- Cisco Community
- Technology and Support
- Networking
- Other Network Architecture Subjects
- Re: Head office network design ideas
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Head office network design ideas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2013 02:47 PM - edited 03-03-2019 07:04 AM
Hej,
I am in planning of LAN re-design for Head office which consists of different networks - user LAN, WAN, DMZ, Internet, Special connection, sever LAN
Present traffic generation across the networks, ofcourse in near by future these values except to go up more 10-20%.
LAN - upto 300 Mbps
WAN - upto 35 Mbps
Internet - upto 55 Mbps
Special connection - 100Mbps
Server LAN - 200 Mbps
DMZ - upto 20 Mbps
Present Core and access layers are existing which is not so optimal.
Based on future vision of business and existing topology we decided to design network something like this
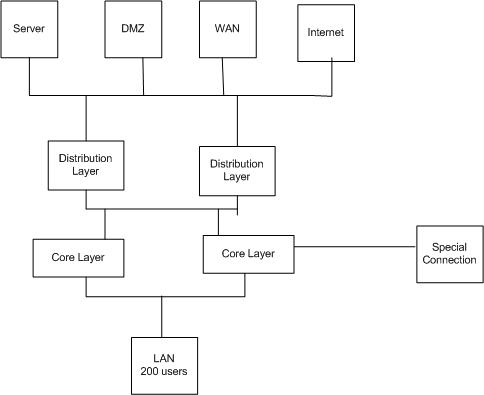
Server, DMZ, WAN, Internet are redundant boxes
Firewall is connect in distribution layer with active standby setup
In core layer - WLC's, proxy, cisco ISE, WCS are planned to connect.
Also in core layer - VLAN routing for client, wireless LAN and related VLANs
Distribution layer - WAN/Server/Internet/DMZ (maybe) inter-VLAN routing
Special connection is also get terminated on core layer as redundancy
In view of this please share your thoughts to build hardware at distribution and core layers, design guides.
- Labels:
-
Other Networking
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2013 04:00 AM
You'd normally hang the access-layer switches off the distribution-layer.
If you're looking at new ASA firewalls, then Cisco has just recently added CX capability to the rest of the 5500-X series. This is effectively application-layer firewalling across all ports, not just web traffic. This brings them more in line with the competition, such as Palo Alto.
Note that you need new 5500-X series hardware which comes with in-built SSD. Also, at the moment you can't combine CX with the integrated IPS, although this might come in time. The alternative is a pair of dedicated inline IPS sensors. At least with dedicated sensors you can move them around your campus and their lifecycle isn't tied to the firewall platform. Quite pricey though, compared to the intergrated license-enabled IPS in the 5500-X series.
Are you looking at the new 3850 series for the access-layer?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2013 04:38 AM
Thanks Shillings,
CX capabilities is good to know, at present in network 5520 are present and also we are not looking for firewall upgrade in this migration.
Distribution layer is quite new which is not in existance in network now, based on present traffic what would be the best hardware platforms to consider to build distribution layer.?
yes, access switches are hanged at core layer (naming of these layers are not correct) but according to diagram core layer is where access switches are hanged along with user require appliances like WLCs, WCS, Proxy, Cisco ACS, Cisco ISE.
Present access switches are in stack model, in future there is also plan to migrate them to gigabit ports with 10g uplinks but again this is in next phase.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-10-2013 04:48 AM
Ref 5520s, you can still use Cisco's Cloud Web Security (CWS) to increase security beyond that of basic stateful inspection. Their SIO can filter all your web traffic (both HTTP and HTTPS) using anti-malware and anti-virus engines. And you can create your own URL filtering policy that you apply to your workforce's Interent usage. It's quite granular, so directors can still watch YouTube This is managed via your own Internet dashboard. CWS can also be applied to your remote workforce too. A split tunnel will force all remote client web traffic via the CWS (Scansafe) cloud and all VPN traffic will go straight to your HQ. You'll need to upgrade the 5520s to version 9.x.
http://www.cisco.com/en/US/solutions/collateral/ns1194/aag_c45-716565.pdf
I'm reluctant to spec switches in this situation. There are so many questions and unknowns. Your budget is likely to be the greatest limiting factor. Also, have you done any capacity planning? My advise is to get as much information as possible - i.e. historic throughput graphs, top-talkers etc
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-10-2013 07:44 AM
Hi Shillings,
Present max peak bandwidth usage based on the bandiwdth usage graphs, we would like to plan 2x fold more bandwidth capacity so that this environment survies itself upto 5 years
LAN - upto 300 Mbps
WAN - upto 35 Mbps
Internet - upto 55 Mbps
Special connection - 100Mbps
Server LAN - 200 Mbps
DMZ - upto 20 Mbps
~800 Mbps of peak usage is observed i.e peaks of different networks. Peak usage is not common across networks.
Yes, budget plays role here mention but put all best models, I will filter based on the budget.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2013 02:58 AM
s-santhosh wrote:
put all best models, I will filter based on the budget.
In that case, a couple of VSS-enabled 6500s with quad-Sup2T's
Personally, I'd want to find a very good Cisco partner and build a trusted relationship with them. This can add a lot of value to your business and help make a strategic plan for the future. I'd still want to price check their proposed kit list against one or two competitors, but with minimal effort required on their part. Your chosen partner will still need some idea of budget though.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-25-2013 03:21 PM
Good points, Simon.
Rated.
Sent from Cisco Technical Support Nintendo App
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: