- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Re: Guest access on the 5508 WLC
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2013 09:06 AM - edited 07-03-2021 11:22 PM
Hi,
I'm looking to implement guest WiFi access with web authentication on one of our 5508 WLC (currently deployed within a sandbox environment), but looking for some assistance.
The WLC currently has a single connection from port 1 to the 'Test Site 2' switch. This is a dot1q trunk. On the WLC, the interface (for port 1) is configured as follows:
Name: Management
Guest LAN: No
Quarantine: No
Enable NAT: No
VLAN ID: 0
IP Address: 10.0.254.105
Mask: 255.255.255.0
Gateway: 10.0.254.1
Physical Port No.: 1
Backup Port: 0
Active Port: 1
Enable Dynamic AP Management: Yes
Primary DHCP Server: 10.0.254.10
ACL: None
Currently, I have one WLAN configured with the profile name 'Guest Test 1', it's enabled and broadcasting the SSID. Security is L3 only with web authentication configured. The WLAN is configured to use the interface names "guest_wifi".
The configuration for the Interface "guest_wifi" is:
Name: guest_wifi
Guest LAN: No
Quarantine: No
Enable NAT: No
VLAN ID: 99
IP Address: 10.99.254.100
Mask: 255.255.255.0
Gateway: 10.99.254.1
Physical Port No.: 1
Backup Port: 0
Active Port: 1
Enable Dynamic AP Management: No
Primary DHCP Server: 10.0.254.105 (The WLC is configured to issue addresses for the guest WLAN)
ACL: None (This will eventually be locked down, but for the purposes of testing, I've disabled the ACL)
The default gateway for the Test Site 2 is 10.0.254.1, and has a sub interface configured which is in VLAN 99 with an IP address of 10.99.254.1 /24.
Diagram of the setup...
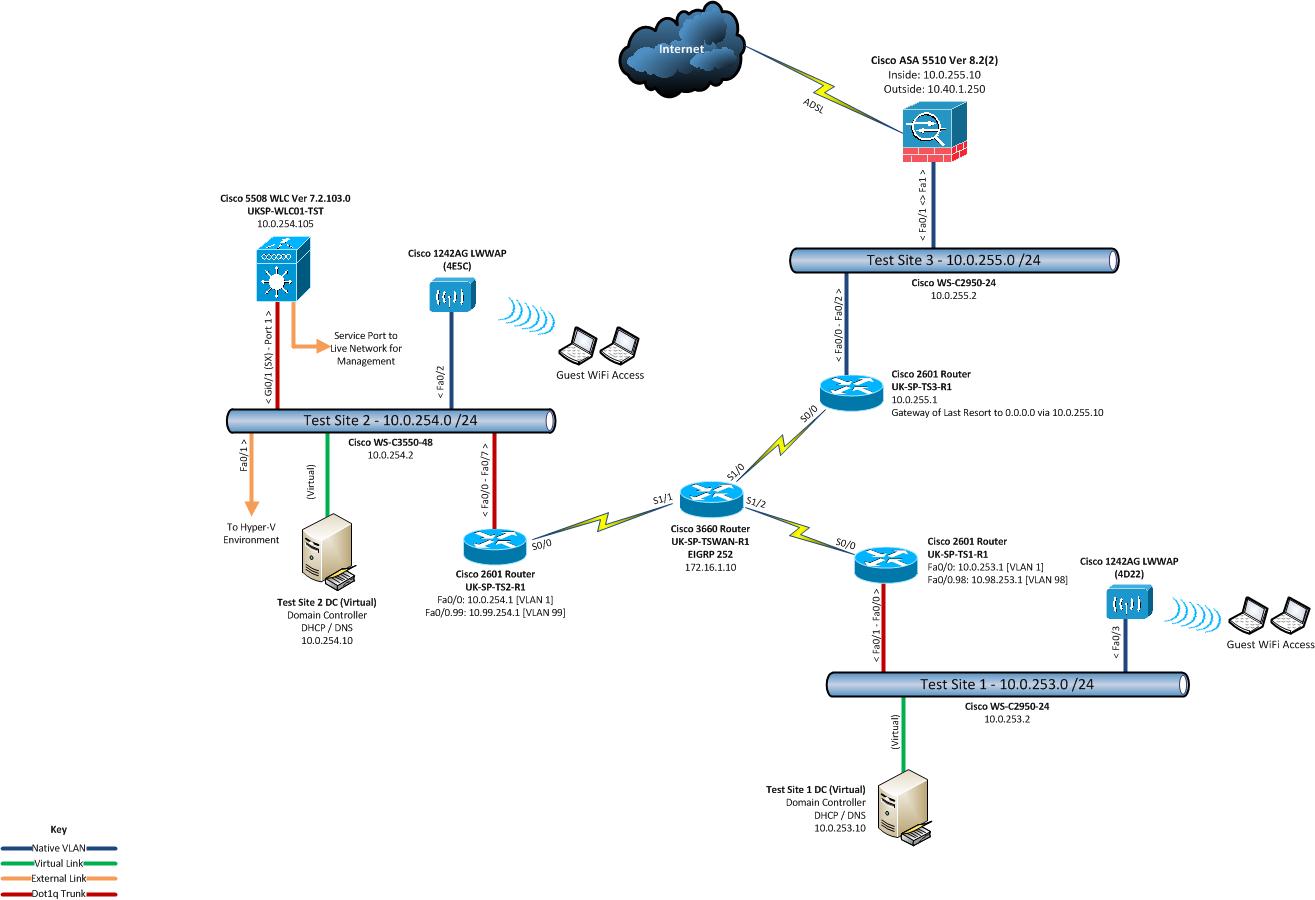
The issue is that when a client connects to the WLAN, it receives an IP address okay (10.99.254.x address), but doesn't seem to be able to contact the WLC to get the web authentication page. Eventually, the WLC terminates the connection due to an authentication failure.
I know there is probably a load more questions on the configuration that I haven't listed, but I'm happy to answer any queries to help solve this.
Equally - does it sound like I'm taking the correct approach here? The idea is that clients connect to the guest WLAN, which puts them on VLAN 99 and routes traffic through to the ASA and then onto the internet.
Thanks
Tony
Solved! Go to Solution.
- Labels:
-
Wireless LAN Controller
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2013 01:58 AM
No problem. The main reason WebAuth doesn't work if the network is fine is DNS. The clients homepage must be http and not an secure site for one. The WLC must be able to resolve the devices homepage before the WebAuth page is displayed to the user. If using a 3rd party certificate, the clients must be able to resolve the FQDN from the DNS server that the client obtains through DNS.
Here is a good guide
https://supportforums.cisco.com/docs/DOC-13954
Sent from Cisco Technical Support iPhone App
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2013 09:21 AM
If you remove the webauth and test just with an open ssid, you can get an ip address and connect to the internet? Just want to make sure the routing is working first?
Thanks,
Scott
Help out other by using the rating system and marking answered questions as "Answered"
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2013 01:42 AM
Hi Scott,
Thanks for the reply, sounds like a sensible move! I'm out of the office now until the 28th Jan, but will try your suggestion when I get back and let you know.
Thanks again
Tony
Sent from Cisco Technical Support iPhone App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2013 01:58 AM
No problem. The main reason WebAuth doesn't work if the network is fine is DNS. The clients homepage must be http and not an secure site for one. The WLC must be able to resolve the devices homepage before the WebAuth page is displayed to the user. If using a 3rd party certificate, the clients must be able to resolve the FQDN from the DNS server that the client obtains through DNS.
Here is a good guide
https://supportforums.cisco.com/docs/DOC-13954
Sent from Cisco Technical Support iPhone App
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2013 06:24 AM
Hi Scott,
Indeed, the issue was with the routing to the internet, and so (as you said above), the WLC will not have been able to resolve the clients homepage in order to proceed with Web Authentication.
The routing issue has been resolved, and now all is working well from this test site (Test Site 2 on the diagram)
I am however now facing another issue on the same network, but from Test Site 1. I need to understand the issue a little more, but will open another discussion if I get stumped again!
Thanks for your help Scott.
Regards
Tony
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2013 07:23 AM
No problem Tony! Just post and one of us will answer:)
Thanks,
Scott
Help out other by using the rating system and marking answered questions as "Answered"
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2013 08:34 AM
Hi again Scott (and others!),
I'm stumped again with guest access, but from a different site.
I've updated the diagram in my original post, showing clients accessing the guest wireless network from Test Site 1. Clients are receiving an IP address from the WLC, but have no connectivity other than to the interface IP address on the WLC.
I've disabled WebAuth and ACLs for the moment. The full configuration is:
Name: TS1_Int_Guest
Guest LAN: No
Quarantine: No
Enable NAT: No
VLAN ID: 98
IP Address: 10.98.253.254
Mask: 255.255.255.0
Gateway: 10.98.253.1
Physical Port No.: 1
Backup Port: 0
Active Port: 1
Enable Dynamic AP Management: No
Primary DHCP Server: 10.0.254.105 (The WLC is configured to issue addresses for the guest WLAN - 10.98.253.10 to 20/24)
ACL: None (This will eventually be locked down, but for the purposes of testing, I've disabled the ACL)
The default gateway for the Test Site 1 is 10.0.253.1, and has a sub interface configured which is in VLAN 98 with an IP address of 10.98.253.1 /24.
Once a client is connected to the WLAN on Test Site 1, it receives an IP address (e.g. 10.98.253.10), and can ping the interface for the WLAN (10.98.253.254), but not the gateway address (10.98.253.1) or beyond.
Incidentally, I can ping the VLAN 98 IP address (10.98.253.1) from the switch on Test Site 2, but not from the WLC.
Routing issue from the WLC??
Thanks
Tony
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2013 08:37 AM
so really dumb question...but are you allowing VLAN 98 on the trunk to the WLC?
HTH,
Steve
------------------------------------------------------------------------------------------------
Please remember to rate useful posts, and mark questions as answered
Steve
------------------------------------------------------------------------------------------------
Please remember to rate useful posts, and mark questions as answered
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2013 09:09 AM
Hi Steve - the switch port that connects the WLC is a trunk with no restrictions (ACLs) applied.
Thanks
Tony
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2013 09:20 AM
can you share the config of the port?
The WLC doesn't 'route', it's just going to dump the traffic onto the port in the VLAN linked to the interface.
HTH,
Steve
------------------------------------------------------------------------------------------------
Please remember to rate useful posts, and mark questions as answered
Steve
------------------------------------------------------------------------------------------------
Please remember to rate useful posts, and mark questions as answered
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2013 03:21 AM
Switch port config (connection to WLC management interface - port 1)
interface GigabitEthernet0/1
switchport trunk encapsulation dot1q
switchport mode trunk
end
WLC port configuration (management interface)
Interface Name................................... management
MAC Address...................................... d4:8c:b5:a7:05:80
IP Address....................................... 10.0.254.105
IP Netmask....................................... 255.255.255.0
IP Gateway....................................... 10.0.254.1
External NAT IP State............................ Disabled
External NAT IP Address.......................... 0.0.0.0
VLAN............................................. untagged
Quarantine-vlan.................................. 0
Active Physical Port............................. 1
Primary Physical Port............................ 1
Backup Physical Port............................. Unconfigured
Primary DHCP Server.............................. 10.0.254.10
Secondary DHCP Server............................ Unconfigured
DHCP Option 82................................... Disabled
ACL.............................................. Unconfigured
AP Manager....................................... Yes
Guest Interface.................................. No
L2 Multicast..................................... Disabled
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2013 03:42 AM
Could this be down to NOT using Interface Groups?
Test Site 1 and Test Site 2 are different subnets, though I want Guest access to function the same way for all sites. (i.e. client connects to AP on Test Site 1, receives a 10.99.254.x IP address, authenticates through WebAuth and then has internet access. A client on test site 2, will go through the same process, but get an IP from the 10.99.253.x subnet).
Thanks
Tony
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2013 04:59 AM
Okay this is getting confusing... this Is how I would do it.
Option 1:
I would make sure that on the guest ssid, that flexconnect local switching is disabled. So basically all the guest traffic will tunnel back to the WLC at test site 2 and be placed in the same interface as guest in test site 1. This is the easiest way.
Option 2:
Is that you create AP's groups and you still keep the guest ssid the same as above... not using local switching and you define and ap group for test 1 and test 2. In there, you map your guest ssid to the interface on the WLC. SO in the WLC, you need to have two subnet's created for guest at test site 1 and test site 2.
Thanks,
Scott
Help out other by using the rating system and marking answered questions as "Answered"
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-06-2013 05:24 AM
Hi Scott,
It most certainly is confusing!
My current config is exactly as per your Option 2 (though my guest SSIDs are different)
TS1 (Test site 1) - Clients receive DHCP IP address, but have no access other than can ping the interface IP.
Interface (Dynamic)
- Name: TS1_Int_Guest
- VLAN 98
- IP Address: 10.98.253.254
- Mask: 255.255.255.0
- Gateway: 10.98.253.1
- Dynamic AP Mgt: No
- DHCP Server: WLC
- ACL: None (disabled for testing)
WLAN
- Type: WLAN
- Name: TS1_WLAN_Guest
- Status: Enabled
- Security Policy: None (disabled Web-Auth for testing)
- FlexConnect: Disabled
AP Group
TS1_AP_Group
- WLANs: TS1_WLAN_Guest
- Interface: TS1_Int_Guest
- Contains 1 AP (MAC ending 4E5C)
TS2 (Test site 2) - Currently works fine!
Interface (Dynamic)
- Name: TS2_Int_Guest
- VLAN 99
- IP Address: 10.99.254.254
- Mask: 255.255.255.0
- Gateway: 10.99.254.1
- Dynamic AP Mgt: No
- DHCP Server: WLC
- ACL: Configured & working
WLAN
- Type: WLAN
- Name: TS2_WLAN_Guest
- Status: Enabled
- Security Policy: Web-Auth
- FlexConnect: Disabled
AP Group
TS2_AP_Group
- WLANs: TS2_WLAN_Guest
- Interface: TS2_Int_Guest
- Contains 1 AP (MAC ending 4D22)
I have two DHCP scopes on the WLC (one for each subnet).
I'm currently in the process of ensure all router IOS versions are the same, the configs are the same, plus I've also spanned the port from the AP at Test Site 1 and run through a Wireshark capture. I can see the CAPWAP packets between the WLC and the AP, and within that I can see ping replies from the TS1 interface IP on the WLC. However, I can't see any other ICMP packets that I'm pinging from the client (i.e. pinging the gateway at TS1... 10.98.253.1).
Sorry if this is confusing - I am trying to keep the explainations as simple as possible.
Tony
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


