- Cisco Community
- Technology and Support
- Security
- Other Security Subjects
- Re: EIGRP flaps after CoPP is applied
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2023 03:02 AM
R1#show ip access-lists 130
Extended IP access list 130
10 permit eigrp any host 224.0.0.10 (349 matches)
20 permit eigrp host 224.0.0.10 any
30 permit eigrp any any (280 matches)
40 permit ip host 172.16.1.1 any
50 permit ip host 192.168.1.1 any
60 permit ip 10.1.0.0 0.0.255.255 any (10 matches)
70 permit ip any any
===
class-map match-all CoPP-CRITICAL
match access-group 130
class-map match-all CoPP-NORMAL
match access-group 122
class-map match-all CoPP-IMPORTANT
match access-group 121
!
policy-map CoPP
class CoPP-CRITICAL
police 1000000 50000 50000 conform-action transmit exceed-action transmit
class CoPP-IMPORTANT
police 1000000 20000 20000 conform-action transmit exceed-action drop
class CoPP-NORMAL
police 64000 6400 64000 conform-action transmit exceed-action drop
class class-default
police 8000 1500 1500 conform-action drop exceed-action drop
!
control-plane
service-policy input CoPP
After I applied the service policy CoPP EIGRP flaps every min:
R1#
*Mar 10 10:52:05.100: %DUAL-5-NBRCHANGE: EIGRP-IPv4 10: Neighbor 10.1.13.2 (Ethernet1/1) is down: retry limit exceeded
R1#
*Mar 10 10:52:08.063: %DUAL-5-NBRCHANGE: EIGRP-IPv4 10: Neighbor 10.1.13.2 (Ethernet1/1) is up: new adjacency
R1#
*Mar 10 10:52:13.235: %DUAL-5-NBRCHANGE: EIGRP-IPv4 10: Neighbor 10.1.12.2 (Ethernet1/0) is down: retry limit exceeded
R1#
*Mar 10 10:52:18.030: %DUAL-5-NBRCHANGE: EIGRP-IPv4 10: Neighbor 10.1.12.2 (Ethernet1/0) is up: new adjacency
R1#
*Mar 10 10:53:27.663: %DUAL-5-NBRCHANGE: EIGRP-IPv4 10: Neighbor 10.1.13.2 (Ethernet1/1) is down: retry limit exceeded
R1#
====
R2#debug ip eigrp neighbor
R2#
*Mar 10 10:42:34.214: EIGRP: Retransmission retry limit exceeded
*Mar 10 10:42:34.222: EIGRP: Holdtime expired
*Mar 10 10:42:34.222: %DUAL-5-NBRCHANGE: EIGRP-IPv4 10: Neighbor 10.1.12.1 (Ethernet1/0) is down: retry limit exceeded
R2#
*Mar 10 10:42:34.222: Going down: Peer 10.1.12.1 total=0 stub 0, iidb-stub=0 iid-all=0
*Mar 10 10:42:34.222: EIGRP: Handle deallocation failure [0]
*Mar 10 10:42:34.224: EIGRP: Neighbor 10.1.12.1 went down on Ethernet1/0
R2#
*Mar 10 10:42:37.968: EIGRP: New peer 10.1.12.1
R2#
*Mar 10 10:42:37.968: %DUAL-5-NBRCHANGE: EIGRP-IPv4 10: Neighbor 10.1.12.1 (Ethernet1/0) is up: new adjacency
*Mar 10 10:42:38.197: EIGRP: Retransmission retry limit exceeded
*Mar 10 10:42:38.202: EIGRP: Holdtime expired
Am I missing anything on ACL 130?
Solved! Go to Solution.
- Labels:
-
Access List
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2023 10:27 AM
No changes.
Extended IP access list 121
10 permit tcp 10.1.0.0 0.0.255.255 any eq 22
Extended IP access list 122
10 permit udp 10.1.0.0 0.0.255.255 any range 33434 33464
Extended IP access list 130
10 permit eigrp any any (239 matches)
Extended IP access list 131
10 permit ip 10.1.0.0 0.0.255.255 any
Extended IP access list 132
10 permit eigrp any host 224.0.0.10
Extended IP access list 133
10 permit eigrp host 224.0.0.10 any
R1#show class-map
Class Map match-any CoPP-CRITICAL (id 1)
Match access-group 130
Match access-group 131
Match access-group 132
Match access-group 133
Class Map match-all CoPP-NORMAL (id 2)
Match access-group 122
Class Map match-any class-default (id 0)
Match any
Class Map match-all CoPP-IMPORTANT (id 3)
Match access-group 121
R1#show policy-map control-plane input
Control Plane
Service-policy input: CoPP
Class-map: CoPP-CRITICAL (match-any)
1908 packets, 131969 bytes
5 minute offered rate 0000 bps, drop rate 0000 bps
Match: access-group 130
315 packets, 21668 bytes
5 minute rate 0 bps
Match: access-group 131
0 packets, 0 bytes
5 minute rate 0 bps
Match: access-group 132
0 packets, 0 bytes
5 minute rate 0 bps
Match: access-group 133
0 packets, 0 bytes
5 minute rate 0 bps
police:
cir 1000000 bps, bc 50000 bytes, be 50000 bytes
conformed 1908 packets, 131969 bytes; actions:
transmit
exceeded 0 packets, 0 bytes; actions:
transmit
violated 0 packets, 0 bytes; actions:
transmit
conformed 0000 bps, exceeded 0000 bps, violated 0000 bps
Class-map: CoPP-IMPORTANT (match-all)
0 packets, 0 bytes
5 minute offered rate 0000 bps, drop rate 0000 bps
Match: access-group 121
police:
cir 100000 bps, bc 20000 bytes, be 20000 bytes
conformed 0 packets, 0 bytes; actions:
transmit
exceeded 0 packets, 0 bytes; actions:
drop
violated 0 packets, 0 bytes; actions:
drop
conformed 0000 bps, exceeded 0000 bps, violated 0000 bps
Class-map: CoPP-NORMAL (match-all)
0 packets, 0 bytes
5 minute offered rate 0000 bps, drop rate 0000 bps
Match: access-group 122
police:
cir 64000 bps, bc 64000 bytes, be 64000 bytes
conformed 0 packets, 0 bytes; actions:
transmit
exceeded 0 packets, 0 bytes; actions:
drop
violated 0 packets, 0 bytes; actions:
drop
conformed 0000 bps, exceeded 0000 bps, violated 0000 bps
Class-map: class-default (match-any)
8980 packets, 685073 bytes
5 minute offered rate 2000 bps, drop rate 2000 bps
Match: any
police:
cir 8000 bps, bc 1500 bytes, be 1500 bytes
conformed 8980 packets, 685073 bytes; actions:
drop
exceeded 0 packets, 0 bytes; actions:
drop
violated 0 packets, 0 bytes; actions:
drop
conformed 2000 bps, exceeded 0000 bps, violated 0000 bps
R1#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2023 11:07 AM
this way
Class Map match-all CoPP-CRITICAL-130
Match access-group 130
Class Map match-all CoPP-CRITICAL-131
Match access-group 131
Class Map match-all CoPP-CRITICAL-132
Match access-group 132
Class Map match-all CoPP-CRITICAL-133
Match access-group 133
note:- add policer for each class
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2023 11:30 AM
@MHM Cisco World thank you for your suggestion. I tried it and unfortunately did not work. eigrp still flaps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2023 11:42 AM - edited 03-11-2023 11:47 AM
ok let me apply policer value you use and see result in my side.
show policy-map control-plane input <<- PLEASE share output after last config you enter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2023 12:14 PM
R1#show policy-map control-plane input
Control Plane
Service-policy input: CoPP
Class-map: CoPP-CRITICAL (match-any)
168 packets, 11855 bytes
5 minute offered rate 0000 bps, drop rate 0000 bps
Match: access-group 130
168 packets, 11855 bytes
5 minute rate 0 bps
police:
cir 1000000 bps, bc 50000 bytes, be 50000 bytes
conformed 168 packets, 11855 bytes; actions:
transmit
exceeded 0 packets, 0 bytes; actions:
transmit
violated 0 packets, 0 bytes; actions:
transmit
conformed 0000 bps, exceeded 0000 bps, violated 0000 bps
Class-map: CoPP-CRITICAL-2 (match-any)
0 packets, 0 bytes
5 minute offered rate 0000 bps, drop rate 0000 bps
Match: access-group 131
0 packets, 0 bytes
5 minute rate 0 bps
police:
cir 1000000 bps, bc 50000 bytes, be 50000 bytes
conformed 0 packets, 0 bytes; actions:
transmit
exceeded 0 packets, 0 bytes; actions:
transmit
violated 0 packets, 0 bytes; actions:
transmit
conformed 0000 bps, exceeded 0000 bps, violated 0000 bps
Class-map: CoPP-CRITICAL-3 (match-any)
0 packets, 0 bytes
5 minute offered rate 0000 bps, drop rate 0000 bps
Match: access-group 132
0 packets, 0 bytes
5 minute rate 0 bps
police:
cir 1000000 bps, bc 50000 bytes, be 50000 bytes
conformed 0 packets, 0 bytes; actions:
transmit
exceeded 0 packets, 0 bytes; actions:
transmit
violated 0 packets, 0 bytes; actions:
transmit
conformed 0000 bps, exceeded 0000 bps, violated 0000 bps
Class-map: CoPP-IMPORTANT (match-all)
0 packets, 0 bytes
5 minute offered rate 0000 bps, drop rate 0000 bps
Match: access-group 121
police:
cir 100000 bps, bc 20000 bytes, be 20000 bytes
conformed 0 packets, 0 bytes; actions:
transmit
exceeded 0 packets, 0 bytes; actions:
drop
violated 0 packets, 0 bytes; actions:
drop
conformed 0000 bps, exceeded 0000 bps, violated 0000 bps
Class-map: CoPP-NORMAL (match-all)
0 packets, 0 bytes
5 minute offered rate 0000 bps, drop rate 0000 bps
Match: access-group 122
police:
cir 64000 bps, bc 64000 bytes, be 64000 bytes
conformed 0 packets, 0 bytes; actions:
transmit
exceeded 0 packets, 0 bytes; actions:
drop
violated 0 packets, 0 bytes; actions:
drop
conformed 0000 bps, exceeded 0000 bps, violated 0000 bps
Class-map: class-default (match-any)
906 packets, 69120 bytes
5 minute offered rate 2000 bps, drop rate 2000 bps
Match: any
police:
cir 8000 bps, bc 1500 bytes, be 1500 bytes
conformed 906 packets, 69120 bytes; actions:
drop
exceeded 0 packets, 0 bytes; actions:
drop
violated 0 packets, 0 bytes; actions:
drop
conformed 2000 bps, exceeded 0000 bps, violated 0000 bps
Extended IP access list 121
10 permit tcp 10.1.0.0 0.0.255.255 any eq 22
Extended IP access list 122
10 permit udp 10.1.0.0 0.0.255.255 any range 33434 33464
Extended IP access list 130
10 permit eigrp any any (90 matches)
Extended IP access list 131
10 permit eigrp host 224.0.0.10 any
Extended IP access list 132
10 permit eigrp any host 224.0.0.10
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2023 02:16 PM
the EIGRP use multicast and unicast,
multicast not need arp
unicast need arp
and since the class-default is drop which cause the ARP request/reply drop
and the EIGRP can not know the mac address of neighbor and hence it unicast is drop, this make EIGRP flapping.
I solve it without change CoPP by add static ARP to config, but this not solution because sure there are many other protocol use class-default and action drop can cause reachability issue in your network.
thanks
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-13-2023 02:49 PM
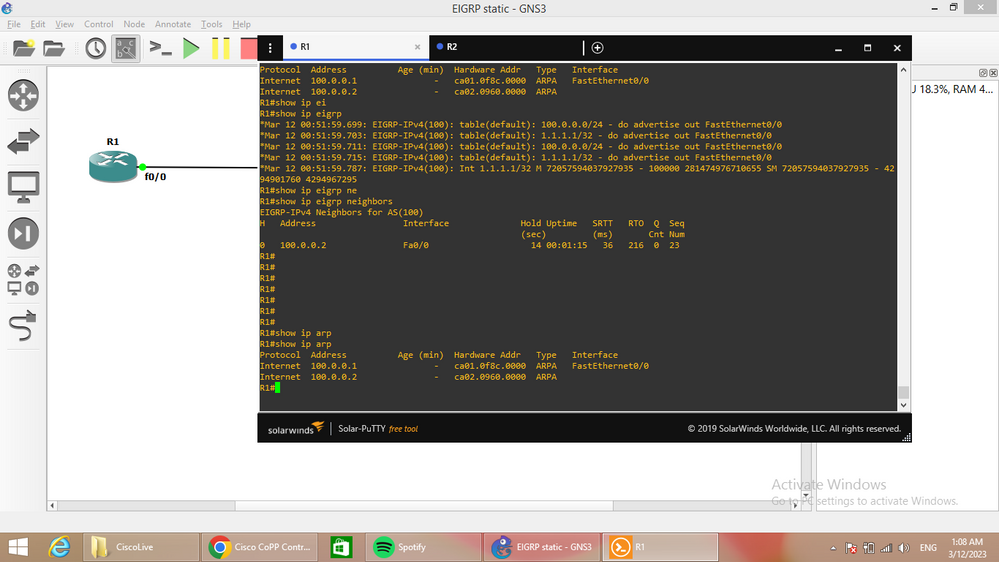
@MHM Cisco World You are completely right ! Your solution helped me a lot. I actually configured the class map like this:
R1#show class-map
Class Map match-any CoPP-CRITICAL (id 1)
Match access-group 130
Match protocol arp <<<<
and since i applied this line the flaps stop.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-13-2023 02:54 PM
You are so so welcome
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide