- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: 2911 Port forward, router is not default GW
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
2911 Port forward, router is not default GW
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2019 12:14 AM
Hi,
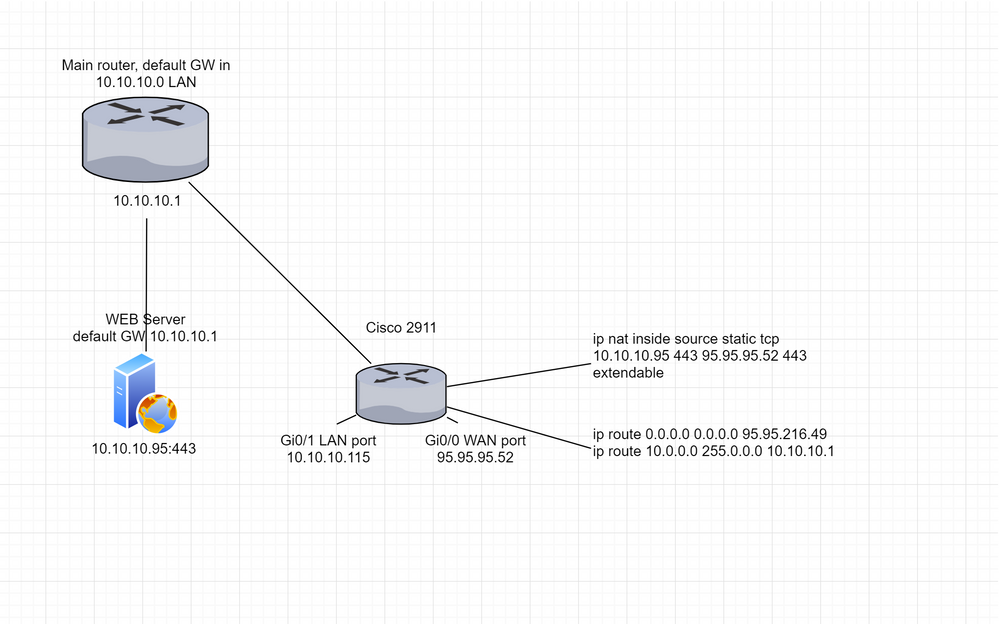
I have an 2911 (WAN_INT-95.95.95.52, LAN-INT10.10.10.115) is NOT default GW in LAN network. I need port forward from LAN to WAN. It works, when i set up service GW cisco (10.10.10.115), maybe i need PBR or Rute-map? Guys, plese help. Config below:
version 15.4 no service pad service timestamps debug datetime msec service timestamps log datetime msec service password-encryption ! hostname *** ! boot-start-marker boot-end-marker ! ! no logging console ! aaa new-model ! ! ! ! ! ! ! aaa session-id common ! ! ! ! ! ! no ip source-route ! ! ! ! ! ! ! ! no ip bootp server no ip domain lookup ip domain name **** ip name-server 10.10.10.97 ip cef no ipv6 cef multilink bundle-name authenticated ! ! cts logging verbose ! ! license udi pid CISCO2911R/K9 ! ! archive log config logging enable hidekeys ! redundancy ! ! ip ssh source-interface GigabitEthernet0/1 ! ! ! ! interface Embedded-Service-Engine0/0 no ip address shutdown ! interface GigabitEthernet0/0 description REALIP ip address 95.95.95.52 255.255.255.248 ip access-group FIREWALL in no ip redirects no ip proxy-arp ip nat outside ip nat enable ip virtual-reassembly in ip verify unicast reverse-path duplex auto speed auto no cdp enable ! interface GigabitEthernet0/1 description LAN ip address 10.10.10.115 255.255.255.128 ip nat inside ip nat enable ip virtual-reassembly in duplex auto speed auto ! interface GigabitEthernet0/2 description NONE no ip address ip nat enable ip virtual-reassembly in shutdown duplex auto speed auto ! ip forward-protocol nd ! ip policy-list TEST permit ! no ip http server no ip http secure-server ip flow-export version 9 ! ip nat pool NAT 95.95.95.52 95.95.95.52 netmask 255.255.255.255 ip nat inside source list ACL_NAT interface GigabitEthernet0/0 overload ip nat inside source static tcp 10.10.10.95 443 95.95.95.52 443 extendable ip route 0.0.0.0 0.0.0.0 95.95.95.49 ip route 10.10.10.0 255.255.255.128 10.10.10.1 ! ip access-list standard ACL_NAT permit any deny any ! ip access-list extended FIREWALL permit tcp any any eq 443 deny tcp any any ! ! route-map TEST permit 10 set ip next-hop 10.10.10.1 ! ! ! ! ! control-plane ! ! ! line con 0 line aux 0 line 2 no activation-character no exec transport preferred none transport output pad telnet rlogin lapb-ta mop udptn v120 ssh stopbits 1 line vty 0 4 exec-timeout 60 0 transport input ssh ! scheduler allocate 20000 1000 ! end
- Labels:
-
Other Routers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2019 03:05 AM
Hello
@Roman8305 wrote:
Hi,
I have an 2911 (WAN_INT-95.95.95.52, LAN-INT10.10.10.115) is NOT default GW in LAN network. I need port forward from LAN to WAN.
interface GigabitEthernet0/0 description REALIP ip address 95.95.95.52 255.255.255.248 ip access-group FIREWALL in no ip redirects no ip proxy-arp ip nat outside ip nat enable ip virtual-reassembly in ip verify unicast reverse-path duplex auto speed auto no cdp enable ! interface GigabitEthernet0/1 description LAN ip address 10.10.10.115 255.255.255.128 ip nat inside ip nat enable ip virtual-reassembly in duplex auto speed auto ! ! ip policy-list TEST permit ! ip route 0.0.0.0 0.0.0.0 95.95.95.49 ip route 10.10.10.0 255.255.255.128 10.10.10.1 ! ip access-list standard ACL_NAT permit any deny any ! ip access-list extended FIREWALL permit tcp any any eq 443 deny tcp any any ! ! route-map TEST permit 10 set ip next-hop 10.10.10.1
Not so sure i understand, Currently you have default route pointing to your wan interface, and I see you have a partial PBR statement to policy route to a host 10.10.10.1 which is on the same lan subnet of you lan users.
Are you wanting all lan users to be routed to host 10.10.1 by default?
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2019 04:33 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2019 06:19 AM
Hello
@Roman8305 wrote:
No, curent PBR is for testing and i think it's not working. i just need access from WAN_IP 95.95.95.52 to LAN_IP 10.10.10.95 443 port.
It seems a simple static pat static would help here but then i dont understand you last comments
@Roman8305 wrote:
. It works only when i'm set GW cisco LAN interface adress for service hosted LAN network. Service 10.10.10.95 should have GW 10.10.10.1 (main router for LAN 10.10.10.0), but in this case port forwarding is not working.
Is there something that isnt being shown here, can you post a topology diagram?
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2019 01:31 AM
Yes, simple static pat. It's not working when web server default GW is 10.10.10.1 but i need it. Port forwarfing works only when web server default GW 10.10.10.115.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2019 01:49 AM - edited 08-07-2019 01:59 AM
Hello
Thank you for sharing the additional information, it has made it much clearer on your topology and issue
This other router looks like its bridging or it needs to be between the main router and the web server,can you confirm this or maybe share the running config or that router also
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2019 02:43 AM
2911 should be between main router and web server. 2911 just have global IP connection. I already solved this problem, only with a different router, not with cisco. Using routing and security policies. With cisco, I suppose i need to use PBR, but I did not understand how
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2019 03:13 AM
Hello
The main router looks like it has two interfaces on the same subnet 10.10.10.0/25 ( one connected to the 2911 and the other to the web server) now for that to work you need some bridging involved, if this isnt the case how is the web server which is on the same subnet connecting?
Can you share the config of the main router?
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2019 08:51 AM
The main router has one LAN interface. 2911 and the web server are connected through the switch like all hosts on the 10.10.10.0 network. The main router is Fortinet and i'm can’t make any changes to its configuration :( It is necessary to manage only 2911.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2019 07:37 PM
Hello
It still isnt clear
@Roman8305 wrote:
The main router has one LAN interface. 2911 and the web server are connected through the switch like all hosts on the 10.10.10.0 network.
So physically the main router, the web server and 2911 lan interface are interconnected via a switch?
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2019 12:09 AM
Yes. Does it affect something?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2019 05:00 AM - edited 08-08-2019 05:25 AM
Hello
Now i understand, it was your topology diagram confusing me.
Can you do the following:
2911
conf t
int gig0/0
no ip access-group FIREWALL in
no ip verify unicast reverse-path
no ip nat enable
int gig0/1
no ip nat enable
no ip redirects
exit
no ip policy-list TEST permit
no ip route 10.10.10.0 255.255.255.128 10.10.10.1
no ip access-list standard ACL_NAT
no route-map TEST
access-list 10 deny 10.10.10.95
access-list 10 permit 10.10.10.0 0.0.0.127
ip nat inside source list 10 interface gig0/1 overload
ip nat inside source static tcp 10.10.10.95 443 95.95.95.52 443 extendable
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2019 05:35 AM
Still not working. However, translations are present
Pro Inside global Inside local Outside local Outside global
tcp 95.95.95.52:443 10.10.10.95:443 77.123.139.187:12412 77.123.139.187:12412
But they were present in last my config too
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: