- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: block access in same vlan
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2019 12:36 AM
Hello all,
We have 3 vlans
vlan 10 - 192.168.1.0/24
vlan 30 - 192.168.2.0/24
vlan 40 - 192.168.3.0/24
there is one server in vlan 10, server1 (192.168.1.5) and it only needs to access server2(192.168.1.9) on https port but its access to other clients on same vlan should be blocked.
Preferrably other clients(server1, server2,server3, server4) should not communicate to each other but clients on different VLANs should not be blocked (they already have access via firewall now)
How can I achive this? Vlan access-map or access list or any other suggestion? Please send me config example.
Thank you very much in advance.
Isac
Solved! Go to Solution.
- Labels:
-
Catalyst Switch
-
LAN Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2019 01:32 AM - edited 04-17-2019 10:30 PM
Hello
Vlan access map would be applicable here:
Example:
access-list 101 permit tcp host 192.168.0.9 host 192.168.0.5 eq 443
access-list 101 permit tcp host 192.168.0.5 host 192.168.0.9 eq 443
access-list 102 permit ip host 192.168.1.5 host 192.168.1.9
access-list 102 permit ip host 192.168.1.9 host 192.168.1.5
vlan acess-map srv2srv 10
match ip address 101
action forward
vlan access-map srv2srv 20
match ip address 102
action drop
vlan access-map srv2srv 99
vlan filter srv2srv vlan-list 10
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2019 12:57 AM
- The only option in this case is to have local firewalling on the intended server
M.
-- ' 'Good body every evening' ' this sentence was once spotted on a logo at the entrance of a Weight Watchers Club !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2019 01:25 AM
vlan access-map NAME
SW1(config-access-map)#match ip address CREATED-ACL name of acl you used to classify the traffic
SW1(config-access-map)#action drop
SW1(config-access-map)#vlan access-map NAME this allows all other communication to take place
SW1(config-access-map)#action forward
You then use vlan-filter NAME vlan-list VLAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2019 01:29 AM - edited 04-17-2019 01:31 AM
You can't make layer 2 switch emulate like a firewall or layer 3 packet filtering. I agree with marce1000 that your only option is to create a firewall at the server side.
Another option is segmentation through private vlan, see link https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3750x_3560x/software/release/12-2_53_se/configuration/guide/3750xscg/swpvlan.html.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2019 01:30 AM
Hello,
a VACL should work. You need to draw out in detail who needs access to what, as your brief post does not contain enough information. So, best post a schematic drawing with IP addresses, and indicate which IP address needs access to which other IP addresses.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2019 01:32 AM - edited 04-17-2019 10:30 PM
Hello
Vlan access map would be applicable here:
Example:
access-list 101 permit tcp host 192.168.0.9 host 192.168.0.5 eq 443
access-list 101 permit tcp host 192.168.0.5 host 192.168.0.9 eq 443
access-list 102 permit ip host 192.168.1.5 host 192.168.1.9
access-list 102 permit ip host 192.168.1.9 host 192.168.1.5
vlan acess-map srv2srv 10
match ip address 101
action forward
vlan access-map srv2srv 20
match ip address 102
action drop
vlan access-map srv2srv 99
vlan filter srv2srv vlan-list 10
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2019 02:22 AM
Thank you for your answers.
More info:
inside vlan 10 permit server1 (192.168.1.5) https TO server2(192.168.1.9) only https(443)
inside vlan 10 deny any other communication among clients
Clients on other VLANs coming via firewall should not be affected since they have already access.
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2019 05:15 AM
Hello,
not sure if you have already resolved this, but below is what I have come up with:
vlan access-map FILTER_10 10
match ip address 101
action forward
vlan access-map FILTER_10 20
match ip address 102
action drop
vlan access-map FILTER_10 30
action forward
!
vlan filter FILTER_10 vlan-list 10
!
access-list 101 permit ip host 192.168.1.5 host 192.168.1.9 eq 443
access-list 101 permit ip host 192.168.1.9 host 192.168.1.5 eq 443
access-list 102 permit ip 192.168.1.0 0.0.0.255 192.168.1.0 0.0.0.255
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2019 06:05 AM
Hello
Looks your acl 102 relating to map 20 will deny all traffic on that vlan it needs to be more specific( host-host)
lastly no need specifying action forward in the catch all map 30 as the default action is to forward anyway
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2019 02:57 AM
- Acknowledged but be aware : it may become difficult to keep up in high redundancy environments ; suppose the server is connected to a dual-homed fex behind a nexus vpc pair with hsrp etc... Not applying the access list on all needed components may need to cheese holes permitting access anyway. Better is to separate app/servers and clients with Intranet firewalling solutions.
M.
-- ' 'Good body every evening' ' this sentence was once spotted on a logo at the entrance of a Weight Watchers Club !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2019 03:06 AM
Hello
@marce1000 not so sure i understand why would you require FW rules - this will only be L2 traffic not L3 , its only negating access between hosts WITHIN the same broadcast domain
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2019 04:52 AM
Hello Paul,
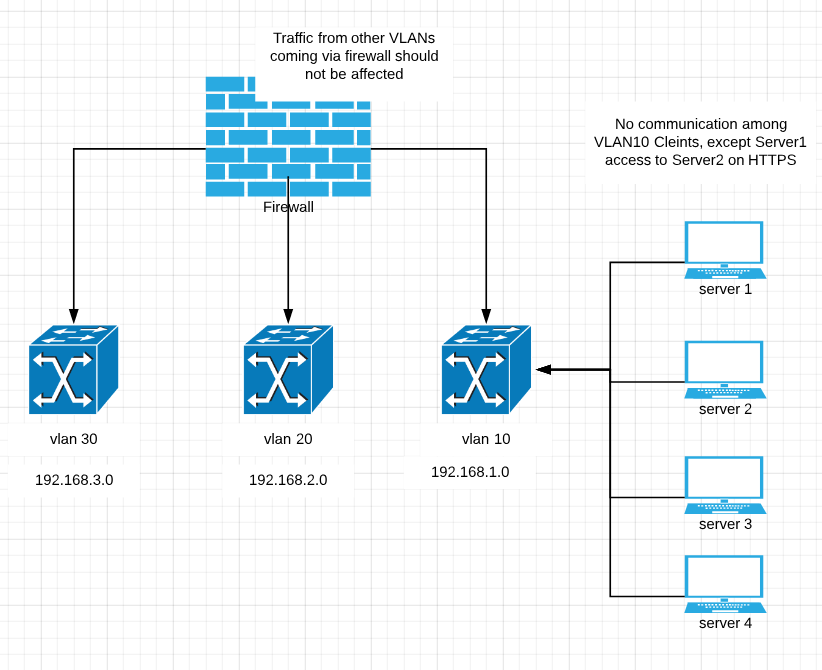
Thank you for the solution but we also want server1 to access to server2 on https and block any other traffic among clients inside VLAN10. Please see the diagram.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2019 06:16 AM
Hello
i have edited previous example please review it
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2020 10:47 PM
Hi Paul,
I had one question in the same context.
If I want to block all communication between all hosts in the VLAN.
e.g. block east west.
but only allow north south from the hosts to internet or anywhere in the network.
How will I be able to achieve that.
Can you provide any config for that ?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2020 01:12 AM
Hello
@parag_waghmare wrote:
Hi Paul,
I had one question in the same context.
If I want to block all communication between all hosts in the VLAN.
e.g. block east west.
but only allow north south from the hosts to internet or anywhere in the network.
How will I be able to achieve that.
Can you provide any config for that ?
Thanks.
Ammend access-list 102 to encompass the whole of vlan 10
no access-list 102
access-list 102 permit ip 192.168.1.0 0.0.0.255 192.168.1.0 0.0.0.255
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: