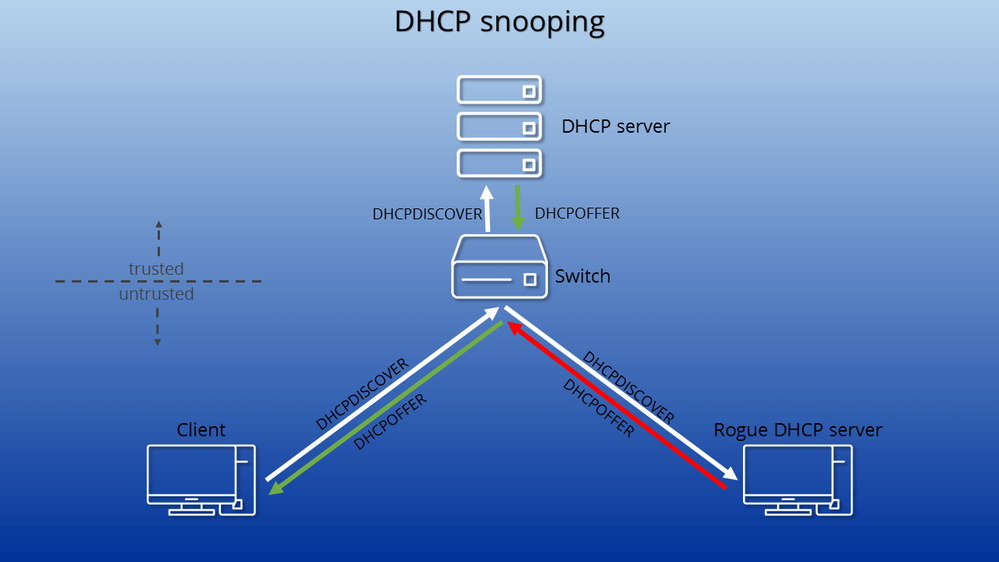
what is DHCP Snooping ? as its name is very cleared what is that, its an mechanism to control your network DHCP Servers, in the DHCP Snooping we define DHCP Server connected to which port or VLAN and then after enable DHCP Snooping, if Switch receive any DHCP DISCOVERY massage, just forward that to Trusted ports, and its very basic operation for block some attacks like man-in-the-middle, cause in the networks without DHCP Snooping everyone can respond to DHCP Client massage and get IP to them with custom information like different Gateway.
maybe ask yourself how it work !? its very simple, each frame came from un-trust port for DHCPDISCOVERY, switch forward it to only Trusted port and then when ACK Massage was send to client, switch register some information to DHCP-Snooping Database, this Info include: Client MAC Address, Lease Time, Switch Port,IP Address and VLAN.
This table was stored in Flash by default but as you know flash capacity is limited and maybe you have a big Network with a lot of workstations, you need another place for store this Database(this database is a flat file with simple format), if your Database was out of your switches, then if switch was fail, you have copies of your DHCP Snooping Data and can very easily recover them to new switches or as you know when switch was reloaded, all of here DHCP Snooping Database data be cleared, but if you have an external database, you can keep this data to unlimited next reboot.This Database can accessed by CISCO Switches via remote protocols like TFTP.
IP Source Guard and Dynamic ARP Inspection uses this Database entry to perform own filtering or any operation must to do.
All entry will be remain in this Database file ? NO ! when they removed ? in two situation items in DHCP Snooping was removed Automatically via switches, 1: When lease time was ended and if workstation at this time send another request to DHCP, DHCP Server get it maybe new IP Address, then switch store new information of that host.
2: when client or workstation send RELEASE frame to DHCP Server.
and you must remember this tips, DHCP Snooping doesn't store Host Information about Every Host on Trusted ports. and when you want to view Hosts Information from DHCP Snooping Database, you cant see any data entry from ports that are Trusted already.
By default DHCP Snooping is disabled and you can enable it via this commands:
1.config t
2. ip dhcp snooping
After Enabling DHCP Snooping Globally, then now is time to configure DHCP Snooping on one or more VLAN,via this command:
ip dhcp snooping vlan [vlan-list]
DHCP snooping MAC address verification:
This feature by default is enabled and if any packet revived from untrust ports have different MAC Address to client MAC Address for when it get IP Address from DHCP Server, then all of there packet be dropped.
How to register a port as a Trust:
conf t
inter [x/y]
ip dhcp snoop trust
Verify DHCP
get overall information about your DHCP Snooping configuration and ports status
show ip dhcp snooping
Show DHCP Snooping Binding Database entries:
show ip dhcp snooping binding
resources:
https://www.cisco.com/c/en/us/td/docs/switches/datacenter/sw/4_1/nx-os/security/configuration/guide/sec_nx-os-cfg/sec_dhcpsnoop.html
https://www.certprepare.com/dhcp-snooping
http://www.pearsonitcertification.com/articles/article.aspx?p=2474170
https://grumpy-networkers-journal.readthedocs.io/en/latest/VENDOR/CISCO/SWITCHING/DHCPSNOOPING.html
