A customer of ours was running Cisco ASA firewalls (HA) for more than 10 years which was mainly handling their corporate segment traffic. Over the time these boxes faced end of life and end of support, what made the customer go for the next generation firewalls as replacement option. As a replacement process they procured Cisco Firepower Threat Defense boxes.
As we started planning for the migration we found few challenges listed below -
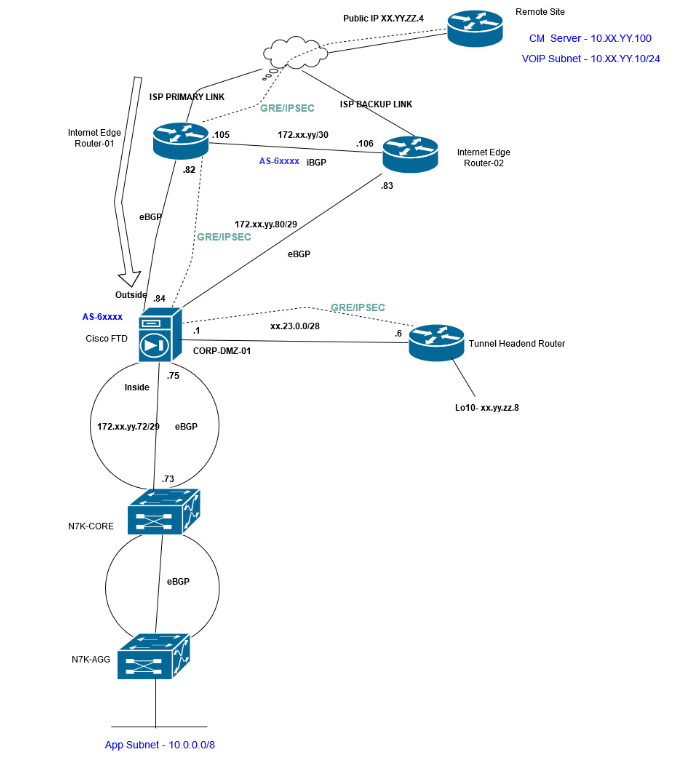
- Routing from static, EIRGP to BGP.
- GRE/IPSEC traffic that would traverse the FTD.
- Time based ACL – Not resolved as the current version 6.4.0.9 running on this boxes don’t support this feature. Waiting for a stable version of 6.6 or above.
- S2S VPN etc.
Used Firepower migration tool to migrate the configuration from ASA to FTD which is quite helpful to build up the migration process with all the unsupported configurations listed in the pre and post migration reports.
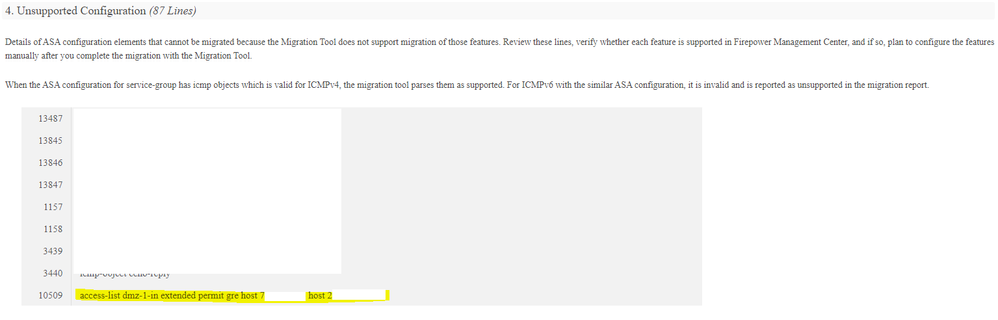
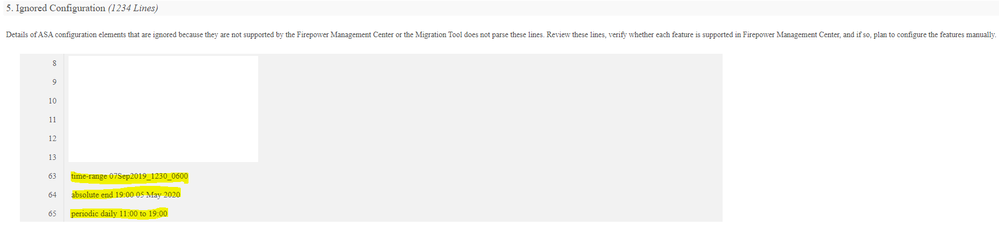
We had to face failure during the initial migration window and reschedule the migration. GRE/IPSec traffic found out the main culprit for failing the tunnels pairing. We took support from Cisco TAC and the engineers were quite supportive and further we did our homework too by reproducing the issue at our office lab. The GRE/IPSec traffic are subjected to get inspected by the Snort in FTD and the verdict for these types of traffic is dropped.

In our rescheduled migration window we exactly knew what needs to be done but still faced the same issue with the GRE/IPsec traffic getting dropped by Snort. Eventually, after 30mins we were able to fix it by fine tuning the pre-filter policy and allowing the GRE and ESP with action as fastpath and “clear conn” was a great help to bounce the tunnels and traffic to take the correct rules.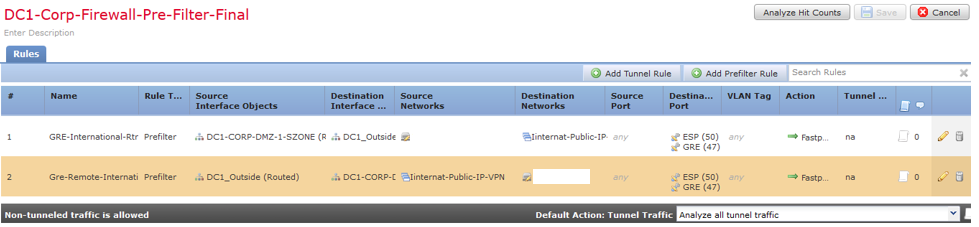
The allocated migration window time was 4 hours but we managed to finish the activity within 3 hours. After that came the big challenge with all the application owners going to check their applications and we just put our finger crossed as we didn’t want a roll back. Almost all applications worked fine, but few issues were reported like remote branches VIOP calls weren’t going through and also swift application reported an issue. All these issues were related to routing and was taking care. Some other issues were reported related to RAVPN anyconnect with ISE posturing and windows login slowness which were related to NAT and access rules on FTD and were also taken care. Constantly, worked for almost 26 long hours to provide a better experience to the client for their next business working day.
Now with the successful migration and handed over the boxes to their operation team, we provided a KT session where we pointed few things out.
- This NGFW comes loaded with advanced features like Security intelligence, URL blacklist and Whitelist, DNS blacklist and Whitelist, Intrusion prevention system and some more features.
- These features are connected to Talos and snort cloud to provide proactive resolution for network security related threats.
- So they need understand the power and capability of it and use it in proper and efficient way.
“With great power comes great responsibility.”
