- Cisco Community
- Technology and Support
- Networking
- Routing
- Inside - Inside NATting
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Inside - Inside NATting
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2020 12:10 PM - edited 12-28-2020 01:21 PM
Hello everyone.
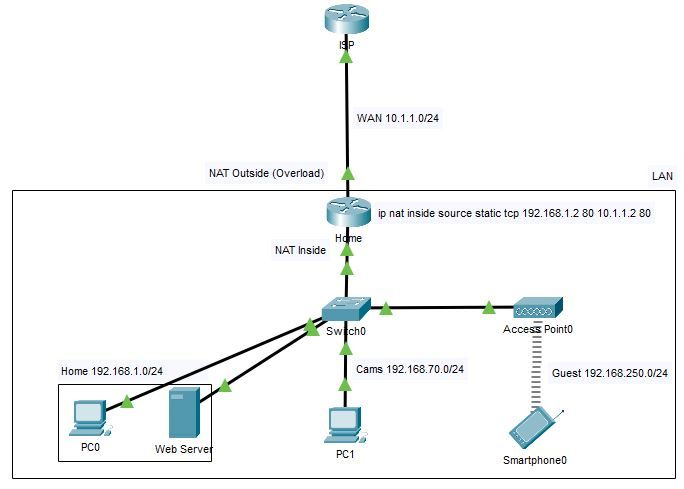
The image below is a simplified layout of my home network where I have a web server with port forwarding. From the WAN the server is accessible, and from the LAN it is through its LAN IP, as expected. The question is, how to make the server accessible from all 3 networks on the LAN through the public IP? Note that I'm using ZBF with each network on a separate zone and the required policies to allow specific interzone traffic.
This has proven surprisingly convoluted to pull off. I tried domainless NAT changing all 3 subtinterfaces and the WAN interface to ip nat enable with different combinations of no ip redirects, changing static NAT entries to ip nat source and clearing the NAT translation table, but all results in losing access to the internet; despite the router (ISR 1941 on IOS 15.8) showing NVI translations being made.
Running config attached.
- Labels:
-
Routing Protocols
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2021 12:33 PM
Hello Georg.
The self zone is implicit, that's why you don't see zone security self.
I need policies between the self zone and others to allow specific traffic destined to the router (DHCP from ISP for the WAN int, ping the default gateway from inside networks, etc). When I tested the loopback technique I only removed a couple of test interfaces from the ZBF. Most likely I'd have to move all interfaces out the ZBF and/or delete firewall zones. I've read that this can work with the ZBF but some ACL magic is needed.
For now I'll content myself with split DNS and if later I'm forced to do hairpining I'll get an ASA or hopefully Cisco will have fixed the bug.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2020 04:28 PM
Hello @tresdodi
i seem to be having editing issues with my csc mobile app -
keeping with the hairpin @Georg Pauwen suggested and with zbfw enabled you would need to add the loopback interface to a security zone and create the necessary zone pairing
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2021 05:11 AM
@tresdodi wrote:
Switching to NVI and taking the interfaces out of the Zone-Based Firewall (leaving URPF on) does the trick. I have Internet and NAT hairpinning works. I prefer this solution over the Loopback interface because it's much simpler. But I need ZBF and there's a bug in the interoperability of NVI and ZBF. When a policy is applied to the outside -> self zone pair, ZBF drops traffic returning to the self zone (the public IP). I confirmed that the bug occurs for me as described by many others. There are conflicting reports of this working fine on some IOS releases. The workarounds are stop using ZBF or pass traffic between outside and self zones, which are a no-go.
The loopback technique for some reason didn't work for me even without the ZBF. It must be something that I'm missing but I didn't dig deeper.
Regardless, I decided to use split DNS and put an ASA between the ISP modem and the router later if needed.
Thank you you both for your help!
Excellent - good to know glad you got it sorted, thanks for the feedback
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide