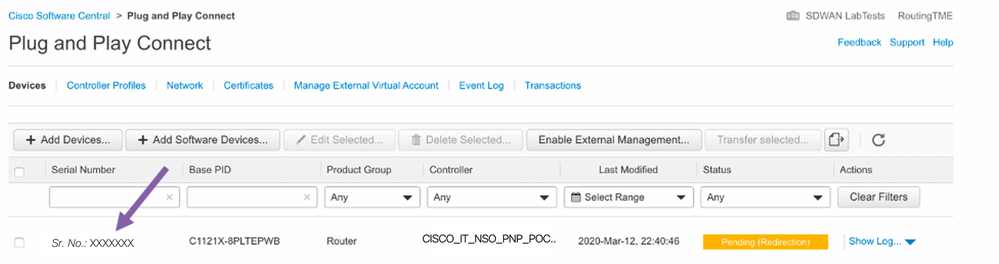
7. You will be redirected to the PnP Devices tab, where you should find your device (identifiable by Serial Number) listed with a status of Pending (Redirection)
NSO Server Requirements
1. On the NSO Server, ensure the device serial number and Base PID are entered correctly
2. Add the configuration file to the NSO Server as shown below
WiFi Configuration 2: Zero-Touch Deployment (ME Mode)
The event manager applet script can be pushed as part of the configuration file from the NSO server which will automatically configure the router with the required ME configuration with the SSID "Area_WiFi_Access" that can be used for Direct Internet Access
hostname Router ! ! ip dhcp excluded-address 192.168.1.1 192.168.1.10 ip dhcp excluded-address 192.168.1.250 192.168.1.255 ! ip dhcp pool Hotspot-Internet network 192.168.1.0 255.255.255.0 default-router 192.168.1.1 dns-server 8.8.8.8 8.8.4.4 option 43 ip 192.168.1.3 lease 0 8 ! ! login on-success log ! ! vlan 2 ! ! username admin privilege 15 password 0 admin ! ! interface GigabitEthernet0/0/0 shutdown negotiation auto ! interface GigabitEthernet0/0/1 shutdown negotiation auto ! interface GigabitEthernet0/1/0 description Wired switchport access vlan 2 switchport mode access spanning-tree portfast no shutdown ! interface GigabitEthernet0/1/1 description Wired switchport access vlan 2 switchport mode access spanning-tree portfast no shutdown ! interface GigabitEthernet0/1/2 description Wired switchport access vlan 2 switchport mode access spanning-tree portfast no shutdown ! interface GigabitEthernet0/1/3 description Wired switchport access vlan 2 switchport mode access spanning-tree portfast no shutdown ! interface GigabitEthernet0/1/4 description Wired switchport access vlan 2 switchport mode access spanning-tree portfast no shutdown ! interface GigabitEthernet0/1/5 description Wired switchport access vlan 2 switchport mode access spanning-tree portfast no shutdown ! interface GigabitEthernet0/1/6 description Wired switchport access vlan 2 switchport mode access spanning-tree portfast no shutdown ! interface GigabitEthernet0/1/7 description Wired switchport access vlan 2 switchport mode access spanning-tree portfast no shutdown ! interface Wlan-GigabitEthernet0/1/8 description Wireless switchport access vlan 2 switchport mode access no shutdown ! interface Cellular0/2/0 no shutdown ip address negotiated ip nat outside dialer in-band dialer-group 1 ipv6 enable pulse-time 1 ! interface Cellular0/2/1 no ip address ! interface Vlan1 no ip address ! interface Vlan2 description Internet-Users ip address 192.168.1.1 255.255.255.0 ip nat inside no shutdown ! ! ip nat inside source list NAT interface Cellular0/2/0 overload ip route 0.0.0.0 0.0.0.0 Cellular0/2/0 253 ! ! ip access-list extended NAT 10 permit ip any any ! ! ip access-list standard 1 10 permit any dialer-list 1 protocol ip list 1 ! ! line vty 0 4 password admin login local transport input telnet ssh transport output none ! ! !Configure 'event timer countdown time 480 maxrun 900' !to trigger the EEM after ample time for bootstrap !config deployments ! event manager applet setup_AP event timer countdown time 480 maxrun 900 action 000 syslog msg "Checking if Wireless AP is in 'ok' state..." action 001 cli command "enable" action 002 cli command "show platform" pattern "#" action 003 foreach line "$_cli_result" "\n" action 004 regexp "ISR-AP" "$line" action 005 if $_regexp_result eq "1" action 006 regexp ".\/." "$line" subslot action 007 regexp "ok" "$line" state action 008 syslog msg "OK check regex: $_regexp_result" action 009 if $_regexp_result eq "1" action 010 syslog msg "Module is in OK state!" action 011 break action 012 else action 013 syslog msg "Module is not in OK state!" action 014 cli command "config t" action 015 cli command "event manager applet setup_AP" action 016 cli command "event timer countdown time 30 maxrun 900" action 017 cli command "end" action 018 break action 019 end action 020 end action 021 end action 022 syslog msg "Disabling invocation of the EEM script and waiting 240 seconds for ME controller..." action 023 wait 240 action 024 cli command "enable" action 025 cli command "config t" action 026 cli command "event manager applet setup_AP" action 027 cli command "event none maxrun 900" action 028 cli command "end" action 029 syslog msg "Saving completed configuration for next reboot..." action 030 cli command "write mem" action 100 syslog msg "Starting to session into the Wireless AP in subslot $subslot..." action 101 cli command "hw-module session $subslot" pattern "Terminal ready" action 102 syslog msg "Look for Admin User Name prompt..." action 103 cli command "" pattern "Administrative User Name" action 104 syslog msg "Setting username..." action 105 cli command "admin" pattern "Password" action 106 syslog msg "Setting password..." action 107 cli command "Master123" pattern "Password" action 108 syslog msg "Verifying password..." action 109 cli command "Master123" pattern "characters" action 110 syslog msg "Setting system name..." action 111 cli command "CISCO" pattern "countries" action 112 syslog msg "Setting country code..." action 113 cli command "US" pattern "NTP" action 114 syslog msg "Setting NTP server state..." action 115 cli command "YES" pattern "default" action 116 syslog msg "Setting use of default NTP servers..." action 117 cli command "YES" pattern "timezone" action 118 syslog msg "Setting timezone..." action 119 cli command "5" pattern "dhcp" action 120 syslog msg "Setting use of STATIC address..." action 121 cli command "STATIC" pattern "IP Address" action 122 syslog msg "Setting static IP address for ME controller..." action 123 cli command "192.168.1.3" pattern "Netmask" action 124 syslog msg "Setting IP netmask for ME controller..." action 125 cli command "255.255.255.0" pattern "Default Router" action 126 syslog msg "Setting IP default router for ME controller..." action 127 cli command "192.168.1.1" pattern "DHCP Scope" action 128 syslog msg "Setting DHCP scope..." action 129 cli command "NO" pattern "Employee" action 130 syslog msg "Setting SSID name..." action 131 cli command "Area_WiFi_Access" pattern "Security" action 132 syslog msg "Setting SSID security..." action 133 cli command "PSK" pattern "Passphrase" action 134 syslog msg "Setting SSID passphrase..." action 135 cli command "W1r3l355!" pattern "Passphrase" action 136 syslog msg "Verifying SSID passphrase..." action 137 cli command "W1r3l355!" pattern "Optimization" action 138 syslog msg "Setting RF parameter optimization..." action 139 cli command "YES" pattern "Density" action 140 syslog msg "Setting density..." action 141 cli command "TYPICAL" pattern "Voice" action 142 syslog msg "Setting voice usage..." action 143 cli command "NO" pattern "correct" action 144 syslog msg "Verifying config..." action 145 cli command "yes" pattern "Cleaning" action 146 syslog msg "AP and Mobility Express Controller provisioned successfully!" action 147 syslog msg "Done, exiting." ! no pnp profile pnp_redirection_profile !
Use Case #3 (boot strap using USB/bootflash)
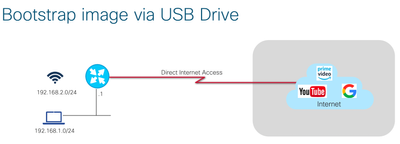
WiFi Configuration 3: Zero-Touch Deployment - External WLC (CAPWAP Mode)
To attach the Wireless AP to an external WLC, configure the router with DHCP Option 43 command as shown below, with the IP address of the external WLC in hexadecimal form. f205 will indicate to the router to convert from ME to CAPWAP mode. In this way, you can configure your router to join the WLC of your office and connect to the office wireless SSID at your remote location
hostname USB_CAPWAP ! ! ip dhcp excluded-address 192.168.1.1 192.168.1.10 ip dhcp excluded-address 192.168.1.250 192.168.1.255 ! ip dhcp pool Hotspot-Internet network 192.168.1.0 255.255.255.0 default-router 192.168.1.1 option 43 hex f205.806b.ea05 dns-server 8.8.8.8 8.8.4.4 lease 0 8 ! ! login on-success log ! ! vlan 2 ! ! username admin privilege 15 password 0 admin ! ! interface GigabitEthernet0/0/0 shutdown negotiation auto ! interface GigabitEthernet0/0/1 shutdown negotiation auto ! interface GigabitEthernet0/1/0 description Wired switchport access vlan 2 switchport mode access spanning-tree portfast no shutdown ! interface GigabitEthernet0/1/1 description Wired switchport access vlan 2 switchport mode access spanning-tree portfast no shutdown ! interface GigabitEthernet0/1/2 description Wired switchport access vlan 2 switchport mode access spanning-tree portfast no shutdown ! interface GigabitEthernet0/1/3 description Wired switchport access vlan 2 switchport mode access spanning-tree portfast no shutdown ! interface GigabitEthernet0/1/4 description Wired switchport access vlan 2 switchport mode access spanning-tree portfast no shutdown ! interface GigabitEthernet0/1/5 description Wired switchport access vlan 2 switchport mode access spanning-tree portfast no shutdown ! interface GigabitEthernet0/1/6 description Wired switchport access vlan 2 switchport mode access spanning-tree portfast no shutdown ! interface GigabitEthernet0/1/7 description Wired switchport access vlan 2 switchport mode access spanning-tree portfast no shutdown ! interface Wlan-GigabitEthernet0/1/8 description Wireless switchport access vlan 2 switchport mode access no shutdown ! interface Cellular0/2/0 no shutdown ip address negotiated ip nat outside dialer in-band dialer-group 1 ipv6 enable pulse-time 1 ! interface Cellular0/2/1 no ip address ! interface Vlan1 no ip address ! interface Vlan2 description Internet-Users ip address 192.168.1.1 255.255.255.0 ip nat inside no shutdown ! ! ip nat inside source list NAT interface Cellular0/2/0 overload ip route 0.0.0.0 0.0.0.0 Cellular0/2/0 253 ! ! ip access-list extended NAT 10 permit ip any any ! ! ip access-list standard 1 10 permit any dialer-list 1 protocol ip list 1 ! ! line vty 0 4 password admin login local transport input telnet ssh transport output none ! !
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
interesting; thanks for sharing!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi.
Thank you for interesting post.
Regarding "WiFi Configuration 2: Zero-Touch Deployment (ME Mode)"
had to add "event manager session cli username" for cli commands to run.
I have a problem, getting to step "action 100 syslog msg "Starting to session into the Wireless AP in subslot $subslot..." nothing happens after that. Syslog posts "%HA_EM-6-LOG: setup_AP: Starting to session into the Wireless AP in subslot 0/3", after this nothing happens.
Any clue what's missing?
I can log in to "hw-module session 0/3" and see that "Terminal ready" is there.
BR,
Aleksander
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: