- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- Deploying SD-WAN Remote Access Solution
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
05-04-2023 10:28 AM - edited 05-19-2023 02:31 AM
- 1. Goal
- 2. Use Case Benefits
- 3. Solution Architecture
- 3.1 Topology Elements
- 3.2 Prerequisites
- 3.3 Restrictions
- 4. Solution Deployment
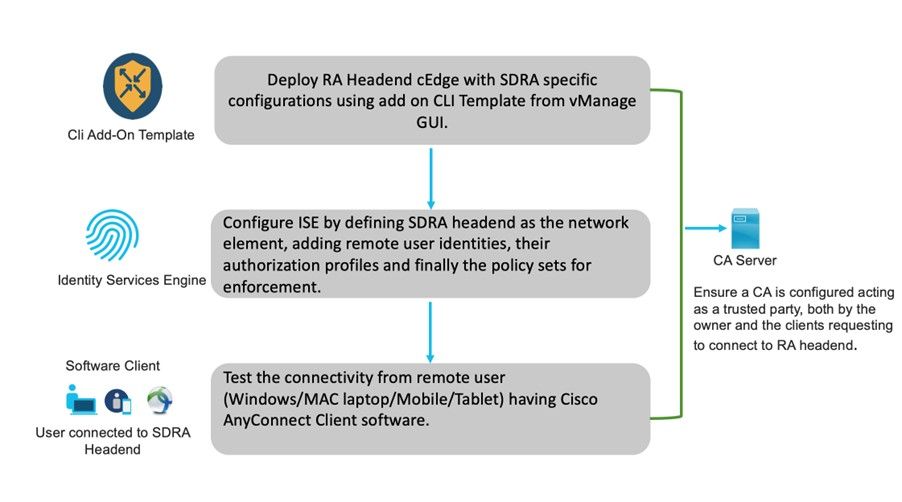
- 4.1 High Level Deployment Workflow
- 5. Detailed deployment instructions
- 5.1 CLI Configuration for Addon Template
- 5.1.1 CLI Configuration required on SDRA router
- 5.1.2 CLI Configuration Components and Explanation
- 5.1.2.1 RA IP Pool
- 5.1.2.2 RADIUS and AAA Parameters
- 5.1.2.3 PKI Trustpoint for Certificate Enrollment
- 5.1.2.4 IKEv2 Proposal and Policy
- 5.1.2.5 Virtual Template Interface
- 5.1.2.6 IKEv2 Ciphers, Parameters, and Profile
- 5.1.2.7 Loopback Interface
- 5.2 Task 1: Provision SDRA Headend – Add Remote Access Configuration using CLI Add-on Template
- 5.2.1 Attach the CLI Addon Template to the SDRA Headend
- 5.2.2 Attach Add-On CLI Template to SDRA Headend Router
- 5.3 Task 2: Configure Cisco Identity Services Engine(ISE)
- 5.3.1 Adding SDRA Headend Network Device
- 5.3.2 Adding Remote Access Client Identity (Credentials)
- 5.3.3 Create Authorization Policy for AnyConnect users
- 5.3.4 Create a Policy Set to enforce the authorization policy against the user type
- 5.4 Task 3: Configure Cisco AnyConnect Client for testing
- 5.4.1 AnyConnect Client Installation
- 5.4.2 Download and Install the Cisco AnyConnect Profile Editor
- 5.4.3 Modify the Cisco AnyConnect Profile using Profile Editor
- 5.4.4 Disable the AnyConnect Downloader
- 5.4.5 Unblock Untrusted Servers (Optional)
- 5.4.6 Validate the Connectivity to SDRA Headend
- 6. Solution Planning
- 6.1 RA Headend Platform selection/dependencies
- 6.2 Port and Protocol Information for Firewalls
- 6.2 Site Scale Requirements
- 6.3 RA Client Dependencies
- 7. AnyConnect Traffic Use case
- 7.1 Use Case 1 - Split Tunnelling
- 7.1.1 Split Tunneling Workflow on ISE
- 7.1.2 Split Tunnelling - Workflow on SDRA Router
- 7.1.3 Split Tunnelling – Verification on from Remote Access Client
- 7.2 Use Case 2 - Tunnel All
- 7.2.1 Tunnel All - Workflow on ISE
- 7.2.2 Tunnel All - NAT-DIA Workflow on SDRA Router
- 7.2.2.1 Equivalent CLI Generated for NAT-DIA on SDRA
- 7.2.3 Tunnel All - Verification on Remote Access Client
- 7.3 Use Case 3 - Umbrella Integration with SDRA
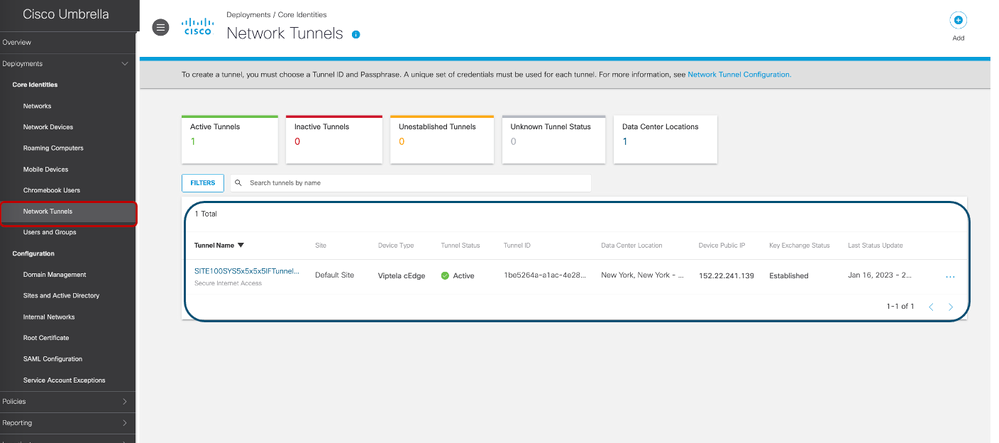
- 7.3.1.1 Verify the Umbrella SIG Tunnel Status on SDRA Headend
- 7.3.2 Verification on Umbrella Dashboard
- 7.3.3 Configure SDRA traffic redirection to SIG Interface on vManage
- 7.3.4 Testing Umbrella SIG for SDRA User
- 7.3.5 Perform Web Testing from RA Client
- 8. SDRA Monitoring
- 8.1 SDRA Monitoring from CLI
- 8.1.1 Verifying Successful connection with ISE (Radius server) from SDRA router
- 8.1.2 Verify Virtual Template Interface
- 8.1.3 Verify Routing Information specific to the VRF
- 8.1.4 Verify Configuration on Virtual Access Interface
- 8.1.5 Verify IPsec Security Associations
- 8.1.6 Verify IKEv2 Session Details
- 8.1.7 Verify Crypto session information
- 8.1.8 Verify IKEv2 SA Parameters
- 8.1.9 Verify RA Pool and Active RA client
- 8.1.10 Verify the CA Certificate and the Edge Router Certificate
- 8.2 SDRA Monitoring from vManage
- 9. Appendix A: How to advertise RA pool in OMP as a summary-route
- 9.1 Visibility into Redistributed route from the RA client in the SD-WAN network
- 10. Appendix B: SD-WAN Remote Access Package/ Licensing
- 10.1 Cisco SD-WAN RA Add-On Pricing and Ordering
- 10.2 Simplified steps of ordering
- 11. Appendix C: SD-WAN Remote Access Configuration
- 12. Appendix D – SIG Credentials/Feature Template Configuration
- 12.1 Where to find Organization ID and Registration key from Umbrella Dashboard
1. Goal
The goal of this document is to explain the deployment of the SD-WAN Remote Access (SDRA) feature with the Cisco AnyConnect Client, along with its configuration.
The solution uses the following additional elements:
• Windows Server as a CA server
• Cisco Identity Services Engine (ISE) server for Authentication, Authorization, and Accounting
2. Use Case Benefits
This solution is aimed at existing SD-WAN customers who wish to re-engineer their remote access framework by utilizing existing SD-WAN infrastructure. The SDRA feature integrates remote access capability into Cisco SD-WAN IOS XE SD-WAN devices, thereby providing seamless transition to all the documented benefits of SD-WAN.
This solution enables segmentation per user type (Enterprise, Guest, IOT, etc.) and provides elegant support for brownfield deployments. This eliminates the need for separate Cisco SD-WAN and RA infrastructure and enables rapid scalability of RA services.
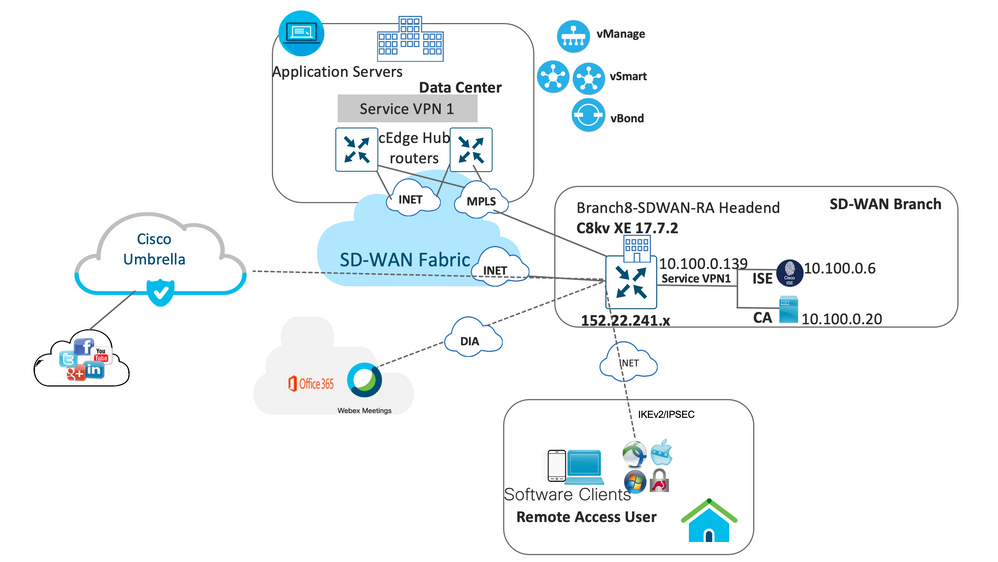
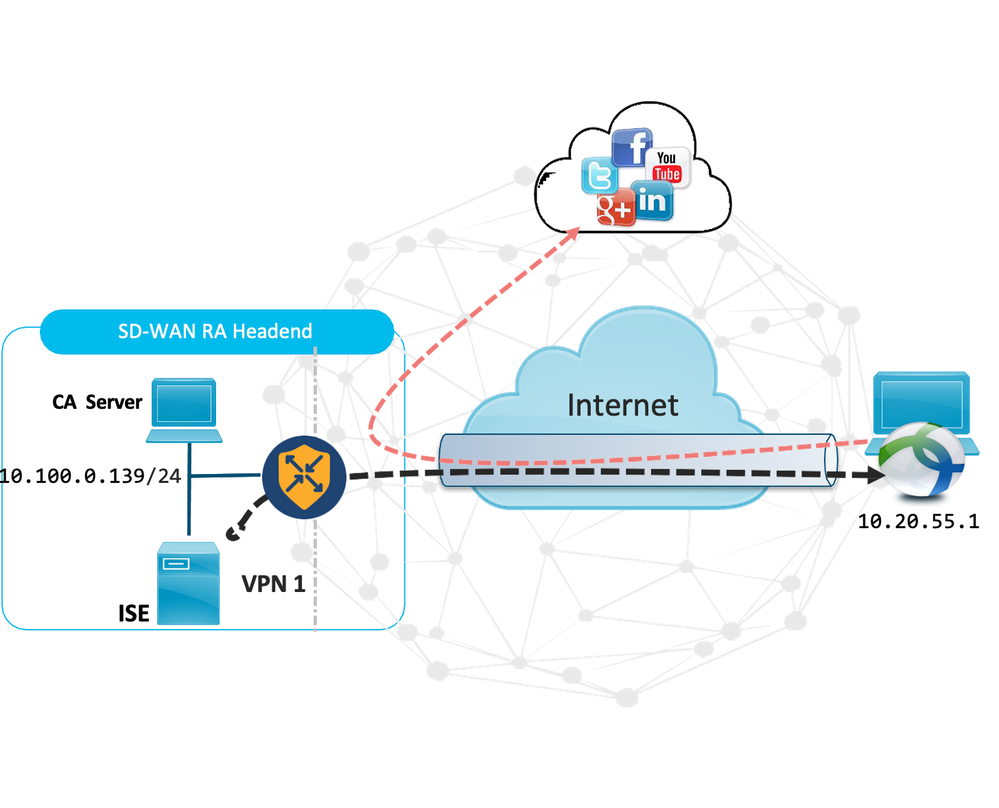
3. Solution Architecture
This solution utilizes an existing IOS XE SD-WAN router as a Remote Access Headend (RA Headend) in one of the SD-WAN branches. The SDRA Router is configured to utilize Cisco ISE (Identity Service Engine) to provide AAA functionality for remote access users. The SDRA Router also utilizes a CA Server that acts as a trusted entity that issues the digital certificate to the SDRA router.
3.1 Topology Elements
Following are the products used to validate the SDRA setup
|
PRODUCT |
QUANTITY |
ROLE |
|
vManage (20.7) |
1 |
SDWAN Infra |
|
vBond (20.7) |
1 |
SDWAN Infra |
|
vSmart (20.7) |
1 |
SDWAN Infra |
|
Edge(17.7.2) (Cat 8kv) |
1 |
SDRA Headend Router |
|
Edge (Any) |
Any |
Non-SDRA Routers |
|
Windows Server (2019) |
1 |
CA Server |
|
Cisco ISE (3.1) |
1 |
AAA Server |
|
Windows Laptop (Win 10/ Win 11) |
1 |
Any Connect Client for Testing |
|
Mac Laptop (Ventura 13.1) |
1 |
Any Connect Client for Testing |
|
Android Phone (v13) |
1 |
AnyConnect Client for Testing |
|
Apple iPhone (iOS 16) |
1 |
AnyConnect Client for Testing |
IP and Subnet Information for Config Reference
|
Solution Components |
IP Address |
|
VPN0 |
152.22.241.139 |
|
VPN1 |
10.100.0.9 |
|
ISE |
10.100.0.6 |
|
Certificate Authority |
10.100.0.20 |
Assumption :- SD-WAN overlay is already up and operational. No configuration/workflow specific to overlay bring-up is covered in this document.
3.2 Prerequisites
- RA Headend should be strategically chosen based on product’s remote access scale capacity. Once this decision is made, please ensure it has reachability to CA and ISE server from the given Service VPN(in this case VPN1).
- The VPN0 interface should have a Public IP Address.
- The Internet serving off VPN 0 should allow IPsec traffic.
- For licensing requirements refer to Appendix B: SD-WAN Remote Access Package/ Licensing
3.3 Restrictions
- As of today, this feature can only be configured via Add-on CLI Template for the devices functioning as RA Headend.
- vManage GUI support is in future roadmap as of writing this document.
- RA VPN support is limited to IKEv2/IPsec-based tunnels.
- SSL-based tunnels are in future roadmap as of writing this document.
- The SDRA Headend IP details needs to be manually uploaded in the Cisco AnyConnect Client tray loader by editing the XML Profile.
4. Solution Deployment
This section provides detailed step-by-step instructions to manually deploy the solution from the various components.
4.1 High Level Deployment Workflow
5. Detailed deployment instructions
5.1 CLI Configuration for Addon Template
5.1.1 CLI Configuration required on SDRA router
<< RA IP Pool >>>
!
ip local pool RA_IP_POOL 10.20.55.1 10.20.55.10
ip http client source-interface GigabitEthernet3
!
<< RADIUS and AAA parameters >>>
aaa group server radius RA_RADIUS_SERVER
server-private 10.100.0.6 key 6 OLLgTTceWcQCR_eV_]AB^cHCV[MQhIVPXAAB
ip radius source-interface GigabitEthernet3
ip vrf forwarding 1
!
aaa authentication enable default enable
aaa authentication login default local
aaa authentication login RA_AUTHEN_MLIST group RA_RADIUS_SERVER
aaa authorization console
aaa authorization exec default local
aaa authorization network RA_AUTHOR_MLIST group RA_RADIUS_SERVER
aaa accounting network RA_ACC_MLIST start-stop group RA_RADIUS_SERVER
aaa server radius dynamic-author
!
<< PKI Trustpoint for Certificate Enrollment >>>
!
crypto pki trustpoint SRV1-ROOT-CA
auto-enroll regenerate
enrollment url http://192.168.250.20:80/certsrv/mscep/mscep.dll
fqdn CS5_SDRA-8kv.cisco.com
fingerprint C24D4BD6135E37BF79225B323A67DBAA
revocation-check none
subject-name CN=CS5_SDRA-8kv.cisco.com,OU=SDWAN-LAB,O=Cisco,ST=NC,C=US
!
!
<< IKEv2 Proposal and Policy >>>
!
crypto ikev2 name-mangler ikev2-ra-mangler
eap suffix delimiter @
!
crypto ikev2 proposal RA_IKEV2_PROPOSAL
encryption aes-cbc-256
group 19
integrity sha256
!
crypto ikev2 policy RA_IKEV2_POLICY
proposal RA_IKEV2_PROPOSAL
!
<< Virtual-Template and Loopback Interface >>>
!
!
exit
interface Virtual-Template101 type tunnel
no shutdown
vrf forwarding 1
tunnel mode ipsec ipv4
exit
!
interface Loopback1
no shutdown
arp timeout 1200
vrf forwarding 1
ip address 10.100.76.1 255.255.255.255
ip mtu 1500
exit
!
<< IKEv2 Profile >>>
!
crypto ikev2 profile RA_IKEV2_PROFILE
aaa accounting anyconnect-eap RA_ACC_MLIST
aaa authentication anyconnect-eap RA_AUTHEN_MLIST
aaa authorization group anyconnect-eap list RA_AUTHOR_MLIST name-mangler ikev2-ra-mangler password 6 ]]_AcWMZiCf_gUEVaNLdDY`cCHNXYVEFaaRh
authentication local rsa-sig
authentication remote anyconnect-eap aggregate
match identity remote any
pki trustpoint SRV1-ROOT-CA
reconnect timeout 1800
virtual-template 101
!
<< IPSec Transform >>
!
crypto ipsec transform-set RA_IPSEC_TS esp-gcm 256
mode tunnel
!
crypto ipsec profile RA_IPSEC_PROFILE
set ikev2-profile RA_IKEV2_PROFILE
set transform-set RA_IPSEC_TS
!
<< IPSec Profile to Virtual-Template>>
!
interface Virtual-Template101 type tunnel
tunnel protection ipsec profile RA_IPSEC_PROFILE
5.1.2 CLI Configuration Components and Explanation
5.1.2.1 RA IP Pool
This is a private IP pool on the SD-WAN RA headend router defined by the administrator. Once the IPsec connection is built, the headend assigns an IP address from this pool to the RA clients that are requesting an IP address. RA clients use the assigned IP address as the source IP address for VPN inner traffic.
The same pool name needs to be configured for ISE Authorization as an AV pair.
Ensure to advertise this pool in OMP as a summary-only route. If the SD-WAN RA IP pool summary is not advertised, OMP automatically advertises static host routes for each RA client which are dynamically programmed by the SD-WAN RA headend. This may not be optimal in a large SDRA deployment in SD-WAN fabric.
Please refer to Appendix A: How to advertise RA pool in OMP as a summary-route
Technical Tip: Each SDRA Headend must have a unique RA IP Pool defined. This should strictly not overlap with any other IP subnets within the Service VPN in question. The pool is shared across RA service VPN’s.
5.1.2.2 RADIUS and AAA Parameters
Configure Radius (ISE), define its IP address and shared key and associated VRF it is in.
Also configure Global AAA method lists for authentication, authorization and accounting.
5.1.2.3 PKI Trustpoint for Certificate Enrollment
Certificate Authority issues Digital Certificates. Digital Certificates are verifiable small data files that contain identity credentials to help the SDRA router represent its authentic online identity (authentic because the CA has verified the identity). These digital certificates are used to protect information, encrypt, and enable secure communication.
5.1.2.4 IKEv2 Proposal and Policy
An IKEv2 proposal is a collection of transforms used in the negotiation of IKE SAs as part of the IKE_SA_INIT exchange. An IKEv2 policy contains proposals that are used to negotiate the encryption, integrity, PRF ( pseudo-random functions) algorithms, and DH group in SA_INIT exchange.
5.1.2.5 Virtual Template Interface
A virtual template interface is used to provide the configuration for dynamically created Virtual-Access interfaces. This is a virtual interface which is referenced under the IPsec Profile.
5.1.2.6 IKEv2 Ciphers, Parameters, and Profile
An IKEv2 profile contain non-negotiable repository parameters of IKE SA, such as local or remote identities and authentication methods and the services that are available to the authenticated peers that match the profile.
The IKEv2 profile enables grouping of peers by identity and specifies authentication and authorization policy.
5.1.2.7 Loopback Interface
Configure a loopback interface with some dummy IP address which does not overlap with your network address space. The Virtual-Access interfaces will borrow this IP address.
5.2 Task 1: Provision SDRA Headend – Add Remote Access Configuration using CLI Add-on Template
5.2.1 Attach the CLI Addon Template to the SDRA Headend
The Cat8kv device is already configured and onboarded in SD-WAN. Use this device to integrate SD-WAN RA capability.
Note: Ensure this SDRA headend router is onboarded successfully in vManage and In-Sync status.
- Login to vManage using your login credentials
- Navigate to the menu Configuration > Templates
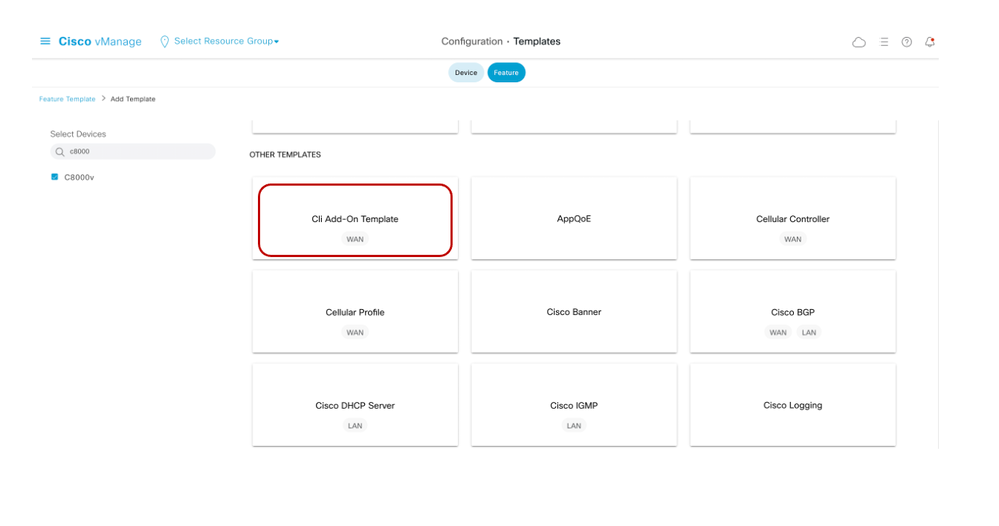
- Click Feature and Select Add Template
- In the search bar enter the PID C8000v followed by Cli-Add on Template under Other Templates
- Enter the Template Name and Description.
- Add the SDRA CLI in this template and save.
NOTE: The Order of Operation to deploy the configuration is to create the Virtual –Template interface first and then mention it under the crypto IKEV2 profile.
For the complete SDRA configuration refer to Appendix C: SD-WAN Remote Access Configuration
5.2.2 Attach Add-On CLI Template to SDRA Headend Router
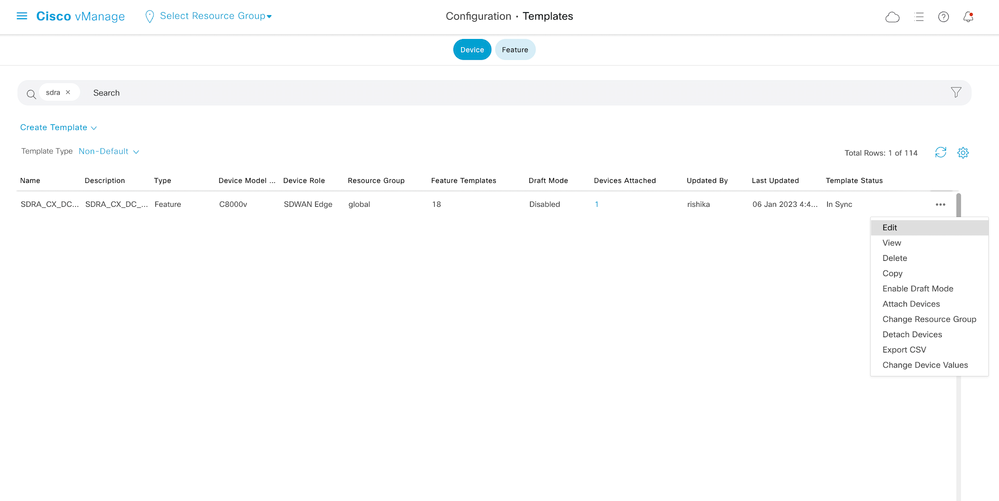
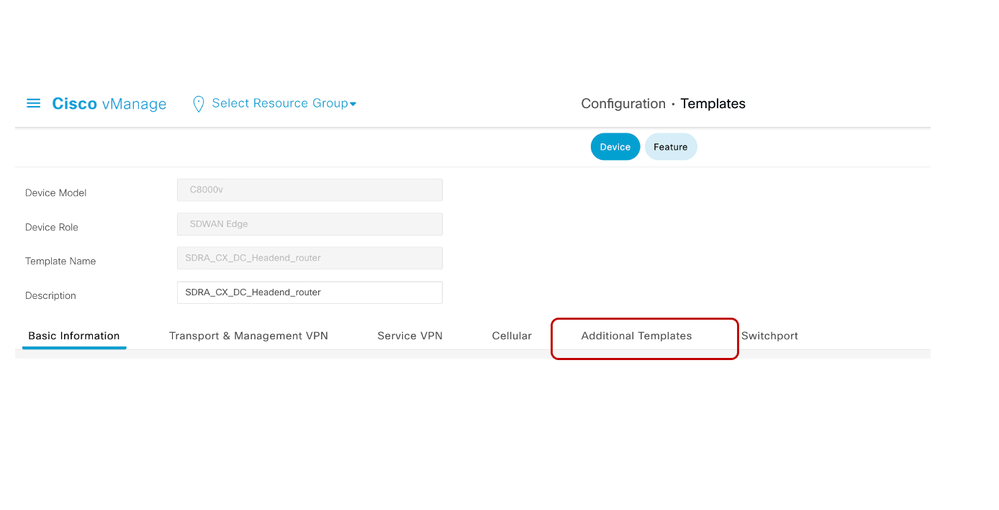
- Navigate to the menu Configuration> Templates
- Search the headend router under Devices, in this case Cat8kv and click on Edit.
- Click Additional Templates on the front menu
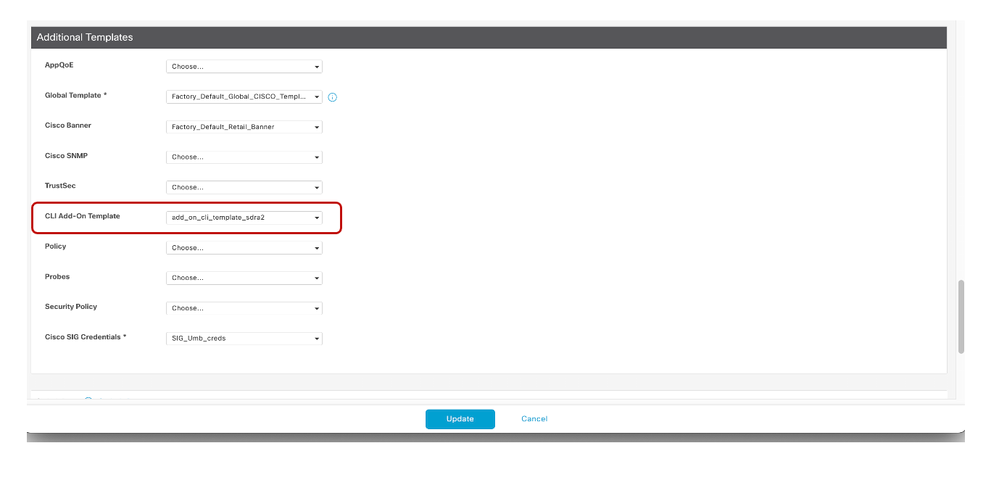
- Choose the newly created add-on CLI Template created and then Update.
- You should see a green status check once this is successfully deployed from vManage.
5.3 Task 2: Configure Cisco Identity Services Engine (ISE)
Cisco ISE is the next generation feature-rich AAA (Authentication, Authorization and Accounting) server with many different NAC features. In the SDRA deployment, ISE is used to authenticate the remote access users and enforce the authorization policies based on the per-user group type.
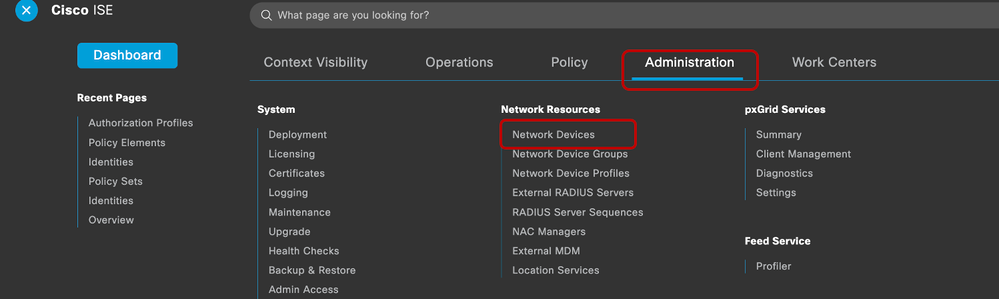
5.3.1 Adding SDRA Headend Network Device
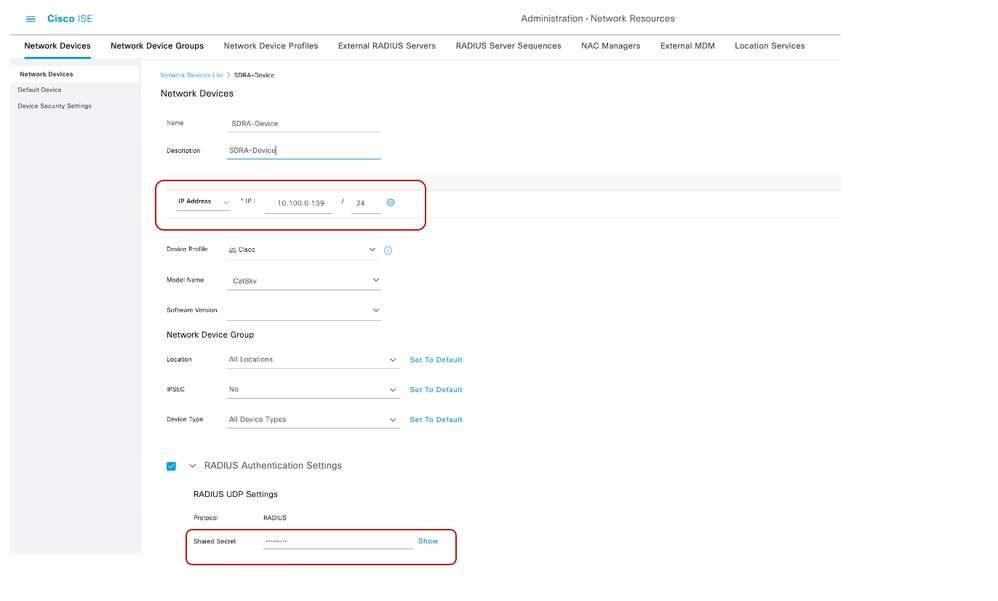
In the ISE GUI, Navigate to Administration > Network Devices and add the RA headend (Edge) IP address and Password as shown in the image.
10.100.0.139 is the IP address of GigabitEthernet3 (interface that connects to ISE) on the RA headend.
5.3.2 Adding Remote Access Client Identity (Credentials)
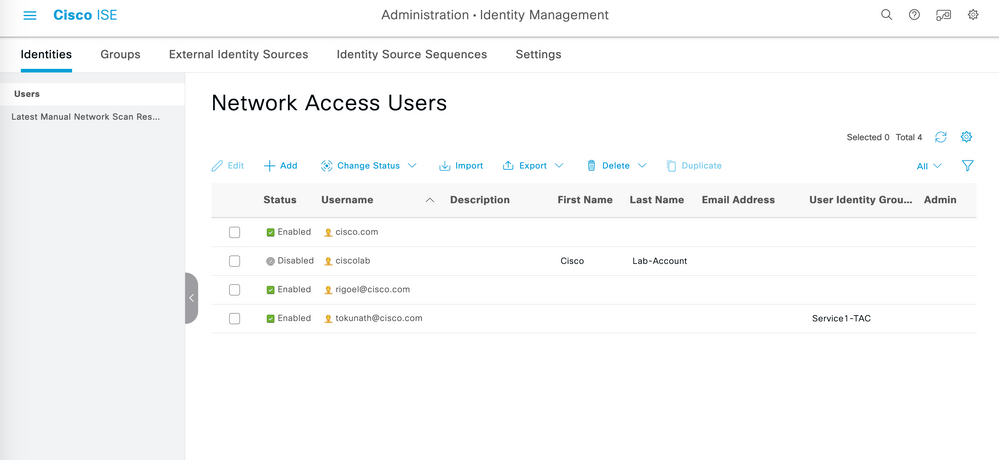
- ISE should be configured with the usernames and passwords for the AnyConnect authentication. This should be configured under Administration > Identity Management > Identities.
- Validate the RA Client username/password created locally on ISE server.
Note: Cisco ISE can also integrate with Active Directory (AD) for RA clients identity and authentication. For the purpose of this documentation, local user identities are created on the ISE server.
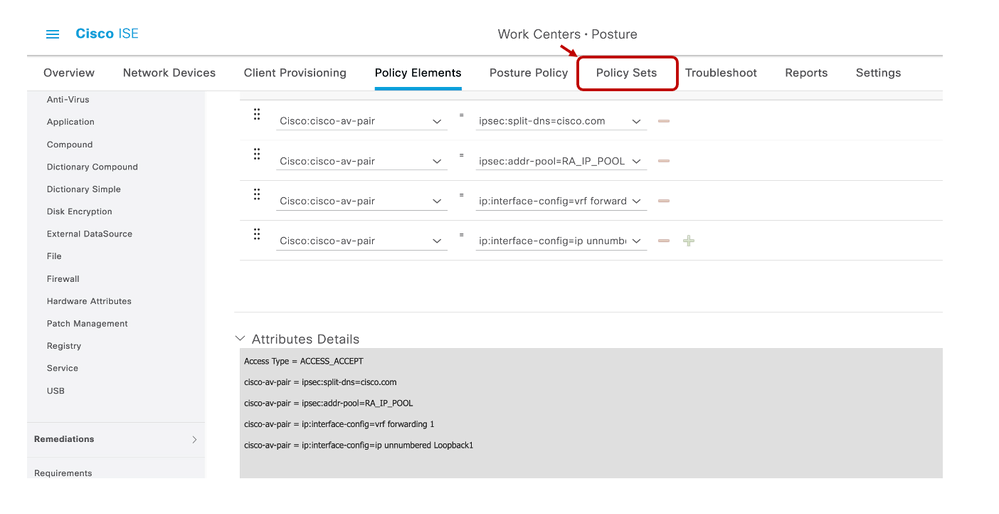
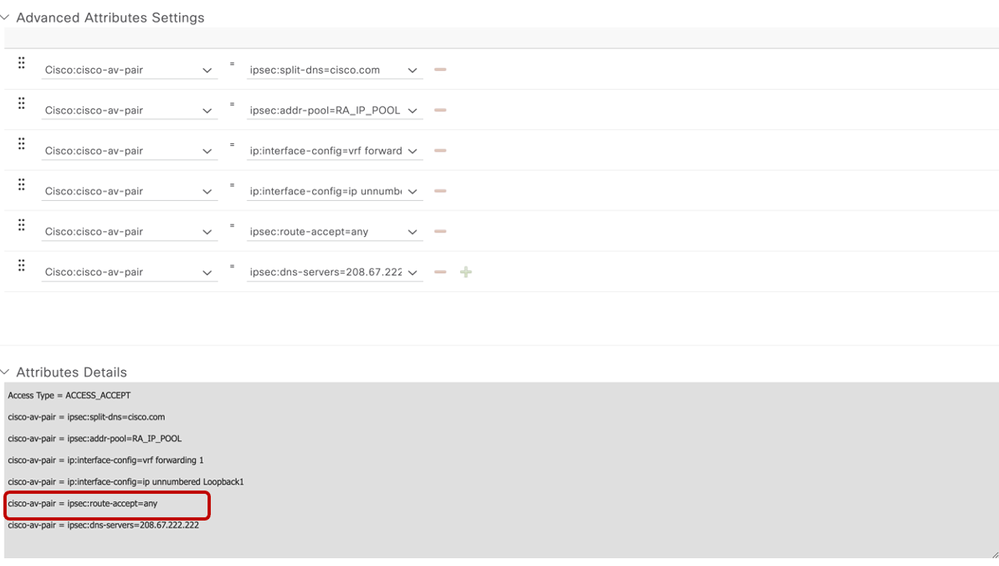
5.3.3 Create Authorization Policy for AnyConnect users
- Create an authorization policy in ISE server: Navigate to the top left side and go to Work Centers > Posture > Policy Elements.
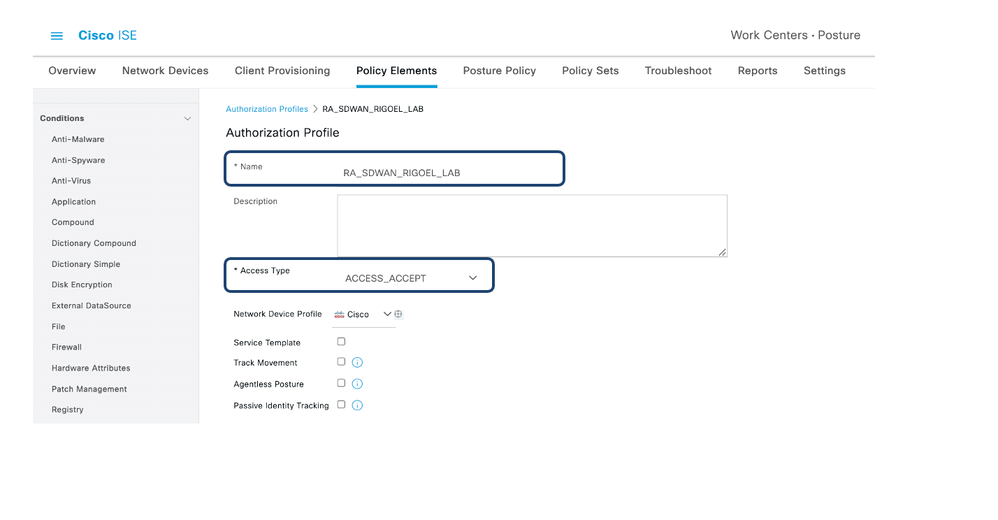
- In the Authorization Profile, Add the profile.
- Configure the Access Type as Access_ACCEPT
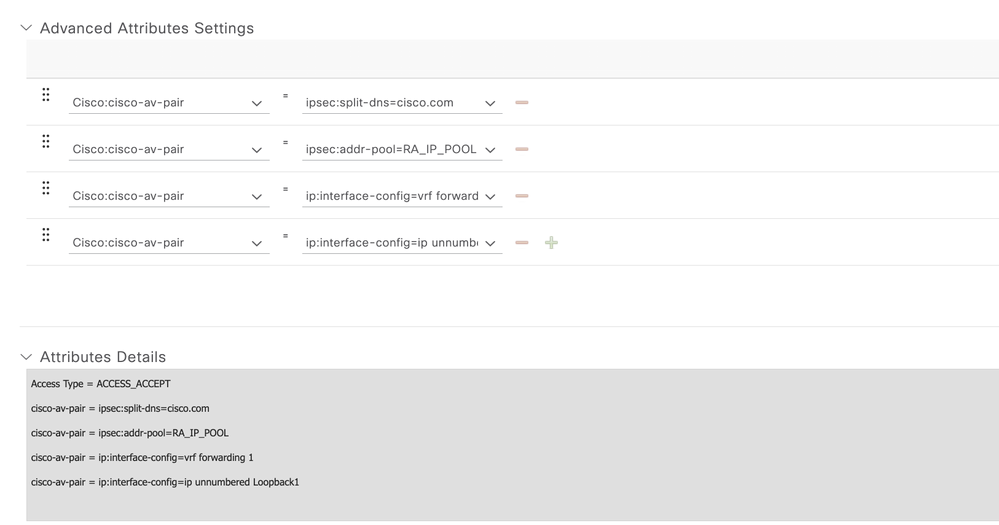
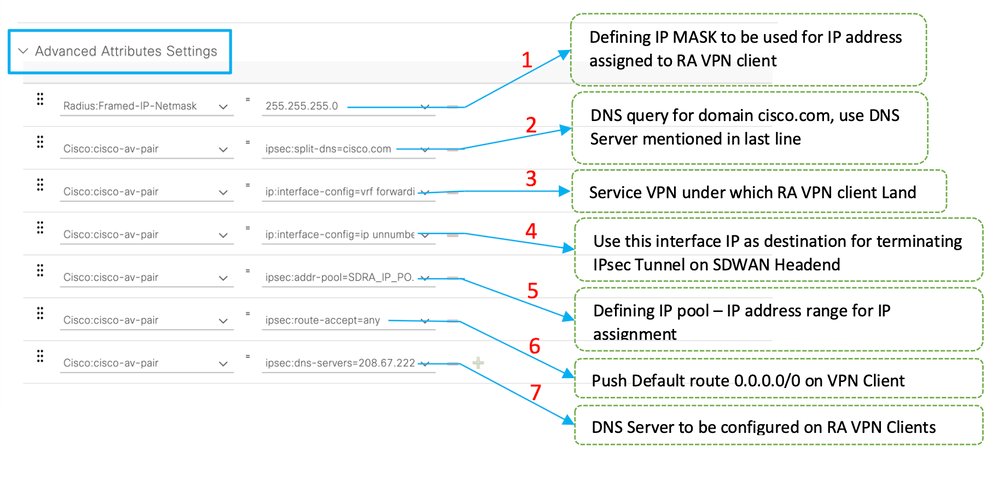
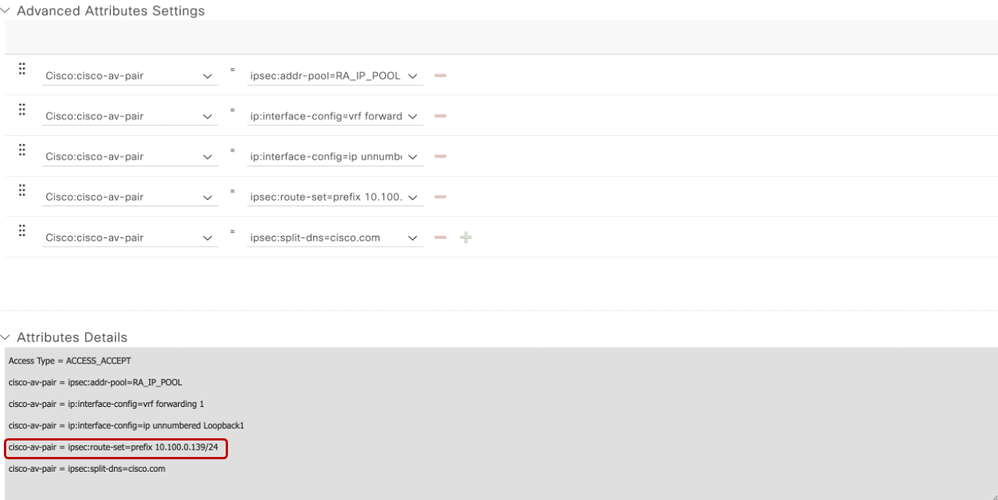
- Under the Advanced Attributes Settings, select the Cisco vendor and Cisco-AV-pair attributes for the remote access user.
It is necessary to configure the following policy parameters for the users:
- VRF, the Service VRF to which the user belongs.
- IP pool name where each user connection is assigned an IP address that belongs to the IP pool configured in the Edge router.
- Subnets that the user can access
- Domain (in this case, cisco.com)
- Split tunneling (by configuring explicit service side subnets) or tunnel all traffic (by configuring route-accept as any).
- For explicit prefixes configured for split tunnelling, this would be the destination traffic that remote users will be routed against.
5.3.4 Create a Policy Set to enforce the authorization policy against the user type
A Policy Set should to be created with the match condition to hit as shown in the image.
- Navigate to the top left side and go to Work Centers > Posture > Policy Sets.
- For allowing default authentication select All_User_ID_Stores.
- Select the authorization policy that was created for users/identities.
- As soon as the authentication happens for the user, the authorization against that user is triggered.
- This allows the user to be a part of a specific VRF, to get an IP address from a given defined pool, and network access is allowed in either split tunnel or full tunnel mode (as per configuration).
Note: The ISE server must be reachable from the SD-WAN RA headend in the service VPN.
5.4 Task 3: Configure Cisco AnyConnect Client for testing
5.4.1 AnyConnect Client Installation
The remote users need to have the AnyConnect Software Client on their system. The remote use could be using any of the following:
- Desktop PC or Laptop
- MAC
- Windows
- Mobile or Tablet
- iOS
- Android
Note: Software version (4.10.06079)
There are pre-deployment packages available for download. Please refer to the following link to download the relevant software.
5.4.2 Download and Install the Cisco AnyConnect Profile Editor
The AnyConnect Client uses SSL as the default protocol for tunnel establishment, and this protocol is not supported for SD-WAN RA (Road map). RA uses FlexVPN, therefore IPsec is the underlying protocol used and it is mandatory to change it. This modification is done in the XML profile.
The software used for editing the AnyConnect profile is known as Cisco AnyConnect Profile Editor. It is a program that enables you to create and configure one or more AnyConnect Secure Mobility profiles. Profiles are deployed to administrator-defined end user requirements and authentication policies on endpoints as part of AnyConnect, and they make the preconfigured network profiles available to end users.
Note: The AnyConnect Profile Editor is only available for Windows machines.
In order to configure a XML profile in MAC, it is necessary to edit an existing XML profile manually.
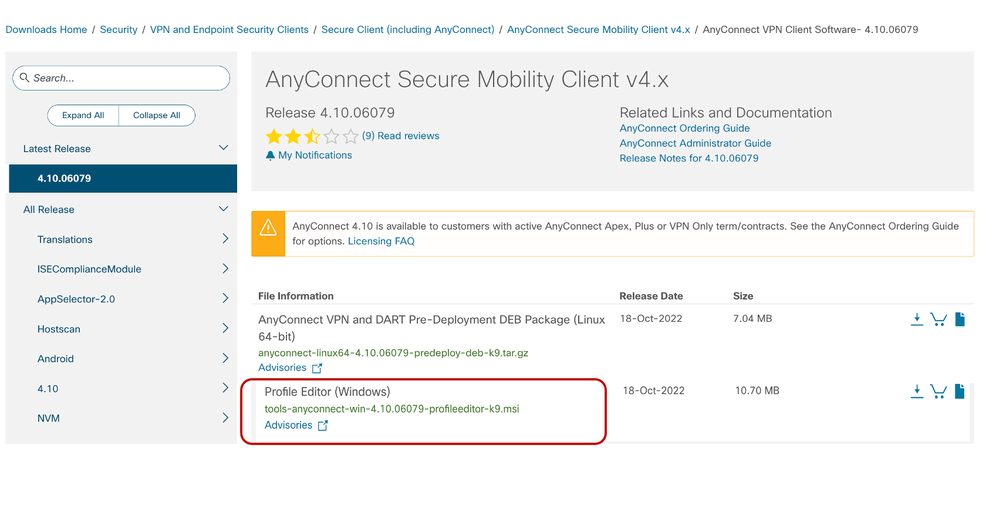
- Download Cisco AnyConnect Profile Editor.
- Go to https://software.cisco.com/download/home/283000185 (Downloads Home/Security/VPN and Endpoint Security Clients/Secure Client (including AnyConnect). Select AnyConnect Secure Mobility Client v4.x
Select version 4.10.06079 (or later), then select Profile Editor (Windows) - Perform the installation.
5.4.3 Modify the Cisco AnyConnect Profile using Profile Editor
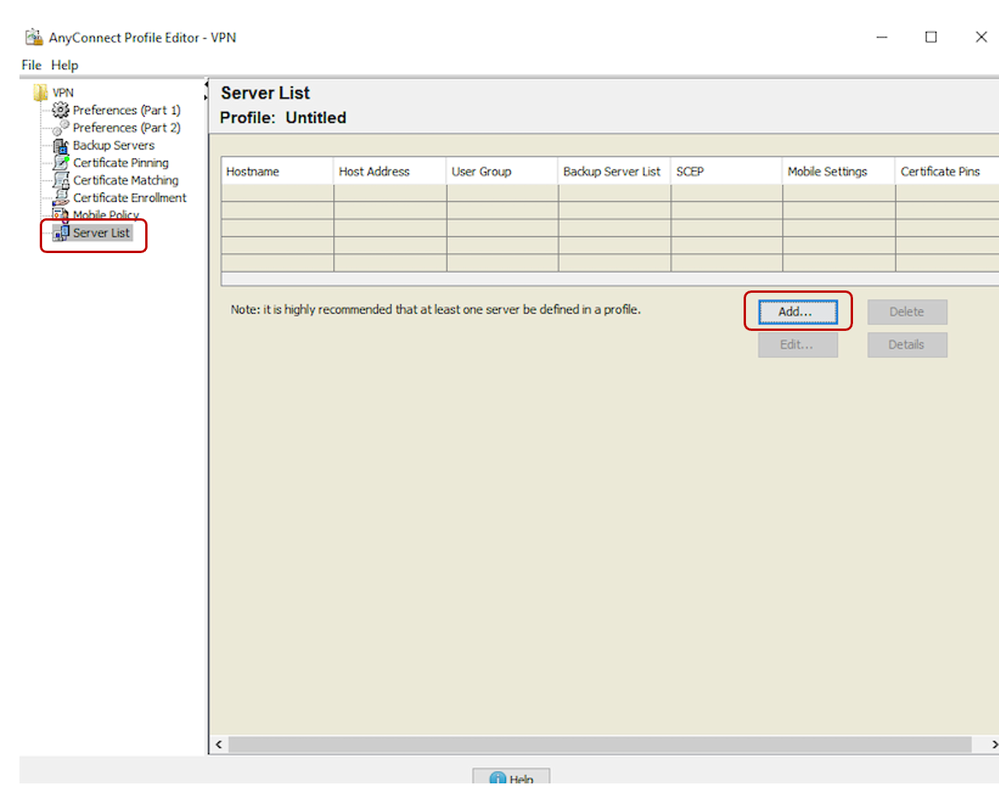
- Open the Cisco AnyConnect Profile Editor
- Navigate to the Server List and click Add as below.
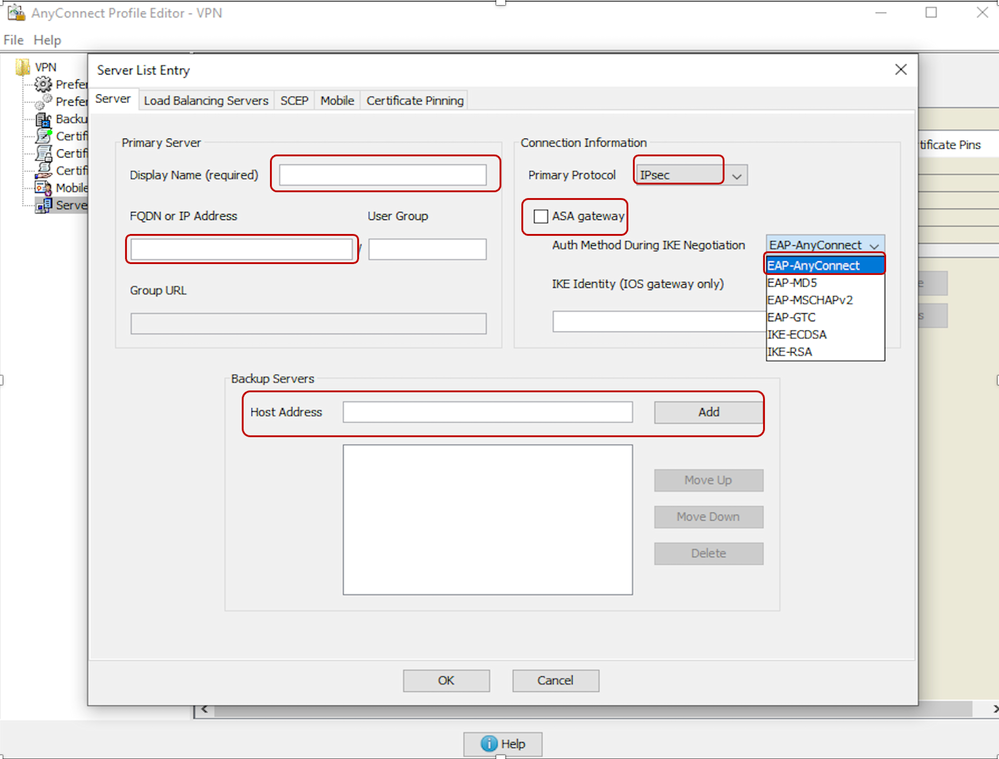
- Select IPsec as "Primary Protocol".
- Uncheck the ASA gateway option.
- Select EAP-AnyConnect as the “Auth Method During IKE Negotiation”.Display/Name(Required) is the name used to save this connection under the AnyConnect client.
- FQDN or IP Address must be filled in with the Edge router (Public) IP Address.
- Additionally, you can add backup servers (host IP address).
This can be a high availability cluster (second RA headend at the same site).
- Save the profile.
The following snapshot shows the XML equivalent of this profile:
Note: By default, the xml profile is saved in “My Documents” folder.
- The XML profile needs to be manually put into the following directory:
- For Windows:
C:\ProgramData\Cisco\Cisco AnyConnect Secure Mobility Client\Profile - For MAC OS:
/opt/cisco/anyconnect/profile
- For Windows:
Note: In case the above files are not visible, it may be required to edit the folder settings to show hidden files.
- Restart the AnyConnect client in order for the profile to become visible in the GUI.
The process can be restarted by right-clicking the AnyConnect icon in the Windows tray and selecting the "Quit" option.
5.4.4 Disable the AnyConnect Downloader
By Default, The AnyConnect client tries to perform download of the XML profile after successful login. If the profile is not available, the connection fails.
As a workaround, disable the AnyConnect profile download capability on the client itself.
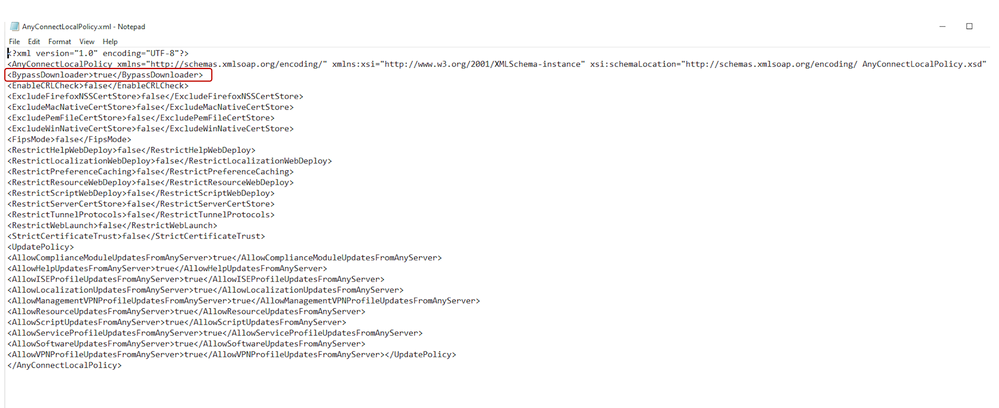
- Open the AnyConnectLocalPolicy.xml file
- For Windows:
C:\ProgramData\Cisco\Cisco AnyConnect Secure Mobility Client\AnyConnectLocalPolicy.xml - For MAC OS:
/opt/cisco/anyconnect/AnyConnectLocalPolicy.xml
- For Windows:
- Set the "BypassDownloader" option to "true"
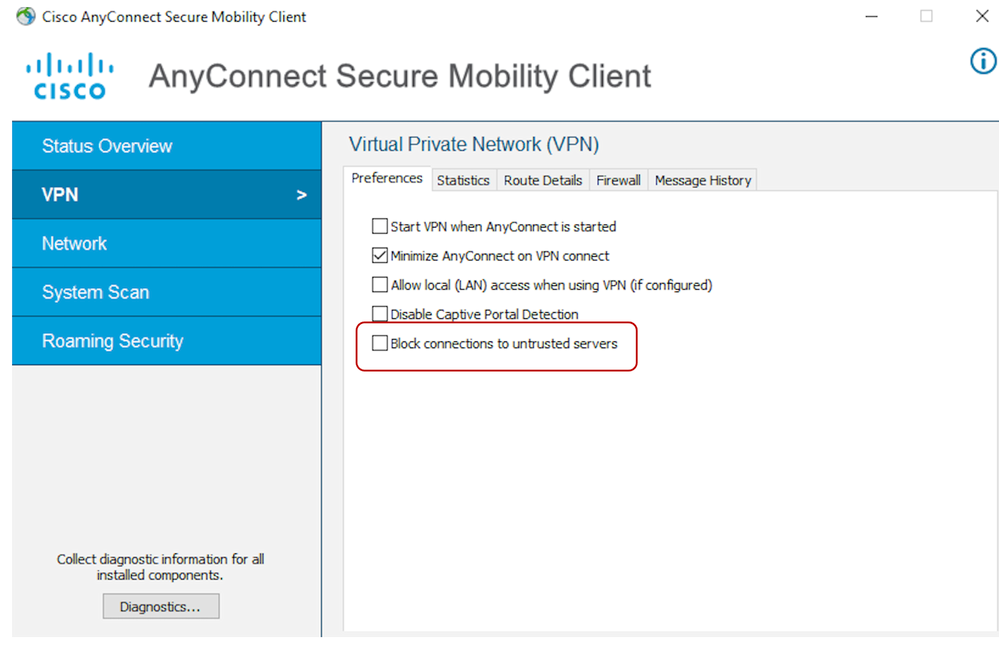
5.4.5 Unblock Untrusted Servers (Optional)
Since the CA server used in Lab Validation is not a public entity like GoDaddy, Symantec, Cisco, etc, the client will interpret the SDRA Headed as an untrusted server.
NOTE: In production deployment, This will be fixed using a Public Certificate or CA server.
For the purpose of the testing, we can uncheck the option that blocks connections to untrusted servers.
In the AnyConnect VPN Client, navigate to
Settings> Preferences and uncheck the “Block Connections to untrusted servers” option.
The certificate used for RA headend/Edge router authentication is the one previously created and signed by the CA server in IOS-XE.
5.4.6 Validate the Connectivity to SDRA Headend
The validation for SDRA connectivity has been successfully completed on:
- Windows 10
- Windows 11
- MAC OS 13.1 Ventura
- iOS 16
- Android OS 13
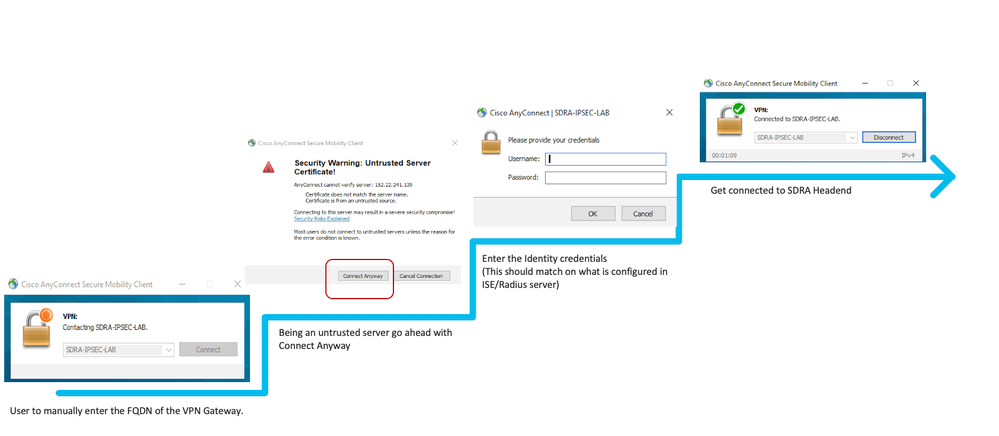
The following is the step-by-step procedure to connect to an SDRA headend:
- Enter the FQDN / IP for the SDRA headend in the AnyConnect client.
- If prompted to accept an untrusted server certificate, click on Connect Anyway.
- Enter your credentials when prompted and click OK.
- Wait a few seconds to allow the connection to complete, until you see the Connected to <DQDN> message.
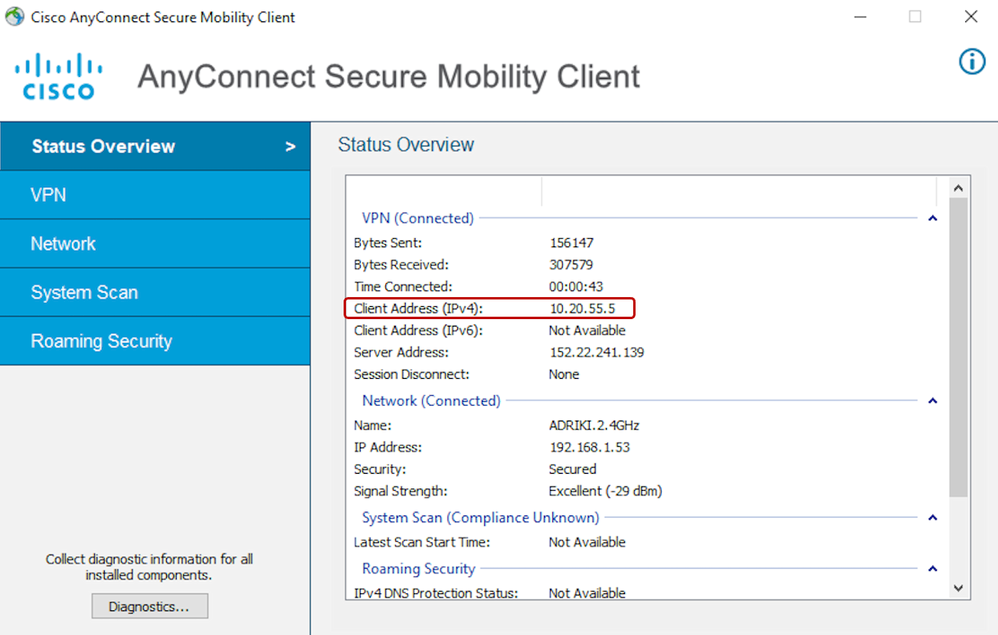
- For further validation:
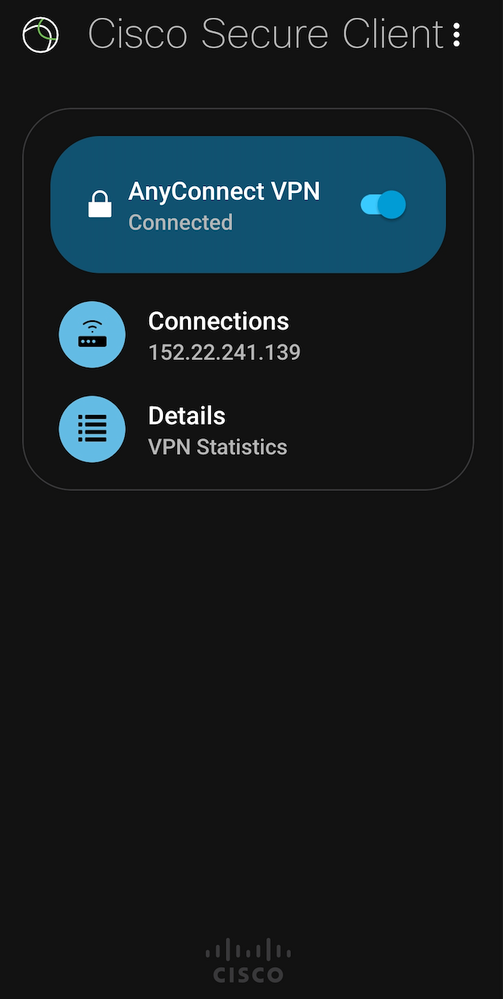
- Check the VPN Client “Status Overview” and allocated IP address.
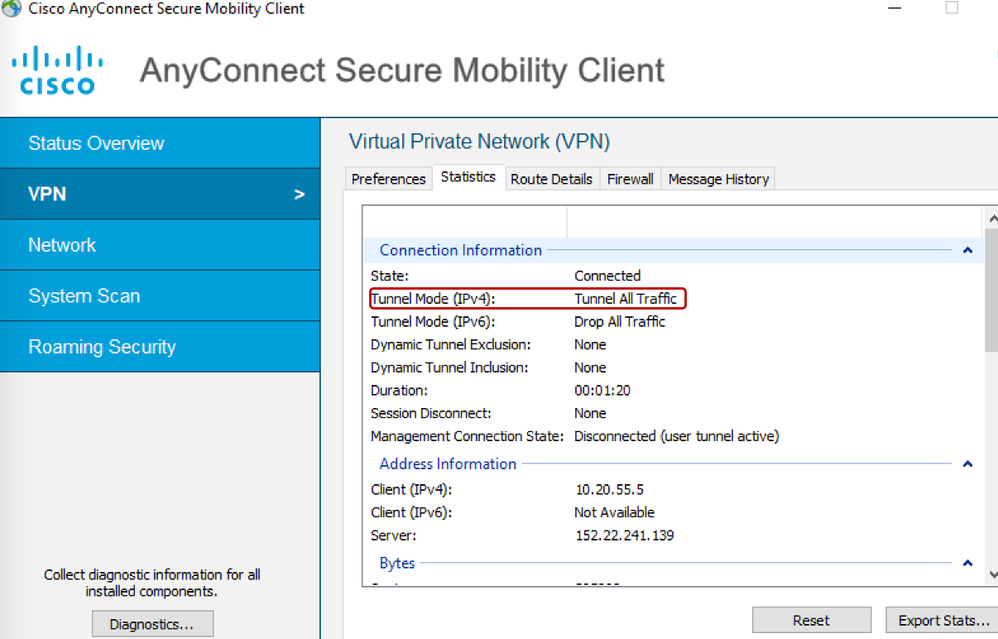
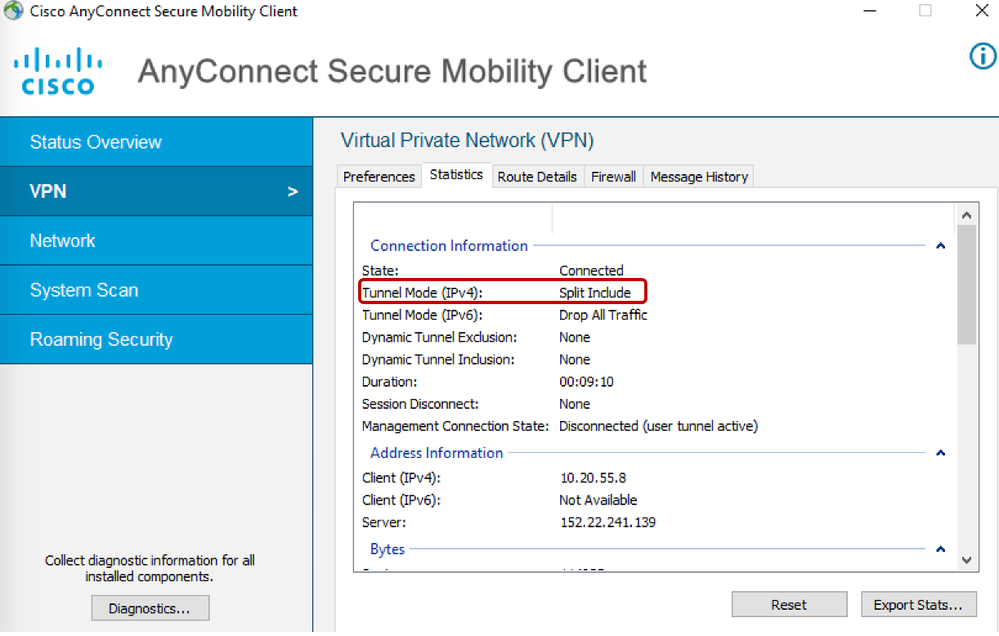
- Verify the VPN Tunnel mode under VPN>Statistics and look for Tunnel Mode IPv4
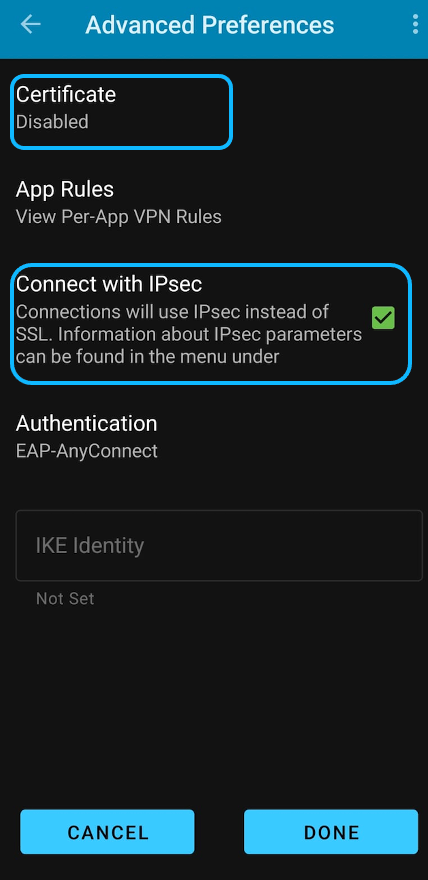
NOTE: For Mobile Devices, it’s important to Disable Certificate check and enable Connect with IPsec (and not SSL), under advanced settings in the phone as shown below.
|
|
|
6. Solution Planning
6.1 RA Headend Platform selection/dependencies
Several factors must be considered, and several questions should be answered when choosing the appropriate SD-WAN RA Headend platform for a site.
Some of these questions include but are not limited to following:-
- Type of SDWAN Edge Router
- Physical / Hardware Based
- Virtual / Software based
- Selected Platform’s Hardware and Capability
- Maximum Amount of IPSEC Sessions
- Maximum Throughput with IPSEC Sessions
- Use of Cryptographic Accelerator
- WAN Bandwidth Available
- Total Throughput capacity
- Total Number of IPsec connections terminating on this device? (This should be shared between SD-WAN IPsec/BFD and IKEv2/IPsec RA)
- Per User Considerations
- Total Number of Remote Access connections (including SDRA IPSEC and SDWAN IPSEC)
- The throughput for each SDRA User
- Planning Feature Deployment, Scalability and High Availability
- Is it going to be Active/Active IKEv2 cluster bases the RA load or Active/Backup scenario?
- Planning additional capacity at a site based on the above requirements?
- Are redundant headend routers necessary/available to meet high availability targets?
- Will the RA Headend WAN Edge need to provide advanced branch features such as on-prem security or need to support host compute modules for local virtual machines?
Based on careful evaluation, the decision can be taken to either continue using the existing infrastructure or to add more capacity.
Note : The maximum number of IPsec sessions supported on a Cisco IOS XE SD-WAN device is shared between Cisco SD-WAN IPsec/BFD and SDRA IPsec sessions. Similarly, the IPsec throughput capacity of a device is shared between Cisco SD-WAN and RA IPsec.
6.2 Port and Protocol Information for Firewalls
If your SD-WAN RA headend is sitting behind a firewall, the firewall must allow the following ports and protocols in the inbound and outbound directions:
Inbound:
- IKEv2: UDP ports 500 and 4500
- IPsec: IP protocol ESP
- TLS: TCP 443
- Source IP address: Any
- Destination IP address: SD-WAN RA headend public IP
Outbound:
- IKEv2: UDP ports 500 and 4500
- IPsec: IP protocol ESP
- TLS: TCP 443
- Source IP address: SD-WAN RA headend public IP
- Destination IP address: Any
6.2 Site Scale Requirements
The SDRA feature does not introduce any additional scale numbers but utilizes the existing scale capability of the platforms. The total IPsec Tunnels are divided amongst SD-WAN and SDRA.
From a design and deployment standpoint - If the SD-WAN sessions remains constant, then the remaining scale can be used by remote access. Overall, the platform limit can be distributed to accommodate to its complete platform limit in whatever way the admin wants.
The following scale numbers have been validated for 17.7 release.
|
Platform |
IPSec Tunnel Limit |
SD-WAN + RA IPSec Tunnels |
|
C8500-12X ( Ramones) |
8000 |
4000 + 4000 |
|
C8500-12X4Q ( Greenday) |
8000 |
4000 + 4000 |
|
C8500L-8S4X ( Fugazi) |
8000 |
3000 + 3000 |
|
C8300-1N1S-6T ( Thallium) |
6000 |
3000 + 3000 |
|
C8300-2N2S-6T ( Uranium) |
6000 |
3000 + 3000 |
|
c8000v ( ESXi, 16 vCPU 32GB RAM) |
2000 |
1000 + 1000 |
6.3 RA Client Dependencies
Before RA Clients can connect to the SDRA headend, the clients must be configured with either the DNS names or the IP addresses of the SD-WAN RA headend devices. This includes primary as well as backup devices; considering that backup devices have been configured in SDRA site design and deployment.
Address used on SDRA Headend - In a scenario where RA clients connects by public Internet, the address on the SDRA headend is a static public IP address. In a scenario where RA clients connect by private WAN, the address on the SDRA headend is a private IP addresses.
Proximity to the SDRA Headend - Proximity to remote users should be considered during the design and deployment phase to ensure optimal user experience. Remote users should ideally connect to their closest RA headend. In case of travel or location change, the closet SDRA headend should be used for connectivity.
Support for SSL Based VPN’s – As of the current release and roadmap at the time of writing this document, only IPsec connectivity is supported. SSL-based VPNs are not supported.
7. AnyConnect Traffic Use case
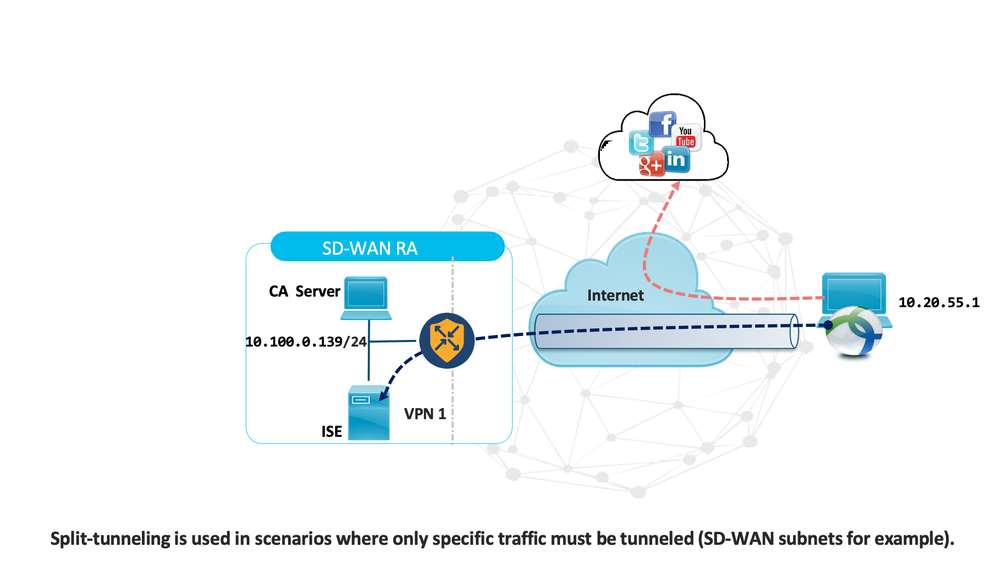
The SDRA Solution allows customizable traffic profiles for AnyConnect, be it routing all traffic over the IPsec tunnel to the SDRA headend (full tunnel) or only routing specific prefixes over the SDRA headend and the rest of the traffic via local internet (split tunnel).
7.1 Use Case 1 - Split Tunnelling
VPN split tunnelling enables routing for certain device traffic through the encrypted VPN tunnel and the rest of the traffic through a separate tunnel on the open network.
The VPN traffic prefixes are identified by the route-set AV pair(s) defined on ISE.
7.1.1 Split Tunneling Workflow on ISE
The subnets required to be tunneled over VPN should be defined as AV-Pairs on Cisco ISE.
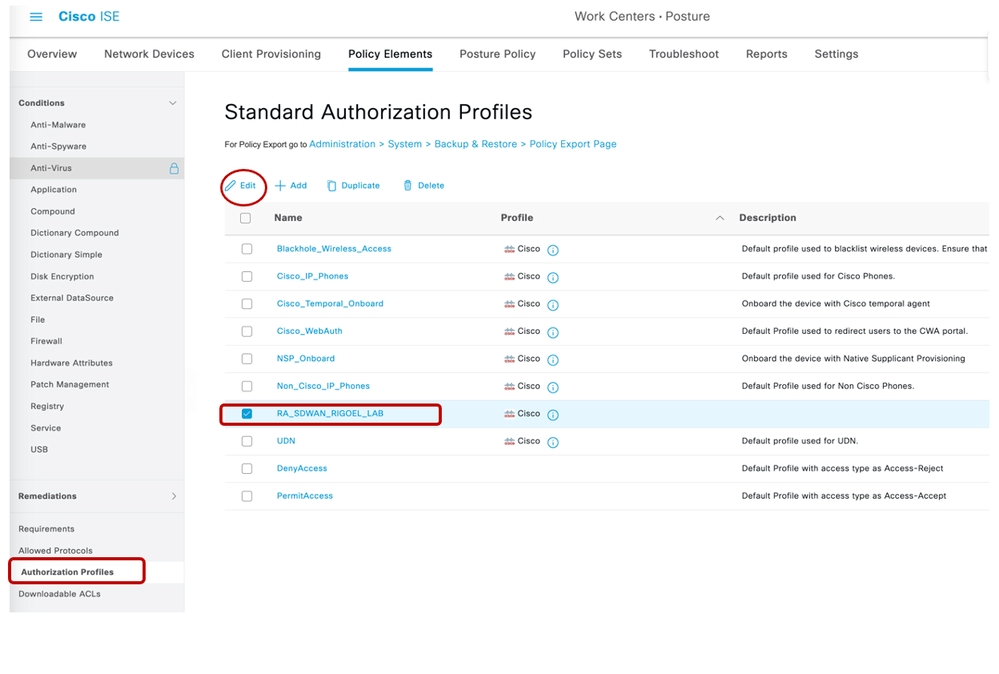
- Navigate to the following path in ISE - Work Centre > Posture > Policy Elements.
- Navigate to Authorization profile and select the target profile by clicking on checkbox and click on Edit
- Edit the authorization profile by adding the Subnets that needs to be Tunneled. These include your service-side subnets.
- This is done by adding the Cisco AV Pair named cisco-av-pair = ipsec:route-set=prefix 10.100.0.139/24
Note: 10.100.0.139/24 is the Service VPN 1 subnet as used in the lab topology.
You can add more than one/multiple prefixes, just need to add another set of cisco-av-pair for each prefix and keep adding it under the same authorization policy.
This prefix doesn’t necessarily has to be something on SDRA Headend but anywhere within the SD-WAN network that You want to reach to.
7.1.2 Split Tunnelling - Workflow on SDRA Router
From the SDRA headend standpoint, no additional configuration is required.
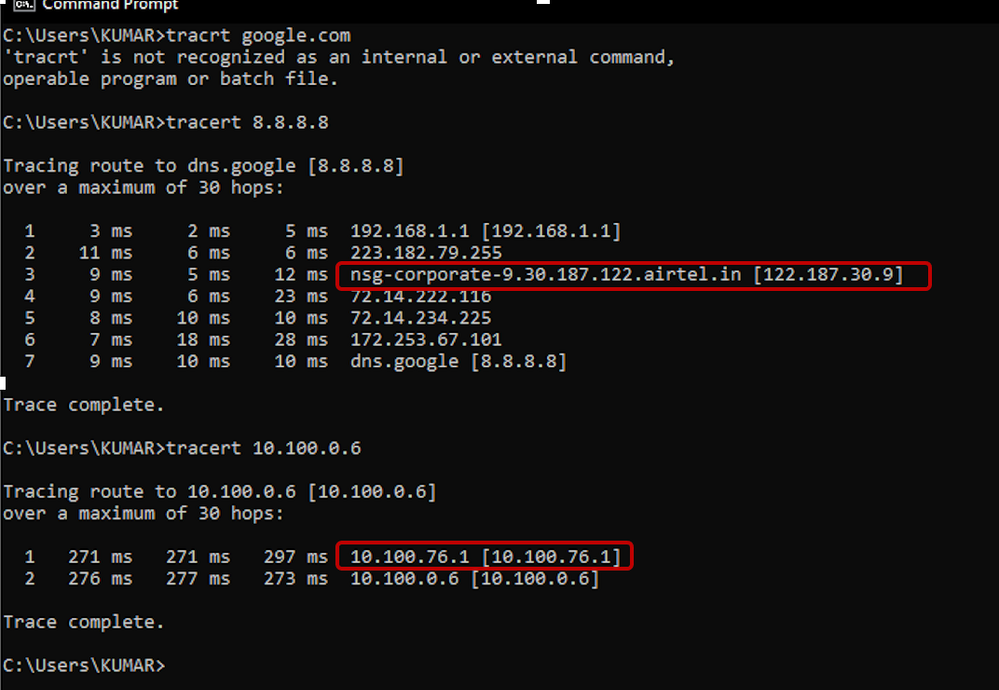
7.1.3 Split Tunnelling – Verification on from Remote Access Client
- Traceroute an external IP address in the public domain / Outside the Data Centre (ISE) .
- Verify that the next hops / path is leading to local Internet service provider network.
- Traceroute an internal IP address and within the Data Centre (ISE) .
- Verify that the next hop is the Virtual-Access Interface on the SDRA Router.
- Verify that the next hop seen on client device is located on the SDRA headend router.
- Open the AnyConnect Client and verify the Tunnel Mode under VPN > Statistics.
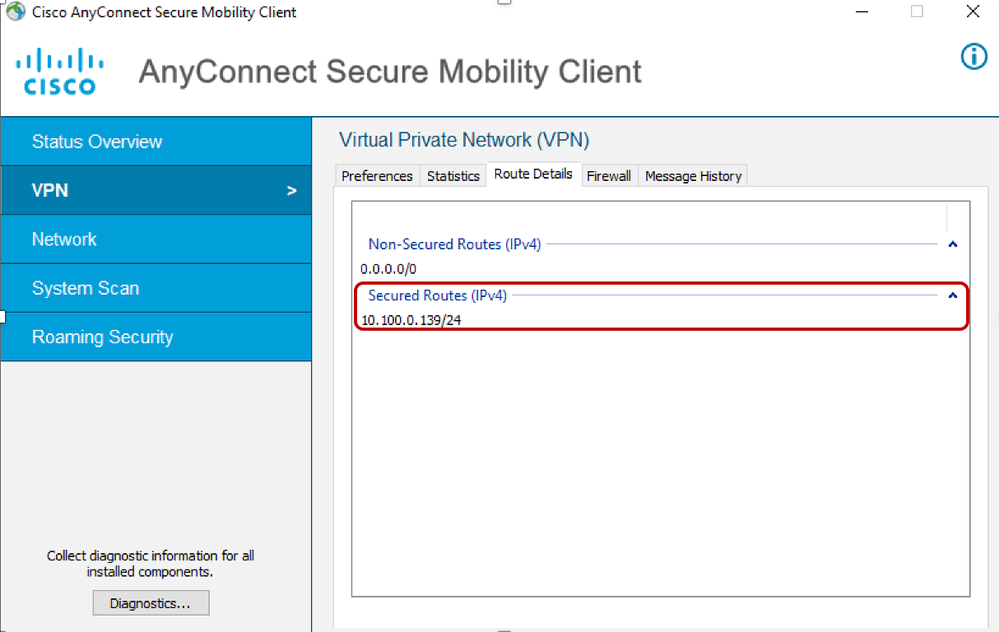
- Examine how the authorization policy has been enforced by the AnyConnect client. Under Route Details, the Cisco av pair pertaining to ipsec:route-set=prefix x.x.x.x will show up as secured routes for the user.
7.2 Use Case 2 - Tunnel All
7.2.1 Tunnel All - Workflow on ISE
Edit the authorization profile by adding aCisco AV pair named cisco-av-pair = ipsec:route-accept=any
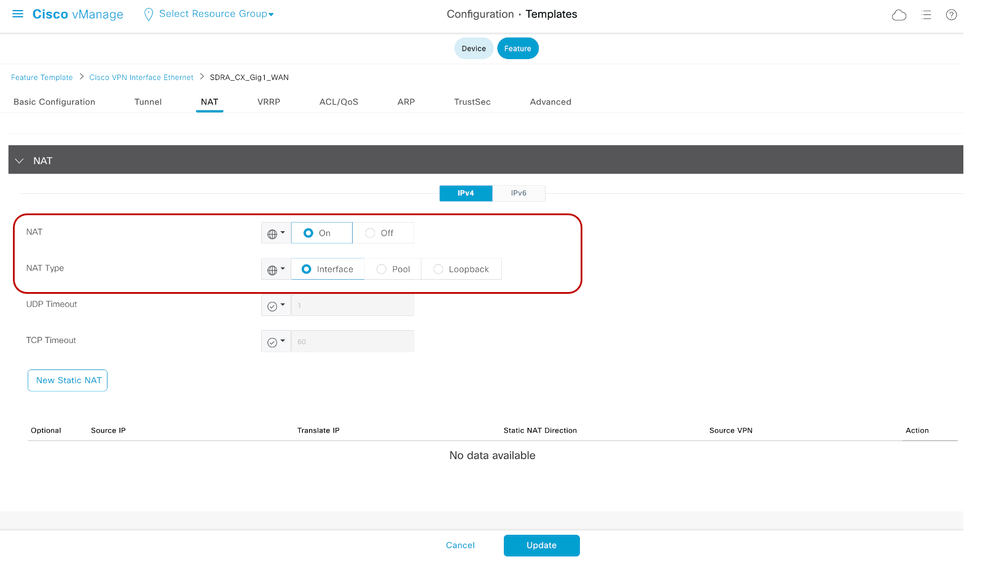
7.2.2 Tunnel All - NAT-DIA Workflow on SDRA Router
For sending all the traffic (including Internet traffic) via the secure tunnel, the SDRA router needs to be configured for NAT.
The below procedures show how to enable NAT-DIA for service VPN 1. If NAT-DIA is already configured, skip to procedure 7.3.
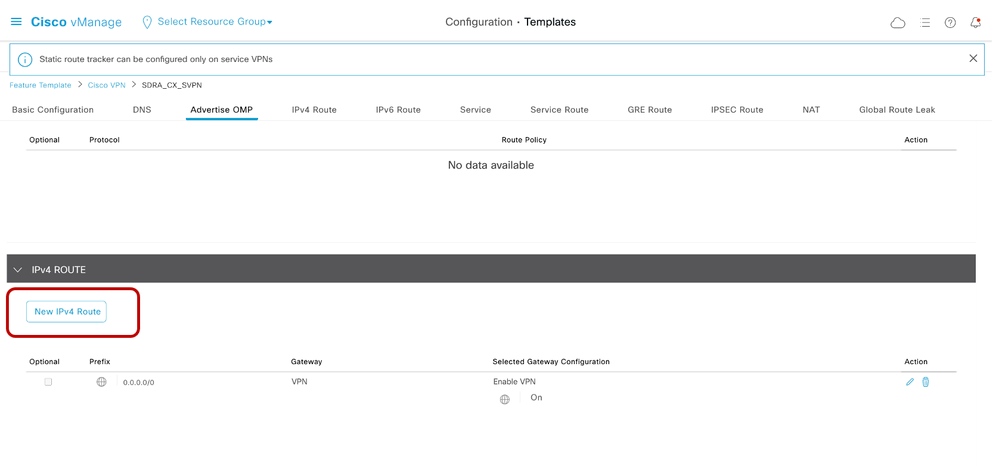
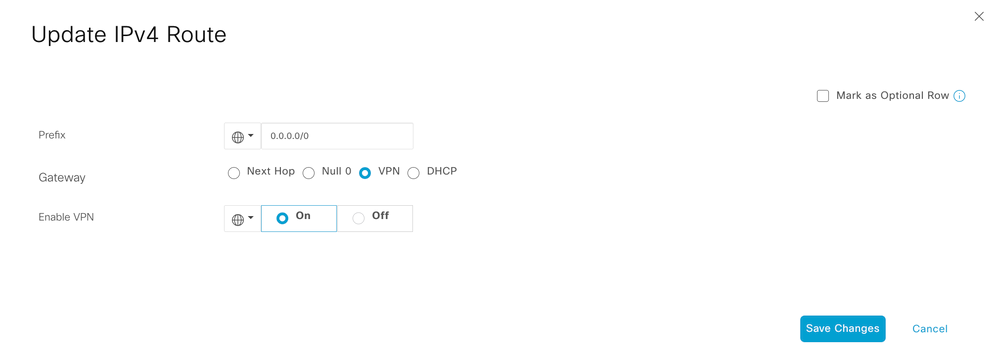
- Edit the existing Service VPN1 template to point the default route towards VPN 0.
- Update the next hop towards VPN 0.
- Edit the existing Cisco VPN Interface template for the WAN GigabitEtherent1 interface, which connects to the Internet transport.
7.2.2.1 Equivalent CLI Generated for NAT-DIA on SDRA
Interface GigabitEthernet1
ip nat outside
!
ip nat inside source list nat-dia-vpn-hop-access-list interface GigabitEthernet1 overload
!
ip nat route vrf 1 0.0.0.0 0.0.0.0 global
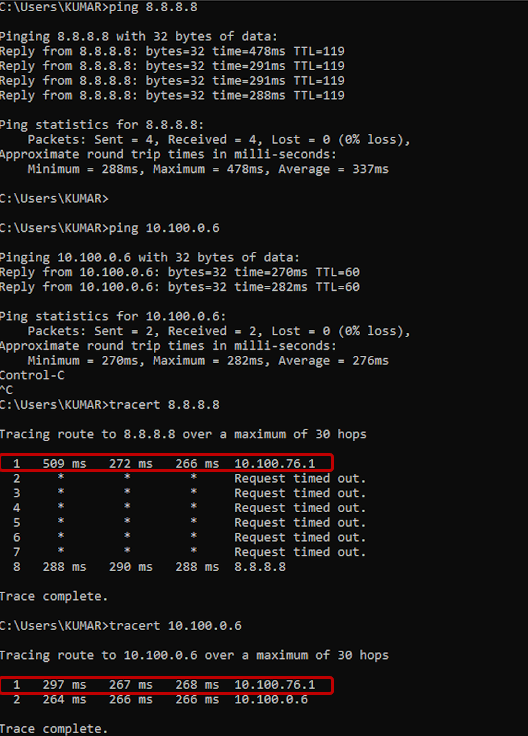
7.2.3 Tunnel All - Verification on Remote Access Client
- Traceroute an internal IP address and within the Data Centre (ISE) .
- Verify that the next hop is Virtual-Access Interface on the SDRA Router.
- Traceroute an External IP address in Public Domain / Outside the Data Centre (ISE) .
- Verify that the next hop is Virtual-Access Interface on the SDRA Router.
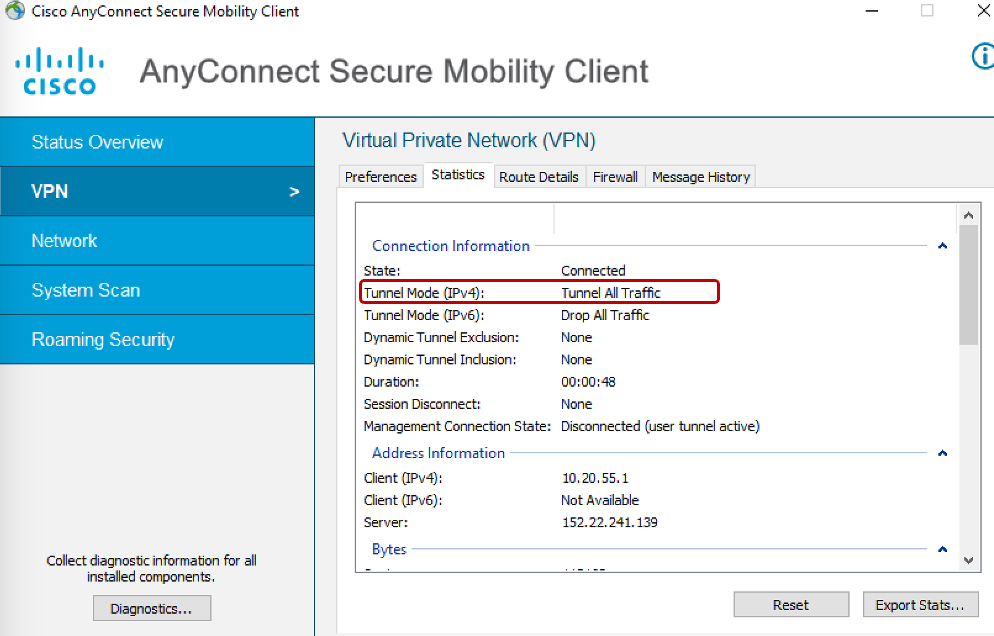
- Open AnyConnect Client and verify the Tunnel Mode under VPN > Statistics
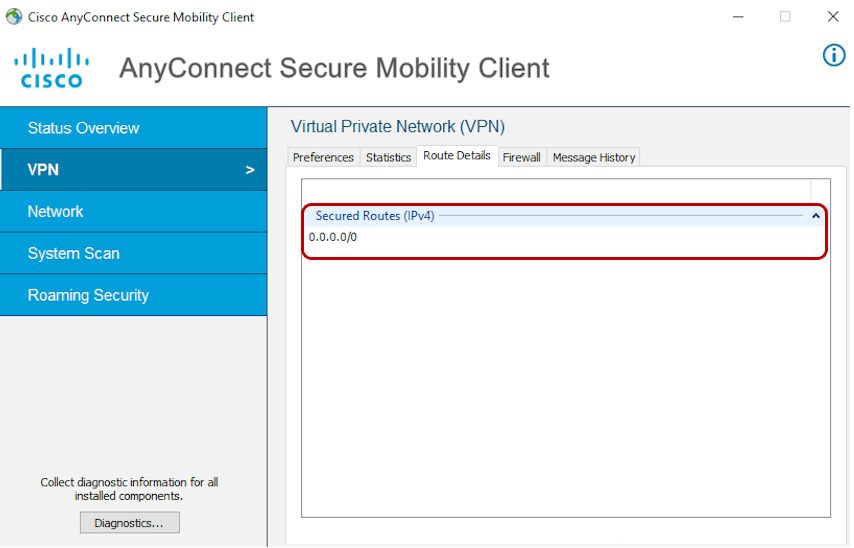
- Under Route Details, 0.0.0.0/0 should be visible.
7.3 Use Case 3 - Umbrella Integration with SDRA
The SDRA solution can be used alongside a the Umbrella Secure Internet Gateway (SIG) service.. In the following use case, the remote access user will be connected to Umbrella SIG through the SDRA headend to reach the Internet.
The admin needs to create SIG Templates and attach it to the SDRA device. This creates Umbrella SIG tunnels to locally breakout to the Internet to securely access SaaS applications/internet applications. The home remote access user can now have cloud-delivered security provided by Umbrella.
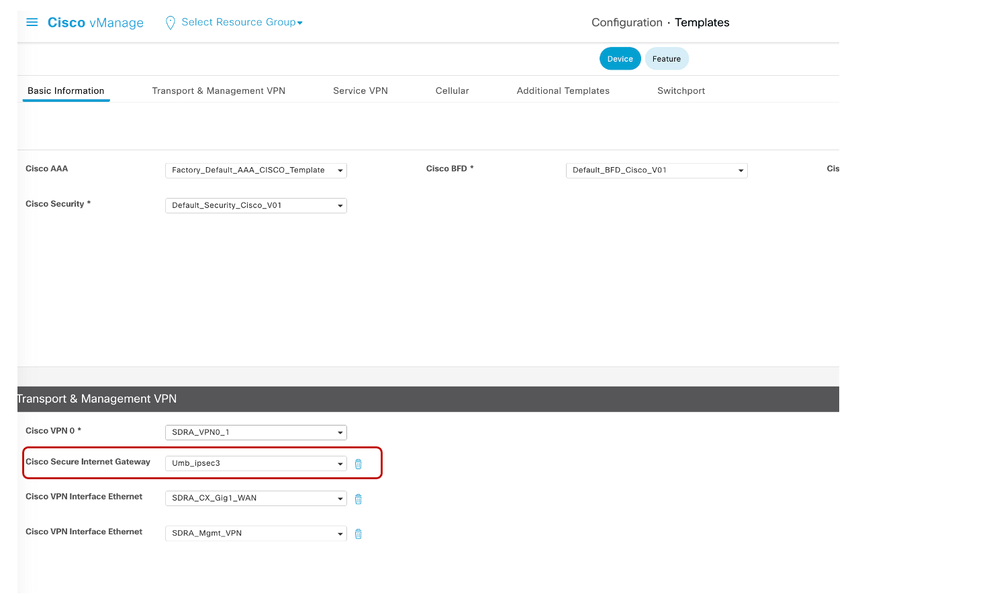
Any Umbrella customization to secure the remote user (URL filtering malicious URL’s, social networking sites, gaming, etc.) can be performed via the Umbrella dashboard in a few clicks. Attach SIG Feature and SIG credentials template to SDRA Router
- In the vManage GUI, navigate to Configuration>Templates and select the SDRA router and click on the three dots on the right to select Edit.
- Add the SIG Feature and Credentials Template to the SDRA router.
(Refer to Appendix D – SIG Credentials/Feature Template Configuration )
- Click Update.
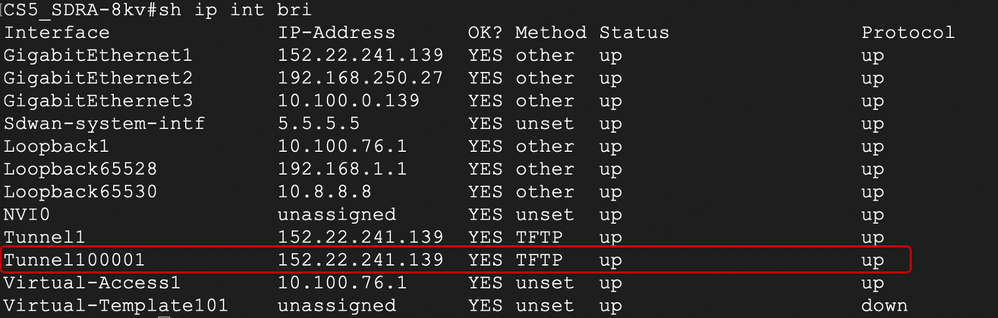
7.3.1.1 Verify the Umbrella SIG Tunnel Status on SDRA Headend
CS5_SDRA-8kv#show crypto session
Interface: Tunnel100001
Profile: if-ipsec1-ikev2-profile
Session status: UP-ACTIVE
Peer: 146.112.83.8 port 4500
Session ID: 10
IKEv2 SA: local 152.22.241.139/4500 remote 146.112.83.8/4500 Active
IPSEC FLOW: permit ip 0.0.0.0/0.0.0.0 0.0.0.0/0.0.0.0
Active SAs: 2, origin: crypto map
7.3.2 Verification on Umbrella Dashboard
- Verify that the SIG tunnel can be seen on the Umbrella dashboard under Deployments >Network Tunnels
7.3.3 Configure SDRA traffic redirection to SIG Interface on vManage
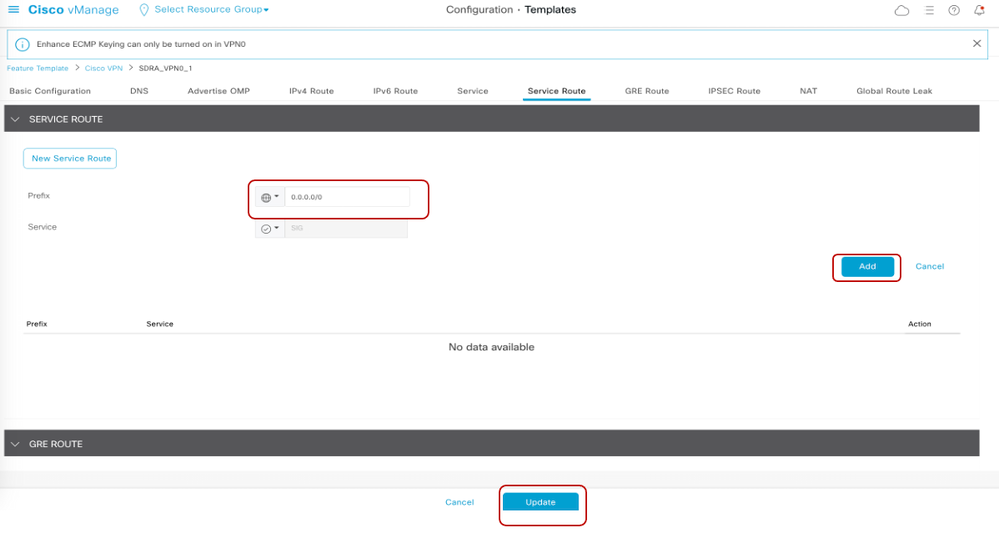
- Edit the Service VPN template on SDRA router to include a Service Route to SIG for 0.0.0.0/0
CLI Reference: Equivalent Umbrella SIG CLI Config Pushed in Above
!
ip sdwan route vrf 1 0.0.0.0/0 service sig
!
7.3.4 Testing Umbrella SIG for SDRA User
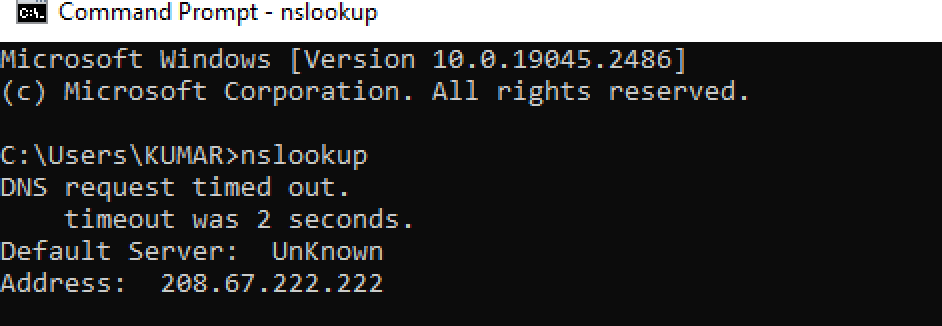
- Verify if the test laptop has extracted the Umbrella DNS from the ISE authorization policy.
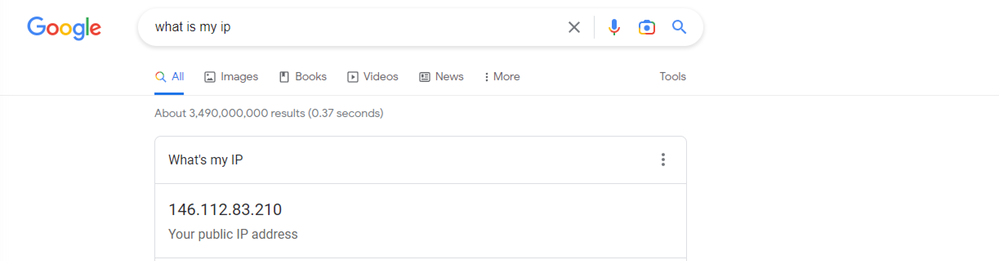
- Verify the public IP address from your laptop/mobile. Open the Google browser and type “What is my IP” in the search bar.
- You should see a 146.112.x.x subnet, which belongs to Umbrella.
- Open the Umbrella dashboard to block the content-based category for securing Internet access from RA users.
a. Navigate to Policies> Policy Components > Content Categories
b. Navigate to Default Web Settings > and click on the drop-down arrow.
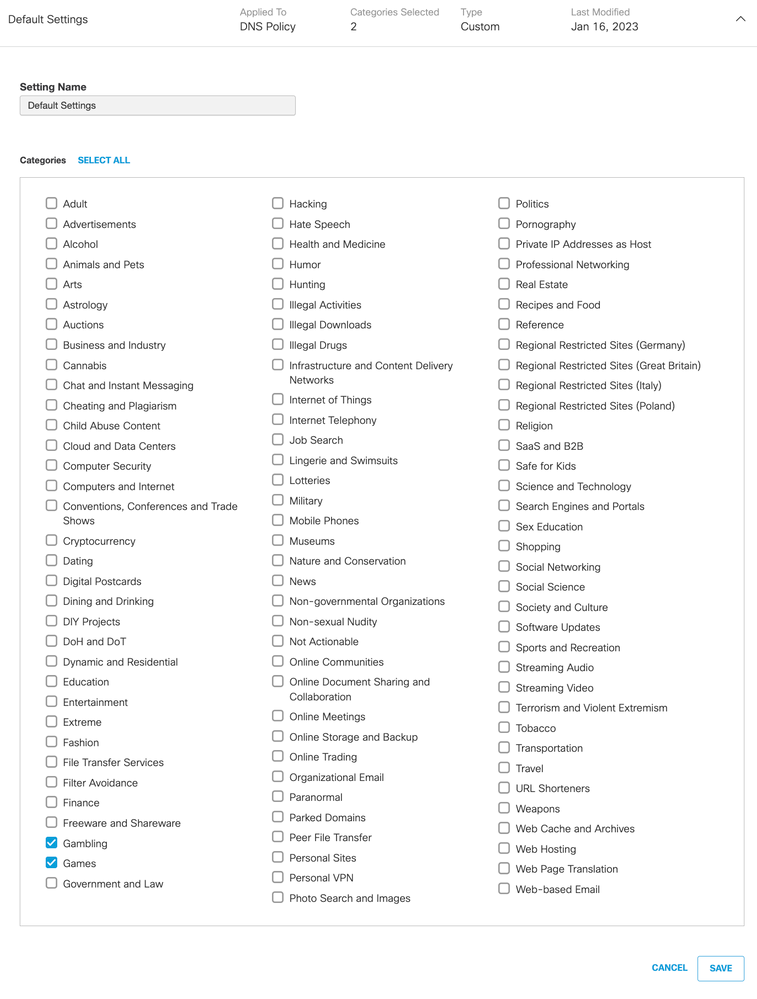
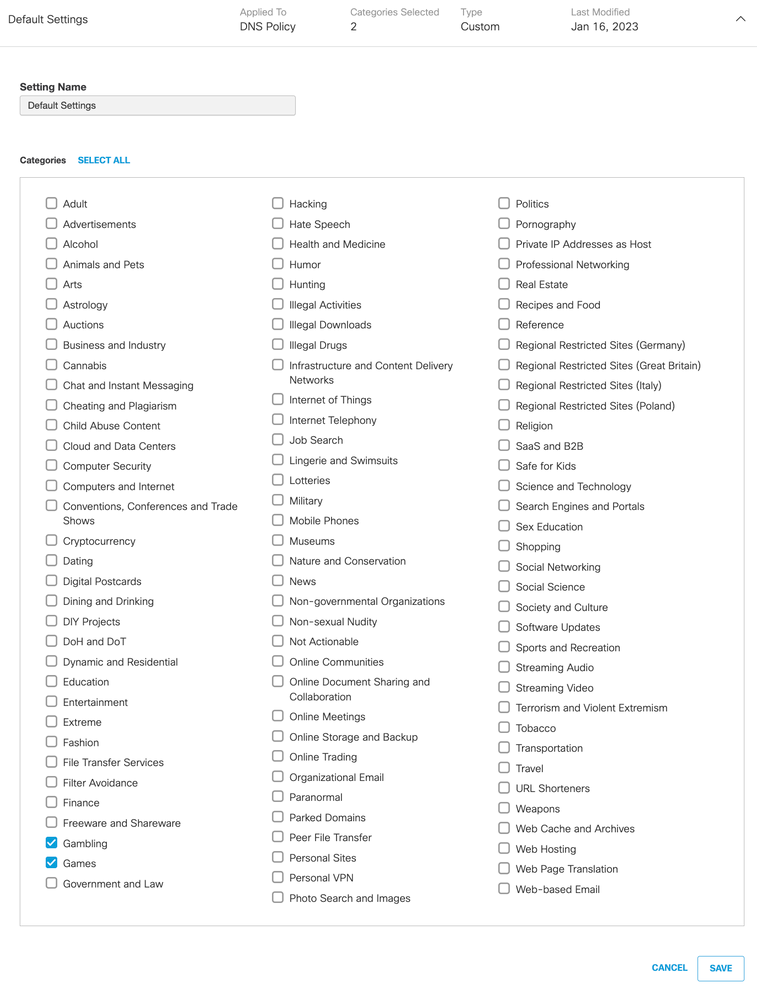
5. Review the DNS policy for Gambling and Games (same content ategories as above).
a. Click Gambling and Games and save the DNS Policy settings.
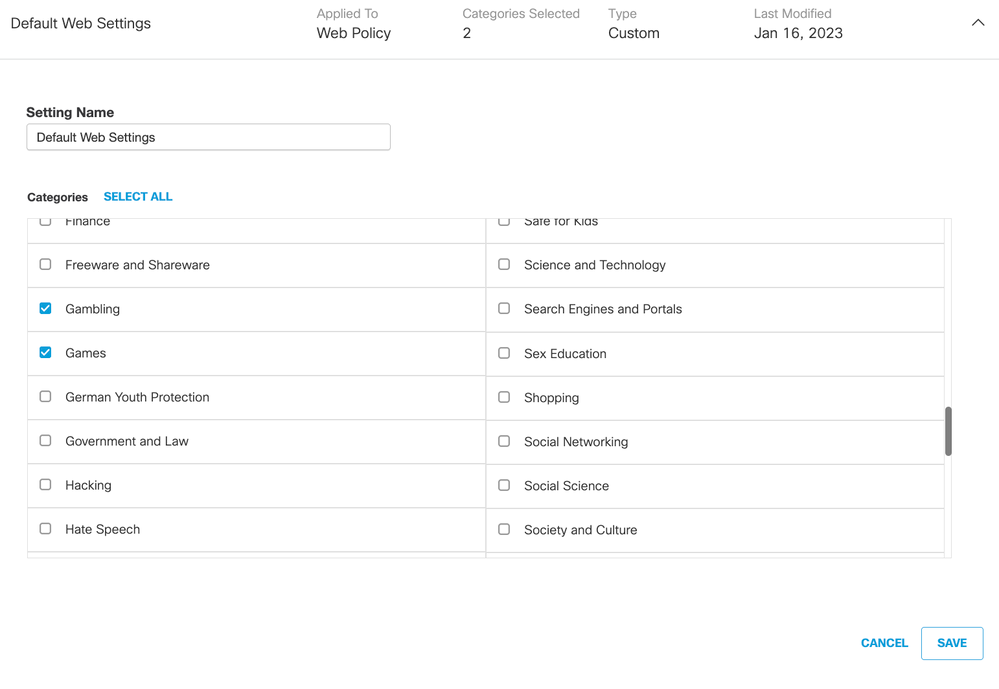
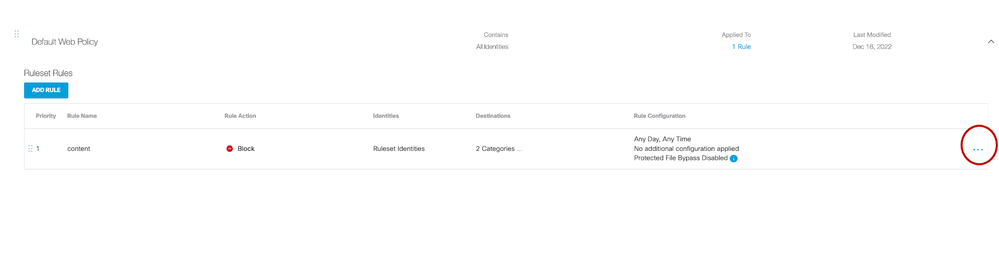
- Review the Web Policy status and block content category.
a. Navigate to Policies > Web Policy
b. Click Default Web Policy and click on the drop-down arrow.
c. Add a new rule to block content categories.
d. Click on three dots and the end of this policy and make sure this rule is enabled.
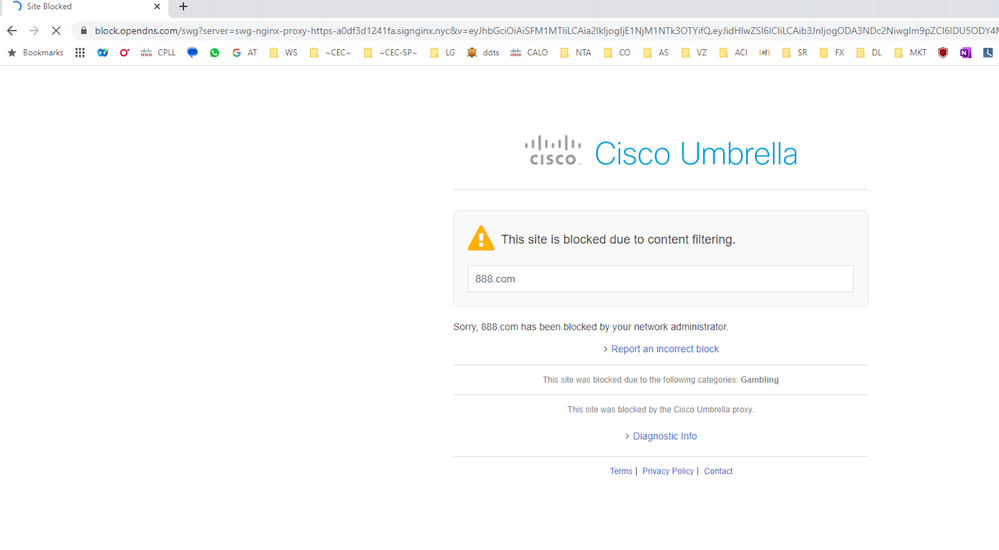
7.3.5 Perform Web Testing from RA Client
- Go to 888.com or any other gaming/gambling site.
- Verify that the below message is seen indicating that the site has been blocked due to content filtering.
8. SDRA Monitoring
As of today (17.7 release), this solution can only be monitored via command line interface from the SDRA headend device.
For future releases (17.11 and on), vManage will have UX2.0 SDRA workflow templates, making the configuration and monitoring experience much simpler and automated.
8.1 SDRA Monitoring from CLI
Following are some of the useful show commands that we can use to verify successful operation/deployment of this solution.
8.1.1 Verifying Successful connection with ISE (Radius server) from SDRA router
CS5_SDRA-8kv#show aaa server
RADIUS: id 4, priority 0, host 10.100.0.6, auth-port 1812, acct-port 1813, hostname RA_RADIUS_SERVER_PrivateServer_10.100.0.6_1812_1813
State: current UP, duration 94006s, previous duration 0s
Dead: total time 0s, count 0
Platform State from SMD: current UP, duration 4294967s, previous duration 0s
SMD Platform Dead: total time 0s, count 0
Platform State from WNCD (1) : current UP
Platform State from WNCD (2) : current UP
Platform State from WNCD (3) : current UP
Platform State from WNCD (4) : current UP
Platform State from WNCD (5) : current UP
Platform State from WNCD (6) : current UP
Platform State from WNCD (7) : current UP
Platform State from WNCD (8) : current UP, duration 0s, previous duration 0s
Platform Dead: total time 0s, count 0UP
Quarantined: No
Authen: request 5, timeouts 0, failover 0, retransmission 0
Response: accept 5, reject 0, challenge 0
Response: unexpected 0, server error 0, incorrect 0, time 30ms
Transaction: success 5, failure 0
Throttled: transaction 0, timeout 0, failure 0
Malformed responses: 0
Bad authenticators: 0
Dot1x transactions:
Response: total responses: 0, avg response time: 0ms
Transaction: timeouts 0, failover 0
Transaction: total 0, success 0, failure 0
MAC auth transactions:
Response: total responses: 0, avg response time: 0ms
Transaction: timeouts 0, failover 0
Transaction: total 0, success 0, failure 0
Author: request 10, timeouts 0, failover 0, retransmission 0
Response: accept 6, reject 4, challenge 0
Response: unexpected 0, server error 0, incorrect 0, time 22ms
Transaction: success 10, failure 0
Throttled: transaction 0, timeout 0, failure 0
Malformed responses: 0
Bad authenticators: 0
MAC author transactions:
Response: total responses: 0, avg response time: 0ms
Transaction: timeouts 0, failover 0
Transaction: total 0, success 0, failure 0
Account: request 2, timeouts 0, failover 0, retransmission 0
Request: start 1, interim 0, stop 1
Response: start 1, interim 0, stop 1
Response: unexpected 0, server error 0, incorrect 0, time 13ms
Transaction: success 2, failure 0
Throttled: transaction 0, timeout 0, failure 0
Malformed responses: 0
Bad authenticators: 0
Elapsed time since counters last cleared: 1d2h6m
Estimated Outstanding Access Transactions: 0
Estimated Outstanding Accounting Transactions: 0
Estimated Throttled Access Transactions: 0
Estimated Throttled Accounting Transactions: 0
Maximum Throttled Transactions: access 0, accounting 0
Consecutive Response Failures: total 0
SMD Platform : max 0, current 0 total 0
WNCD Platform: max 0, current 0 total 0
IOSD Platform : max 0, current 0 total 0
Consecutive Timeouts: total 0
SMD Platform : max 0, current 0 total 0
WNCD Platform: max 0, current 0 total 0
IOSD Platform : max 0, current 0 total 0
Requests per minute past 24 hours:
high - 22 hours, 39 minutes ago: 4
low - 2 hours, 7 minutes ago: 0
average: 0
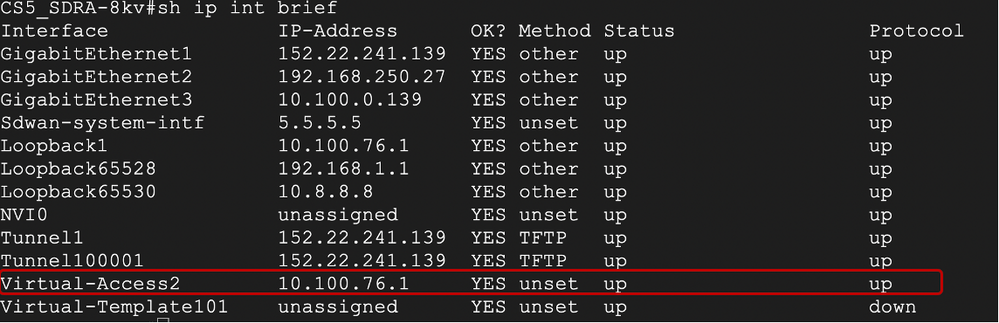
8.1.2 Verify Virtual Template Interface
The virtual template interface is used to create the virtual access interface to start a crypto channel and establish IKEv2 and IPsec security associations (SAs) between the client (AnyConnect user) and server (Edge router).
Note: The virtual-template interface is always up/down. Status is up and Protocol is down.
As soon as a remote user gets connected there is a new Virtual-Access interface created and this will remain up till the time the user stays connected.
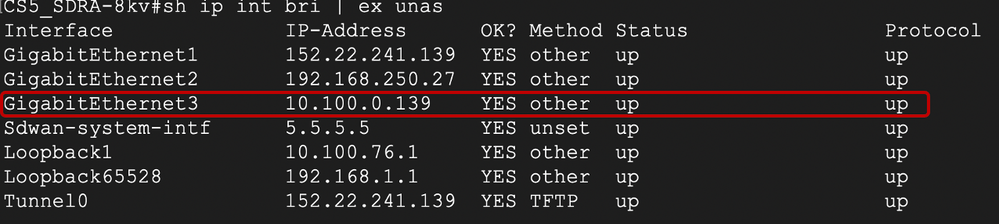
CS5_SDRA-8kv#sh ip int brief
Interface IP-Address OK? Method Status Protocol
GigabitEthernet1 152.22.241.139 YES other up up
GigabitEthernet2 192.168.250.27 YES other up up
GigabitEthernet3 10.100.0.139 YES other up up
Sdwan-system-intf 5.5.5.5 YES unset up up
Loopback1 10.100.76.1 YES other up up
Loopback65528 192.168.1.1 YES other up up
Tunnel0 152.22.241.139 YES TFTP up up
Virtual-Access1 10.100.76.1 YES unset up up
Virtual-Template101 unassigned YES unset up down
8.1.3 Verify Routing Information specific to the VRF
Use the show ip route vrf command to view route information. Specify the VRF assigned to a client. The command output shows information regarding the routes used in the VRF.
Lines containing "Virtual-Access1" indicate that a client is connected.
CS5_SDRA-8kv#sh ip route vrf 1
Routing Table: 1
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is 192.168.250.152 to network 0.0.0.0
m* 0.0.0.0/0 [251/0] via 192.168.250.152, 7w0d, Sdwan-system-intf
[251/0] via 192.168.250.147, 7w0d, Sdwan-system-intf
1.0.0.0/32 is subnetted, 2 subnets
m 1.110.1.1 [251/0] via 192.168.250.147, 7w0d, Sdwan-system-intf
m 1.204.1.2 [251/0] via 192.168.250.168, 7w0d, Sdwan-system-intf
10.0.0.0/8 is variably subnetted, 20 subnets, 6 masks
m 10.0.0.0/8 [251/0] via 192.168.250.152, 7w0d, Sdwan-system-intf
[251/0] via 192.168.250.147, 7w0d, Sdwan-system-intf
S 10.20.55.2/32 is directly connected, Virtual-Access 1
C 10.100.0.0/24 is directly connected, GigabitEthernet3
8.1.4 Verify Configuration on Virtual Access Interface
Check the actual configuration applied for the Virtual-Access interface associated with the client with show derived-config interface virtual-access <number>.
CS5_SDRA-8kv#show derived-config interface virtual-access 1
Building configuration...
Derived configuration : 251 bytes
!
interface Virtual-Access1
vrf forwarding 1
ip unnumbered Loopback1
tunnel source 152.22.241.139
tunnel mode ipsec ipv4
tunnel destination 223.190.80.72
tunnel protection ipsec profile RA_IPSEC_PROFILE
no tunnel protection ipsec initiate
end
8.1.5 Verify IPsec Security Associations
Check the IPsec security associations (SAs) for the AnyConnect client with the show crypto ipsec sa command.
CS5_SDRA-8kv#show crypto ipsec sa
interface: Virtual-Access1
Crypto map tag: Virtual-Access1-head-0, local addr 152.22.241.139
protected vrf: 1
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (10.20.55.2/255.255.255.255/0/0)
current_peer 223.190.80.72 port 21257
PERMIT, flags={origin_is_acl,}
#pkts encaps: 12, #pkts encrypt: 12, #pkts digest: 12
#pkts decaps: 2142, #pkts decrypt: 2142, #pkts verify: 2142
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 152.22.241.139, remote crypto endpt.: 223.190.80.72
plaintext mtu 1438, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet1
current outbound spi: 0xA456424A(2757116490)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xC7C02189(3351257481)
transform: esp-gcm 256 ,
in use settings ={Tunnel UDP-Encaps, }
conn id: 2177, flow_id: CSR:177, sibling_flags FFFFFFFF80000048, crypto map: Virtual-Access1-head-0
sa timing: remaining key lifetime (k/sec): (4607620/2893)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xA456424A(2757116490)
transform: esp-gcm 256 ,
in use settings ={Tunnel UDP-Encaps, }
conn id: 2178, flow_id: CSR:178, sibling_flags FFFFFFFF80000048, crypto map: Virtual-Access1-head-0
sa timing: remaining key lifetime (k/sec): (4607998/2893)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
8.1.6 Verify IKEv2 Session Details
Check IKEv2 SA parameters for the session, the username, and the assigned IP address.Note: The assigned IP address must match the IP address on the AnyConnect client side.
CS5_SDRA-8kv#show crypto ikev2 session detailed
IPv4 Crypto IKEv2 Session
Session-id:3, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote fvrf/ivrf Status
1 152.22.241.139/4500 223.190.80.72/21257 none/1 READY
Encr: AES-CBC, keysize: 256, PRF: SHA256, Hash: SHA256, DH Grp:19, Auth sign: RSA, Auth verify: PSK
Life/Active Time: 86400/2432 sec
CE id: 1024, Session-id: 3
Local spi: 774703B42A444158 Remote spi: 5F03347174B3F8DA
Status Description: Negotiation done
Local id: 152.22.241.139
Remote id: 696277754270797453476D5A4B4242504E77446B74
Remote Reconnect id: rigoel@cisco.com
Local req msg id: 0 Remote req msg id: 82
Local next msg id: 0 Remote next msg id: 82
Local req queued: 0 Remote req queued: 82
Local window: 5 Remote window: 1
DPD configured for 45 seconds, retry 2
Fragmentation not configured.
Dynamic Route Update: disabled
Extended Authentication not configured.
NAT-T is detected outside
Cisco Trust Security SGT is disabled
Assigned host addr: 10.20.55.2 <<<<<<<<<<<<
Initiator of SA : No
Child sa: local selector 0.0.0.0/0 - 255.255.255.255/65535
remote selector 10.20.55.2/0 - 10.20.55.2/65535
ESP spi in/out: 0xC7C02189/0xA456424A
AH spi in/out: 0x0/0x0
CPI in/out: 0x0/0x0
Encr: AES-GCM, keysize: 256, esp_hmac: None
ah_hmac: None, comp: IPCOMP_NONE, mode tunnel
8.1.7 Verify Crypto session information
CS5_SDRA-8kv#show crypto session detail
Interface: Virtual-Access1
Profile: RA_IKEV2_PROFILE
Uptime: 00:01:30
Session status: UP-ACTIVE
Peer: 223.190.80.72 port 12640 fvrf: (none) ivrf: 1
Phase1_id: 696277754270797453476D5A4B4242504E77446B74
Desc: (none)
Session ID: 52
IKEv2 SA: local 152.22.241.139/4500 remote 223.190.80.72/12640 Active
Capabilities:DNR connid:1 lifetime:23:58:30
IPSEC FLOW: permit ip 0.0.0.0/0.0.0.0 host 10.20.55.2
Active SAs: 2, origin: crypto map
Inbound: #pkts dec'ed 805 drop 0 life (KB/Sec) 4607740/3509
Outbound: #pkts enc'ed 2 drop 0 life (KB/Sec) 4607999/3509
8.1.8 Verify IKEv2 SA Parameters
CS5_SDRA-8kv#show crypto ikev2 sa detailed
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 152.22.241.139/4500 122.161.94.46/15293 none/1 READY
Encr: AES-CBC, keysize: 256, PRF: SHA256, Hash: SHA256, DH Grp:19, Auth sign: RSA, Auth verify: AnyConnect-EAP
Life/Active Time: 86400/680 sec
CE id: 1049, Session-id: 11
Local spi: E39C1ABBEE7F8B35 Remote spi: 23EF03F12B6062C9
Status Description: Negotiation done
Local id: 152.22.241.139
Remote id: Windows-PC-SDRA
Remote EAP id: rigoel@cisco.com
Local req msg id: 0 Remote req msg id: 28
Local next msg id: 0 Remote next msg id: 28
Local req queued: 0 Remote req queued: 28
Local window: 5 Remote window: 1
DPD configured for 45 seconds, retry 2
Fragmentation not configured.
Dynamic Route Update: disabled
Extended Authentication not configured.
NAT-T is detected outside
Cisco Trust Security SGT is disabled
Assigned host addr: 10.20.55.9
Initiator of SA : No
IPv6 Crypto IKEv2 SA
8.1.9 Verify RA Pool and Active RA client
Validate the RA pool and In-Use IP address
CS5_SDRA-8kv#sh ip local pool RA_IP_POOL
Pool Begin End Free In use
RA_IP_POOL 10.20.55.1 10.20.55.10 9 1
Available addresses:
10.20.55.10
10.20.55.1 IKEv2 Addr IDB
10.20.55.2 IKEv2 Addr IDB
10.20.55.3 IKEv2 Addr IDB
10.20.55.4 IKEv2 Addr IDB
10.20.55.5 IKEv2 Addr IDB
10.20.55.6 IKEv2 Addr IDB
10.20.55.7 IKEv2 Addr IDB
10.20.55.8 IKEv2 Addr IDB
Inuse addresses:
10.20.55.9 IKEv2 Addr IDB
8.1.10 Verify the CA Certificate and the Edge Router Certificate
CS5_SDRA-8kv#sh crypto pki certificates SRV1-ROOT-CA
Certificate
Status: Available
Certificate Serial Number (hex): 2F00000026D4D97901F9EB9428000000000026
Certificate Usage: General Purpose
Issuer:
cn=cisco-SRV1-CA
dc=cisco
dc=com
Subject:
Name: CS5_SDRA-8kv.cisco.com
cn=CS5_SDRA-8kv.cisco.com
ou=SDWAN-LAB
o=Cisco
st=NC
c=US
hostname=CS5_SDRA-8kv.cisco.com
CRL Distribution Points:
ldap:///CN=cisco-SRV1-CA,CN=SRV1,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=cisco,DC=com?certificateRevocationList?base?objectClass=cRLDistributionPoint
Validity Date:
start date: 18:06:21 UTC Jan 12 2023
end date: 18:06:21 UTC Jan 11 2025
Associated Trustpoints: SRV1-ROOT-CA
Storage: nvram:cisco-SRV1-C#26.cer
CA Certificate
Status: Available
Certificate Serial Number (hex): 52DCD4C9FE93DB8B4923823E3E8FEA90
Certificate Usage: Signature
Issuer:
cn=cisco-SRV1-CA
dc=cisco
dc=com
Subject:
cn=cisco-SRV1-CA
dc=cisco
dc=com
Validity Date:
start date: 18:19:01 UTC Aug 8 2022
end date: 18:29:00 UTC Aug 8 2027
Associated Trustpoints: SRV1-ROOT-CA
Storage: nvram:cisco-SRV1-C#EA90CA.cer
8.2 SDRA Monitoring from vManage
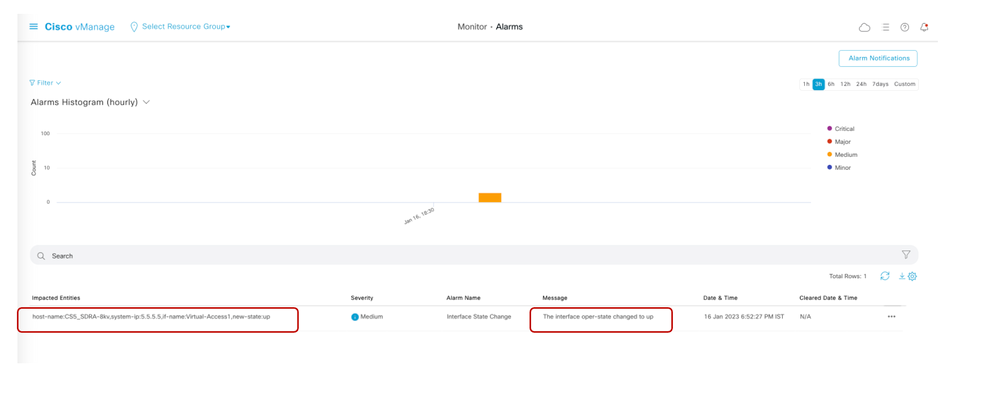
As of today (17.7 release), we have no monitoring capability from vManage. From release 17.11 and onwards, vManage will make the monitoring experience much simpler.
For now, there is limited monitoring capability on vManage. As soon as the remote access user gets connected, we can see vManage alerting via alarms that the Virtual-Access1 interface is up.
9. Appendix A: How to advertise RA pool in OMP as a summary-route
By default, with advertise static under OMP, the /32 routes assigned to remote access clients will get distributed across the network, this is not scalable as we don’t want bunch of /32 routes floating around in the infrastructure, it consumes more memory for the route table and is not scalable for large scale of RA clients.
To circumvent this problem, we can advertise the RA pool network as summary route only from the SDRA headend, this way only summary route will be visible across the entire network as opposed to individual /32 host routes.
Below is the configuration on SDRA Router used to advertise RA pool in OMP as summary route only:
For individual VRFs, routes from the specified prefix can be aggregated after advertising them into OMP using advertise protocol config command. By default, the aggregated prefixes and all individual prefixes are advertised. To advertise only the aggregated prefix, include the aggregate-only option as shown below.
config-transaction
sdwan
omp
address-family ipv4 vrf 1
advertise aggregate <RA Pool/Subnet> aggregate-only
exit
Example:
config-transaction
sdwanomp
address-family ipv4 vrf 1
advertise aggregate 10.20.55.0/28 aggregate-only
9.1 Visibility into Redistributed route from the RA client in the SD-WAN network
As soon as the remote access client comes up it gets assigned an IP address from the RA pool defined by the admin. This can be seen placed in the preferred VRF as a static route.
With OMP advertising static routes, these RA clients can be seen propagating the network as OMP route. With the above settings of summarizing them they can be seen summary OMP route along the path.
DC2_cEdge1#sh ip route vrf 1 | in 10.20
m 10.20.55.0/28 [251/0] via 5.5.5.5, 00:00:05, Sdwan-system-intf
DC2_cEdge2#sh ip route vrf 1 | in 10.20
m 10.20.55.0/28 [251/0] via 5.5.5.5, 00:00:11, Sdwan-system-intf
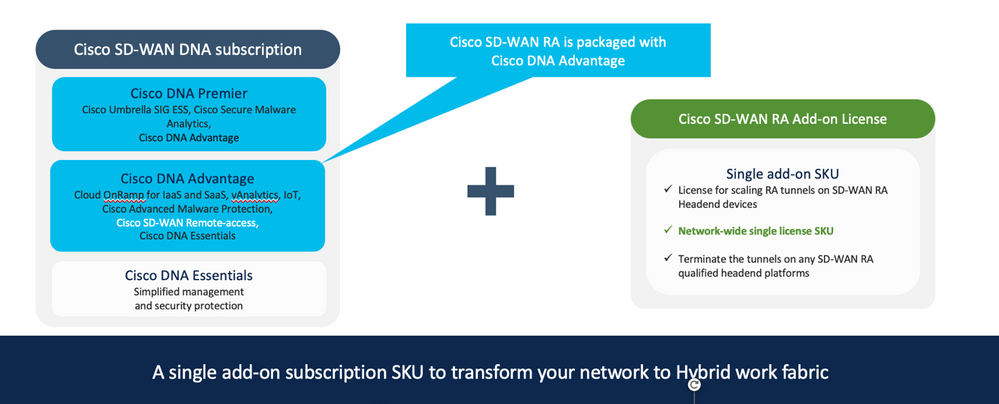
10. Appendix B: SD-WAN Remote Access Package/ Licensing
The SDRA feature is natively packaged within the DNA Advantage Tier.
For customers looking to migrate to the SDRA solution, please ensure that the DNA Advantage Tier has been purchased and placed in their correct admin Smart Account/ Virtual account. Once this is done, the license can be assigned to the RA headend from vManage using the License Management tab.
10.1 Cisco SD-WAN RA Add-On Pricing and Ordering
There is a single add-on subscription SKU for scaling RA tunnels on SD-WAN RA headend devices.
SDWAN-RA-SESS is a sub item under SKU L-SDWAN-RA-SUB.
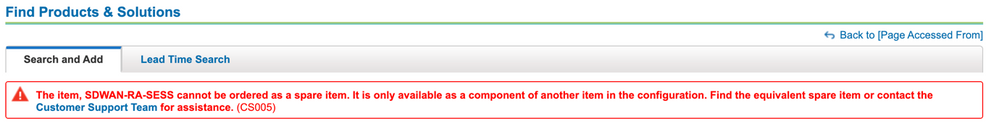
SDWAN-RA-SESS is not a standalone license in itself that can be purchased/added. An attempt to add just the SDWAN-RA-SESS item will result in following error :
10.2 Simplified steps of ordering
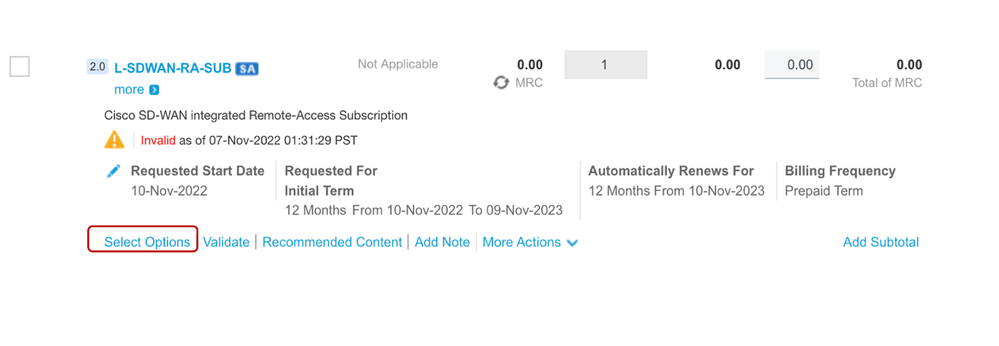
- Add L-SDWAN-RA-SUB to your CCW estimate.
- Once the estimate has been created, click on Select Options as seen below
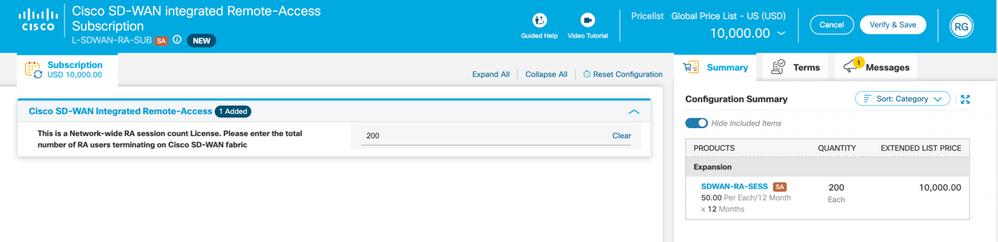
- Input the total number of RA users on the SD-WAN fabric, as seen below:
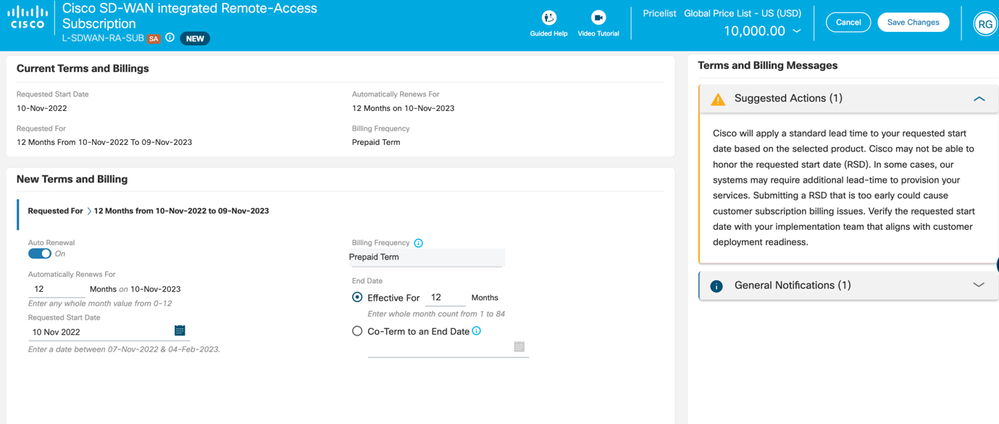
- Configure the term as seen below:
This completes the ordering process.
Important Note: Cisco AnyConnect Mobility Client end-point licenses are NOT included and they need to be ordered separately.
Please go through: https://www.cisco.com/c/en/us/products/collateral/security/anyconnect-og.html
11. Appendix C: SD-WAN Remote Access Configuration
clock calendar-valid
!
!
ip local pool RA_IP_POOL 10.20.55.1 10.20.55.10
ip http client source-interface GigabitEthernet3
!
aaa group server radius RA_RADIUS_SERVER
server-private 10.100.0.6 key 6 OLLgTTceWcQCR_eV_]AB^cHCV[MQhIVPXAAB
ip radius source-interface GigabitEthernet3
ip vrf forwarding 1
!
aaa authentication enable default enable
aaa authentication login default local
aaa authentication login RA_AUTHEN_MLIST group RA_RADIUS_SERVER
aaa authorization console
aaa authorization exec default local
aaa authorization network RA_AUTHOR_MLIST group RA_RADIUS_SERVER
aaa accounting network RA_ACC_MLIST start-stop group RA_RADIUS_SERVER
aaa server radius dynamic-author
!
crypto pki trustpoint SRV1-ROOT-CA
auto-enroll regenerate
enrollment url http://192.168.250.20:80/certsrv/mscep/mscep.dll
fqdn CS5_SDRA-8kv.cisco.com
fingerprint C24D4BD6135E37BF79225B323A67DBAA
revocation-check none
subject-name CN=CS5_SDRA-8kv.cisco.com,OU=SDWAN-LAB,O=Cisco,ST=NC,C=US
!
!
crypto ikev2 name-mangler ikev2-ra-mangler
eap suffix delimiter @
!
crypto ikev2 proposal RA_IKEV2_PROPOSAL
encryption aes-cbc-256
group 19
integrity sha256
!
crypto ikev2 policy RA_IKEV2_POLICY
proposal RA_IKEV2_PROPOSAL
!
!
exit
interface Virtual-Template101 type tunnel
no shutdown
vrf forwarding 1
tunnel mode ipsec ipv4
exit
!
interface Loopback1
no shutdown
arp timeout 1200
vrf forwarding 1
ip address 10.100.76.1 255.255.255.255
ip mtu 1500
exit
!
!
crypto ikev2 profile RA_IKEV2_PROFILE
aaa accounting anyconnect-eap RA_ACC_MLIST
aaa authentication anyconnect-eap RA_AUTHEN_MLIST
aaa authorization group anyconnect-eap list RA_AUTHOR_MLIST name-mangler ikev2-ra-mangler password 6 ]]_AcWMZiCf_gUEVaNLdDY`cCHNXYVEFaaRh
authentication local rsa-sig
authentication remote anyconnect-eap aggregate
match identity remote any
pki trustpoint SRV1-ROOT-CA
reconnect timeout 1800
virtual-template 101
!
!
crypto ipsec transform-set RA_IPSEC_TS esp-gcm 256
mode tunnel
!
crypto ipsec profile RA_IPSEC_PROFILE
set ikev2-profile RA_IKEV2_PROFILE
set transform-set RA_IPSEC_TS
!
!
interface Virtual-Template101 type tunnel
tunnel protection ipsec profile RA_IPSEC_PROFILE
12. Appendix D – SIG Credentials/Feature Template Configuration
- Login to vManage using your login credentials
- Navigate to the menu Configuration > Templates
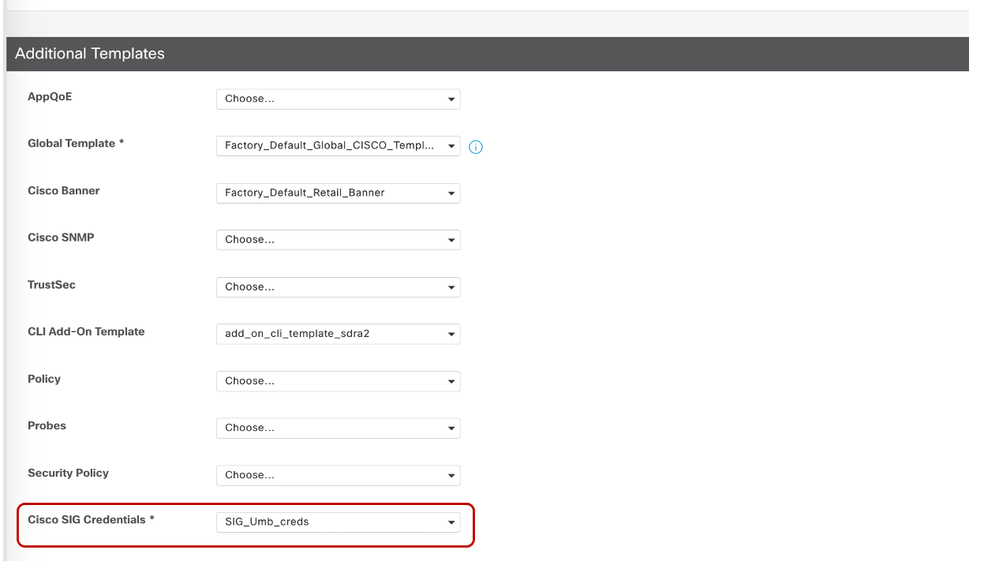
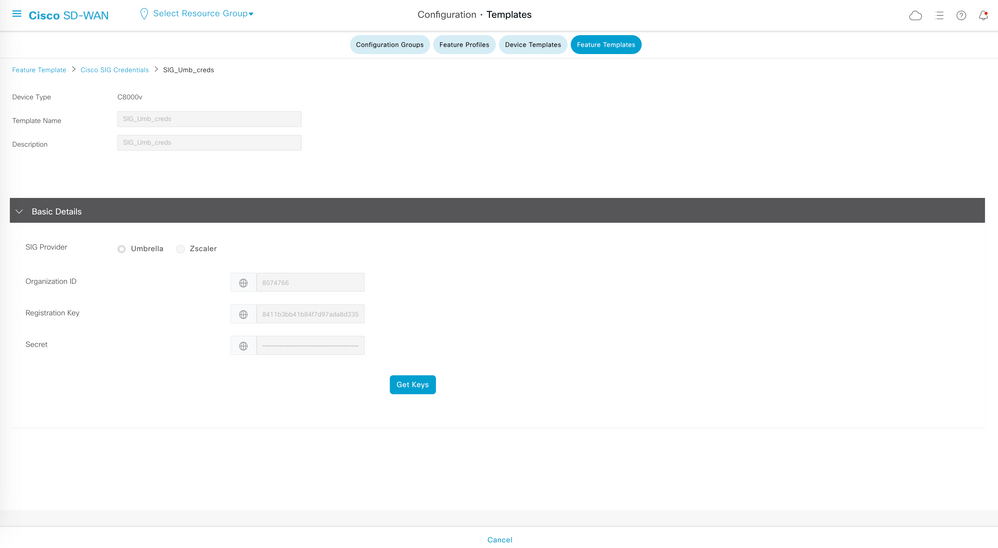
- Click Feature Templates and select existing Cisco SIG Credentials Template named SIG_Umb_creds.
- Navigate to the three dots on the right and select View.
- Below is the snapshot for this template.
Admin can obtain the Organization ID and Registration key from Umbrella dashboard.
12.1 Where to find Organization ID and Registration key from Umbrella Dashboard
This can be found under Admin > API Keys ( Select Legacy Keys on the right) followed by Umbrella Management.
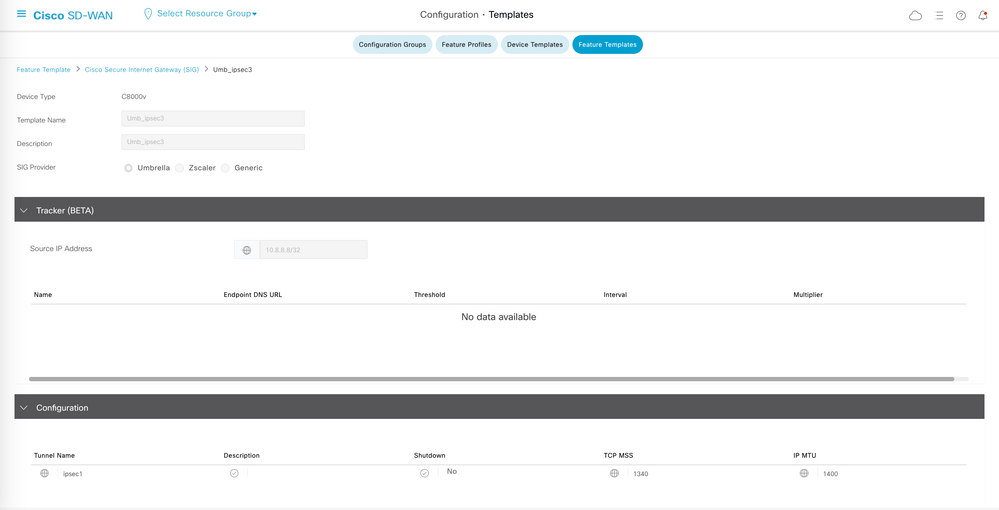
- Navigate back to Feature Templates and select Cisco SIG - Secure Internet Gateway Template named Umb_ipsec3.
- Navigate to the three dots on the right and select View.
- Below is the snapshot for this template.
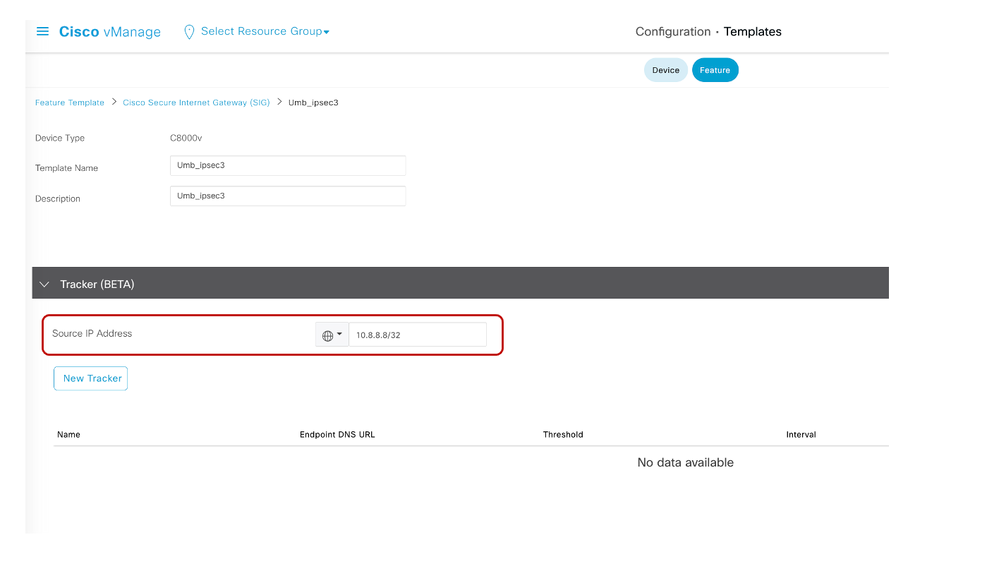
- Ensure to add a tracker source IP address for SIG Template starting 17.7. This could be any dummy IP not being used in your network. This can be any unused non overlapping private IP in your network.
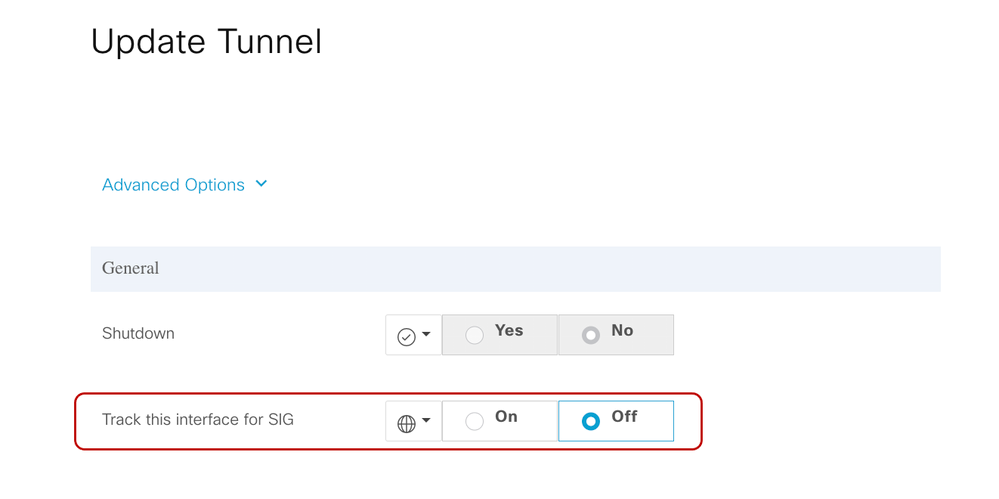
- Disable tunnel tracking under Tunnel Advanced settings.
CLI Reference: Equivalent Umbrella SIG CLI Config Pushed in Above Step.
!
secure-internet-gateway
umbrella org-id 8074766
umbrella api-key 8411b3bb41b84f7d97ada8d335b7ea81
umbrella api-secret "$8$03vuBZxcd6wf+KuqqRJyK8fgKL7oep5qTtpl8kuBIh8pDPn/6vQqMo+HBhGyFxPheWYAs0XX\no5pZLj5B1BTkHg=="
!
interface Tunnel100001
tunnel-options tunnel-set secure-internet-gateway-umbrella tunnel-dc-preference primary-dc source-interface GigabitEthernet1
no track-enable
!
!
crypto ipsec profile if-ipsec1-ipsec-profile
set ikev2-profile if-ipsec1-ikev2-profile
set transform-set if-ipsec1-ikev2-transform
set security-association lifetime kilobytes disable
set security-association lifetime seconds 3600
set security-association replay window-size 512
!
interface Tunnel100001
no shutdown
ip unnumbered GigabitEthernet1
no ip clear-dont-fragment
ip tcp adjust-mss 1340
ip mtu 1400
tunnel source GigabitEthernet1
tunnel destination dynamic
tunnel mode ipsec ipv4
tunnel protection ipsec profile if-ipsec1-ipsec-profile
tunnel vrf multiplexing
!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Once the Anyconnect client connects for the first time and has cached what has been sent to it, could it not then have a list available to connect to either the traditional ASA for the legacy needs until all items have been moved to the RA method? Or you would build this with the profile xml builder? I haven't built out the VPN profiles since the old school type, prior to the Anyconnect type client, my apologies.
Thanks,
Coop
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
For now, the SD-WAN Headend router details has to be fed manually to the Anyconnect using the profile editor, the sentiment here is to have customers who are already using SD-WAN use the remote access capability features. For ones which are not yet onboarded, yes they can continue to use their existing list and connect to ASA while adding the RA headend manually using editor, we are working with Client team to make this a better experience moving forward.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I have completed. But I cant CE . @rigoel
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: