- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE WIN10 Slow Logon
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2019 03:38 AM
Hi
With the increase of Windows 10 installations, there is an intermittent issue of slow logon which occurs after 5 to ten minutes.
This slow logon occurs after sign on, and the workaround the users have is to either use WIFI (not authenticated via ISE) or to pull out/ plug in the network cable. Then the client can be working fine for a month or more before the issue is seen again on this client (if ever). When there is an issue, we do not see any authentication log in ISE. The issue does not occur everytime for a user but mostly when the user has been out of office for a day or so.
This is a global problem and occurs on different types of networks with old and new, large and small networks, desktops and laptops.
The sites affected also have local and remote domain controllers.
The client version is Windows 10 Enterprise v1803. Running 802.1x (eap-tls) with machine certificates (no AD lookup). We are using windows own dot1x supplicant (same settings as our WIN7 that works)
We are seeing this on diferent switch platforms (2960, 3750, 3650 and 9300) with diferent IOS SW.
ISE version is : 2.1 patch 8 (running on 3495 appliances - 2 x PAN, 2x MON, 2 x PSN)
Anyone having the same problems and mayby solved this ?
Regards Henrik
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2019 08:14 PM
Not sure if ACL is used, but if so, suggest allowing IP fragments to AD servers. See: https://community.cisco.com/t5/security-documents/advanced-ise-tips-to-make-your-deployment-easier/ta-p/3850189#toc-hId-1913177494
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2019 08:21 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2019 08:14 PM
Not sure if ACL is used, but if so, suggest allowing IP fragments to AD servers. See: https://community.cisco.com/t5/security-documents/advanced-ise-tips-to-make-your-deployment-easier/ta-p/3850189#toc-hId-1913177494
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2021 09:16 AM
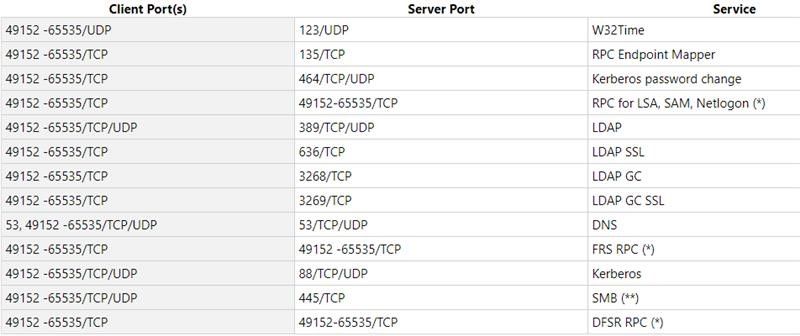
During our deployment we found out that the slow logon/bootup of windows machine was happening due to a Pre Authentication ACL that did not had all the necessary TCP/UDP Ports that were allowed for full communication between Endpoint and Domain Controllers.
So please make sure that the dACL which gets applied soon after the successful machine authentication is completed should have all the below ACL list.
Also remember If you have any additional ACL's applied for your Pre Authentication/Quarantine VLAN on your switch this below ACL should be applied there as well.
!
remark DHCP
permit udp any eq bootpc any eq bootps
remark DNS
permit udp any any eq domain
remark Ping
permit icmp any any
remark Allow HTTPS to ISE PSN Nodes
permit tcp any host <ISE_Node> eq 443
permit tcp any host <ISE_Node> eq 8443
remark Allowing Ports for DNS/LDAP/NTP
permit tcp any any eq 88
permit udp any any eq 88
permit udp any any eq ntp
permit tcp any any eq 135
permit udp any any eq netbios-ns
permit tcp any any eq 139
permit tcp any any eq 389
permit udp any any eq 389
permit tcp any any eq 445
permit tcp any any eq 636
permit udp any any eq 636
Permit tcp any any eq 464
Permit udp any any eq 464
Permit tcp any any range 49152 65535
Permit tcp any any range 3268 3269
remark Drop all the rest
deny ip any any
!
Thank you,
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: