- Cisco Community
- Technology and Support
- Collaboration
- Other Collaboration Subjects
- Re: CUBE TLS problem third party SBC
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2021 02:54 AM
We are trying to setup a SIP trunk between a CUBE and a third party SBC using TLS and self signed certs.
I am following this guide:
There really is not much to the config from the CUBE side. When running the debugs mentioned in the above I get a couple of errors:
TLS 1.2 Alert [length 0002], fatal handshake_failure
SSL routines:ssl3_get_client_hello:no shared cipher
As a test I setup TLS on another spare CUBE and created a trunk between the two and that works fine so the issue has to be the way the third party SBC and the CUBE are trying to setup TLS.
Solved! Go to Solution.
- Labels:
-
Other Collaboration Topics
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2021 05:47 AM
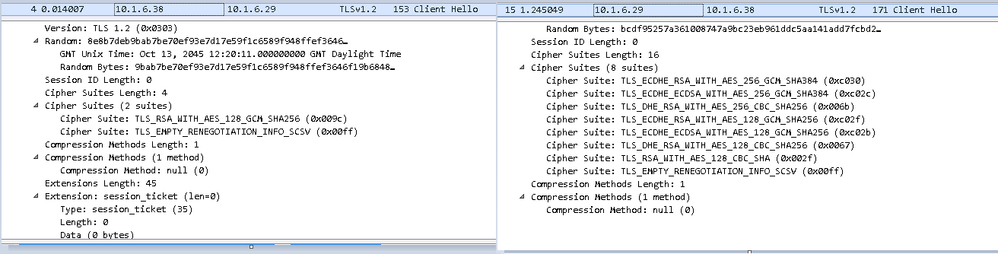
Looks like the "no shared cipher" is exactly the issues:
The hello from the third party to the CUBE on the left vs the right CUBE to the third party.
They done have a cipher that matches.
Is there anyway to change to config on the CUBE to it offers a specific cipher? TLS_RSA_WITH_AES_128_GCM_SHA256 obviously.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2021 05:47 AM
Looks like the "no shared cipher" is exactly the issues:
The hello from the third party to the CUBE on the left vs the right CUBE to the third party.
They done have a cipher that matches.
Is there anyway to change to config on the CUBE to it offers a specific cipher? TLS_RSA_WITH_AES_128_GCM_SHA256 obviously.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2021 12:01 PM
Hi,
Does this link help? See the options for the crypto signaling default command under the sip-ua:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2021 12:27 PM
I was about to send the same one..
Prior to release Cisco IOS15.6(1)T, CUBE supported TLS v1.0 with the following cipher suites:
SSL_RSA_WITH_RC4_128_MD5
TLS_RSA_WITH_AES_128_CBC_SHA
CUBE supports only the mandatory cipher suites for TLS implementation. From Cisco IOS15.6(1)T release onwards, CUBE supports TLS v1.2 which is backward compatible. Following are the cipher suites added:
TLS_DHE_RSA_WITH_AES_128_CBC_SHA1
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
Following cipher suites are added in the Cisco IOS XE Amsterdam 17.3.1a release:
TLS_RSA_WITH_AES_256_CBC_SHA
TLS_DHE_RSA_WITH_AES_128_CBC_SHA
TLS_DHE_RSA_WITH_AES_256_CBC_SHA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2021 12:30 PM
Can you ask the other side to add additional ciphers in why are they set on just that one?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2021 04:11 AM
We did reach out to the third party and they have patched their software to offer additional ciphers.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide