- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Some ports are AUTHORIZED and other are UNAUTHORIZED on the same
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Some ports are AUTHORIZED and other are UNAUTHORIZED on the same switch.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2013 07:11 AM - edited 03-10-2019 08:33 PM
Hi everybody.
I have a problem with my dot1x for wired computers. ACS checks wired access via an Active Directory.
C4507#sh dot1x all summary
Interface PAE Client Status
--------------------------------------------------------
Fa3/23 AUTH d067.e51e.921c AUTHORIZED
Fa3/46 AUTH 7845.c43a.22ee AUTHORIZED
Fa5/7 AUTH 7845.c406.6c5f AUTHORIZED
Fa7/24 AUTH d4be.d9ea.b7c6 UNAUTHORIZED
. UNAUTHORIZED
. UNAUTHORIZED
. UNAUTHORIZED
. UNAUTHORIZED
Some computers works fine but other not and that the reason i need your help. Why some computers can not be authorized ?
%DOT1X-5-FAIL: Authentication failed for client (d4be.d9ea.b7c6) on Interface Fa7/24 AuditSessionID 0A4B4F4400000EBE22077FF8
%AUTHMGR-7-RESULT: Authentication result 'no-response' from 'dot1x' for client (d4be.d9ea.b7c6) on Interface Fa7/24 AuditSessionID 0A4B4F4400000EBE22077FF8
%AUTHMGR-7-FAILOVER: Failing over from 'dot1x' for client (d4be.d9ea.b7c6) on Interface Fa7/24 AuditSessionID 0A4B4F4400000EBE22077FF8
%AUTHMGR-7-NOMOREMETHODS: Exhausted all authentication methods for client (d4be.d9ea.b7c6) on Interface Fa7/24 AuditSessionID 0A4B4F4400000EBE22077FF8
%AUTHMGR-5-FAIL: Authorization failed or unapplied for client (d4be.d9ea.b7c6) on Interface Fa7/24 AuditSessionID 0A4B4F4400000EBE22077FF8
%AUTHMGR-5-START: Starting 'dot1x' for client (d4be.d9ea.b7c6) on Interface Fa7/24 AuditSessionID 0A4B4F4400000EBE22077FF8
That my authorized port configuration:
interface FastEthernet3/46
description 3/46
switchport access vlan 21
switchport mode access
switchport voice vlan 910
speed 100
duplex full
authentication event server dead action authorize vlan 95
authentication event server alive action reinitialize
authentication host-mode multi-host
authentication port-control auto
authentication periodic
authentication timer reauthenticate 64800
dot1x pae authenticator
dot1x max-start 5
macro description dot1x
no cdp enable
spanning-tree portfast
spanning-tree bpduguard enable
service-policy input CC_INGDIRECT
end
That my unauthorized port configuration:
interface FastEthernet7/24
description ""
switchport access vlan 21
switchport mode access
switchport voice vlan 213
speed 100
duplex full
authentication event server dead action authorize vlan 95
authentication event server alive action reinitialize
authentication host-mode multi-host
authentication port-control auto
authentication periodic
authentication timer reauthenticate 64800
dot1x pae authenticator
dot1x max-req 3
dot1x max-start 5
macro description dot1x
no cdp enable
spanning-tree portfast
spanning-tree bpduguard enable
service-policy input CC_INGDIRECT
end
On FastEthernet3/46, port is authorized and why on FastEthernet7/24 it's unauthorized ?
Can you help me please
- Labels:
-
AAA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2013 08:44 PM
Ports in Authorized and Unauthorized States
The switch port state determines whether or not the client is granted access to the network. The port starts in the unauthorized state. While in this state, the port disallows all ingress and egress traffic except for 802.1X packets. When a client is successfully authenticated, the port transitions to the authorized state, allowing all traffic for the client to flow normally.
If a client that does not support 802.1X is connected to an unauthorized 802.1X port, the switch requests the client's identity. In this situation, the client does not respond to the request, the port remains in the unauthorized state, and the client is not granted access to the network.
In contrast, when an 802.1X-enabled client connects to a port that is not running 802.1X, the client initiates the authentication process by sending the EAPOL-start frame. When no response is received, the client sends the request for a fixed number of times. Because no response is received, the client begins sending frames as if the port is in the authorized state.
You control the port authorization state by using the dot1x port-control interface configuration command and these keywords:
•force-authorized—disables 802.1X and causes the port to transition to the authorized state without any authentication exchange required. The port transmits and receives normal traffic without 802.1X-based authentication of the client. This is the default setting.
•force-unauthorized—causes the port to remain in the unauthorized state, ignoring all attempts by the client to authenticate. The switch cannot provide authentication services to the client through the interface.
•auto—enables 802.1X authentication and causes the port to begin in the unauthorized state, allowing only EAPOL frames to be sent and received through the port. The authentication process begins when the link state of the port transitions from down to up, or when an EAPOL-start frame is received. The switch requests the identity of the client and begins relaying authentication messages between the client and the authentication server. Each client attempting to access the network is uniquely identified by the switch by using the client's MAC address.
If the client is successfully authenticated (receives an Accept frame from the authentication server), the port state changes to authorized, and all frames from the authenticated client are allowed through the port. If the authentication fails, the port remains in the unauthorized state, but authentication can be retried. If the authentication server cannot be reached, the switch can retransmit the request. If no response is received from the server after the specified number of attempts, authentication fails, and network access is not granted.
When a client logs off, it sends an EAPOL-logoff message, causing the switch port to transition to the unauthorized state.
If the link state of a port transitions from up to down, or if an EAPOL-logoff frame is received, the port returns to the unauthorized state.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2013 01:33 AM
Hi. Thanks for your response.
I made a test.
I put an authorized computer of this switch on an unauthorized port of this same switch. 802.1X blocked it. So it's not a network adapter problem.
Here the debug dot1x event:
Starting 'dot1x' for client (d4be.d9ea.b7c6) on Interface Fa7/24 AuditSessionID 0A4B4F4400000EC9260656C4
dot1x-ev(Fa7/24): Sending EAPOL packet to group PAE address
dot1x-ev(Fa7/24): Role determination not required
dot1x-ev(Fa7/24): Sending out EAPOL packet
dot1x-ev(Fa7/24): Sending EAPOL packet to group PAE address
dot1x-ev(Fa7/24): Role determination not required
dot1x-ev(Fa7/24): Sending out EAPOL packet
dot1x-ev(Fa7/24): Sending EAPOL packet to group PAE address
dot1x-ev(Fa7/24): Role determination not required
dot1x-ev(Fa7/24): Sending out EAPOL packet
dot1x-ev(Fa7/24): Received an EAP Timeout
%DOT1X-5-FAIL: Authentication failed for client (d4be.d9ea.b7c6) on Interface Fa7/24 AuditSessionID 0A4B4F4400000EC9260656C4
dot1x-ev(Fa7/24): Sending event (2) to Auth Mgr for d4be.d9ea.b7c6
%AUTHMGR-7-RESULT: Authentication result 'no-response' from 'dot1x' for client (d4be.d9ea.b7c6) on Interface Fa7/24 AuditSessionID 0A4B4F4400000EC9260656C4
dot1x-ev(Fa7/24): Received Authz fail for the client 0x3A000450 (d4be.d9ea.b7c6)
dot1x-ev(Fa7/24): Deleting client 0x3A000450 (d4be.d9ea.b7c6)
%AUTHMGR-7-FAILOVER: Failing over from 'dot1x' for client (d4be.d9ea.b7c6) on Interface Fa7/24 AuditSessionID 0A4B4F4400000EC9260656C4
%AUTHMGR-7-NOMOREMETHODS: Exhausted all authentication methods for client (d4be.d9ea.b7c6) on Interface Fa7/24 AuditSessionID 0A4B4F4400000EC9260656C4
%AUTHMGR-5-FAIL: Authorization failed or unapplied for client (d4be.d9ea.b7c6) on Interface Fa7/24 AuditSessionID 0A4B4F4400000EC9260656C4
dot1x-ev:Delete auth client (0x3A000450) message
dot1x-ev:Auth client ctx destroyed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2013 08:07 AM
No one can help me ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2013 01:02 AM
Hi,
I'm still investigate but i do not find a solution.
- on the same switch some ports are authorized and others not,
- an authorized computer become unauthorized on the same switch (authentication failed) and conversely.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2013 05:53 AM
Hi.
I put Wiresharck on a laptop (HP) to test the port.
Here the result:
Cisco - Request, Identity [RFC3748]
HP - Response, Identity [RFC3748]
Cisco - Failure - Code: Failure (4)
Why ?
The computeur exist in AD and is in the right group.
On ACS, computeur is allowed
01:14:08.668 PM
Jun 26, 13 01:14:08.668 PM
RADIUS Status: Pass
NAD Failure : No
Authentication Results
User-Name: host/XXXXXXXXXXXXXX
Class: CACS:idf1pacs01/144770248/776136
EAP-Key-Name: 19:51:ca:e9:3b:13:48:d9:1c:42:12:00:8d:05:4d:0b:1e:b9:c4:56:4d:1d:ae:09:ee:82:e5:7d:53:78:4d:81:30:51:ca:e9:20:f5:62:3d:ec:31:2e:21:d6:72:0c:b7:ce:a8:41:3e:dc:39:6a:90:89:85:53:87:9f:3b:00:53:e5
N/A host/XXXXXXXXXXXXXX
ACS Username: host/XXXXXXXXXXXXXX
Radius Username: host/XXXXXXXXXXXXXX D4-BE-D9-EA-B7-C6 A.B.C.D
Network Device: 4507
NAS IP Address: A.B.C.D
NAS Identifier:
NAS Port ID: FastEthernet7/24
NAS Port: 50724
NAS Port Type: Ethernet
Network Device Groups
Device Type:All Device Types
Location:All Locations: XX
SNMP Query to NAD: Click Here FastEthernet7/24 Default Network Access
Access Service: Default Network Access
Identity Store: AD1
Authorization Profiles: Permit Access
Exception Authorization Profiles:
Authorization Policy Matched Rule: 801.x Computers
Authorization Exception Matched Rule: MSCHAPV2
but, on the switch unauthorized
4507#sh dot1x all summary
Interface PAE Client Status
--------------------------------------------------------
Fa7/24 AUTH none UNAUTHORIZED
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2013 06:37 PM
Oliver,
Can you run the debug radius authentication command (reauthenticate the user) and share the results. Also in ACS is the the client hitting the same authorization rule?
What version of code is this switch running?
Is this a phone if so, your voice vlans are different on both ports? Can you make sure that the vlan is active?
Thanks,
Tarik Admani
*Please rate helpful posts*
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2013 05:34 AM
Hi.
Thanks for your answer.
Can you run the debug radius authentication command (reauthenticate the user) and share the results. Also in ACS is the the client hitting the same authorization rule?
I attached a file with logs, i hope it will be helpful. In ACS, we have same rule for workers, and for someone, Radius authorized and other not
What version of code is this switch running?
switch#sh version
Cisco IOS Software, Catalyst 4500 L3 Switch Software (cat4500-IPBASEK9-M), Version 12.2(54)SG1, RELEASE SOFTWARE (fc1)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2011 by Cisco Systems, Inc.
Compiled Thu 27-Jan-11 11:46 by prod_rel_team
Image text-base: 0x10000000, data-base: 0x120B1F6C
ROM: 12.2(20r)EW1
Dagobah Revision 95, Swamp Revision 3
Is this a phone if so, your voice vlans are different on both ports? Can you make sure that the vlan is active?
Yes, VLAN is active. I have same problem with a single-host
Thanks,
Ce message a été modifié par: Olivier Chambelant
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2013 12:38 AM
I'm still working on it. Anyone have an idea ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2013 04:04 AM
Hi.
i'll check 802.1x status.
#sh dot1x all summ
Interface PAE Client Status
--------------------------------------------------------
Fa3/23 AUTH d067.e51e.921c AUTHORIZED
Fa3/43 AUTH none UNAUTHORIZED
So i decide to make a test. On this switch, i swap computers plug in port 3/43 to 3/23.
On 3/23 802.1x still work and not 3/43:
#sh dot1x all summ
Interface PAE Client Status
--------------------------------------------------------
Fa3/23 AUTH d067.e51e.8e8b AUTHORIZED
Fa3/43 AUTH none UNAUTHORIZED
So it's not a computer problem. Do you think if i upgrade switch version it will solve the problem, or have you a better idea ?
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2013 04:49 AM
Here, wireshark screenshots. i try with one computer.
Architecture: CISCO <-> Computer.
First picture is about 802.1x failure with single-host and multi-host
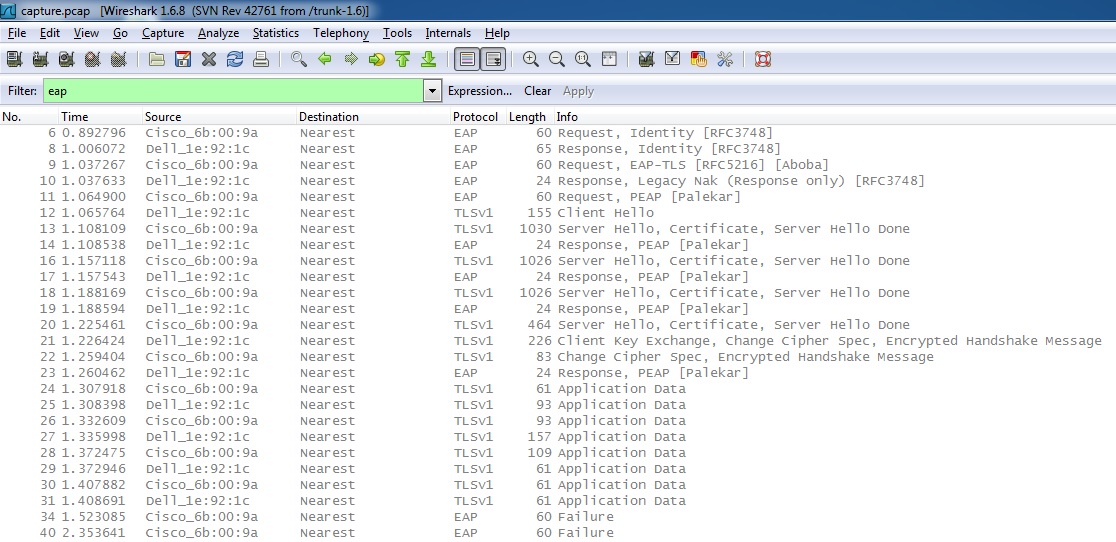
Second one is about successful authz with multi-domain and multi-auth.
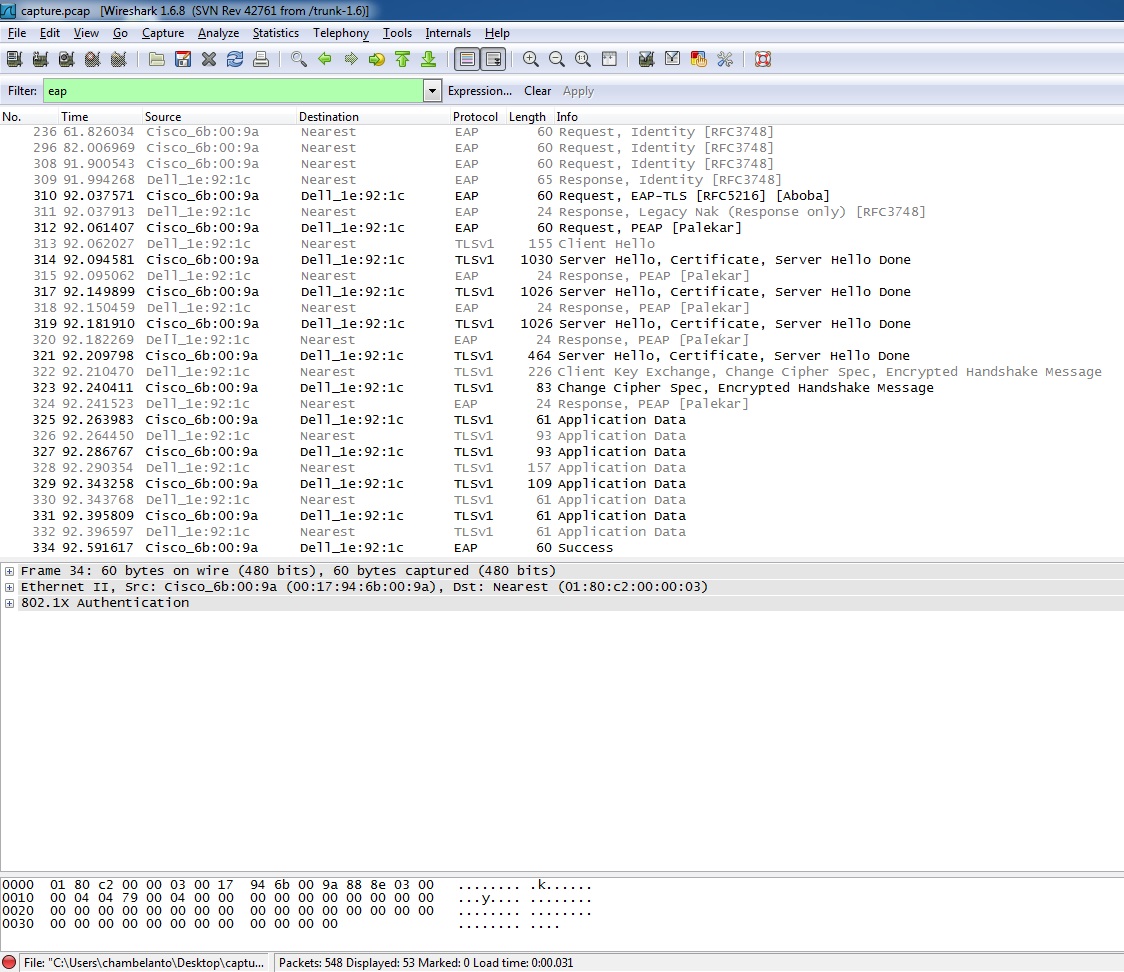
In the second case, switch communicate with computer directly but not in the first case.
Then if i plug a phone (CISCO <-> Phone <-> Computer)
Multi-auth: PC OK - Phone NOK
Mutli-domain: PC OK - Phone NOK
Single-host: PC NOK - Phone NOK
Multi-host: PC NOK - Phone NOK
I'm lost. Can someone help me ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2013 09:39 PM
Hello , if you want to authenticate two endpoints in the same switchport (one in the data vlan and the other one in the voice vlan) you must use multi-domain. This is Cisco recommendation when using IP Phones.
If you want to authenticate three or more endpoints in the same switchport you must use multi-auth.
Single-host it's only useful if you have only one endpoint connected to the switchport. This is not your case and that's why your tests fails when using single-host.
Multi-host is not recommended at all because it's a security hole.
Please rate if this helps
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide