- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Thanks for the input from
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE Sending Hostname in CWA Redirect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-19-2014 03:33 AM - edited 03-10-2019 09:25 PM
Dear Support Team.
we have setup in which wireless controllers are deployed in Foreign & Anchor Scenario. (Guest WLC or Anchor is deployed in DMZ) , Controllers are running 7.3 and CWA config is done as per standard TAC documents.
When WLC redirects the session to ISE, Redirection URL has ISE hostname and is something like this
https://ise-ip-address:8443/guestportal/gateway........
we have setup Guest Access in such a way, that guest dhcp pool is using the Public DNS, we are not providing our internal DNS to guest dhcp pool, since public DNS does not have an entry for ise-ip-address, DNS resolution Fails and CWA is not happening.
is it possible that ISE can send IP address in place of its hostname, for example
https://10.15.24.20:8443/guestportal/gateway......
Any help will be highly appreciated.
Thanks
Ahad
- Labels:
-
AAA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-19-2014 04:59 AM
Ahad,
I think this will work for you:
Go to Policy > Policy Elements > Results, expand Authorization in the Left Menu. Expand Authorization Profiles. Click on the Authorization profile that you are using. Scroll to Web Redirection (CWA, DRW, MDM, NSP, CPP) and place a check mark in the Static IP/Host name box. Enter the IP address of the ISE.
Scroll to the bottom of the page and click Save.
Please Rate Helpful posts and mark this question as answered if, in fact, this does answer your question. Otherwise, feel free to post follow-up questions.
Charles Moreton
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-19-2014 12:25 PM
Hello Charles
Thanks a lot for your response.
I am running Ver 1.1.4 and authorization profile syntax is a little different. I could not find "Static IP/ Host Name" in Common Tasks. I tried to pull it from Dictionaries, but could not find the same.
for CWA we have 2 rules, please view the flow in sequence.first wireless guest rule is for providing them access and other is for redirection. 2 Authorization Profiles used in these rules are also been shown below.
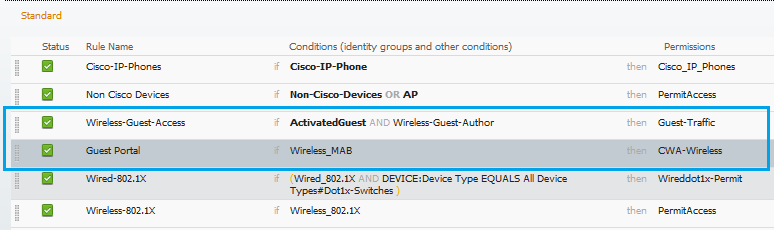
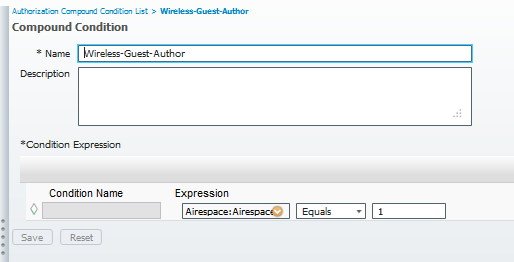
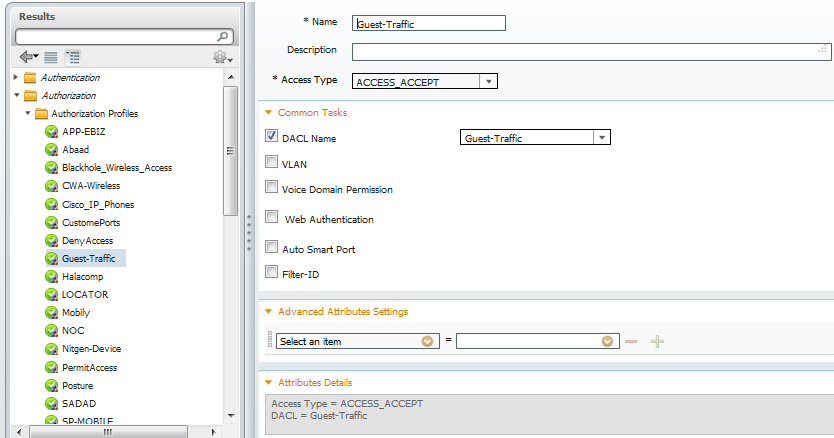
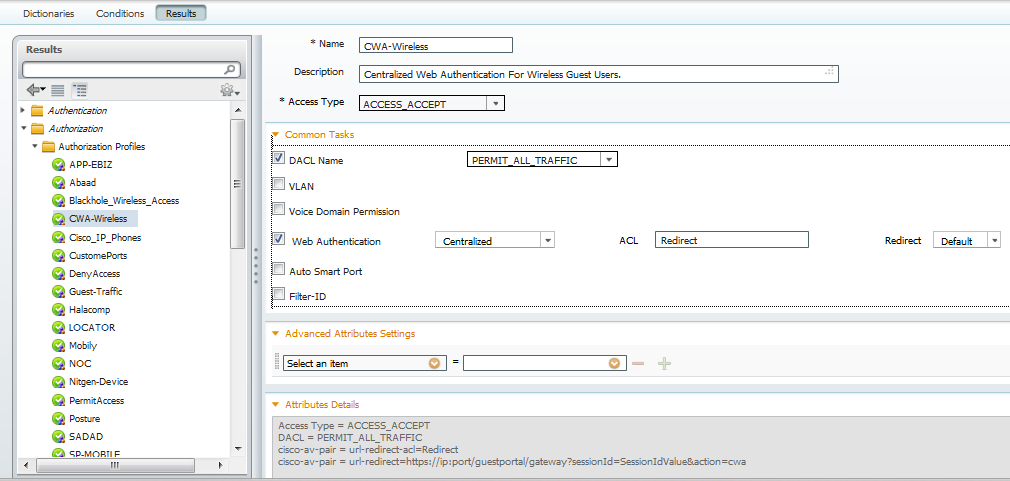
Thanks again for your time to look into the issue.
Ahad
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-19-2014 06:37 PM
Unfortunately what Charles described is only offered as a workaround in ISE 1.2. Is there any reason for you not to upgrade? 1.2 has a ton of other features and bug fixes.
Sent from Cisco Technical Support iPad App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2014 09:59 AM
Dear SAM one of the primary issue for not going to 1.2, is Inline Posture Nodes re-initialization. is there any possible fix in 1.1.4 for the problem that i am encountering. " ISE sending host name in Redirect Message and Guest Users ( using public DNS) can not resolve ISE hostname, as a result CWA is not happening. Thanks Ahad
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2014 11:11 PM
There isn't a workaround for CWA without DNS in1.1.x unfortunately. If going to 1.2 currently isn't an option for you you should consider having guests use a local DNS you manage.
Sent from Cisco Technical Support iPad App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2014 10:13 AM
One workaround that I have gotten to work in the past when using ASA firewalls is to create a static NAT entry and leverage DNS inspection to translate the Private IP address for you. It is important to note that in this example the domain name that the ISE PSN is registered as is on a publicly resolvable domain name which you have control of the DNS entries.
In this example we will have a three legged ASA. Inside, DMZ, and Outside.
The PSN's hostname is psn.example.com.
The PSN's Private IP address is 10.1.1.100
Steps:
Create a Public DNS record for psn.example.com. For best practices you should use an IP address that belongs to you and that is not a part of RFC 1918. This way the public DNS servers do not reject the IP address for some other reason. In this example we will use 1.1.1.1
Enable DNS inspeciton on the ASA.
Create a Static NAT entry for 1.1.1.1 (outside) -> 10.1.1.100 (inside) and enable DNS translation.
Now when the CWA user connects and gets a public DNS server it will query the public server for psn.exmaple.com and the public DNS server will return 1.1.1.1. Now because of the DNS inspection the reply of 1.1.1.1 is replaced with the private IP address of 10.1.1.100.
End result is the DMZ host using a public DNS server to return a private IP address. If you have multiple PSNs you will need to create multiple DNS and NAT.
You are welcome to try and use RFC Bogus RFC 1918 addresses, but the public DNS servers may have rules against doing so which is why i recommend using the public IP addresses that you own. It is important to remember that even though you are creating Inside to Outside NAT entries for your ISE servers because you haven't created any inboundACL's they are not exposed to the Internet just because you created a NAT for them.
Here is a cisco doc on how to do "DNS Doctoring"
I should note that I have tested this using 1.2 with the static hostname, but I have not tested it with 1.1.4, but the underlying pricipals should be the same.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2014 09:35 AM
You don't actually need to use those checkboxes in order to send information back to switches/WLCs, they just provide a nicer way of doing so. Take note of the cisvo-av-pair url-redirect and url-redirect-acl entries, uncheck the web authentication box and then use the Advanced Attribute Settings area to recreate them. Your url-redirect-acl entry will stay the same but you can specify the URL to be the IP/port you are looking for without ISE doing the on-demand replacement. This should give you what you wan't without needing to upgrade to 1.2.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2014 10:58 AM
Dear Charles / SAM / Justin / Thejman85 Many Thanks for your active contribution and inputs, it seems that upgrade to 1.2 is inevitable and should be carried out, as 1.1.4 has many other issues.... if upgrade to 1.2 resolves my issue, i will further update this post. Thanks Again Ahad...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-11-2014 01:29 PM
duplicate entry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-11-2014 01:30 PM
Thanks for the input from this forum, and Like others, believe I will have to upgrade, as I can get the IP address URL redirect to work, by not checking Web Authentication, and manually entering the Attribute Details, when I do this I get the "86017: Session cache entry missing" when trying to login after this. and this is very close to the bug in 1.2.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: