- Cisco Community
- Technology and Support
- Security
- Other Security Subjects
- EIGRP flaps after CoPP is applied
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2023 03:02 AM
R1#show ip access-lists 130
Extended IP access list 130
10 permit eigrp any host 224.0.0.10 (349 matches)
20 permit eigrp host 224.0.0.10 any
30 permit eigrp any any (280 matches)
40 permit ip host 172.16.1.1 any
50 permit ip host 192.168.1.1 any
60 permit ip 10.1.0.0 0.0.255.255 any (10 matches)
70 permit ip any any
===
class-map match-all CoPP-CRITICAL
match access-group 130
class-map match-all CoPP-NORMAL
match access-group 122
class-map match-all CoPP-IMPORTANT
match access-group 121
!
policy-map CoPP
class CoPP-CRITICAL
police 1000000 50000 50000 conform-action transmit exceed-action transmit
class CoPP-IMPORTANT
police 1000000 20000 20000 conform-action transmit exceed-action drop
class CoPP-NORMAL
police 64000 6400 64000 conform-action transmit exceed-action drop
class class-default
police 8000 1500 1500 conform-action drop exceed-action drop
!
control-plane
service-policy input CoPP
After I applied the service policy CoPP EIGRP flaps every min:
R1#
*Mar 10 10:52:05.100: %DUAL-5-NBRCHANGE: EIGRP-IPv4 10: Neighbor 10.1.13.2 (Ethernet1/1) is down: retry limit exceeded
R1#
*Mar 10 10:52:08.063: %DUAL-5-NBRCHANGE: EIGRP-IPv4 10: Neighbor 10.1.13.2 (Ethernet1/1) is up: new adjacency
R1#
*Mar 10 10:52:13.235: %DUAL-5-NBRCHANGE: EIGRP-IPv4 10: Neighbor 10.1.12.2 (Ethernet1/0) is down: retry limit exceeded
R1#
*Mar 10 10:52:18.030: %DUAL-5-NBRCHANGE: EIGRP-IPv4 10: Neighbor 10.1.12.2 (Ethernet1/0) is up: new adjacency
R1#
*Mar 10 10:53:27.663: %DUAL-5-NBRCHANGE: EIGRP-IPv4 10: Neighbor 10.1.13.2 (Ethernet1/1) is down: retry limit exceeded
R1#
====
R2#debug ip eigrp neighbor
R2#
*Mar 10 10:42:34.214: EIGRP: Retransmission retry limit exceeded
*Mar 10 10:42:34.222: EIGRP: Holdtime expired
*Mar 10 10:42:34.222: %DUAL-5-NBRCHANGE: EIGRP-IPv4 10: Neighbor 10.1.12.1 (Ethernet1/0) is down: retry limit exceeded
R2#
*Mar 10 10:42:34.222: Going down: Peer 10.1.12.1 total=0 stub 0, iidb-stub=0 iid-all=0
*Mar 10 10:42:34.222: EIGRP: Handle deallocation failure [0]
*Mar 10 10:42:34.224: EIGRP: Neighbor 10.1.12.1 went down on Ethernet1/0
R2#
*Mar 10 10:42:37.968: EIGRP: New peer 10.1.12.1
R2#
*Mar 10 10:42:37.968: %DUAL-5-NBRCHANGE: EIGRP-IPv4 10: Neighbor 10.1.12.1 (Ethernet1/0) is up: new adjacency
*Mar 10 10:42:38.197: EIGRP: Retransmission retry limit exceeded
*Mar 10 10:42:38.202: EIGRP: Holdtime expired
Am I missing anything on ACL 130?
Solved! Go to Solution.
- Labels:
-
Access List
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2023 02:16 PM
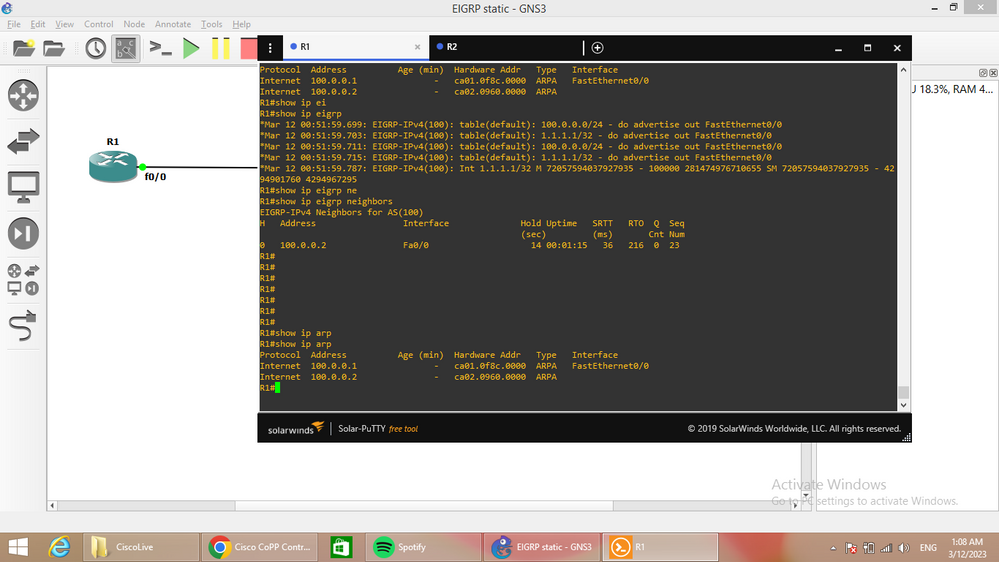
the EIGRP use multicast and unicast,
multicast not need arp
unicast need arp
and since the class-default is drop which cause the ARP request/reply drop
and the EIGRP can not know the mac address of neighbor and hence it unicast is drop, this make EIGRP flapping.
I solve it without change CoPP by add static ARP to config, but this not solution because sure there are many other protocol use class-default and action drop can cause reachability issue in your network.
thanks
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2023 03:35 AM
how about try :
permit eigrp any any
Can you post :
#show policy-map control-plane input
what is the content of 121 and 122 ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2023 04:45 AM
permit eigrp any any
this is already seq 30 in the ACL 130
R1#show policy-map control-plane input
Control Plane
Service-policy input: CoPP
Class-map: CoPP-CRITICAL (match-all)
6633 packets, 463120 bytes
5 minute offered rate 0000 bps, drop rate 0000 bps
Match: access-group 130
police:
cir 10000000 bps, bc 50000 bytes
conformed 6633 packets, 463120 bytes; actions:
transmit
exceeded 0 packets, 0 bytes; actions:
transmit
conformed 0000 bps, exceeded 0000 bps
Class-map: CoPP-IMPORTANT (match-all)
0 packets, 0 bytes
5 minute offered rate 0000 bps, drop rate 0000 bps
Match: access-group 121
police:
cir 1000000 bps, bc 20000 bytes, be 20000 bytes
conformed 0 packets, 0 bytes; actions:
transmit
exceeded 0 packets, 0 bytes; actions:
drop
violated 0 packets, 0 bytes; actions:
drop
conformed 0000 bps, exceeded 0000 bps, violated 0000 bps
Class-map: CoPP-NORMAL (match-all)
0 packets, 0 bytes
5 minute offered rate 0000 bps, drop rate 0000 bps
Match: access-group 122
police:
cir 64000 bps, bc 6400 bytes, be 64000 bytes
conformed 0 packets, 0 bytes; actions:
transmit
exceeded 0 packets, 0 bytes; actions:
drop
violated 0 packets, 0 bytes; actions:
drop
conformed 0000 bps, exceeded 0000 bps, violated 0000 bps
Class-map: class-default (match-any)
29836 packets, 2275316 bytes
5 minute offered rate 2000 bps, drop rate 2000 bps
Match: any
police:
cir 8000 bps, bc 1500 bytes, be 1500 bytes
conformed 29836 packets, 2275316 bytes; actions:
drop
exceeded 0 packets, 0 bytes; actions:
drop
violated 0 packets, 0 bytes; actions:
drop
conformed 2000 bps, exceeded 0000 bps, violated 0000 bps
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2023 03:40 AM
there is two traffic here
multicast and unicast
the hello is send multicast
but the update send unicast
I see ACL you use only for multicast ?? can I know why ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2023 04:53 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2023 05:41 AM
To give more context :
R1#show ip eigrp neighbors detail
EIGRP-IPv4 VR(CISCO) Address-Family Neighbors for AS(10)
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 10.1.12.2 Et1/0 14 00:00:55 1 5000 1 131
Version 10.0/2.0, Retrans: 12, Retries: 12, Waiting for Init Ack
Topology-ids from peer - 0
UPDATE seq 260 ser 0-0 Sent 55042 Init Sequenced
R2#show ip eigrp neighbors detail
EIGRP-IPv4 VR(CISCO) Address-Family Neighbors for AS(10)
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 10.1.12.1 Et1/0 14 00:00:05 1 4500 1 0
Version 10.0/2.0, Retrans: 2, Retries: 2, Waiting for Init, Waiting for Init Ack
Topology-ids from peer - 0
UPDATE seq 133 ser 0-0 Sent 5419 Init Sequenced
Topology-ids from peer - 0
UPDATE seq 261 ser 0-0 Sent 26504 Init Sequenced
0 10.1.12.2 Et1/0 14 00:00:55 1 5000 1 131
Version 10.0/2.0, Retrans: 12, Retries: 12, Waiting for Init Ack
Topology-ids from peer - 0
UPDATE seq 260 ser 0-0 Sent 55042 Init Sequenced
Both ends are waiting for the Init Ack, which is blocked somewhere but i cannot find out where. I also added a deny any any at the end of the ACL but i see no hits.
Extended IP access list 121
10 permit tcp 10.1.0.0 0.0.255.255 any eq 22
20 permit icmp 10.1.0.0 0.0.255.255 any
30 permit icmp host 172.16.1.1 any
40 permit icmp host 192.168.1.1 any
50 permit icmp any any
60 permit icmp any any host-unreachable
70 permit icmp any any ttl-exceeded
Extended IP access list 122
10 permit udp 10.1.0.0 0.0.255.255 any range 33434 33464
20 permit udp 10.1.0.0 0.0.255.255 any
30 permit udp any any
Extended IP access list 130
10 permit eigrp any host 224.0.0.10 (5000 matches)
20 permit eigrp host 224.0.0.10 any
30 permit eigrp any any (4436 matches)
40 permit ip host 172.16.1.1 any
50 permit ip host 192.168.1.1 any
60 permit ip 10.1.0.0 0.0.255.255 any (136 matches)
70 permit ip any any (27 matches)
80 deny ip any any
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2023 02:16 AM
R2#show ip eigrp neighbors detail
EIGRP-IPv4 VR(CISCO) Address-Family Neighbors for AS(10)
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 10.1.12.1 Et1/0 14 00:00:05 1 4500 1 0
Version 10.0/2.0, Retrans: 2, Retries: 2, Waiting for Init, Waiting for Init AckThis means after you apply the CoPP - somehow each other lost connection. are you able to ping each other?
Your class default messing up here - ( will do close look up your config later weekend)
For now, change as below and test it (and let us know the outcome ?)
class class-default
police 8000 1500 1500 conform-action transmit exceed-action drop
Other note : (have a look below Policy, is the BOLD one typo or intention ?)
class CoPP-NORMAL
police 64000 6400 64000 conform-action transmit exceed-action drop
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2023 07:19 AM
It is exactly like this:
- when CoPP is applied the connection is lost
- from R1 (the router with the CoPP) ping to 224.0.0.10 is successful :
R1#ping 224.0.0.10
Type escape sequence to abort.
Sending 1, 100-byte ICMP Echos to 224.0.0.10, timeout is 2 seconds:
Reply to request 0 from 10.1.13.2, 1 ms
Reply to request 0 from 10.1.12.2, 1 ms
- From R2,R3 (the eigrp neighbors) the ping to 224.0.0.10 is not successful
- I cannot get successful ping results when i ping the connected interface , while route is in the routing table:
R1#ping 10.1.12.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.12.2, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
R1#
R1#
R1#show ip rouy
R1#show ip rout
R1#show ip route | i 10.1.12.
C 10.1.12.0/30 is directly connected, Ethernet1/0
L 10.1.12.1/32 is directly connected, Ethernet1/0
- the only CoPP class maps that they have hits are the CRITICAL and the default one. So definitely packets are dropped in the default one because they cannot get matched to the previous classes (?).
- CRITICAL class does not have hits for "exceeded" packets... so that makes me think that all hits do not excheed cir threshold:
R1#show policy-map control-plane input
Control Plane
Service-policy input: CoPP
Class-map: CoPP-CRITICAL (match-all)
673 packets, 46937 bytes
5 minute offered rate 0000 bps, drop rate 0000 bps
Match: access-group 130
police:
cir 1000000 bps, bc 50000 bytes, be 50000 bytes
conformed 673 packets, 46937 bytes; actions:
transmit
exceeded 0 packets, 0 bytes; actions: <<< zero packets exceeded cir
transmit
violated 0 packets, 0 bytes; actions:
transmit
conformed 0000 bps, exceeded 0000 bps, violated 0000 bps
Class-map: CoPP-IMPORTANT (match-all)
0 packets, 0 bytes
5 minute offered rate 0000 bps, drop rate 0000 bps
Match: access-group 121
police:
cir 100000 bps, bc 20000 bytes, be 20000 bytes
conformed 0 packets, 0 bytes; actions: <<< zero packets matched
transmit
exceeded 0 packets, 0 bytes; actions:
drop
violated 0 packets, 0 bytes; actions:
drop
conformed 0000 bps, exceeded 0000 bps, violated 0000 bps
Class-map: CoPP-NORMAL (match-all)
0 packets, 0 bytes
5 minute offered rate 0000 bps, drop rate 0000 bps
Match: access-group 122
police:
cir 64000 bps, bc 6400 bytes, be 64000 bytes
conformed 0 packets, 0 bytes; actions: <<< zero packets matched
transmit
exceeded 0 packets, 0 bytes; actions:
drop
violated 0 packets, 0 bytes; actions:
drop
conformed 0000 bps, exceeded 0000 bps, violated 0000 bps
Class-map: class-default (match-any)
3258 packets, 249302 bytes
5 minute offered rate 2000 bps, drop rate 2000 bps
Match: any
police:
cir 8000 bps, bc 1500 bytes, be 1500 bytes
conformed 3258 packets, 249302 bytes; actions: <<< the drops are here,question is why?which packets don't match CRITICAL?
drop
exceeded 0 packets, 0 bytes; actions:
drop
violated 0 packets, 0 bytes; actions:
drop
conformed 2000 bps, exceeded 0000 bps, violated 0000 bps
- If i change
conform-action drop > conform-action transmit
under class default the flaps disappears, but the idea is that the default class drops all the packets that they don't much the previous classes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2023 09:54 AM
under class default the flaps disappears, but the idea is that the default class drops all the packets that they don't much the previous classes.Not read all your outcomes, so you confirm that when you add the below line - the EIGRP working as expected - is this correct?
class class-default
police 8000 1500 1500 conform-action transmit exceed-action drop
Note: as I mentioned we totally understand what you trying to achieve - as I indicated to you, somehow traffic going to the default class - let me think on why it was the case.
@ponzki - Looking at your comment - ACL always does top to bottom order, if that matches then it is allowed right ? (I do not see any difference I guess here)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2023 10:02 AM
@balaji.bandi yes absolutely no difference on matching the rules from the original ACL entries. What I intend to try was to make an effect on the deny any any rule @katerina86 wanted to attempt on his access-list 130. After that, we can drill down to next troubleshooting steps instead of matching to default class, which has drop actions. Hope it makes sense.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2023 09:33 AM
@katerina86 Could you try to limit your access-list to just the following below without permit ip any any at the bottom and put eigrp any any on top?
ip access-list extended 130
permit eigrp any any
permit ip 10.1.0.0 0.0.0.255 any
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2023 10:12 AM
@ponzki i tried it without any positive results.
Extended IP access list 121
10 permit tcp 10.1.0.0 0.0.255.255 any eq 22
Extended IP access list 122
10 permit udp 10.1.0.0 0.0.255.255 any range 33434 33464
Extended IP access list 130
10 permit eigrp any any (1086 matches)
20 permit ip 10.1.0.0 0.0.255.255 any (5 matches)
R1#show policy-map control-plane input
Control Plane
Service-policy input: CoPP
Class-map: CoPP-CRITICAL (match-all)
1145 packets, 79473 bytes
5 minute offered rate 0000 bps, drop rate 0000 bps
Match: access-group 130
police:
cir 1000000 bps, bc 50000 bytes, be 50000 bytes
conformed 1145 packets, 79473 bytes; actions:
transmit
exceeded 0 packets, 0 bytes; actions:
transmit
violated 0 packets, 0 bytes; actions:
transmit
conformed 0000 bps, exceeded 0000 bps, violated 0000 bps
Class-map: CoPP-IMPORTANT (match-all)
0 packets, 0 bytes
5 minute offered rate 0000 bps, drop rate 0000 bps
Match: access-group 121
police:
cir 100000 bps, bc 20000 bytes, be 20000 bytes
conformed 0 packets, 0 bytes; actions:
transmit
exceeded 0 packets, 0 bytes; actions:
drop
violated 0 packets, 0 bytes; actions:
drop
conformed 0000 bps, exceeded 0000 bps, violated 0000 bps
Class-map: CoPP-NORMAL (match-all)
0 packets, 0 bytes
5 minute offered rate 0000 bps, drop rate 0000 bps
Match: access-group 122
police:
cir 64000 bps, bc 64000 bytes, be 64000 bytes
conformed 0 packets, 0 bytes; actions:
transmit
exceeded 0 packets, 0 bytes; actions:
drop
violated 0 packets, 0 bytes; actions:
drop
conformed 0000 bps, exceeded 0000 bps, violated 0000 bps
Class-map: class-default (match-any)
5457 packets, 415995 bytes
5 minute offered rate 2000 bps, drop rate 2000 bps
Match: any
police:
cir 8000 bps, bc 1500 bytes, be 1500 bytes
conformed 5457 packets, 415995 bytes; actions:
drop
exceeded 0 packets, 0 bytes; actions:
drop
violated 0 packets, 0 bytes; actions:
drop
conformed 2000 bps, exceeded 0000 bps, violated 0000 bps
@balaji.bandi indeed , when i change the police for the default class and from drop is set to transmit the flaps stop.
Any ideas on what else to check?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2023 09:48 AM - edited 03-11-2023 10:14 AM
Cisco CoPP Control Plane Policing Configuration - Study CCNP (study-ccnp.com)
Match-all is the issue here,
you need to divide the ACL to match only one line
for example
access-list extended eigrp
permit eigrp any any
access-list extended icmp
permit icmp any any
then under same
class eigrp
match access-group name eigrp
class icmp
match access-group name icmp
policy-map mhm
class eigrp
policer ....
class icmp
policer ....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2023 10:02 AM
@MHM Cisco World the "match-any" and "match-all" keywords should be relevant only for the class-maps. All my class-maps have a match with only one ACL, so in this case "match-all" and "match-any" should give the same result.
class-map match-all CoPP-CRITICAL
match access-group 130
class-map match-all CoPP-NORMAL
match access-group 122
class-map match-all CoPP-IMPORTANT
match access-group 121
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2023 10:14 AM
this my opinion, try divide acl 130 as I mention above and check result
Note:- instead of three line
permit eigrp host 224.0.0.10 any
permit eigrp any host 224.0.0.10
permit eigrp any any
Use only
permit eigrp any any
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide