- Cisco Community
- Technology and Support
- Networking
- Routing
- Cisco Catalyst 3560-CX as core switch/router on a flat network
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco Catalyst 3560-CX as core switch/router on a flat network
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2018 07:27 AM - edited 03-05-2019 10:55 AM
Hi all,
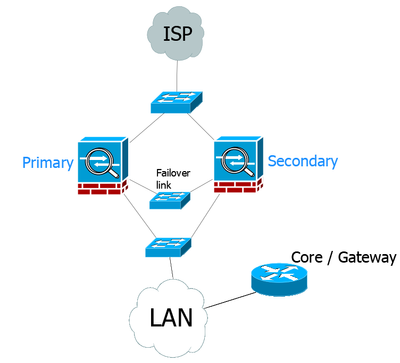
We are in the process of replacing a very old core router that works as the network's default gateway:
network: 10.1.0.0/16 (flat, no VLANs)
ASA SSL VPN remotepool: 172.1.1.0/24
All the router does here is be the default gateway for the network and send all traffic out to the firewall with a static route (it used to route to remote sites too). That includes the SSL VPN remotepool subnet:
ip route 0.0.0.0 0.0.0.0 ASAinsideipaddr
ip route 172.1.1.0 255.255.255.0 ASAinsideipaddr
So I've been thinking of replacing the router with two layer 3 switches for redundancy and future-proofness:
And just realised i'm a but rusty with layer 3 switch routing.
Now my question is, if i configure these switch ports as routed ports they cannot belong to the same network, correct?
I would have to configure a single VLAN 1 on the switch for the 10.1.0.0/16 subnet but would i also have to tag the ports as belonging in VLAN1 or simply add a default route to the firewall's interface? How would this work? If all ports are switch ports and the VLAN is in the 10.1.0.0/16 subnet then i would only need to add a single static route to send remotepool traffic out to the ASA's inside interface?
These LAN connections would be connecting to a HPE switch stack so RSTP would also be needed.
Which makes me think, is it worth using the ASAs as the default gateway instead for now to simplify things and look to buy layer 3 switches only if we decide to split the network into VLANs? The userbase is somewhere between 100-150 users.
In which case, is there anything i should be aware of when using the ASA as the network's default gateway? I assume the ASA would not need any additional routing done to connect the inside interface 10.1.0.x/16 to the remotepool clients.
- Labels:
-
LAN Switching
-
Other Routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2018 08:44 AM - edited 09-17-2018 08:54 AM
Hello
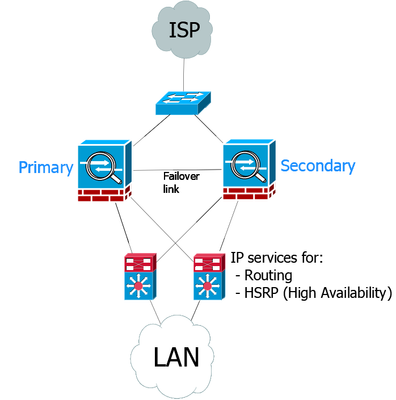
you don’t really need to use hrsp depending switch type you can just use say two stackable 2960x for example in a stack with a default route pointing to the asa HA
I am assuming the Asa’s are HA failover and as such just have each individual asa inside interfaces (and outside if applicable -in different L2 vlan access ports) attach to either one of the physical switches in this stack - HA failover will do the rest.
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2018 01:39 AM - edited 09-18-2018 01:57 AM
Hi Paul,
Thanks for your response.
We are getting 2 x 3560CX-8TC-S, as far as i can these are not stackable?
Currently the LAN and ASA Inside interfaces are all in the same subnet.
In which case, do you think i can get away with configuring the ASA Inside interfaces on a separate subnet, configuring the switch ports as routed and enabling HSRP for LAN nodes so i can use the switches as the network's default gateway? I can then point to the firewalls with a static route and point back from the firewalls with another static route?
edit: alternatively i could use the firewalls as the network's default gateway (they are in an active/standby config) and simply use the switches for L2 switching with STP for failover. I just don't think it feels right to use the firewalls as the default gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2018 03:20 AM - edited 09-18-2018 08:49 AM
Hello
@Nasos Ergot wrote:
Hi Paul,
Thanks for your response.
We are getting 2 x 3560CX-8TC-S, as far as i can these are not stackable?
Currently the LAN and ASA Inside interfaces are all in the same subnet. - Isn't the ASA inside interfaces assigned to a vlan related to a routed svi on the L3 switch?
In which case, do you think i can get away with configuring the ASA Inside interfaces on a separate subnet, configuring the switch ports as routed and enabling HSRP for LAN nodes so i can use the switches as the network's default gateway? I can then point to the firewalls with a
static route and point back from the firewalls with another static route?
Now with this approach and the asa's in an HA active/standby mode, the Fws need to have the same primary/standby addressing on each monitored interface so with HRSP in the mix you will need to point both fws towards the single VIP of the HRSP L3 svi switch as such I would say HRSP is indeed applicable.edit: alternatively i could use the firewalls as the network's default gateway (they are in an active/standby config) and simply use the switches for L2 switching with STP for failover. I just don't think it feels right to use the firewalls as the default gateway. - dont see why this would be a problem depending how may L3 vlans , as really you don't want the FW's doing to much intervlan routing?
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: