- Cisco Community
- Technology and Support
- Security
- Other Security Subjects
- My acces-list doesn't work !!!
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2018 04:31 AM - edited 03-10-2019 01:08 AM
Hello everybody,
I have a problem with my access-list.
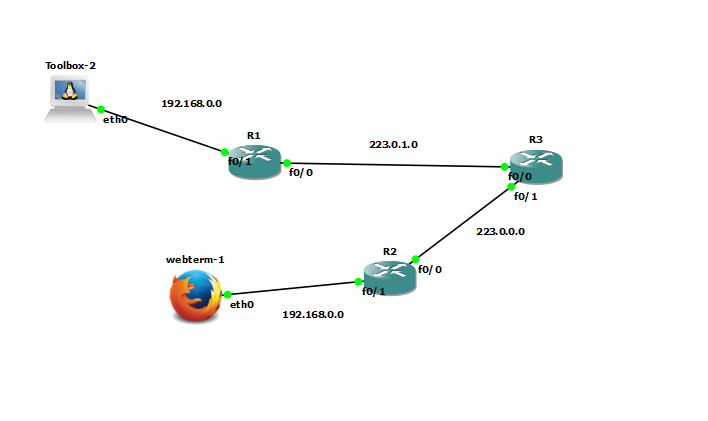
I have a simple topology like you can see on the picture, I'm using OSPF for routing and all seems good, So I'm able to ping the TOOLBOX (which supposed to be the WEBSERVER) from my WEBTERM (docker webterm). I used the NAT outside on the int f0/0 and NAT inside on the int f0/1 of the R1. Now, I wanted to deny access to the TOOLBOX using the extended access-list with http protocol (tcp) so I configure an Access-list 100 with it respective command line and add the command line access-group 100 out to the interface f0/1. Then when I ping the TOOLBOX from the WEBTERM it succed !!!
My topology :
------------------------------------
R1 :
BOX1#sh run
Building configuration...
Current configuration : 2162 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname BOX1
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
no ip icmp rate-limit unreachable
ip cef
!
!
no ip dhcp use vrf connected
ip dhcp excluded-address 192.168.0.20
!
ip dhcp pool BOX
network 192.168.0.0 255.255.255.0
default-router 192.168.0.20
!
!
no ip domain lookup
ip auth-proxy max-nodata-conns 3
ip admission max-nodata-conns 3
!
ip tcp synwait-time 5
!
interface FastEthernet0/0
ip address 223.0.1.2 255.255.255.0
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
!
interface Serial0/0
no ip address
shutdown
clock rate 2000000
!
interface FastEthernet0/1
ip address 192.168.0.20 255.255.255.0
ip access-group 100 out
ip nat inside
ip virtual-reassembly
duplex auto
speed auto
!
interface Serial0/1
no ip address
shutdown
clock rate 2000000
!
interface FastEthernet1/0
!
interface FastEthernet1/1
!
interface FastEthernet1/2
!
interface FastEthernet1/3
!
interface FastEthernet1/4
!
interface FastEthernet1/5
!
interface FastEthernet1/6
!
interface FastEthernet1/7
!
interface FastEthernet1/8
!
interface FastEthernet1/9
!
interface FastEthernet1/10
!
interface FastEthernet1/11
!
interface FastEthernet1/12
!
interface FastEthernet1/13
!
interface FastEthernet1/14
!
interface FastEthernet1/15
!
interface Vlan1
no ip address
!
router ospf 1
log-adjacency-changes
network 223.0.1.0 0.0.0.255 area 0
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 223.0.1.1
!
!
no ip http server
no ip http secure-server
ip nat inside source list BOX1 interface FastEthernet0/0 overload
ip nat inside source static tcp 192.168.0.1 80 223.0.1.2 80 extendable
!
ip access-list standard BOX1
permit 192.168.0.0 0.0.0.255
!
access-list 100 deny tcp host 223.0.0.2 192.168.0.0 0.0.0.255 eq www
no cdp log mismatch duplex
!
!
!
control-plane
!
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
line vty 0 4
login
!
!
end
------------------------------------------------
R2 :
BOX2#sh run
Building configuration...
Current configuration : 1995 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname BOX2
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
no ip icmp rate-limit unreachable
ip cef
!
!
no ip dhcp use vrf connected
ip dhcp excluded-address 192.168.0.25
!
ip dhcp pool BOX
network 192.168.0.0 255.255.255.0
default-router 192.168.0.25
!
!
no ip domain lookup
ip auth-proxy max-nodata-conns 3
ip admission max-nodata-conns 3
!
ip tcp synwait-time 5
!
!
interface FastEthernet0/0
ip address 223.0.0.2 255.255.255.0
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
!
interface Serial0/0
no ip address
shutdown
clock rate 2000000
!
interface FastEthernet0/1
ip address 192.168.0.25 255.255.255.0
ip nat inside
ip virtual-reassembly
duplex auto
speed auto
!
interface Serial0/1
no ip address
shutdown
clock rate 2000000
!
interface FastEthernet1/0
!
interface FastEthernet1/1
!
interface FastEthernet1/2
!
interface FastEthernet1/3
!
interface FastEthernet1/4
!
interface FastEthernet1/5
!
interface FastEthernet1/6
!
interface FastEthernet1/7
!
interface FastEthernet1/8
!
interface FastEthernet1/9
!
interface FastEthernet1/10
!
interface FastEthernet1/11
!
interface FastEthernet1/12
!
interface FastEthernet1/13
!
interface FastEthernet1/14
!
interface FastEthernet1/15
!
interface Vlan1
no ip address
!
router ospf 1
log-adjacency-changes
network 223.0.0.0 0.0.0.255 area 0
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 223.0.0.1
!
!
no ip http server
no ip http secure-server
ip nat inside source list BOX2 interface FastEthernet0/0 overload
!
ip access-list standard BOX2
permit 192.168.0.0 0.0.0.255
!
no cdp log mismatch duplex
!
control-plane
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
line vty 0 4
login
!
!
end
--------------------------------------------------
R3 :
BORDER_ROUTER#sh run
Building configuration...
Current configuration : 1643 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname BORDER_ROUTER
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
no ip icmp rate-limit unreachable
ip cef
!
!
!
!
no ip domain lookup
ip auth-proxy max-nodata-conns 3
ip admission max-nodata-conns 3
!
!
ip tcp synwait-time 5
!
!
interface FastEthernet0/0
ip address 223.0.1.1 255.255.255.0
duplex auto
speed auto
!
interface Serial0/0
no ip address
shutdown
clock rate 2000000
!
interface FastEthernet0/1
ip address 223.0.0.1 255.255.255.0
duplex auto
speed auto
!
interface Serial0/1
no ip address
shutdown
clock rate 2000000
!
interface FastEthernet1/0
!
interface FastEthernet1/1
!
interface FastEthernet1/2
!
interface FastEthernet1/3
!
interface FastEthernet1/4
!
interface FastEthernet1/5
!
interface FastEthernet1/6
!
interface FastEthernet1/7
!
interface FastEthernet1/8
!
interface FastEthernet1/9
!
interface FastEthernet1/10
!
interface FastEthernet1/11
!
interface FastEthernet1/12
!
interface FastEthernet1/13
!
interface FastEthernet1/14
!
interface FastEthernet1/15
!
interface Vlan1
no ip address
!
router ospf 1
log-adjacency-changes
network 223.0.0.0 0.0.0.255 area 0
network 223.0.1.0 0.0.0.255 area 0
!
ip forward-protocol nd
!
!
no ip http server
no ip http secure-server
!
no cdp log mismatch duplex
!
control-plane
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
line vty 0 4
login
!
!
end
-----------------------------------------------
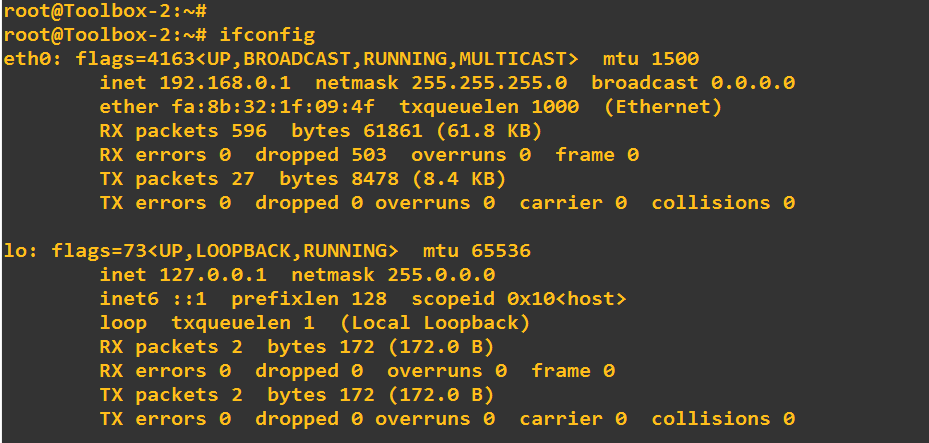
TOOLBOX :
--------------------------------
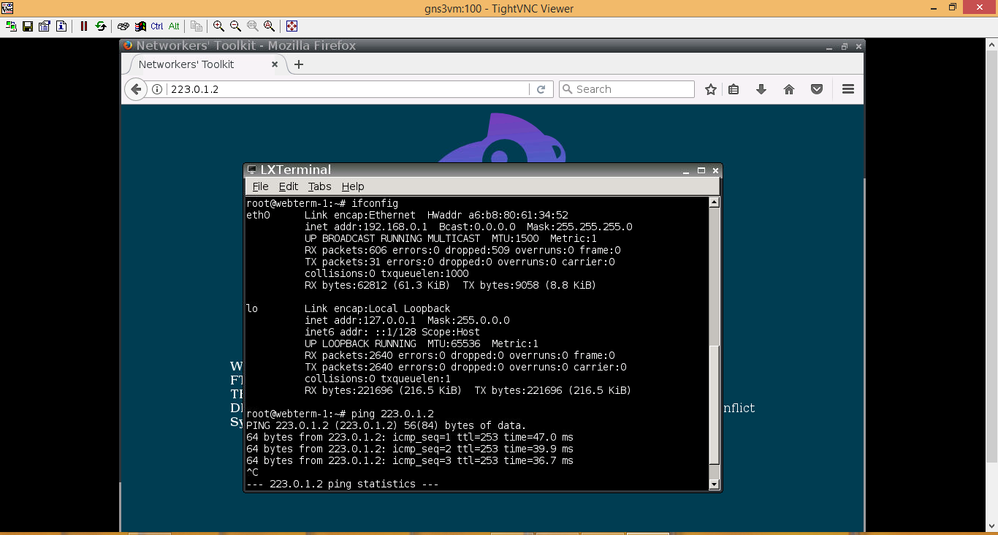
WEBTERM :
When I ping 223.0.1.2 it works even if I the access-list 100 exists !
I don't know where is the problem and thank's everyone for helpful.
Solved! Go to Solution.
- Labels:
-
Other Security Topics
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2018 06:41 AM
If you apply the ACL as it's configured now, everything will be denied, which I think is not your intention.
If you just want to permit tcp/80 to the webserver, then explicitly permit it and then either rely on the implicit deny at the end of the ACL or define an deny any any with log ACE rule, so you can determine what is being blocked.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2018 04:04 PM - edited 12-04-2018 04:06 PM
At the end I detected the problem and it was not my configuration, I just deleted the webterm and addeed another new one and restart the R2 using my first configuration and it works now.
The ACL 100 that I used is on the inside interface and it is good for me because if I want to add another interface, the trafic doesn't block as if I place it on the out interface.
So, you have to be careful if you are using WEBTERM because the problem is it in.
thank you fos your helpful, everyday I learn new things and I'm proud to be a tiny part of this community :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2018 06:07 AM
Quick look You have access list to deny WWW not for Ping
access-list 100 deny tcp host 223.0.0.2 192.168.0.0 0.0.0.255 eq www
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2018 06:17 AM
Hi @balaji.bandi and thank you for reply
Yes of course you're right but when I try to access to the TOOLBOX from the navigator MOZILLA it's works ! logically it mustn't work even if the ping works :
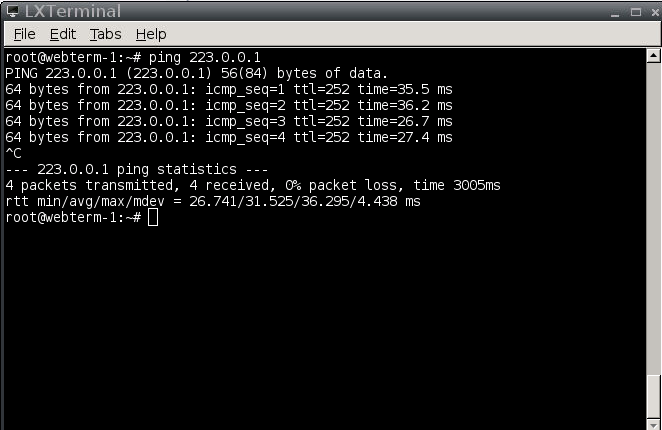
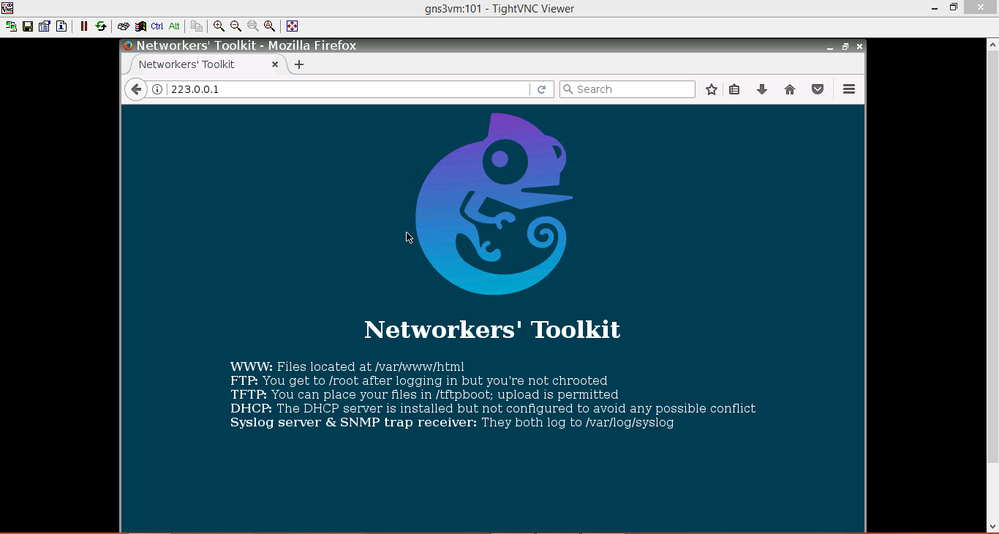
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2018 06:31 AM
Check the ACL as suggest by @Rob Ingram and do the test.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2018 06:24 AM - edited 12-04-2018 06:26 AM
Hi,
You have applied the ACL to the inside interface Fa0/1, but you are pinging the outside interface Fa0/0, so the traffic would never hit the ACL to be denied. Ans you are only natting tcp/80 to the server, not all traffic.
You should look to apply the ACL inbound on the outside interface and amend it's configuration. Remember there is an implicit deny at the end of an ACL. In your example you are explicitly denying www traffic to the private IP address of the server, then the implicit deny would deny all other traffic. Probavly not what you wanted.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2018 06:36 AM - edited 12-04-2018 06:42 AM
Hi @Rob Ingram
If I apply the ACL on the int F0/0 of my router, All the inside network will be unaccessible, is it true ?
Because I'm going to deny the inbounded interface of the router, so if I add another TOOLBOX, this will be blocked and I don't want to do that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2018 06:41 AM
If you apply the ACL as it's configured now, everything will be denied, which I think is not your intention.
If you just want to permit tcp/80 to the webserver, then explicitly permit it and then either rely on the implicit deny at the end of the ACL or define an deny any any with log ACE rule, so you can determine what is being blocked.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2018 06:44 AM
okay sir,
I've understood, I'm going to test it now thank you for your help my friend :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2018 07:06 AM - edited 12-04-2018 07:07 AM
@Rob Ingram Now it works,
the ping is worked and the access with the navigator don't work and this is what I wanted to accomplish, I added the command line on the interface F0/1 :
'ip access-group 100 in' like you told me to do.
If I supposed that there is another WEBTERM connected with R3 with the same configuration of interfaces which is on the R2 (NAT,PAT) , and if I test the access to TOOLBOX, do you think that it will work ? and thank you very much my friend, you made my day :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2018 07:16 AM
Not sure of what you've configured, so test it and if any problem post the updated configuration for review.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2018 07:20 AM
Good Idea,
I'm going to test it later and post the configuration if I have problem, or just tell you that it works :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2018 04:04 PM - edited 12-04-2018 04:06 PM
At the end I detected the problem and it was not my configuration, I just deleted the webterm and addeed another new one and restart the R2 using my first configuration and it works now.
The ACL 100 that I used is on the inside interface and it is good for me because if I want to add another interface, the trafic doesn't block as if I place it on the out interface.
So, you have to be careful if you are using WEBTERM because the problem is it in.
thank you fos your helpful, everyday I learn new things and I'm proud to be a tiny part of this community :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2018 09:11 AM
HTH
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: