- Cisco Community
- Technology and Support
- Networking
- Routing
- Adding SSL cert chain for duckdns.org dynamic DNS updates to Cisco IOS trusted cert store
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Adding SSL cert chain for duckdns.org dynamic DNS updates to Cisco IOS trusted cert store
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2017 09:20 PM - edited 03-05-2019 09:30 AM
I am using a free dynamic DNS (DDNS) updating service called Duck DNS (duckdns.org). The URL I'm using to trigger DDNS updates from the router is:
https://www.duckdns.org/update?domains=<h>&token=<REMOVED>&ip=<a>&verbose=true
AFAIK, Cisco IOS replaces <h> with the DDNS hostname to update and <a> with the current IP address.
I enabled dynamic DNS update debugging, and it looks like the router is attempting to trigger the update, but when I log into my account on duckdns.org, the IP is not being updated.
I believe there's an issue with Cisco IOS not trusting the SSL certificate at https://www.duckdns.org.
Can someone please help me walk through how I can add the entire SSL certificate chain to the Cisco router so that it will trigger DDNS updates properly? I am using a Cisco 1921 ISR router running
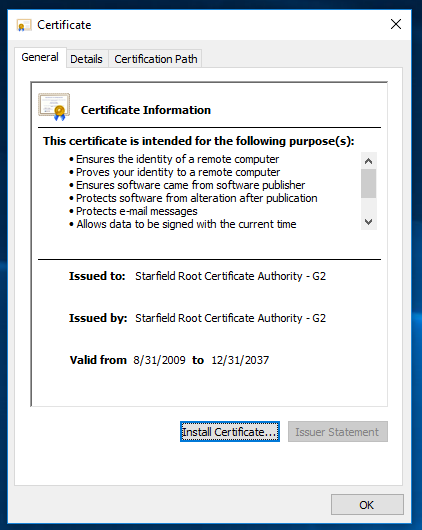
15.4(3)M8. I looked at the cert chain for https://www.duckdns.org, and it looks like there's a root CA (Starfield), a subordinate CA, and the cert for https://www.duckdns.org.
Here are the logs:
router#show debug
Dynamic DNS debugging is on
Cryptographic Subsystem:
Crypto Engine Error debugging is on
PKI:
Crypto PKI Msg debugging is on
Crypto PKI Trans debugging is on
verbose debug output debugging is on
router#
Nov 19 2017 22:16:16.361 MST: DYNDNSUPD: Adding DNS mapping for <host>.duckdns.org <=> <IP>
Nov 19 2017 22:16:16.361 MST: HTTPDNS: Update add called for <host>.duckdns.org <=> <IP>
Nov 19 2017 22:16:16.361 MST: HTTPDNSUPD: Session ID = 0xF2
Nov 19 2017 22:16:16.361 MST: HTTPDNSUPD: URL = 'https://www.duckdns.org/update?domains=<HOSTNAME>&token=<TOKEN>&ip=<IP>&verbose=true'
Nov 19 2017 22:16:16.361 MST: HTTPDNSUPD: Sending request
Nov 19 2017 22:16:16.573 MST: CRYPTO_PKI: (A03DA) Session started - identity selected (TP-self-signed-2092446490)x
Nov 19 2017 22:16:16.573 MST: CRYPTO_PKI: Rcvd request to end PKI session A03DA.
Nov 19 2017 22:16:16.573 MST: CRYPTO_PKI: PKI session A03DA has ended. Freeing all resources.
Nov 19 2017 22:16:16.573 MST: CRYPTO_PKI: unlocked trustpoint TP-self-signed-2092446490, refcount is 0
Nov 19 2017 22:16:16.685 MST: CRYPTO_PKI: (A03DB) Session started - identity not specified
Nov 19 2017 22:16:16.689 MST: CRYPTO_PKI: Added x509 peer certificate - (1371) bytes
Nov 19 2017 22:16:16.689 MST: CRYPTO_PKI: Added x509 peer certificate - (1284) bytes
Nov 19 2017 22:16:16.689 MST: CRYPTO_PKI: Added x509 peer certificate - (1188) bytes
Nov 19 2017 22:16:16.693 MST: CRYPTO_PKI: Added x509 peer certificate - (1043) bytes
Nov 19 2017 22:16:16.693 MST: CRYPTO_PKI: create new ca_req_context type PKI_VERIFY_CHAIN_CONTEXT,ident 491
Nov 19 2017 22:16:16.693 MST: CRYPTO_PKI: (A03DB)validation path has 1 certs
Nov 19 2017 22:16:16.693 MST: CRYPTO_PKI: Unable to locate cert record by issuername
Nov 19 2017 22:16:16.693 MST: CRYPTO_PKI: No trust point for cert issuer, looking up cert chain
Nov 19 2017 22:16:16.693 MST: CRYPTO_PKI: destroy ca_req_context type PKI_VERIFY_CHAIN_CONTEXT,ident 491
Nov 19 2017 22:16:16.693 MST: CRYPTO_PKI: Rcvd request to end PKI session A03DB.
router#
Nov 19 2017 22:16:16.693 MST: CRYPTO_PKI: PKI session A03DB has ended. Freeing all resources.
Nov 19 2017 22:16:16.693 MST: HTTPDNSUPD: Call returned Request Aborted, update of <HOSTNAME><=> <IP> failed
Nov 19 2017 22:16:16.693 MST: DYNDNSUPD: Another update completed (outstanding=0, total=0)
Nov 19 2017 22:16:16.697 MST: HTTPDNSUPD: Clearing all session 242 info
router#
- Labels:
-
Other Routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2017 12:38 AM
Hello,
not sure if this helps you in any way, but below is a link to a sample configuration including a pastable certificate chain for Starcom...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2017 09:46 AM - edited 11-20-2017 09:47 AM
Thanks. Do you (or anyone else) know how I would enter the certificate chain? Looks like Cisco IOS is asking me to "Enter the certificate in hexidecimal representation...."
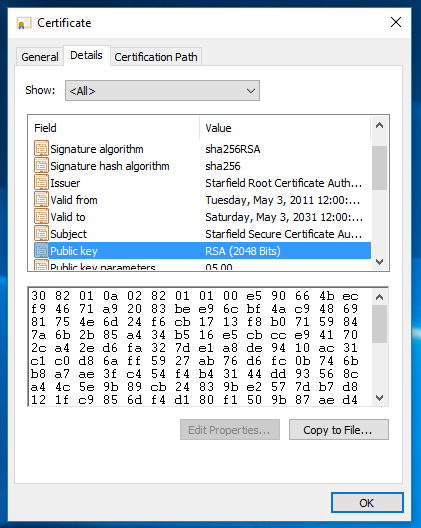
I enter it, but Cisco IOS does not save it. I downloaded the root CA certificate through the Google Chrome browser and copied the public key from the Windows dialog box for the certificate under the "Details" tab.
Then I made groupings of 8 hex digits each and pasted them into Cisco IOS:
3082010a 02820101 00bdedc1 03fcf68f fc02b16f 5b9f48d9 9d79e2a2 b7036156 18c347b6
d7ca3d35 2e8943f7 a1699bde 8a1afd13 209cb449 77322956 fdb9ec8c dd22fa72 dc276197
eef65a84 ec6e19b9 892cdc84
5bd574fb 6b5fc589 a5105289 4655f4b8 751ce67f e454ae4b f8557257 0219f817 7159eb1e
280774c5 9d48be6c b4f4a4b0 f3643779 92c0ec46 5e7fe16d 534c62af cd1f0b63 bb3a9dfb
fc790098 6174cf26 824063f3
b2726a19 0d99cad4 0e75cc37 fb8b89c1 59f1627f 5fb35f65 30f8a7b7 4d765a1e 765e34c0
e8965699 8ab3f07f a4cdbddc 32317c91 cfe05f11 f86baa49 5cd19994 d1a2e363 5b0976b5
5662e14b 741d96d4 26d40804
59d0980e 0ee6defc c3ec1f90 f1020301 0001
Here are the Cisco IOS commands I used:
crypto pki trustpoint STARFIELD
enrollment terminal pem
revocation-check none
exit
crypto pki certificate chain STARFIELD
certificate ca 01
3082010a 02820101 00bdedc1 03fcf68f fc02b16f 5b9f48d9 9d79e2a2 b7036156 18c347b6
d7ca3d35 2e8943f7 a1699bde 8a1afd13 209cb449 77322956 fdb9ec8c dd22fa72 dc276197
eef65a84 ec6e19b9 892cdc84
5bd574fb 6b5fc589 a5105289 4655f4b8 751ce67f e454ae4b f8557257 0219f817 7159eb1e
280774c5 9d48be6c b4f4a4b0 f3643779 92c0ec46 5e7fe16d 534c62af cd1f0b63 bb3a9dfb
fc790098 6174cf26 824063f3
b2726a19 0d99cad4 0e75cc37 fb8b89c1 59f1627f 5fb35f65 30f8a7b7 4d765a1e 765e34c0
e8965699 8ab3f07f a4cdbddc 32317c91 cfe05f11 f86baa49 5cd19994 d1a2e363 5b0976b5
5662e14b 741d96d4 26d40804
59d0980e 0ee6defc c3ec1f90 f1020301 0001
quit
exit
For some reason Cisco IOS doesn't save the certificate when I do a "show run".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2017 11:03 AM
Hello Sam,
just to make sure: you need to copy the beginning and end lines as well, including the five dashes...
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2017 11:14 AM - edited 11-20-2017 11:15 AM
Hi Georg,
It doesn't seem like I'm supposed to, as I get a "Invalid input" error. I believe that the BEGIN and END certificate lines are only present in Base64 encoded certificates.
router(config-cert-chain)#certificate ca 00
Enter the certificate in hexidecimal representation....
router(config-pki-hexmode)#-----BEGIN CERTIFICATE-----
^
% Invalid input detected at '^' marker.
router(config-pki-hexmode)#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2017 11:24 AM
Odd...which router and IOS version are you running ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2017 10:14 PM
I'm on a Cisco 1921 ISR router running 15.4(3)M8.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-31-2018 04:34 AM
Hi Sam,
Did you every get the Starfield certs loaded onto your 1921? I'm hitting the same problem on my 1941. I had this working with the previous Duck DNS CA (Startcom) but since they changed, I've not been able to get it to work. There's a confusing number of cert files on the Starfield repository: https://certs.secureserver.net/repository/
Thanks,
James
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2018 11:21 AM
Hey James -
I never got it to work. Kind of a shame, since I feel like there's a way to do it. Close, but no cigar.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide