- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Help with Cisco 3750X transporting 2nd ISP via Fiber. Is it possible?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2017 10:34 AM - edited 03-05-2019 09:20 AM
Hello,
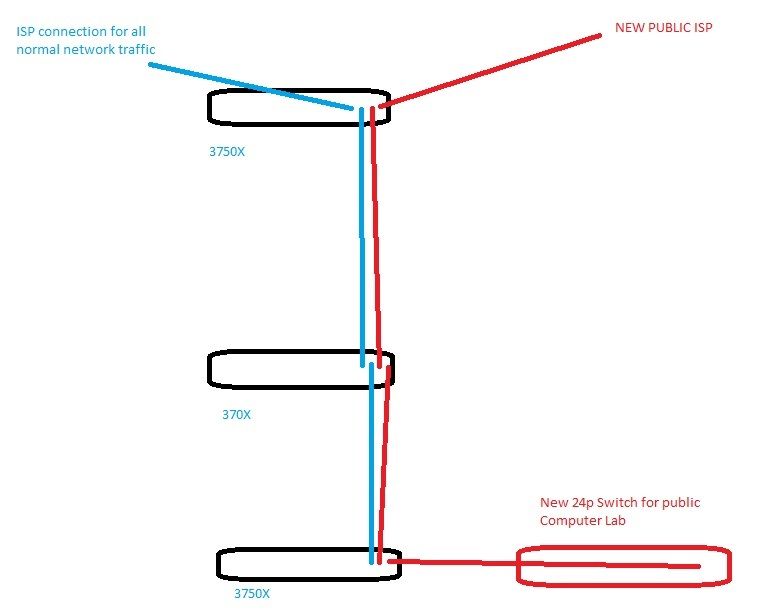
Please bare with me as I don't have my CCNA yet. But I am being asked about the possibility of transporting a 2nd Internet connection (in efforts to save money on hardware) through our existing switches. In this building for example, a 3750X is handling layer 3, and two other 3750's are staggered through the building. This building wants a public connection they pay for themselves, and we don't want that traffic in our core EIGRP based network anyway. I have Metro Ethernet providing connection through copper to port 48, and then we are trunking out via fiber to the other switches in the building. Is there anyway I could bring the new fiber public connection in through another gbic, ride the fiber and shoot it down to the furthest switch away and spit it back out? Pretty much we cant afford to buy a new router, do a new run, etc. I dont know if I'm over complicating this for myself, or what. I'm sorry if this is confusing. would I just have to create its own pool and vlan? example?
Solved! Go to Solution.
- Labels:
-
Other Routing
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2017 03:09 PM
Hello,
is this switch already connected to a primary ISP ? I am just asking because I do not see any NAT configuration.
Either way, here is the rudimentary approach. I assume that the new Vlan is 99, and the IP address space used is 192.168.1.0/24. The extended access list used in the route map denies all traffic that goes to the other Vlans, which means you have to add the correct addresses and probably have to add more lines, since you have more Vlans).
access-list extended VLAN99 deny ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
access-list extended VLAN99 deny ip 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255
access-list extended VLAN99 permit ip 192.168.1.0 0.0.0.255 any
access-list 99 permit 192.168.1.0 0.0.0.255
route-map VLAN99_TO_ISP2
match ip address VLAN99
set ip next-hop x.x.x.x
interface Vlan99
ip address 192.168.1.1 255.255.255.0
ip policy route-map VLAN99_TO_ISP2
ip nat inside source list 99 interface GigabitEthernetx/x overload
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2017 10:52 AM
hope link between switches are trunks . dual links are not needed if interconnect links are trunks
allow new vlan created through trunks between switches .assign new 24p switch to new vlan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2017 11:00 AM
As in
interface GigabitEthernet1/1/1
description *** ***
switchport mode access vlan (new)
etc?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2017 11:03 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2017 11:12 AM - edited 10-19-2017 11:13 AM
Is this on the right Track?
I am sorry for all the questions, I just cant find anything that I can make sense of in my searches
interface GigabitEthernet1/1/2 <Switch 1
description *** ***
switchport mode access vlan 99
interface Vlan99
ip address ??.??.??.?? 255.255.255.0 etc
!
interface GigabitEthernet1/1/3 <Switch 3
description *** ***
switchport mode trunk
!
interface GigabitEthernet1/1/1 < New 24P Switch
description *** ***
switchport mode trunk
Interface GigabitEthernet 1/0/1
switchport access vlan 99
spanning tree portfast
etc
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2017 11:17 AM
trunk between sw1 -- sw2 ---sw3 already there
1/1/1 is downlink for new switch in sw3 ..
1/0/1 is up link in new switch , yes correct
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2017 11:23 AM
Hello,
if you successfully manage to trunk the new VLAN to the 3750x, yes, create a VLAN 99 interface on the 3750x. You then need to policy route traffic for the VLAN out the new connection. The entire setup is actually fairly easy to achieve.
If you post the configuration of the 3750x, we can add the necessary bits and pieces...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2017 12:17 PM - edited 10-19-2017 12:18 PM
will shortly
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2017 01:14 PM - edited 10-19-2017 01:27 PM
This is the head end switch. The other two are similar, each has gig modules with atleast two gbics available for fiber. Thank you guys for being patient, I appreciate it.
no service pad
service tcp-keepalives-in
service tcp-keepalives-out
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname 3750X
!
boot-start-marker
boot-end-marker
!
!
enable secret 5
enable password 7
!
username
username
aaa new-model
!
!
aaa authentication login default group tacacs+ local enable
aaa authorization exec default group tacacs+ local if-authenticated
aaa authorization commands 15 default group tacacs+ local
aaa accounting exec default start-stop group tacacs+
!
!
!
!
!
aaa session-id common
clock timezone MST7 -7 0
switch 1 provision ws-c3750x-48p
system mtu routing 1500
ip routing
no ip gratuitous-arps
!
ip dhcp bootp ignore
ip dhcp excluded-address etc
!
ip dhcp pool
network ******* *******
dns-server ******* *******
domain-name *******
netbios-name-server ******* *******
netbios-node-type h-node
default-router *******
option 156 ascii ftpservers=*******,country=1,language=1,layer2tagging=1,vlanid=3
!
ip dhcp pool camera
network ******* 255.255.255.0
dns-server ******* *******
domain-name *******
netbios-name-server ******* *******
netbios-node-type h-node
default-router *******
!
ip dhcp pool *******
network ******* 255.255.255.0
domain-name *******
option 4 ip *******
option 156 ascii ftpservers=*******,country=1,language=1,layer2tagging=1,vlanid=3
dns-server ******* *******
default-router *******
!
ip dhcp pool *******
network ******* 255.255.255.0
dns-server ******* *******
domain-name *******
netbios-name-server ******* 1*******
netbios-node-type h-node
default-router *******
!
!
no ip domain-lookup
ip domain-name *******
ip multicast-routing distributed
ip multicast cache-headers
ip multicast multipath
login block-for 20 attempts 2 within 30
login delay 2
login on-failure log
login on-success log
!
mls qos map policed-dscp 0 10 18 24 46 to 8
mls qos map cos-dscp 0 8 16 24 32 46 48 56
mls qos srr-queue input bandwidth 70 30
mls qos srr-queue input threshold 1 80 90
mls qos srr-queue input priority-queue 2 bandwidth 30
mls qos srr-queue input cos-map queue 1 threshold 2 3
mls qos srr-queue input cos-map queue 1 threshold 3 6 7
mls qos srr-queue input cos-map queue 2 threshold 1 4
mls qos srr-queue input dscp-map queue 1 threshold 2 24
mls qos srr-queue input dscp-map queue 1 threshold 3 48 49 50 51 52 53 54 55
mls qos srr-queue input dscp-map queue 1 threshold 3 56 57 58 59 60 61 62 63
mls qos srr-queue input dscp-map queue 2 threshold 3 32 33 40 41 42 43 44 45
mls qos srr-queue input dscp-map queue 2 threshold 3 46 47
mls qos srr-queue output cos-map queue 1 threshold 3 4 5
mls qos srr-queue output cos-map queue 2 threshold 1 2
mls qos srr-queue output cos-map queue 2 threshold 2 3
mls qos srr-queue output cos-map queue 2 threshold 3 6 7
mls qos srr-queue output cos-map queue 3 threshold 3 0
mls qos srr-queue output cos-map queue 4 threshold 3 1
mls qos srr-queue output dscp-map queue 1 threshold 3 32 33 40 41 42 43 44 45
mls qos srr-queue output dscp-map queue 1 threshold 3 46 47
mls qos srr-queue output dscp-map queue 2 threshold 1 16 17 18 19 20 21 22 23
mls qos srr-queue output dscp-map queue 2 threshold 1 26 27 28 29 30 31 34 35
mls qos srr-queue output dscp-map queue 2 threshold 1 36 37 38 39
mls qos srr-queue output dscp-map queue 2 threshold 2 24
mls qos srr-queue output dscp-map queue 2 threshold 3 48 49 50 51 52 53 54 55
mls qos srr-queue output dscp-map queue 2 threshold 3 56 57 58 59 60 61 62 63
mls qos srr-queue output dscp-map queue 3 threshold 3 0 1 2 3 4 5 6 7
mls qos srr-queue output dscp-map queue 4 threshold 1 8 9 11 13 15
mls qos srr-queue output dscp-map queue 4 threshold 2 10 12 14
mls qos queue-set output 1 threshold 1 100 100 50 200
mls qos queue-set output 1 threshold 2 125 125 100 400
mls qos queue-set output 1 threshold 3 100 100 100 400
mls qos queue-set output 1 threshold 4 60 150 50 200
mls qos queue-set output 1 buffers 15 25 40 20
mls qos
!
crypto pki trustpoint TP-self-signed-902053632
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-902053632
revocation-check none
rsakeypair TP-self-signed-902053632
!
!
crypto pki certificate chain TP-self-signed-902053632
certificate self-signed 01 nvram:IOS-Self-Sig#1.cer
license boot level ipservices
spanning-tree mode pvst
spanning-tree extend system-id
auto qos srnd4
!
!
!
!
vlan internal allocation policy ascending
!
ip ssh authentication-retries 4
!
class-map match-all AUTOQOS_VOIP_DATA_CLASS
match ip dscp ef
class-map match-all AUTOQOS_DEFAULT_CLASS
match access-group name AUTOQOS-ACL-DEFAULT
class-map match-all AUTOQOS_VOIP_SIGNAL_CLASS
match ip dscp cs3
!
policy-map AUTOQOS-SRND4-CISCOPHONE-POLICY
class AUTOQOS_VOIP_DATA_CLASS
set dscp ef
police 128000 8000 exceed-action policed-dscp-transmit
class AUTOQOS_VOIP_SIGNAL_CLASS
set dscp cs3
police 32000 8000 exceed-action policed-dscp-transmit
class AUTOQOS_DEFAULT_CLASS
set dscp default
police 10000000 8000 exceed-action policed-dscp-transmit
!
!
!
!
!
!
!
interface FastEthernet0
no ip address
no ip route-cache cef
no ip route-cache
shutdown
!
interface GigabitEthernet1/0/1
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/2
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/3
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/4
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/5
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/6
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/7
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/8
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/9
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/10
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/11
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/12
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/13
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/14
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/15
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/16
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/17
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/18
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/19
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/20
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/21
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/22
switchport mode access
switchport voice vlan 2
srr-queue bandwidth share 1 30 35 5
srr-queue bandwidth shape 10 0 0 0
priority-queue out
mls qos trust device cisco-phone
mls qos trust cos
auto qos voip cisco-phone
spanning-tree portfast
service-policy input AUTOQOS-SRND4-CISCOPHONE-POLICY
!
interface GigabitEthernet1/0/23
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/24
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/25
switchport mode access
switchport voice vlan 3
power inline never
spanning-tree portfast
!
interface GigabitEthernet1/0/26
switchport mode access
switchport voice vlan 3
power inline never
spanning-tree portfast
!
interface GigabitEthernet1/0/27
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/28
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/29
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/30
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/31
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/32
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/33
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/34
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/35
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/36
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/37
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/38
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/39
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/40
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/41
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/42
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/43
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/44
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/45
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/46
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/47
switchport mode access
switchport voice vlan 3
spanning-tree portfast
!
interface GigabitEthernet1/0/48
no switchport
bandwidth 100000
ip address ******* 255.255.255.0
ip pim sparse-dense-mode
srr-queue bandwidth share 1 30 35 5
srr-queue bandwidth shape 10 0 0 0
priority-queue out
mls qos trust cos
auto qos trust
!
interface GigabitEthernet1/1/1
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet1/1/2
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet1/1/3
switchport trunk encapsulation dot1q
switchport mode trunk
shutdown
!
interface GigabitEthernet1/1/4
switchport trunk encapsulation dot1q
switchport mode trunk
shutdown
!
interface TenGigabitEthernet1/1/1
shutdown
!
interface TenGigabitEthernet1/1/2
shutdown
!
interface Vlan1
ip address ******* 255.255.255.0
!
interface Vlan2
description cisco
ip address ******* 255.255.255.0
!
interface Vlan3
ip address ******* 255.255.255.0
!
interface Vlan4
description *******
ip address ******* 255.255.255.0
!
interface Vlan70
description *******
ip address ******* 255.255.255.0
ip pim sparse-dense-mode
!
interface Vlan80
description timeclock
ip address ******* 255.255.255.0
!
!
router eigrp 24
network *******
network *******
network *******
network *******
passive-interface default
no passive-interface Vlan1
no passive-interface Vlan2
no passive-interface Vlan3
no passive-interface Vlan4
no passive-interface GigabitEthernet1/1/1
no passive-interface GigabitEthernet1/1/2
no passive-interface GigabitEthernet1/1/3
no passive-interface GigabitEthernet1/1/4
no passive-interface Vlan70
no passive-interface Vlan80
no passive-interface GigabitEthernet1/0/48
eigrp stub connected summary
!
ip default-gateway *******
!
no ip http server
ip http secure-server
!
!
!
logging esm config
logging trap debugging
logging *******
logging *******
!
snmp-server community *******
snmp-server location *******
snmp-server contact *******
tacacs-server host *******
tacacs-server key 7 *******
!
!
!
banner motd ^CC
***************************************************************************
* L E G A L N O T I C E -- Y O U M U S T R E A D *
***************************************************************************
* *
* You must have explicit permission to access or configure this *
* device. All activities performed on this device are logged and *
* violations of this policy may result in criminal prosecution. *
* *
***************************************************************************
* *
* This system is for the use of authorized users only. Individuals using *
* this computer system without authority, or in excess of their authority,*
* are subject to having all of their activities on this system monitored *
* and recorded by system personnel. *
* *
* *
* *
* Anyone using this system expressly consents to such monitoring and is *
* advised that if such monitoring reveals possible evidence of criminal *
* activity, system personnel may provide the evidence of such monitoring *
* *
***************************************************************************
* UNAUTHORIZED ACCESS TO THIS NETWORK DEVICE IS PROHIBITED *
***************************************************************************^C
!
line con 0
privilege level 15
password 7 07242E6741191C091B1B595E
logging synchronous
line vty 0 4
exec-timeout 2 0
privilege level 15
password 7 080A43650609001B1E025E56
logging synchronous
length 0
transport input ssh
line vty 5 15
exec-timeout 2 0
privilege level 15
password 7 080A43650609001B1E025E56
logging synchronous
length 0
transport input ssh
!
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2017 03:09 PM
Hello,
is this switch already connected to a primary ISP ? I am just asking because I do not see any NAT configuration.
Either way, here is the rudimentary approach. I assume that the new Vlan is 99, and the IP address space used is 192.168.1.0/24. The extended access list used in the route map denies all traffic that goes to the other Vlans, which means you have to add the correct addresses and probably have to add more lines, since you have more Vlans).
access-list extended VLAN99 deny ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
access-list extended VLAN99 deny ip 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255
access-list extended VLAN99 permit ip 192.168.1.0 0.0.0.255 any
access-list 99 permit 192.168.1.0 0.0.0.255
route-map VLAN99_TO_ISP2
match ip address VLAN99
set ip next-hop x.x.x.x
interface Vlan99
ip address 192.168.1.1 255.255.255.0
ip policy route-map VLAN99_TO_ISP2
ip nat inside source list 99 interface GigabitEthernetx/x overload
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2017 04:37 PM
So assuming these addresses below apply to the following vlans
Vlan 1 172.24.211.1
Vlan 2 10.50.211.1
Vlan 3 10.100.211.1
Vlan 4 10.200.211.1
Vlan 70 10.80.211.1
Vlan 80 100.80.211.1
Vlan 99 172.25.211.1
access-list extended VLAN99 deny ip 172.24.0.0 0.0.0.255
access-list extended VLAN99 deny ip 10.0.0.0 0.0.0.255
access-list extended VLAN99 permit ip 172.25.0.0 0.0.0.255 any
access-list 99 permit 172.25.0.0 0.0.0.255
route-map VLAN99_TO_ISP2
match ip address VLAN99
set ip next-hop x.x.x.x
interface Vlan99
ip address 172.25.211.1 255.255.255.0
ip policy route-map VLAN99_TO_ISP2
ip nat inside source list 99 interface GigabitEthernet1/1 overload
what is best practice to segregate all that other traffic in their own ACL's? create another list with permit any any? Thank you for being so helpful, I will mark this answered and figure out the rest. My environment is kind of tough to test in, as all of the gear is live, I have no dual connections anywhere, and we cant afford training. So I do appreciate you going out of your way, this is my first time on the site, and I'm blown away by the help people offer others.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide