- Cisco Community
- Technology and Support
- Security
- Physical Security
- What's the details on the
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
IPICS IDC certificate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2013 04:36 AM
Hi all,
i am installing IDC from ipics 4.5.2 on my PC
but i can not login because there is certificate issue.
how can i get the certificate from ipics server?
here is the error
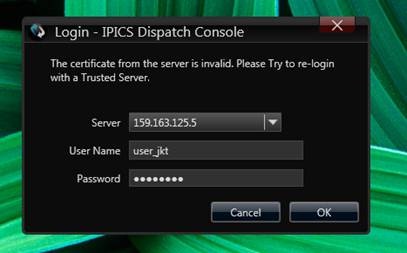
Thx,
Anju Josua
- Labels:
-
Physical Security
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2013 02:27 AM
already solve
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2016 07:45 AM
What was the fix?
thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2016 03:44 PM
Hi Gilbert, I have this same issue. Still working on it but the LCCMreport.log shows this (ip address removed).
Cisco.PSBU.Exceptions.ServerException: Error logging into server x.x.x.x(x.x.x.x) ---> System.Net.WebException: The request was aborted: Could not create SSL/TLS secure channel.
Furthermore I have uninstalled/reinstalled the IDC several time but it NEVER asks for a certificate like it is supposed to when logging in the first time.
CiscoTAC mentioned that removing Windows Update KB3172605 may help since it is tied to certificate validation. It did not solve my problem but maybe it will for you?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2016 08:28 AM
All the usual culprits ruled out? (Time sync between server and client mismatch, etc...). I'm not familiar with
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2016 08:58 AM
Thx Scott. I do not think that is the issue. Whats worse is that is was working on my PC just fine this summer (over SSL VPN and a different time zone). I think we are dealing with a MS office issue. I plan to uninstall all updates on a test PC later on today.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2016 06:34 AM
What's the details on the actual certificate being presented from the server? Perhaps it's just no longer valid / has been impacted or implicated in a security update from MS (as you suspect).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-01-2016 07:05 AM
Hey Scott,
So you were on the right track. Here is the fix for the login error I had.
SR 680790890
Just for your awareness, here is the defect opened about the windows patch I mentioned when we started this case. It certainly sounds like a match for your problem. I am also including a workaround being used for some of our other products. You might try this workaround and see if it resolves the problem.
CSCvb50747 - Server and IDC login failure due to credential issue w/ IE 11 plus Win7 update KB3172605
Work around information for another Cisco product facing the same issue.
The KB's are actually a pack of updates that installs this one in particular KB3161639 Update to add new cipher suites to Internet Explorer and Microsoft Edge in Windows. As you look more closely at this KB, these two Transport Layer Security (TLS) cipher suites are added to the list of ones used by IE: TLS_DHE_RSA_WITH_AES_128_CBC_SHA and TLS_DHE_RSA_WITH_AES_256_CBC_SHA.
In Firefox these can be disabled through this procedure:
1 Navigate to about:config.
2 Search for security.ssl3.dhe in that.
3 Double click on security.ssl3.dhe_rsa_aes_256_sha and security.ssl3.dhe_rsa_aes_128_sha to set them to false.
However with IE11 there is no workaround that can be done through the browser. Instead, an administrator modifies the local or domain group policy to exclude the ciphers in the SSL configuration.
In order to modify the local policy through gpedit.msc Windows module, navigate to Computer Configuration >Administrative Tools >Network >SSL Configuration Settings >SSL Cipher Suite Order.
If the suite order is set to Disabled or Not Configured then the default order is used and block access to UCCX/Finesse. Instead, this should be set to Enabled and the cipher suite order should be modified to exclude the two ciphers mentioned above. Note the restriction that the list of ciphers are to be used, as they cannot exceed 1023 characters in length. The cipher list known to work with UCCX/Finesse 10.6 is as these:
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384_P384,
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P384,
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P384,
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P256,
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P256,
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P384,
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P384,
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P256,
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P256,
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P384,
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P256,
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P384,
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P256,
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P384,
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P256,
TLS_DHE_DSS_WITH_AES_256_CBC_SHA256,
TLS_DHE_DSS_WITH_AES_256_CBC_SHA,
TLS_DHE_DSS_WITH_AES_128_CBC_SHA256,
TLS_DHE_DSS_WITH_AES_128_CBC_SHA,
TLS_DHE_DSS_WITH_3DES_EDE_CBC_SHA,
TLS_RSA_WITH_AES_256_CBC_SHA256,
TLS_RSA_WITH_AES_256_CBC_SHA,
TLS_RSA_WITH_AES_128_CBC_SHA256,
TLS_RSA_WITH_AES_128_CBC_SHA,
TLS_RSA_WITH_3DES_EDE_CBC_SHA,
SSL_CK_DES_192_EDE3_CBC_WITH_MD5
The other option is to remove KB3161608 or KB3161606 from all machines that need to access Finesse or UCCX Web Admin.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-02-2016 05:17 AM
Yup... So it's an exceptionally weak certificate that the industry is trying to mothball support for :-S.
Well, at least we know now :-)
Cheers, and thanks for taking the time to share the outcome.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

