- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Re: 802.11 probe requests with 00:00:00:00:00:00 source mac
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
802.11 probe requests with 00:00:00:00:00:00 source mac
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2018 08:13 AM - edited 07-05-2021 09:24 AM
Hello,
We're having a weird issue that I hope someone here can shed light on.
On several of our 4500 VSS pairs of distribution switches we've observed this type of log message every 6 hours:
Oct 28 11:15:06.463 EDT: %C4K_L2MAN-6-INVALIDSOURCEADDRESSPACKET: (Suppressed 20025 times)Packet received with invalid source MAC address (00:00:00:00:00:00) on port Po40 in vlan 508
We have traced the source of these logs to one of our edge 3850 switch stacks that are running 16.3.6 code. There are no such logs appearing on the 3850 stack however.
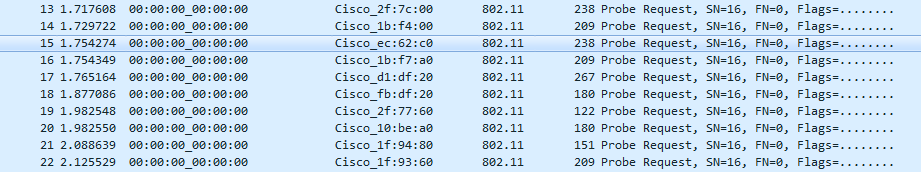
After placing a sniffer on the the 3850 stacks' portchannel uplink to the distribution switch 4500 vss pair, We discovered that the this odd traffic is coming from ALL of the Cisco APs connected to this stack. The traffic in question is predominantly probe requests to other APs.
Any idea why just these 20 APs out of the hundreds that we have across our enterpirse, are performing this way, generating these malformed frames?
Thanks in advance.
John
- Labels:
-
Aironet Access Points
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2018 10:46 AM
What model of APs are they ? What version of AireOS running on these AP/WLC ? All APs connected to that 3850 behaving in same manner ?
Do you have another 3850 running on 16.3.6 & not having this issue ?
If a given AP directly connect to that 3850, pls take a capture from AP connected switchport to confirm its coming from a given AP.
HTH
Rasika
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2018 11:09 AM
Thank you very much for your reply Rasika.
To answer your questions...
AP's are AIR-AP3802I-A-K9 running this code 8.2.166.0.
All AP's on this stack are exhibiting this behavior.
We do not have any other 3850 stack running this code.
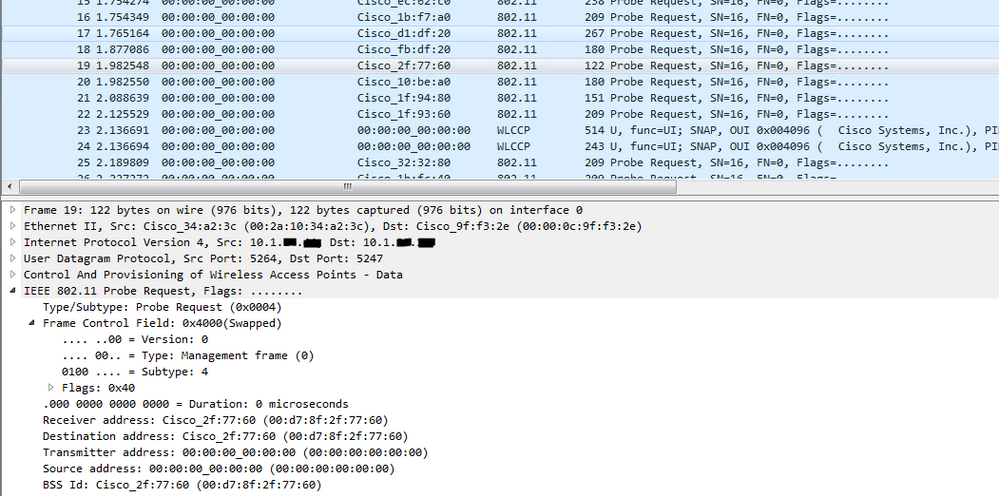
In response to your request, I took captures on a few of the AP ports and quickly realized something I had not realized before... the destination MAC addresses of these frames are the base radio MACs of the APs themselves. The traffic is not originating on the AP switch ports, its destined there... but just to the APs of this stack, for some reason.
I will keep digging around to see I can locate the source of the traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2018 11:21 AM
I did not have good experience with IOS-XE 16.x.x codes yet :) Running couple of stacks 16.6.4a at the moment (3802 had trouble registering after power outage with 16.6.4). Most of our 3850 still running 3.7.5E
If you could not figure it out source of these traffic, I would suggest to try different software version on 3850
HTH
Rasika
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2018 11:23 AM
What's even more confusing to me is that these 802.11 frames going TO the base radio MAC of the AP, are encapped in an ipv4 packet going from the AP to the WLC (which is in the opposite direction to the 802.11 frames).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2018 11:30 AM
Yes, this is strange. Probe requests should not go to wire. So it could be AP side of issue.
Pls check it on a working 3850 connected AP & ensure this behavior is not there.
Rasika
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2018 08:24 AM
Something in that location bridging wireless traffic onto the LAN?
I can't see how the switch or its OS could make any difference to the behaviour of the APs.
Please click Helpful if this post helped you and Select as Solution (drop down menu at top right of this reply) if this answered your query.
------------------------------
TAC recommended codes for AireOS WLC's and TAC recommended codes for 9800 WLC's
Best Practices for AireOS WLC's, Best Practices for 9800 WLC's and Cisco Wireless compatibility matrix
Check your 9800 WLC config with Wireless Config Analyzer using "show tech wireless" output or "config paging disable" then "show run-config" output on AireOS and use Wireless Debug Analyzer to analyze your WLC client debugs
Field Notice: FN63942 APs and WLCs Fail to Create CAPWAP Connections Due to Certificate Expiration
Field Notice: FN72424 Later Versions of WiFi 6 APs Fail to Join WLC - Software Upgrade Required
Field Notice: FN72524 IOS APs stuck in downloading state after 4 Dec 2022 due to Certificate Expired
- Fixed in 8.10.190.0, latest 9800 releases, 8.5.182.11 (8.5 mainline) and 8.5.182.108 (8.5 IRCM)
Field Notice: FN70479 AP Fails to Join or Joins with 1 Radio due to Country Mismatch, RMA needed
How to avoid boot loop due to corrupted image on Wave 2 and Catalyst 11ax Access Points (CSCvx32806)
Field Notice: FN74035 - Wave2 APs DFS May Not Detect Radar After Channel Availability Check Time
Leo's list of bugs affecting 2800/3800/4800/1560 APs
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: