- Cisco Community
- Technology and Support
- Security
- Other Security Subjects
- Re: Security design: DMZ ports on internal switch ,do you think good or bad?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Security design: DMZ ports on internal switch ,do you think good or bad?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2019 02:43 AM
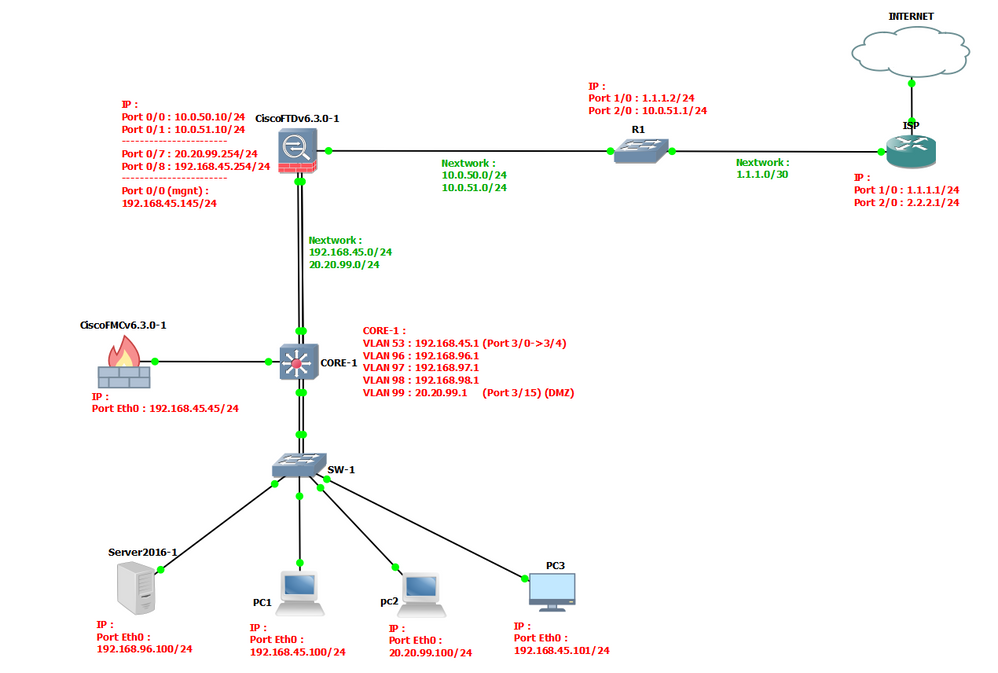
My company is rebuilding the DMZ model, my subnet will be primarily due to the core level DHCP switch and the firewall asa I use primarily to give the internet subnet, nat and the route for the VPN network to see each other, but there is one thing As the network model went into operation so very limited in refreshing, I tried to do a job of creating a VLAN layer in the core switch and using an access-list to prevent access to my subnet. (I think it's DMZ) and create a route-map line for the core switch pointing to firepower so that zone dmz can use the internet, I see it working, but I'm not sure that's the right thing because of the rules on the firewall, so that the network of several local subnets cannot communicate with the DMZ, if you want to make the subnet communicate, you must perform permi t in the access-list on the core switch and that makes me not really interested when the firewall doesn't do what I want. do you have any solution so that I can do the DMZ zone better.
- Labels:
-
Security Management
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2019 04:04 PM
Normally you would use a separate physical switch for the DMZ, connected to separate interface on the firewall. You would control traffic to/from the DMZ on the firewall, not on an ACL on the switch.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2019 05:53 PM - edited 08-08-2019 06:09 PM
Normally I will do the same but the system has only one blade server, I build the VMware system on it and it is connected to the core switch by a physical path (6-way trunk), including the FMC's I'm also in it and all layer 2 switches (end users) focus on two core 3850 switches (Stackwise), I can't physically separate the DMZ line except to do a VLan and separate it from the system (Because my server only communicates with a 10Gb fiber port and my firewall uses only 1Gb fiber, I must concentrate them on the core switch). internally, I tried to add a physical route and pushed my route-map for my core and 5525x firewall switch to the Vlan that I created with the intention of being the DMZ zone, It works when I try to create blocking rules but there is one thing: there are rules for an internal subnet that can communicate with the DMZ, it doesn't seem to work, I'm still wondering what I'm doing. What is wrong?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2019 07:07 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2019 09:30 PM - edited 08-09-2019 09:34 PM
Thank you.
The problem is that I cannot remove svi on VLAN99, I created the route-map and the correct traceroute to the inside-2 (dmz) port as intended, but only failed where the internal network could not be communicated. with zone dmz.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: