- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE and GPO Certificates
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE and GPO Certificates
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2018 01:35 AM - edited 02-21-2020 10:51 AM
Hi,
Customers' Site implemented Cisco Identity Services Engine, Release 2.3.2
We are using GPO in order to use Wired-DOT1X,
Each computer enrolls the certificate from Microsoft CA server and uses the PEAP-EAP-TLS to authenticate machine and user.
We have an issue with some workstations (Windows 7) in our domain, some machines uses MSCHAPv2 instead of PEAP-EAP-TLS, although they receive the correct GPO,
and if we run "gpupdate /force"it will work again.. but will change but after a while..
why would the workstations loses it's defenitions?
How can we resolve that?
thanks a lot!
- Labels:
-
Other NAC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2018 12:08 PM - edited 03-25-2018 12:12 PM
Have a look at this post. It is a list of 802.1X related hot-fixes for Windows. One of the hot-fixes is supposed to resolve behavior similar to what you are seeing.
I have seen the same issue happen for machine authentications at boot, when Windows attempts to use PEAP for auth first and then immediately retries with EAP-TLS. I never really put much effort in trying to fix the problem because the actual impact in our case was just cosmetic, that is ISE auth logs contain some failed PEAP auth entries, immediately followed by successful EAP-TLS ones.
Your scenario might be different though - exactly when do you see the failures, and is it only for machine auth or for user auth as well?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2018 12:45 AM
We have installed the related patches.
We see the issue happens when the user perform a login it use MSCHAP instead of the TLS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2018 01:22 AM
I guess it does not happen if you manually configure EAP-TLS on the client, without group policy?
Try moving a test client to a new OU, isolated from other policies. Then configure 802.1X settings in a new, separate policy and see if the issue happens again
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2018 12:26 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2018 08:09 AM
How is the supplicant configured? Can you post screenshots of each windows?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2018 12:30 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2018 01:52 PM - edited 03-26-2018 01:53 PM
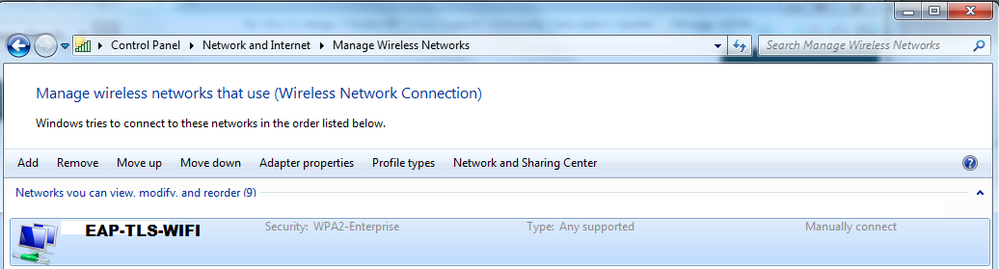
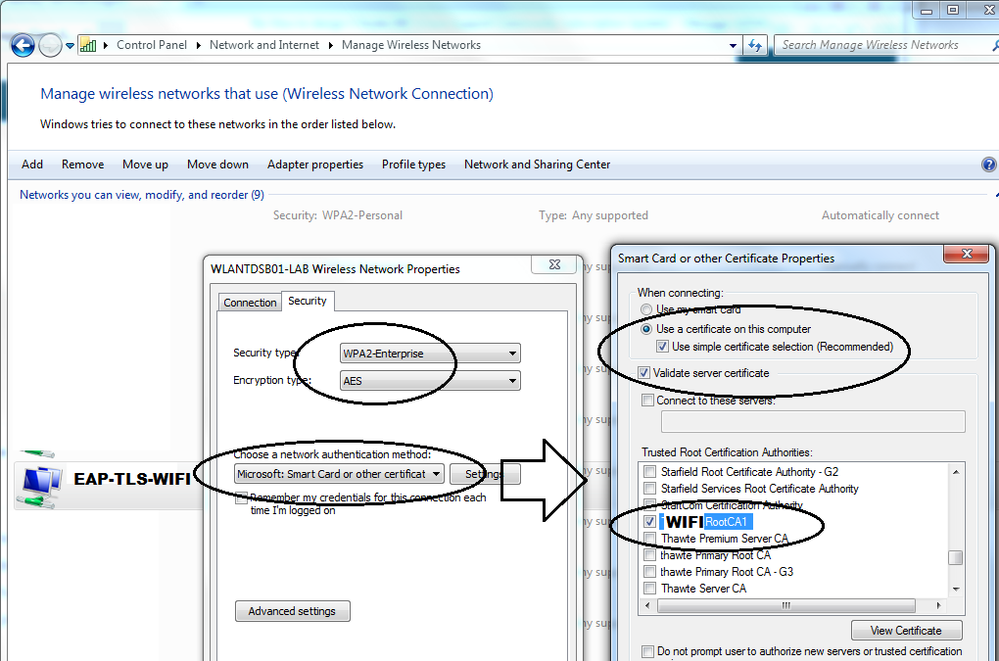
Have you check if the profile is actually deployed into the Win 7 devices at least??. I have tested before and even though I do have the certificate properly installed on the laptop, if I removed the profile then it always tries PEAP. So once I configure back manually that profile (which was originally pushed using GPO) into the laptop, everything works as expected BUT the profile has to indicate something like the following. Important to mention that EAP-TLS is a 2-way authentication using certs so VALIDATE SERVER CERTIFICATE is a must.
PROFILE:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
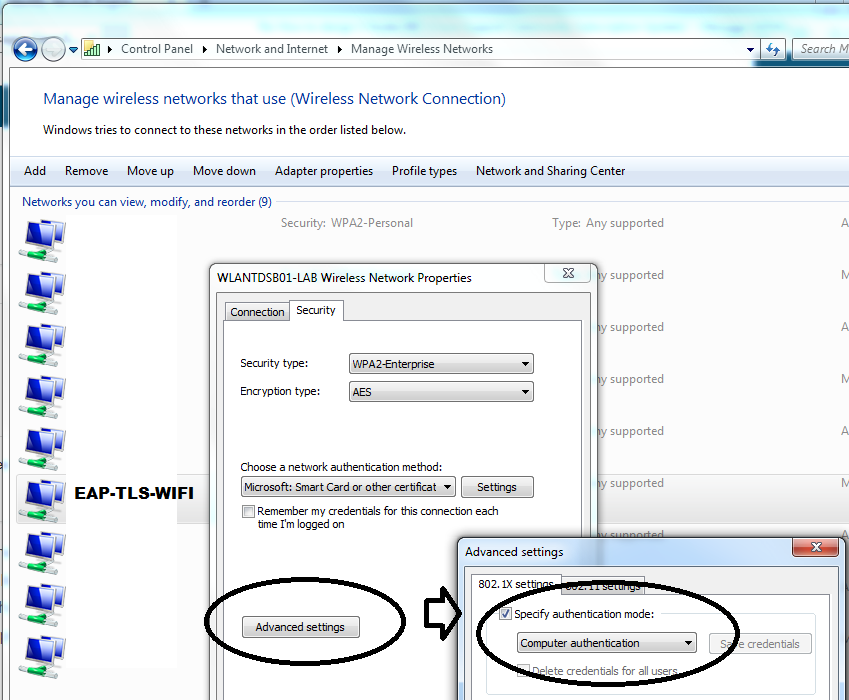
04-08-2018 02:19 AM
There is a Wireless profile configured with GPO, the settings attached on the post above,
thanks,
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: