- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Cisco ISE 2.0 Device administration, authentication compound conditions
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco ISE 2.0 Device administration, authentication compound conditions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2016 04:01 AM - edited 03-10-2019 11:28 PM
Hi,
I am working on getting our ISE device administration working and have hit a snag.
I am trying to only let users of certain Active Directory groups authenticate. I have configured Authorization policies with AD-groups and it works fine. It's the Authentication part that I can't seem to get working.
I am not able to choose my AD from the Attribute dictionary when creating authentication conditions. When creating Authorization conditions I am able to choose it and it works fine.
When creating Authentication conditions I am not able to find the AD-groups. When creating the Device Admin policy set, under Authentication, I am able to choose AD, but not drill down to any groups, see image below.
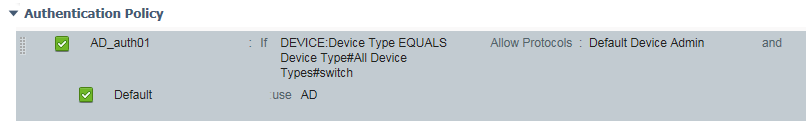
The result is any AD user can authenticate. I only want specific user groups to be allowed to authenticate, not any valid AD account.
Can anyone tell me how I can resolve this issue?
- Labels:
-
AAA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2016 07:47 AM
Cisco ISE retrieves user or machine attributes from Active Directory for use in authorization policy rules. These attributes are mapped to Cisco ISE policies and determine the authorization level for a user or machine. Cisco ISE retrieves user and machine Active Directory attributes after successful authentication and can also retrieve attributes for an authorization that is independent of authentication. Unfortunately these cannot be used in ISE authentication policy.
~ Jatin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2016 12:42 AM
Thank you for your clarification, Jatin! Sounds like I have to come up with a new approach.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide