- Cisco Community
- Technology and Support
- Networking
- Other Network Architecture Subjects
- ASA5505 ICMP flowing only in one direction
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA5505 ICMP flowing only in one direction
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2020 10:40 PM - edited 06-17-2020 11:07 PM
Hi All
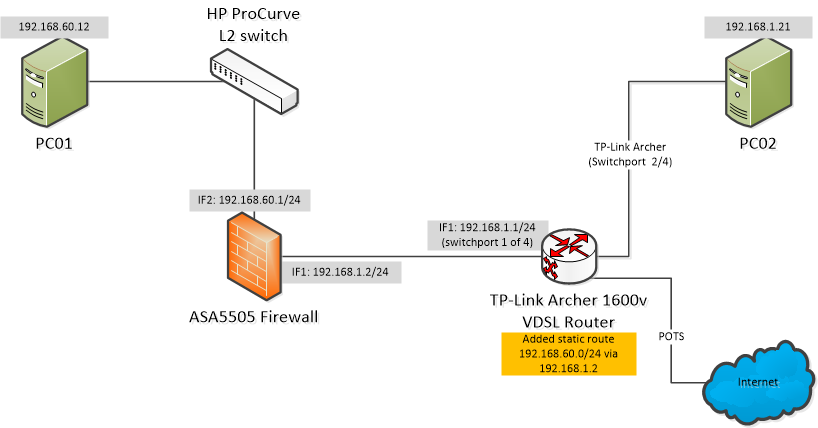
Got a minor problem (possibly) with my ASA5505 configuration:
Check below diagram to get a basic overview of the topology.
I can ping / reach PC1 from PC2.
I can ping / reach PC2 from IF1 (192.168.1.2 / 24) of the ASA5505
Problem in brief:
I cannot ping / reach PC2 from IF2 (192.168.60.1 / 24) of the ASA5505
or from PC1 (192.168.60.12). I need to be able to.
Here is a somewhat pruned version of my ASA config, there is a still a few unnecessary entries, but my ISP connectivity just changed and I am still to clean up entries of the former PPPoE config.
Any feedback appreciated
ASA Version 9.1(3)
!
hostname asa5505
xlate per-session deny tcp any4 any4
xlate per-session deny tcp any4 any6
xlate per-session deny tcp any6 any4
xlate per-session deny tcp any6 any6
xlate per-session deny udp any4 any4 eq domain
xlate per-session deny udp any4 any6 eq domain
xlate per-session deny udp any6 any4 eq domain
xlate per-session deny udp any6 any6 eq domain
multicast-routing
names
!
interface Ethernet0/0
switchport access vlan 10
!
interface Ethernet0/1
!
interface Ethernet0/2
switchport access vlan 20
!
interface Ethernet0/3
switchport access vlan 30
!
interface Ethernet0/4
switchport access vlan 40
!
interface Ethernet0/5
switchport access vlan 40
!
interface Ethernet0/6
switchport access vlan 80
!
interface Ethernet0/7
switchport access vlan 70
!
interface Vlan1
nameif outside_wan
security-level 0
ip address 192.168.1.2 255.255.255.0
!
interface Vlan10
nameif outside_public
security-level 0
pppoe client vpdn group ADSL2
no ip address
!
interface Vlan20
nameif inside_dmz
security-level 100
ip address 192.168.60.1 255.255.255.0
!
interface Vlan30
nameif inside_guest
security-level 70
ip address 192.168.70.1 255.255.255.0
!
interface Vlan40
nameif inside_experimental
security-level 50
ip address 10.255.255.1 255.255.255.0
!
interface Vlan70
nameif inside_phone
security-level 10
ip address 192.168.80.1 255.255.255.192
!
interface Vlan80
nameif inside_exp_mgmt
security-level 50
ip address 99.0.0.1 255.255.255.0
!
boot system disk0:/asa913-k8.bin
ftp mode passive
clock timezone EST 10
clock summer-time EDT recurring last Sun Oct 2:00 last Sun Mar 3:00
dns domain-lookup inside_dmz
dns server-group DefaultDNS
name-server 192.168.60.2
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network LAN_private
subnet 192.168.50.0 255.255.255.0
object network LAN_dmz
subnet 192.168.60.0 255.255.255.0
object network LAN_guest
subnet 192.168.70.0 255.255.255.01
object network LAN_experimental
subnet 10.0.0.0 255.255.0.0
object network QNAP_host
host 192.168.60.11
object network INTELNUC_host
host 192.168.60.2
object network INTELNUC_prtgservice
host 192.168.60.2
object network INTELNUC_webservice
host 192.168.60.2
object network QNAP_management
host 192.168.60.11
object network QNAP_t49091
host 192.168.60.11
object network LAN_guest_wireless
range 192.168.70.31 192.168.70.50
object network QNAP_t51413
host 192.168.60.11
object network QNAP_u51413
host 192.168.60.11
object network LAN_phone
subnet 192.168.80.0 255.255.255.192
object service 16384-32766
service udp destination range 16384 32766
object service 27000-27100
service udp destination range 27000 27100
object network ASUSZ170_t27036
host 192.168.60.12
object network QNAP_ftp
host 192.168.60.11
object network INTELNUC_plexservice
host 192.168.60.2
object network INTELNUC_rdp
host 192.168.60.2
object network Google_dns01
host 8.8.8.8
object network Google_dns02
host 8.8.4.4
object network ASUSZ170_host
host 192.168.60.12
object network PS4_host
host 192.168.70.14
object service 3478-3480
service tcp destination range 3478 3480
object network ASUSZ170_t27037
host 192.168.60.12
object network ASUSZ170_u27031
host 192.168.60.12
object service 3389
service tcp destination eq 3389
object network LAN_guest_trusted
range 192.168.70.1 192.168.70.29
object network ASUSZ170_u27036
host 192.168.60.12
object service prtg
service tcp destination eq 8081
object-group network LAN_all
network-object object LAN_dmz
network-object object LAN_experimental
network-object object LAN_guest
network-object object LAN_private
network-object object LAN_phone
object-group protocol TCPUDP
protocol-object udp
protocol-object tcp
object-group service DM_INLINE_SERVICE_3
service-object object 27000-27100
service-object tcp destination eq 27036
service-object tcp destination eq 27037
service-object tcp destination eq 3389
service-object udp destination eq 27031
service-object udp destination eq 27036
object-group service 53 tcp-udp
port-object eq domain
object-group service DM_INLINE_SERVICE_1
service-object tcp destination eq 49091
service-object tcp destination eq 51413
service-object tcp destination eq 8080
service-object tcp destination eq ftp
service-object udp destination eq 51413
object-group network Google_dnsall
network-object object Google_dns01
network-object object Google_dns02
object-group service DM_INLINE_TCP_1 tcp
port-object eq 32400
port-object eq 3389
port-object eq 8081
port-object eq www
access-list public_ACL extended permit object-group DM_INLINE_SERVICE_1 any object QNAP_host
access-list public_ACL extended permit tcp any object INTELNUC_host object-group DM_INLINE_TCP_1
access-list public_ACL extended permit object-group DM_INLINE_SERVICE_3 any object ASUSZ170_host
access-list dmz_ACL extended permit ip any any
access-list guest_ACL extended permit icmp any any echo
access-list guest_ACL extended permit udp any any eq snmp
access-list guest_ACL extended permit object 3389 object LAN_guest_trusted object ASUSZ170_host
access-list guest_ACL extended permit ip object LAN_guest_trusted object INTELNUC_host
access-list guest_ACL extended deny object prtg object LAN_guest_trusted object ASUSZ170_host
access-list guest_ACL extended permit object-group TCPUDP object LAN_guest_wireless object INTELNUC_host eq domain
access-list guest_ACL extended deny ip object LAN_guest_wireless object INTELNUC_host
access-list guest_ACL extended deny ip object LAN_guest_wireless object QNAP_host
access-list guest_ACL extended deny ip any interface inside_exp_mgmt
access-list guest_ACL extended deny ip any interface inside_experimental
access-list guest_ACL extended deny ip any interface inside_phone
access-list guest_ACL extended deny ip any interface outside_wan
access-list guest_ACL extended permit ip any any
access-list CONNS extended permit object-group TCPUDP any any eq sip
access-list public_wan_ACL extended permit ip any any
access-list netflow-export extended permit ip any any
pager lines 24
flow-export destination inside_dmz 192.168.60.2 2055
flow-export template timeout-rate 1
flow-export delay flow-create 30
mtu outside_wan 1500
mtu outside_public 1492
mtu inside_dmz 1500
mtu inside_guest 1500
mtu inside_experimental 1500
mtu inside_phone 1500
mtu inside_exp_mgmt 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
icmp permit any outside_wan
asdm image disk0:/asdm-714.bin
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
access-group public_wan_ACL in interface outside_wan
access-group public_ACL in interface outside_public
access-group dmz_ACL in interface inside_dmz
access-group guest_ACL in interface inside_guest
!
router eigrp 10
no auto-summary
network 10.0.0.0 255.0.0.0
network 192.168.1.0 255.255.255.0
network 192.168.50.0 255.255.255.0
network 192.168.60.0 255.255.255.0
network 192.168.70.0 255.255.255.0
network 192.168.80.0 255.255.255.0
passive-interface outside_public
redistribute static
!
route outside_wan 0.0.0.0 0.0.0.0 192.168.1.1 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
aaa authentication telnet console LOCAL
aaa authentication ssh console LOCAL
http server enable
http server session-timeout 1440
http 192.168.50.0 255.255.255.0 outside_wan
http 192.168.60.0 255.255.255.0 inside_dmz
snmp-server host inside_dmz 192.168.60.2 community *****
snmp-server location inside_dmz
no snmp-server contact
snmp-server community *****
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpoint localtrust
enrollment self
fqdn asa5505.somename.org
subject-name CN=sasa5505.somename.org
keypair sslvpnkey
crl configure
crypto ca trustpool policy
crypto ca certificate chain localtrust
telnet 192.168.50.0 255.255.255.0 outside_wan
telnet 192.168.60.0 255.255.255.0 inside_dmz
telnet timeout 60
ssh 192.168.50.0 255.255.255.0 outside_wan
ssh 192.168.60.0 255.255.255.0 inside_dmz
ssh timeout 60
ssh version 2
ssh key-exchange group dh-group1-sha1
console timeout 0
vpdn group ADSL2 request dialout pppoe
vpdn group ADSL2 localname somename
vpdn group ADSL2 ppp authentication pap
vpdn username somename password ***
dhcpd auto_config outside_public
!
dhcprelay server 192.168.60.2 inside_dmz
dhcprelay enable inside_guest
dhcprelay enable inside_experimental
dhcprelay enable inside_phone
dhcprelay timeout 60
threat-detection rate scanning-threat rate-interval 600 average-rate 10 burst-rate 15
threat-detection rate scanning-threat rate-interval 3600 average-rate 8 burst-rate 12
threat-detection basic-threat
threat-detection statistics protocol
threat-detection statistics access-list
threat-detection statistics tcp-intercept rate-interval 30 burst-rate 400 average-rate 200
ntp server 49.176.193.230
ntp server 129.250.35.250
ssl encryption aes256-sha1 aes128-sha1 3des-sha1 rc4-sha1
ssl trust-point localtrust outside_public
webvpn
anyconnect-essentials
username someusername password ***
!
class-map netflow-export-class
match access-list netflow-export
class-map CONNS
match access-list CONNS
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect ip-options
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect xdmcp
inspect icmp
inspect pptp
class netflow-export-class
flow-export event-type all destination 192.168.60.2
policy-map CONNS
class CONNS
set connection timeout idle 2:00:00
!
service-policy global_policy global
service-policy CONNS interface inside_phone
prompt hostname context
no call-home reporting anonymous
: end
asa5505(config-if)#
- Labels:
-
Other Network
-
Other Networking
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2020 05:07 PM
Hi,
I'll take a crack at thinking about your problem. I've not setup things this way, but I have a 5505 and regularly troubleshoot it, have sys engineering background, etc.
What about connection initiation check-routines such as telnet <192.168.1.21> <port #- common 1 like "80" for example> or ssh <192.168.21> run from pc1 on the 192.168.60 what looks like "dmz" network? Will that connect and open a session or at least change your screen indicating the port connects, thus affirming or disqualifying some kind of connectivity? If ssh or telnet won't work, it's likely completely ruled and firewalled off between the 2 networks- no ports whatsoever reachable on the 192.168.1 from anything on 192.168.60, indicating not firewall acl entries or incorrectly configured ones.
Should the dmz 192.168.60 network have a different and lower priority than the 192.168.1 network, almost acting closer to an outside(world) vlan vs the inside vlan? That seems to make sense, being a dmz, but you could have it so that it is so constricted or misconfigured that it is actually no different whatsoever than the outside cruel world- in other words nothing opened at all by default, or those things that are intentionally opened are misconfigured.
Without going through your "mumbo-jumbo" of rules, you might want to bring things up pictorially in your ASDM gui and look at the configuration for the firewall acl rules. You probably have to add services like tcp/udp/icmp to the 192.168.1 to individual hosts or the whole subnet of the 192.168.60 network.
Last thing I can think of is there is a hardening chapter in the ASA Configuration and Administration guide that talks about among other things how make configuration tweaks to reject icmp echo replies from the "outside" vlan.
You could lastly temporarily set the VLAN priority of DOT-60 to the same as DOT-1, and make sure there is a route between the 2. See if by default i allows ping icmp replies.
Hope it's helpful.
BK
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide