- Cisco Community
- Technology and Support
- Security
- Network Access Control
- User logged in via AD cannot see Network Devices
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2018 06:24 AM - edited 02-21-2020 10:45 AM
I have setup login access on ISE 2.3 to use AD
Under Authentication - Password Based > Identity Source AD
Under Authorisation / Policy I have created a new Rule saying IT Admins - mapped to AD IT Admin group gets Super admin Menu Access
However when logged in I cannot see any network devices? It shows Total 6 but they are not visible?
If I log in as local Admin locally they are there.
Any ideas?
Solved! Go to Solution.
- Labels:
-
Other NAC
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2018 07:26 AM - edited 02-21-2018 07:29 AM
How did you create that ADMIN GROUP = IT-ISE-ADMINS?. Did you duplicate an existing default group? If it so, there is an identified bug when doing that.
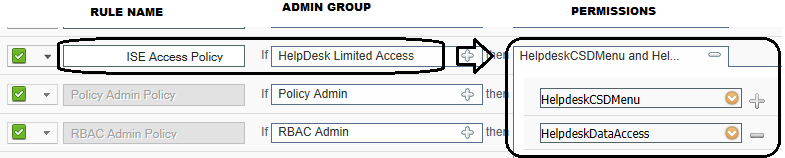
However, let's assume that your issue has nothing to do with that bug. Then, looks like you are missing the DATA ACCESS option in the RBAC Policy. See example next.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2018 03:37 PM
Hi
Can you share screenshots of your config?
Never add any issues like that on 2.3 or any other versions. This works well.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2018 01:41 PM
Please check that you AD IT Admin Group was NOT a duplicated copy of the default SUPER ADMIN Group on which you checked the EXTERNAL box to include the AD Group = IT ADMINS because there is a bug when creating those copies from default groups. Create it from scratch.
If the previous was created from scratch then you probably have a misconfiguration on the RBAC Policies in the permissions part. I mean, you created a rule name pointing to the customized ADMIN Group BUT the menu and data access probably do not include all the information/options you need.
Let's recall local admin user has super admin privileges and that's why it worked fine for you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2018 02:07 PM
Hi braham, Thanks for your reply however I am not exactly sure what you mean about a duplicated copy of the default Super Admin group?
within RBAC policies I created a new line and added the following
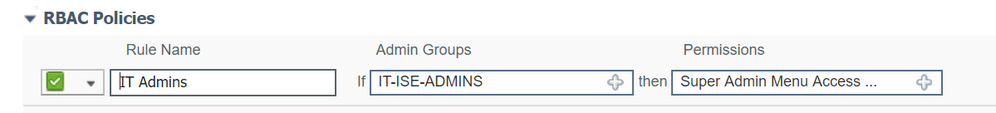
However when logging in with an AD user in this group you cannot see any network devices, and also all the dashboards show zero Total Endpoints and zero Active endpoints.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2018 05:12 PM
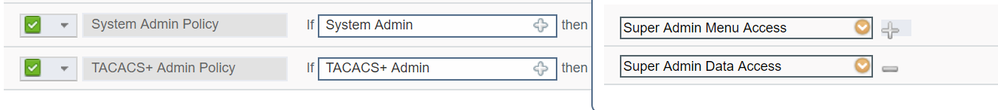
You should have Super Admin Menu and Super Admin Data under permissions.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2018 07:26 AM - edited 02-21-2018 07:29 AM
How did you create that ADMIN GROUP = IT-ISE-ADMINS?. Did you duplicate an existing default group? If it so, there is an identified bug when doing that.
However, let's assume that your issue has nothing to do with that bug. Then, looks like you are missing the DATA ACCESS option in the RBAC Policy. See example next.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2018 07:50 AM
Perfect, this is the solution, checking the built in Super Admin User - it's all there to see!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2022 08:23 AM
Hi,
Even I am facing the same issue in my ISE box 2.4 release.
Not able to see the network devices and network device type.
In the policy i have given both the super user menu and data access for the admin group which i have created (external groups)
Please help me here
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2022 08:56 AM
share screenshots about what you did
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2022 04:28 PM
There are a number of RBAC related bugs fixed in various patches for ISE 2.4. If you have not already installed the latest (patch 14), I would suggest trying that first. If the issue still exists, you will likely need to open a TAC case.
You should also note that ISE 2.4 reaches end of support in December 2022. You should strongly consider upgrading to a newer version that will continue to be supported.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: