- Cisco Community
- Technology and Support
- Networking
- Other Network Architecture Subjects
- Forcing no split-tunnel in remote site IPSec/GRE VPN connection
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Forcing no split-tunnel in remote site IPSec/GRE VPN connection
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2017 07:51 PM - edited 03-03-2019 08:27 AM
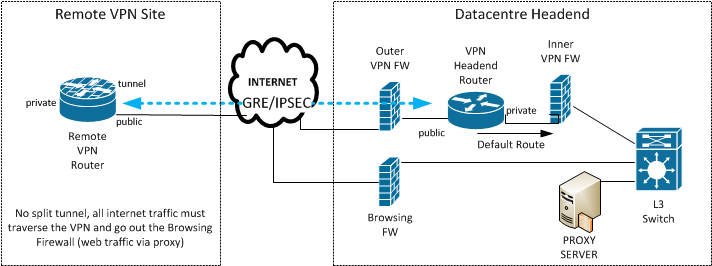
We have a number of remote sites connecting to headends via IPSec encrypted GRE tunnels over the public internet.
Our current configuration works, but we would like to see if there is a better way of handling the no-split tunnel rule.
At the headend site, we have static routes on the VPN Headend router for each of the remote VPN site routers, via the public interface next hop (Outer VPN FW). The default route on the VPN headend router is via the private interface next hop (Inner VPN FW).
At the remote site, we have a static route to the VPN headend router public interface via the remote VPN router public interface next hop (ISP gateway). The default route on the remote VPN router is via the GRE tunnel interface next hop.
This works ok, but requires static IP addressing on the Remote VPN router (which is not always possible). We'd also like to move towards dynamic routing to allow for automatic failover between headends.
I know on the ASA anyconnect product there is the option of having two default routes (with interface specified) and the "tunneled" command to direct tunneled traffic out that default route, but I'm not aware of anything in IOS to achieve that.
Appreciate any suggestions you have!
- Labels:
-
Other Networking
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2017 08:12 AM
Hi Andrew,
A good option is the DMVPN solution, along with BGP inside the tunnels in order to have dynamic routing with failover.
Cheers.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide