- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: DHCP pools to seperate VLANS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2018 10:56 PM - edited 03-05-2019 10:59 AM
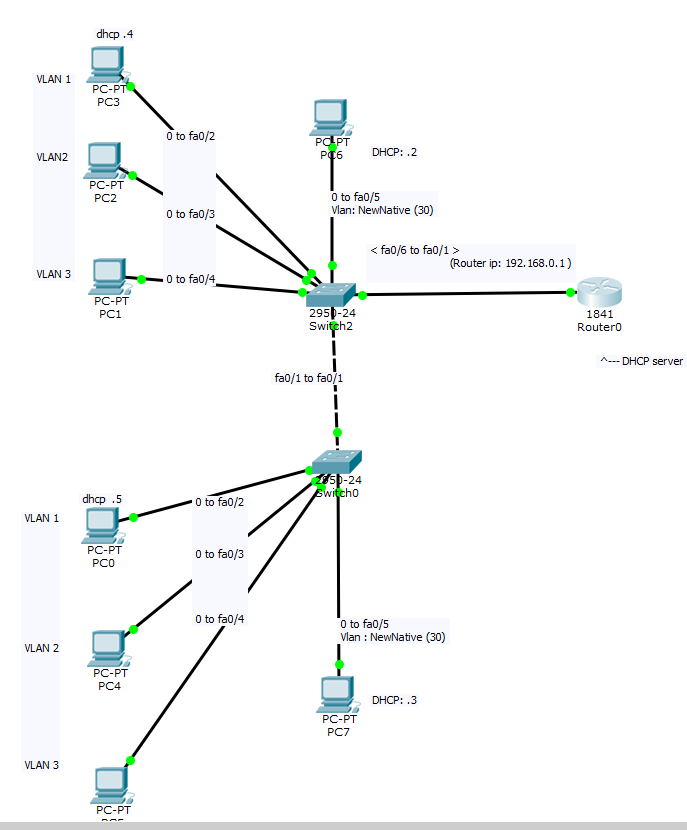
Greetings! so this is a very loaded question in my mind but a pretty straight forward aim: I am trying to setup a DHCP pool PER VLAN
I have the following topology:
So I have two switches that have a trunk connection (and from Switch2 to Router0, I have a trunk connection as well). And all vlans are allowed over on both.
I was a little confused at the difference between a native and the default vlan1 when I set it up, so my vlan 1 has PC3 and PC0 on it but also, out of consequence, PC6 and PC7. I wanted to treat these as normal-"public"-default clients who interact on the open broadcast domain with no special demarcation.
I created a DHCP pool on router1, called 'NewNative' and it has been successfully giving out IP addresses to PC6, PC3, PC0 and PC7. I don't really want it giving ip addresses to VLAN1 (PC3 and PC0).
I suppose that their is no way to move all my interfaces lodged in vlan1 over to VLAN 30 ( the Native VLAN, that I manually set between switch0 and switch2) and just let that be the new default.
It doesn't matter that much.. Just not sure how to mimic good practice.
My main problem is that I'm struggling with subinterfaces. I created subinterfaces on router0 ( ex. 'fa0/1.2' was set for vlan 2. I gave it an ip address of 192.168.2.1 )
How do I set up a new DHCP pool within router0, and get PC2 to DORA successfully?
Like what am I missing? So that when I click 'dynamic' on PC2, it will send a broadcast that will travel to switch2, and end up on interface fa0/1.2 to the router, so that the router knows which DHCP pool to give out from?
In fact, what would I have to say to the router to make my "VLAN2DHCP-pool", interface specific even?
Solved! Go to Solution.
- Labels:
-
LAN Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2018 12:45 AM
Hello,
I have made a few changes to your project, revised file is attached. Basically, if you change the native Vlan, this needs to be reflected on the subinterface of the router, by adding the keyword 'native'. I have created a subinterface .30 on the router.
For the sake of simplicity, I have also created DHCP pools on the router for all 4 Vlans. And last but not least, the trunk between the switch and the router needs to have Vlan 30 set as native as well...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2018 12:45 AM
Hello,
I have made a few changes to your project, revised file is attached. Basically, if you change the native Vlan, this needs to be reflected on the subinterface of the router, by adding the keyword 'native'. I have created a subinterface .30 on the router.
For the sake of simplicity, I have also created DHCP pools on the router for all 4 Vlans. And last but not least, the trunk between the switch and the router needs to have Vlan 30 set as native as well...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2018 05:59 AM
Hello Georg
Would you be a gent and repost your packet tracer file, the one attached doesn't seem to show your dhcp scopes and it has password enabled switches
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2018 06:09 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2018 08:46 PM
Now that I've kinda opened the box though, as the file sits (after your improvements), what is the meaningful functional difference between the default vlan and the native vlan, in the context of this aim: to forward traffic from hosts, off either switch, that do NOT have vlan assignments. If I go through the effort of assigning a new host to vlan 30, rather than default vlan, what would be the consequence, let's say, if it was to send a packet to the router to actually be routed to another network?
Assuming dot1q encapsulation is enabled for vlan30 and default vlan is just as is. Does it make a difference at all? I don't think so?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2018 02:30 PM
You ask a couple of questions that I would respond to
1) what is the meaningful functional difference between the default vlan and the native vlan
This seems to get back to the discussion in the previous post. default vlan deals with what vlan an interface belongs to if there is no explicit vlan assignment for that interface. And native vlan deals with frames sent over a trunk interface and which frames will have vlan tags and which frames will not have vlan tags.
So for example if a switch had this in its config
interface Gig0/0/1
switchport access vlan 30
interface Gig0/0/2
interface Gig0/0/3
switchport access vlan 20
we can look at that config and be confident that Gig0/0/1 is in vlan 30 and Gig0/0/3 is in vlan 20. But what about Gig0/0/2? There is no vlan assignment. Some people might think that this means that the interface is not in a vlan. But that is not true. Every interface on the switch that is an access port will belong to some vlan. If there is no vlan assignment on the interface then it will belong to the default vlan.
2) to forward traffic from hosts, off either switch, that do NOT have vlan assignments.
Perhaps this is also related to the point above. Every access port belongs to some vlan. If there is not a specific vlan assignment then the port belongs in the default vlan, which is usually vlan 1.
3) a new host to vlan 30, rather than default vlan, what would be the consequence, let's say, if it was to send a packet to the router to actually be routed to another network?
I am not sure what you are really asking here. But let me try to answer it this way. Assuming that you have assigned a host to vlan 30 then it should have an IP address that is part of the subnet associated with vlan 30. And it should have configured a default gateway (or default router in some terminology) that is a router interface (or a layer 3 switch vlan interface) that belongs in vlan 30. The host could not use a gateway that belongs in vlan 10 or in vlan 1 but must use a gateway that belongs in vlan 30.
So let us think about a host that is assigned to vlan 30 and it wants to send a packet to the Internet. The host knows that the destination is remote so it will want to forward the packet to its default gateway. It will arp for the gateway address. If the gateway address is in the same vlan 30 then arp will succeed. If the gateway were not in vlan 30 then the arp request would fail and the host could not send the packet. If the gateway is in vlan 30 then arp request is successful and the host can forward the packet to the gateway. The gateway will receive the packet from the host in vlan 30 and will use its default route to forward the packet on toward the Internet.
4) Assuming dot1q encapsulation is enabled for vlan30 and default vlan is just as is. Does it make a difference at all? I don't think so?
I do not understand what you are asking here. For one thing dot1q encapsulation is enabled for trunk ports and not enabled for a vlan. And since you have specified that you assigned the host to vlan 30 then the default vlan does not come into play here.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2018 04:55 PM
And yes 3 does answer my question, in the case that vlan 30 was my native and that all the surrounding parameters being, that the proper subnets and default-routers needed to be declared and matching. It would of made more sense if I just said Native rather than vlan 30 I think but I'm still one to make word spaghetti haha. Thank you so much for your time! I really appreciate your detailed responses. Really takes me out of the bog I've been cultivating, jumping around.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2018 05:32 PM
It is ok to think out loud. And ok to sometimes post those to the community. Glad that my explanations were helpful. If you have other questions feel free to post them here. These communities are excellent places to post questions and to learn about networking. I hope to see you continue to be active in the community.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2018 02:14 PM
There are a couple of points in the original post that I would like to address.
First: there is this statement
I was a little confused at the difference between a native and the default vlan1
I remember being confused about that as I was starting to learn about switching and networking. But it is really pretty simple if you think about these points:
- Every access port on a switch belongs to some vlan. If the interface config has statements like switchport access vlan 20 then it is pretty simple to understand that this interface belongs to vlan 20. But what if the interface does not assign a vlan membership? There is a default assignment (remember that basically default says "in the absence of specific information what should I do") and that default assignment is to vlan 1. So any switch interface that is not a trunk, and is not specifically assigned to some vlan would be assigned to vlan 1.
- native vlan is a concept used in trunking vlans. So it does not have anything to do with what vlan a particular port belongs to (so it is quite different from default vlan).
- so default vlan is for individual interface vlan assignment and native vlan is for trunking.
- so what is the native vlan? To understand this we should think about how a trunk works between switches. Remember that the most important aspect of a trunk is that it carries multiple vlans. So if switchA is sending to switchB over a trunk that carries vlans 1, 10, 20, and 30 how does it identify which vlan a particular frame belongs to? The solution is that the switch adds a "tag" to the Ethernet frame that identifies the individual vlan. So Ethernet frames can have a "tag" as part of the frame. But what if some device is connected to the trunk and that device does not understand "tags" (in particular what if some host PC - or some router interface does not understand tags). So 802.1q trunking specifies that one vlan in the trunk will have frames that do not have tags. That is the native vlan. The main purpose of native vlan was to provide compatibility between devices that do understand 802.1q trunking and devices that do not. In an 802.1q trunk the default native vlan is vlan 1 but there is a configuration option to specify that some other vlan is the native vlan. remember that the main thing about native vlan is that it is the vlan whose frames do not contain vlan tags.
The other point in the original post that I would like to respond to is this
In fact, what would I have to say to the router to make my "VLAN2DHCP-pool", interface specific even?
It is really quite simple. The DHCP pool specifies that it applies to some subnet. It only works for interfaces that are in that subnet. So the DHCP pool is automatically interface specific.
And perhaps understanding that might help to explain the use of sub interfaces on the router. The router physical interface is connected to an interface on the switch that is configured as a trunk. The router physical interface does not have a vlan assignment and would process frames for the native vlan (which do not have tags). The sub interfaces on the router interface do have vlan assignments and would look for the vlan tags and the sub interface would process frames for the vlan tags matching what vlan it was assigned to.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2018 08:39 PM
I was under the impression that VLAN30 was used as the tag of even, already, tagged frames for some reason. I really appreciate your detailed response! So it seems that native vlan is not really very pertinent to anything I was trying to accomplish in my file.
So it sounds like DORA is just exactly what it stands for. A discovery request is sent out until it finds any pool that corresponds to that subnet that is assigned via switch to the vlan interface?
ex. on the Switch-A, I set the vlan network to be a.a.a.x. Then when a host, directly connected on that interface, sends its broadcast/discover frame out, the first device set up as a DHCP server with a corresponding pool to that interface, is the one "selected" to give an ip from sed-pool?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2018 02:06 PM
I am glad that now you have a better understanding of native and default vlan. It is easy if you remember that default vlan has to do with what vlan an access port will belong to while native vlan has to do with what frames get vlan tags and what frames do not get vlan tags when sent over a trunk.
Your understanding of discovery and address assignment is almost right. A device connected to a switch interface sends out a discovery frame. This is sent as a broadcast so it is forwarded to every device in that vlan. If a device in that vlan is configured with an appropriate scope then it will offer to assign an address from that scope. Bear in mind that if there were two devices configured as servers with appropriate scopes then both of them would receive the discovery frame and both would respond offering addresses.
HTH
Rick
Rick
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: