- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- Configuration Example : Site-to-Site VPN for IPv6 IPsec
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
09-21-2012 03:13 AM - edited 03-01-2019 04:51 PM
- Step 1: Configure IKE Policy and Pre-shared Key:
- Step 2: Configuring an IPsec Transform Set and IPsec Profile:
- Step 3: Configure an ISAKMP Profile in IPv6:
Introduction:
This document discuss about IPv6 IPsec Site-to-Site VPN Using Virtual Tunnel Interface with configuration example.
Cisco IOS IPsec functionality provides network data encryption at the IP packet level, offering a robust, standards-based security solution. IPsec provides data authentication and anti-replay services in addition to data confidentiality services. With IPsec, data can be sent across a public network without observation, modification, or spoofing.
General usage scenarios for IPv6 IPSec:
1) Site-to-site VPN – protect all IPv6 traffic between two trusted networks
2) Configured Secure Tunnel – protect IPv6 traffic being tunneled over an non trusted IPv4 network.
3) IPSec can also be used to protect control plane functions, such as IPSec to protect OSPFv3.
Background:
In following example IPSec-protected tunnel is set up between CE1 and CE2 to communicate over public network. The routers ISP_IR1 and ISP_IR2 have global IPv6 address and does not have knowledge about private subnets present on CE1 and CE2.
Topology diagram:
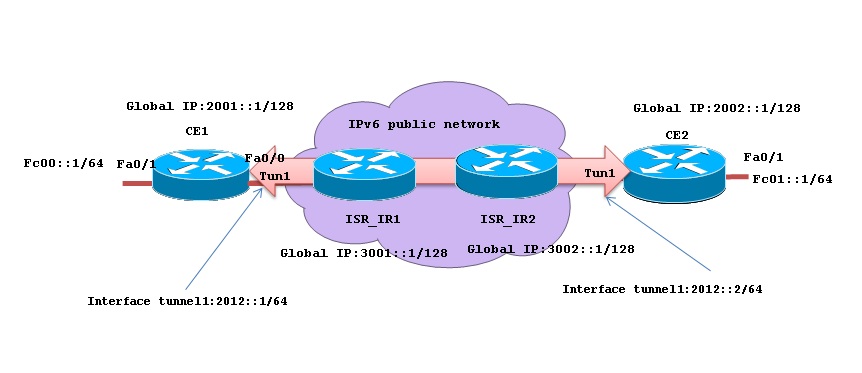
Configuration overview:
Site-to-site VPN is configure on router as follows:
Step 1: Configure IKE Policy and Pre-shared Key:
Configure same ISAKMP policy on the routers CE1 and CE2
CE1#conf t
Enter configuration commands, one per line. End with CNTL/Z.
CE1(config)#crypto isakmp policy 10
CE1(config-isakmp)#encryption 3des
CE1(config-isakmp)#group 2
CE1(config-isakmp)#authentication pre-share
CE1(config-isakmp)#exit
Each router must be configured with the same key, but the configuration statement should designate the address of the appropriate interface on the peer router.
CE1:
CE1(config)#crypto isakmp key 0 ipsecvpn address ipv6 2002::1/128
CE2:
CE2(config)#crypto isakmp key 0 ipsecvpn address ipv6 2001::1/128
These keys are default ISAKMP keyring. We can use multiple named keyrings used when the router is hosting remote client VPNs for multiple different groups of clients.
crypto keyring keyring-name ……………(to specify keyring)
Step 2: Configuring an IPsec Transform Set and IPsec Profile:
Configure same IPsec Transform Set and IPsec Profile on the routers CE1 and CE2:
CE1(config)#crypto ipsec transform-set ipv6_tran esp-3des esp-sha-hmac
CE1(cfg-crypto-trans)#mode tunnel
CE1(cfg-crypto-trans)#exit
CE1(config)#crypto ipsec profile ipv6_ipsec_pro ……(This transform set need to bind in VTI step4)
CE1(ipsec-profile)#set transform-set ipv6_tran
CE1(ipsec-profile)#exit
CE1(config)#
Step 3: Configure an ISAKMP Profile in IPv6:
ISAKMP profile is configured in the routers CE1 and CE2 and ensure that configuration statement must designate the identity address of the appropriate interface on the peer router.
CE1(config)#crypto isakmp profile 3des
% A profile is deemed incomplete until it has match identity statements
CE1(conf-isa-prof)#self-identity address ipv6
CE1(conf-isa-prof)#match identity address ipv6 2002::1/128
CE1(conf-isa-prof)#keyring default
CE1(conf-isa-prof)# exit
CE1(config)#
Step 4: Configure ipsec IPv6 VTI :
Configuring IPv6 IPsec VTI on router is pretty simple
CE1(config)#int tunnel 1
CE1(config-if)#ipv6 enable
CE1(config-if)#ipv6 address 2012::1/64
CE1(config-if)#tunnel source 2001::1
CE1(config-if)#tunnel destination 2002::1
CE1(config-if)#tunnel mode ipsec ipv6
CE1(config-if)#tunnel protection ipsec profile ipv6_ipsec_pro
*Mar 1 01:32:30.907: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
CE1(config-if)#exit
CE2(config)#int tunnel 1
CE2(config-if)#ipv6 enable
CE2(config-if)#ipv6 address 2012::2/64
CE2(config-if)#tunnel source 2002::1
CE2(config-if)#tunnel destination 2001::1
CE2(config-if)#tunnel mode ipsec ipv6
CE2(config-if)#tunnel protection ipsec profile ipv6_ipsec_pro
*Mar 1 01:32:30.907: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
CE2(config-if)#exit
To make the tunnel as best path for the remote site network, you must configure static routes in the routers CE1 and CE2.
CE1:
CE1(config)#ipv6 route FC01::/64 2012::2
CE2:
CE2(config)#ipv6 route FC00::/64 2012::1
Verification commands:
1) This command displays the active ISAKMP sessions on the router
CE1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
IPv6 Crypto ISAKMP SA
dst: 2002::1
src: 2001::1
state: QM_IDLE conn-id: 1007 slot: 0 status: ACTIVE
To displays a summary of the configuration information for the crypto engines.
CE1#show crypto engine connection active
Crypto Engine Connections
ID Interface Type Algorithm Encrypt Decrypt IP-Address
1 Tu1 IPsec 3DES+SHA 0 95 2001::1
2 Tu1 IPsec 3DES+SHA 128 0 2001::1
1007 Tu1 IKE SHA+3DES 0 0 2001::1
CE1#ping fc01::1 source fc00::1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to FC01::1, timeout is 2 seconds:
Packet sent with a source address of FC00::1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 36/187/388 ms
CE1#traceroute
Protocol [ip]: ipv6
Target IPv6 address: fc01::1
Source address: fc00::1
Insert source routing header? [no]:
Numeric display? [no]:
Timeout in seconds [3]:
Probe count [3]:
Minimum Time to Live [1]:
Maximum Time to Live [30]:
Priority [0]:
Port Number [33434]:
Type escape sequence to abort.
Tracing the route to FC01::1
1 FC01::1 304 msec 184 msec 160 msec
Related Information:
http://www.cisco.com/en/US/docs/ios-xml/ios/ipv6/configuration/15-2mt/ip6-ipsec.html
http://tools.ietf.org/html/rfc4294#page-10
Base Initial configuration:
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thx Ashish..........very useful
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello Akshay,
Thanks for your feedback.
Regards,
Ashish Shirkar
Technical community manager(Network Infrastructure)
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: