- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: ASA 5505 - Whats Wrong with this Configuration
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2020 04:55 AM
Cisco Packet Tracer 6.2 - I am trying configure Site-to-Site VPN between HQ and Branch Office. Can someone help me, whats wrong with this configuration.
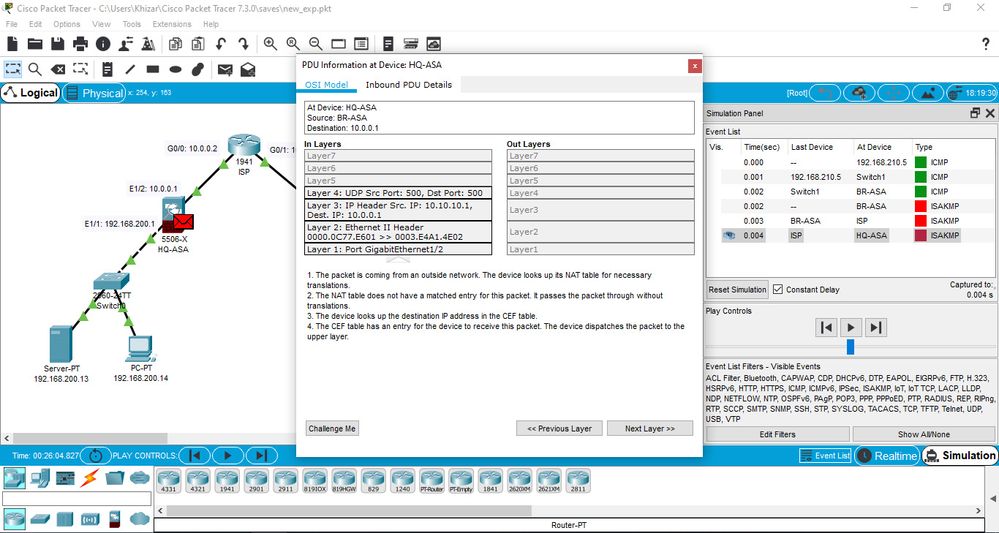
Network Topology:
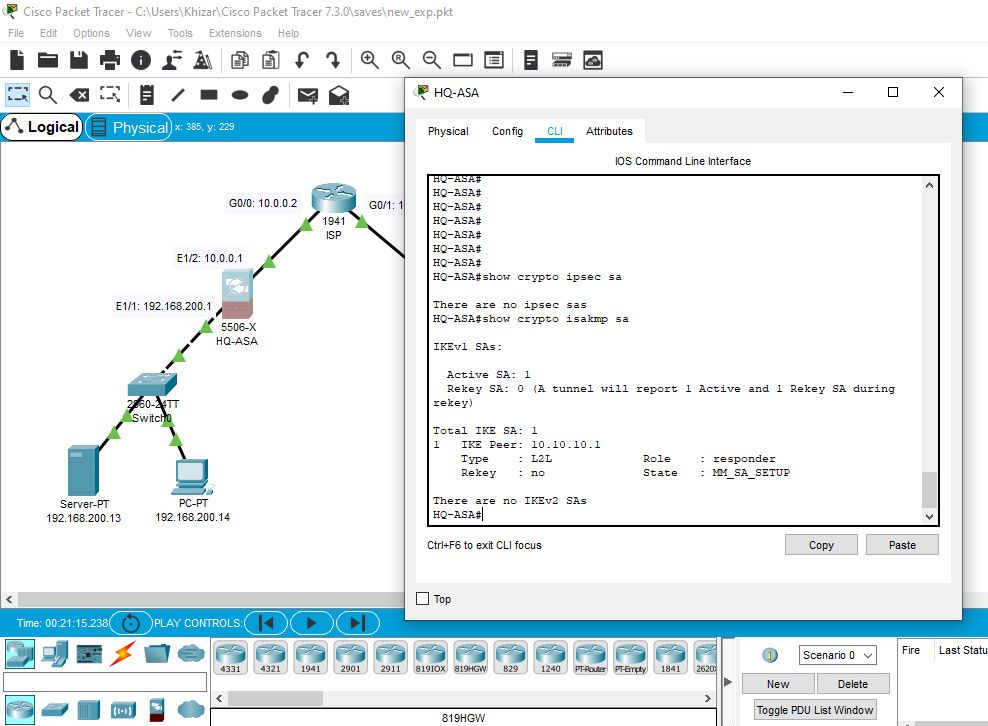
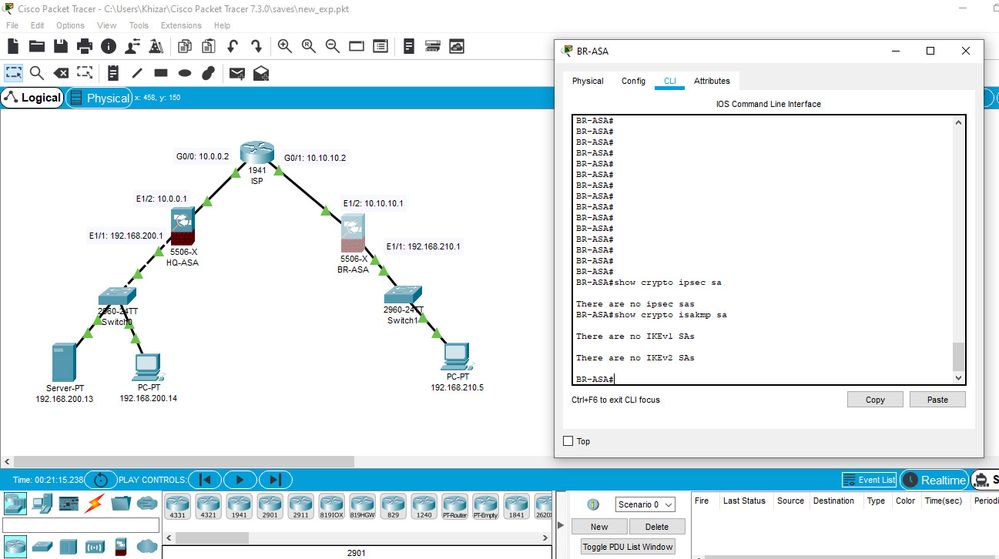
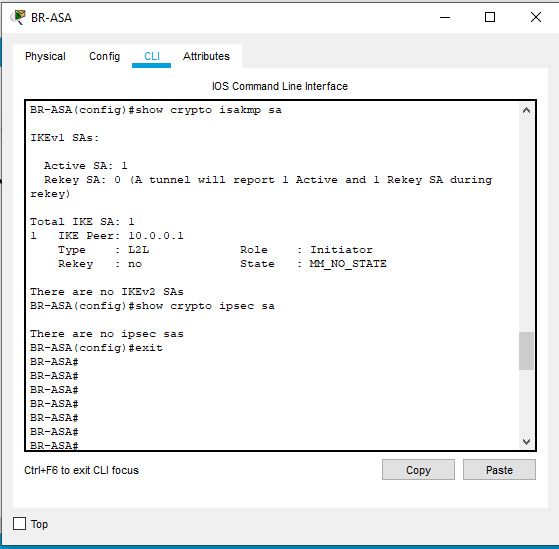
Show Crypto ipsec sa, shows no sa
HQ-ASA
ASA Version 8.4(2)
!
hostname HQ-ASA
names
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan1
nameif inside
security-level 100
ip address 192.168.200.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address 10.0.0.1 255.255.255.0
!
object network BR
subnet 192.168.210.0 255.255.255.0
object network HQ
subnet 192.168.200.0 255.255.255.0
!
route outside 0.0.0.0 0.0.0.0 10.0.0.2 1
!
access-list HQ<->BR extended permit icmp object HQ object BR
access-list HQ<->BR extended permit tcp object HQ object BR
access-list OUTSIDE extended permit tcp object BR object HQ
access-list OUTSIDE extended permit icmp object BR object HQ
!
!
access-group OUTSIDE out interface inside
!
!
!
!
!
!
!
telnet timeout 5
ssh timeout 5
!
dhcpd auto_config outside
!
!
!
!
crypto ipsec ikev1 transform-set HQ->BR esp-3des esp-md5-hmac
!
crypto map VPNMAP 10 match address HQ<->BR
crypto map VPNMAP 10 set peer 10.10.10.1
crypto map VPNMAP 10 set security-association lifetime seconds 86400
crypto map VPNMAP 10 set ikev1 transform-set HQ->BR
crypto map VPNMAP interface outside
crypto ikev1 enable outside
crypto ikev1 policy 1
encr 3des
hash md5
authentication pre-share
group 2
!
tunnel-group 10.10.10.1 type ipsec-l2l
tunnel-group 10.10.10.1 ipsec-attributes
ikev1 pre-shared-key cisco123
BR-ASA
hostname BR-ASA
names
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan1
nameif inside
security-level 100
ip address 192.168.210.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address 10.10.10.1 255.255.255.0
!
object network BR
subnet 192.168.210.0 255.255.255.0
object network HQ
subnet 192.168.200.0 255.255.255.0
!
route outside 0.0.0.0 0.0.0.0 10.10.10.2 1
!
access-list BR<->HQ extended permit tcp object BR object HQ
access-list BR<->HQ extended permit icmp object BR object HQ
access-list OUTSIDE extended permit icmp object HQ object BR
access-list OUTSIDE extended permit tcp object HQ object BR
!
!
access-group OUTSIDE out interface inside
!
!
!
!
!
!
!
telnet timeout 5
ssh timeout 5
!
!
!
!
!
crypto ipsec ikev1 transform-set BR->HQ esp-3des esp-md5-hmac
!
crypto map VPNMAP 10 match address BR<->HQ
crypto map VPNMAP 10 set peer 10.0.0.1
crypto map VPNMAP 10 set security-association lifetime seconds 86400
crypto map VPNMAP 10 set ikev1 transform-set BR->HQ
crypto map VPNMAP interface outside
crypto ikev1 enable outside
crypto ikev1 policy 1
encr 3des
hash md5
authentication pre-share
group 2
!
tunnel-group 10.0.0.1 type ipsec-l2l
tunnel-group 10.0.0.1 ipsec-attributes
ikev1 pre-shared-key cisco123
Solved! Go to Solution.
- Labels:
-
Other Routing
-
Routing Protocols
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 01:32 AM
Sorry about that, my bad, I forgot to apply the access lists again.
You need to give it a few minutes before you see the SAs, the ASAs seem to start slowly...
Attached the revised file. Start a ping -t from the PCs and wait for a few minutes, you should then see the SAs...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2020 05:36 AM
Hi,
1. Do you have IP connectiivity between the two ASA's: 10.0.0.1 and 10.10.10.1?
2. Configure your crypto-ACL's, where the encryption domain is defined, with IP statements, not TCP/ICMP statements:
no access-list HQ<->BR extended permit icmp object HQ object BR
no access-list HQ<->BR extended permit tcp object HQ object BR
access-list HQ<->BR extended permit ip object HQ object BR
no access-list BR<->HQ extended permit tcp object BR object HQ
no access-list BR<->HQ extended permit icmp object BR object HQ
access-list BR<->HQ extended permit ip object BR object HQ
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2020 11:49 PM - edited 04-05-2020 11:49 PM
Thank you
1. Yes - ISP Router is forwarding traffic, I can ping both firewalls from each other.
2. Added this line but problem still exists
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2020 12:08 AM
Hello,
post the (zipped) Packet Tracer project (.pkt) file...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2020 12:10 AM
Hi,
Have you remove the existing 2 lines and added just that one IP statement? Generate traffic between the protected subnets and post the output of "show crypto ipsec sa" and "show crypto isakmp sa".
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2020 01:53 AM
Downloaded Packet Tracer 7.3 and reconfigured with ASA 5506-x. Remove that two lines and added this online on both sides:
Result on HQ-ASA:
Result on BR-ASA
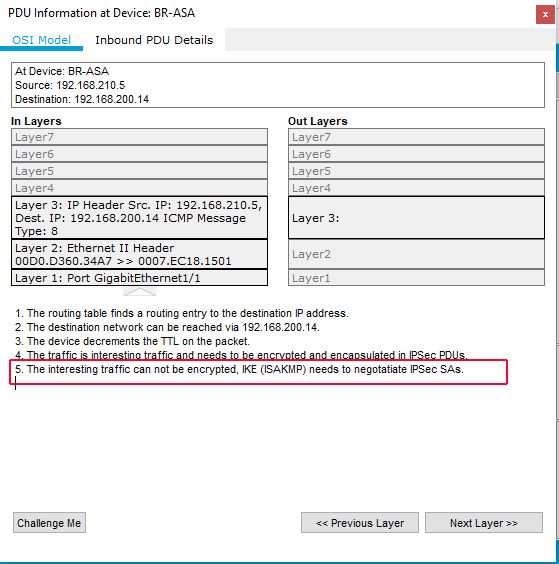
In Simulation Mode - Ping from BR to HQ:
Result on HQ-ASA
Packed managed to cross ISP Router and Error on HQ-ASA
Configuration file is attached pl
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2020 02:20 AM
Hi,
Can you reactivate IKE on the outside interface by removing and re-applying the command "crypto ikev1 enable outside"? Lso ensure to generate traffic between he protected subnets, don't ping from the ASA< but from behind the ASA.
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2020 02:37 AM
Remove and reapplied. It shows this:
run a ping and after that no IKEV1 sa, as usual. Complete configuration file is also attached above.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2020 03:39 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2020 11:39 PM - edited 04-06-2020 11:39 PM
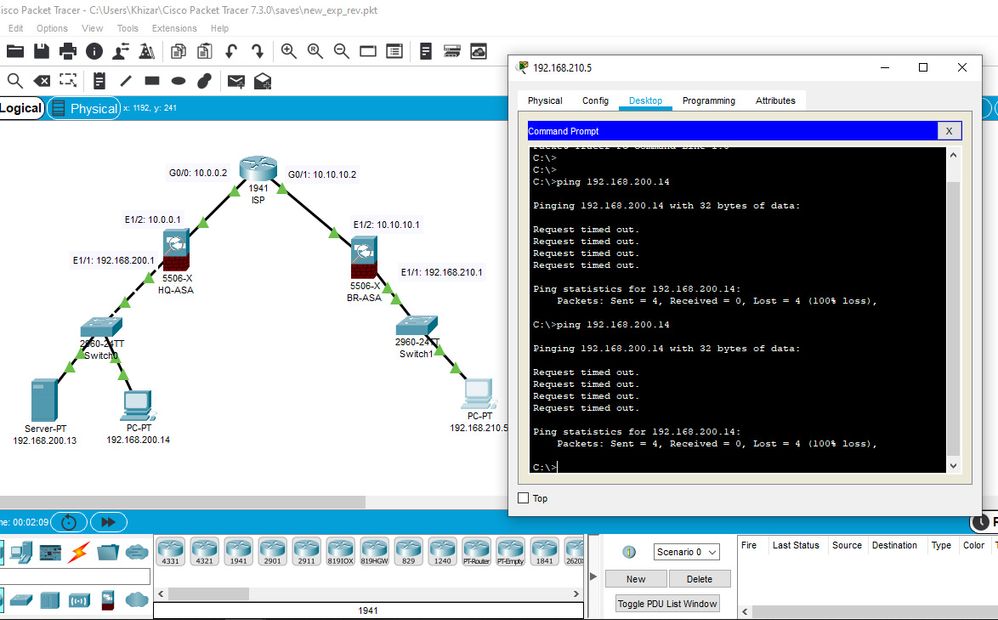
@Georg Pauwen thank you very much for your time and effort. I observed that access-group OUTSIDE was removed but after downloading and straight pinging from BR to HQ, not working. Below is attached image of ping result. May be my packet tracer is faulty ..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 01:32 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 02:18 AM
Thank you again for your time and efforts.
At first ping not started for 5 minutes. Closed Packet Tracer and re-opened. Ping started immediately and now it is working.
One thing more regarding IP Route of subnets at ISP Router -> I was not aware of this practice. Previously, if we place Routers instead of Firewall, we don't need any configuration on ISP Router apart from Interface configuration. Added a new thing in my knowledge, I really appreciate -> Thank you again
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide