- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: ISR4321 - adding second S2S VPN, phase 2 not coming up
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISR4321 - adding second S2S VPN, phase 2 not coming up
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2019 10:29 PM
I have a 4321 ver. 15.5 that has a certificate authentication IKEv2 site to site tunnel setup to an ASA. This tunnel is working fine.
I am adding a second S2S tunnel to a Cisco RV340 router. Phase 1 is coming up OK, but phase 2 never establishes. The RV340 thinks that everything is fine and the phase 2 is up, but the ISR does not.
Config:
Current configuration : 9407 bytes
!
! Last configuration change at 00:16:41 CDT Thu May 23 2019 by user
!
version 15.5
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
no platform punt-keepalive disable-kernel-core
platform hardware throughput level 100000
!
hostname 4321-pLAN9-co
!
boot-start-marker
boot-end-marker
!
!
vrf definition Mgmt-intf
!
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
!
enable secret 5 xxxxx
!
aaa new-model
!
!
aaa authentication login default local
!
!
!
!
!
!
aaa session-id common
clock timezone CDT -5 0
clock summer-time CDT recurring 1 Sun Nov 2:00 2 Sun Mar 2:00
!
!
!
!
!
!
!
!
!
!
!
ip name-server 75.75.75.75
ip dhcp excluded-address 192.168.211.2
!
ip dhcp pool DHCP
network 192.168.211.0 255.255.255.248
default-router 192.168.211.1
dns-server 192.168.211.1
lease 0 0 10
!
!
!
!
!
!
!
!
!
!
subscriber templating
!
multilink bundle-name authenticated
!
!
!
crypto pki trustpoint pLAN9
enrollment terminal
fqdn none
subject-name CN=4321.pLAN9.co
revocation-check none
rsakeypair MAINRSA
!
!
!
crypto pki certificate map CERTMAP 10
issuer-name co = CA_COMMON_NAME
!
crypto pki certificate chain pLAN9
certificate 00CF75E3A8D2772F2D
xxxxxxxxxxxxxxxxxxxxxx
quit
certificate ca 00A64BD6B54544EEC6
xxxxxxxxxxxxxxxxxxxxx
quit
license udi pid ISR4321/K9 sn FDO21032NET
!
spanning-tree extend system-id
!
username user password 7 xxxxxx
!
redundancy
mode none
!
crypto ikev2 proposal aes256-sha1
encryption aes-cbc-256
integrity sha1
group 5
!
crypto ikev2 policy policy
proposal aes256-sha1
!
!
crypto ikev2 profile ASA
match certificate CERTMAP
identity local dn
authentication local rsa-sig
authentication remote rsa-sig
pki trustpoint pLAN9
lifetime 28800
!
no crypto ikev2 http-url cert
!
!
vlan internal allocation policy ascending
no cdp run
!
!
class-map type inspect match-any ALL
match protocol tcp
match protocol udp
match protocol icmp
class-map type inspect match-any EXPOSED
match access-group name EXPOSED
!
policy-map type inspect OUT_IN_POL
class type inspect EXPOSED
inspect
class class-default
drop log
policy-map type inspect SELF_OUT_POL
class type inspect ALL
inspect
class class-default
drop log
policy-map type inspect IN_OUT_POL
class type inspect ALL
inspect
class class-default
drop log
policy-map type inspect OUT_SELF_POL
class type inspect EXPOSED
inspect
class class-default
drop log
!
zone security INSIDE
zone security OUTSIDE
zone-pair security IN_OUT_ZONE source INSIDE destination OUTSIDE
service-policy type inspect IN_OUT_POL
zone-pair security OUT_IN_ZONE source OUTSIDE destination INSIDE
service-policy type inspect OUT_IN_POL
zone-pair security OUT_SELF_ZONE source OUTSIDE destination self
service-policy type inspect OUT_SELF_POL
zone-pair security SELF_OUT_ZONE source self destination OUTSIDE
service-policy type inspect SELF_OUT_POL
!
!
!
!
!
crypto isakmp identity dn
!
!
crypto ipsec transform-set aes256-sha1 esp-aes 256 esp-sha-hmac
mode tunnel
!
!
crypto ipsec profile profile
set transform-set aes256-sha1
set ikev2-profile ASA
!
!
crypto map MAP 10 ipsec-isakmp
set peer ASA_WAN_IP
set security-association lifetime kilobytes disable
set security-association lifetime seconds 28800
set transform-set aes256-sha1
set pfs group5
set ikev2-profile ASA
match address VPN_1176
crypto map MAP 20 ipsec-isakmp
set peer RV340_WAN_IP
set security-association lifetime kilobytes disable
set security-association lifetime seconds 28800
set transform-set aes256-sha1
set pfs group5
set ikev2-profile ASA
match address VPN_340
!
!
!
!
!
!
!
!
!
!
!
!
interface GigabitEthernet0/0/0
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet0/0/1
ip address ISR4321_WAN_IP 255.255.255.248
ip nat outside
zone-member security OUTSIDE
negotiation auto
crypto map MAP
!
interface GigabitEthernet0/1/0
switchport access vlan 20
switchport mode access
spanning-tree bpdufilter enable
!
interface GigabitEthernet0/1/1
switchport access vlan 20
switchport mode access
spanning-tree bpdufilter enable
!
interface GigabitEthernet0/1/2
switchport access vlan 20
switchport mode access
spanning-tree bpdufilter enable
!
interface GigabitEthernet0/1/3
switchport access vlan 20
switchport mode access
spanning-tree bpdufilter enable
!
interface GigabitEthernet0
vrf forwarding Mgmt-intf
no ip address
shutdown
negotiation auto
!
interface Vlan1
no ip address
shutdown
!
interface Vlan20
ip address 192.168.211.1 255.255.255.248
ip nat inside
zone-member security INSIDE
!
ip nat inside source list NAT interface GigabitEthernet0/0/1 overload
ip forward-protocol nd
no ip http server
no ip http secure-server
ip tftp source-interface GigabitEthernet0
ip dns server
ip route 0.0.0.0 0.0.0.0 DEFAULT_GATEWAY
ip route 192.168.34.0 255.255.255.240 RV340_WAN_IP
ip route 192.168.222.0 255.255.255.224 ASA_WAN_IP
ip ssh source-interface Vlan20
!
!
ip access-list extended EXPOSED
permit icmp any any
permit udp any any eq isakmp
permit udp any any eq non500-isakmp
permit esp any any
permit ip 192.168.222.0 0.0.0.31 any
permit ip 192.168.211.8 0.0.0.7 any
permit ip 192.168.34.0 0.0.0.15 any
ip access-list extended NAT
deny ip 192.168.211.0 0.0.0.15 192.168.34.0 0.0.0.15
deny ip 192.168.211.0 0.0.0.7 192.168.211.8 0.0.0.7
deny ip 192.168.211.0 0.0.0.15 192.168.222.0 0.0.0.31
permit ip 192.168.211.0 0.0.0.15 any
ip access-list extended VPN_1176
permit ip 192.168.211.0 0.0.0.15 192.168.222.0 0.0.0.31
ip access-list extended VPN_340
permit ip 192.168.211.0 0.0.0.15 192.168.34.0 0.0.0.15
!
!
!
!
!
!
control-plane
!
!
line con 0
stopbits 1
line aux 0
stopbits 1
line vty 0 4
transport input ssh
!
!
enddebug output during failure:
*May 23 05:27:12.293: IKEv2-INTERNAL:New ikev2 sa request admitted
*May 23 05:27:12.293: IKEv2-INTERNAL:Incrementing incoming negotiating sa count by one
*May 23 05:27:12.293: IKEv2-PAK:Next payload: SA, version: 2.0 Exchange type: IKE_SA_INIT, flags: INITIATOR Message id: 0, length: 596
Payload contents:
SA Next payload: KE, reserved: 0x0, length: 244
last proposal: 0x2, reserved: 0x0, length: 44
Proposal: 1, Protocol id: IKE, SPI size: 0, #trans: 4 last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA96
last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA1
last transform: 0x0, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_1536_MODP/Group 5
last proposal: 0x0, reserved: 0x0, length: 196
Proposal: 2, Protocol id: IKE, SPI size: 0, #trans: 22 last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
last transform: 0x3, reserved: 0x0: length: 8
type: 1, reserved: 0x0, id: 3DES
last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA256
last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA384
last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA512
last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: AES XCBC 96
last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA96
last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: MD596
last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: AES CBC
last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA256
last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA384
last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA512
last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA1
last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: MD5
last transform: 0x3, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_3072_MODP/Group 15
last transform: 0x3, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_4096_MODP/Group 16
last transform: 0x3, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: Unknown - 18
last transform: 0x3, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_2048_MODP/Group 14
last transform: 0x3, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_2048_256_MODP/Group 24
last transform: 0x0, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_1024_MODP/Group 2
KE Next payload: N, reserved: 0x0, length: 200
DH group: 5, Reserved: 0x0
N Next payload: NOTIFY, reserved: 0x0, length: 36
*May 23 05:27:12.294: IKEv2-INTERNAL:Parse Notify Payload: NAT_DETECTION_SOURCE_IP NOTIFY(NAT_DETECTION_SOURCE_IP) Next payload: NOTIFY, reserved: 0x0, length: 28
Security protocol id: Unknown - 0, spi size: 0, type: NAT_DETECTION_SOURCE_IP
*May 23 05:27:12.294: IKEv2-INTERNAL:Parse Notify Payload: NAT_DETECTION_DESTINATION_IP NOTIFY(NAT_DETECTION_DESTINATION_IP) Next payload: NOTIFY, reserved: 0x0, length: 28
Security protocol id: Unknown - 0, spi size: 0, type: NAT_DETECTION_DESTINATION_IP
*May 23 05:27:12.294: IKEv2-INTERNAL:Parse Notify Payload: IKEV2_FRAGMENTATION_SUPPORTED NOTIFY(IKEV2_FRAGMENTATION_SUPPORTED) Next payload: NOTIFY, reserved: 0x0, length: 8
Security protocol id: Unknown - 0, spi size: 0, type: IKEV2_FRAGMENTATION_SUPPORTED
*May 23 05:27:12.294: IKEv2-INTERNAL:Parse Notify Payload: Unknown - 16431 NOTIFY(Unknown - 16431) Next payload: NOTIFY, reserved: 0x0, length: 16
Security protocol id: Unknown - 0, spi size: 0, type: Unknown - 0
*May 23 05:27:12.294: IKEv2-INTERNAL:Parse Notify Payload: REDIRECT_SUPPORTED NOTIFY(REDIRECT_SUPPORTED) Next payload: NONE, reserved: 0x0, length: 8
Security protocol id: Unknown - 0, spi size: 0, type: REDIRECT_SUPPORTED
*May 23 05:27:12.294: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 0 CurState: IDLE Event: EV_RECV_INIT
*May 23 05:27:12.294: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 0 CurState: R_INIT Event: EV_VERIFY_MSG
*May 23 05:27:12.294: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 0 CurState: R_INIT Event: EV_INSERT_SA
*May 23 05:27:12.294: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 0 CurState: R_INIT Event: EV_GET_IKE_POLICY
*May 23 05:27:12.294: IKEv2-INTERNAL:Adding Proposal aes256-sha1 to toolkit policy
*May 23 05:27:12.295: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 0 CurState: R_INIT Event: EV_PROC_MSG
*May 23 05:27:12.295: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 0 CurState: R_INIT Event: EV_DETECT_NAT
*May 23 05:27:12.295: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):Process NAT discovery notify
*May 23 05:27:12.295: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):Processing nat detect src notify
*May 23 05:27:12.295: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):Remote address matched
*May 23 05:27:12.295: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):Processing nat detect dst notify
*May 23 05:27:12.295: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):Local address matched
*May 23 05:27:12.295: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):No NAT found
*May 23 05:27:12.295: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 0 CurState: R_INIT Event: EV_CHK_CONFIG_MODE
*May 23 05:27:12.295: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 0 CurState: R_BLD_INIT Event: EV_SET_POLICY
*May 23 05:27:12.295: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):Setting configured policies
*May 23 05:27:12.295: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 0 CurState: R_BLD_INIT Event: EV_CHK_AUTH4PKI
*May 23 05:27:12.295: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 0 CurState: R_BLD_INIT Event: EV_PKI_SESH_OPEN
*May 23 05:27:12.295: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):Opening a PKI session
*May 23 05:27:12.295: CRYPTO_PKI: (9000F) Session started - identity not specified
*May 23 05:27:12.295: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 0 CurState: R_BLD_INIT Event: EV_GEN_DH_KEY
*May 23 05:27:12.304: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 0 CurState: R_BLD_INIT Event: EV_NO_EVENT
*May 23 05:27:12.304: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 0 CurState: R_BLD_INIT Event: EV_OK_RECD_DH_PUBKEY_RESP
*May 23 05:27:12.304: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):Action: Action_Null
*May 23 05:27:12.304: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 0 CurState: R_BLD_INIT Event: EV_GEN_DH_SECRET
*May 23 05:27:12.314: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 0 CurState: R_BLD_INIT Event: EV_NO_EVENT
*May 23 05:27:12.314: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 0 CurState: R_BLD_INIT Event: EV_OK_RECD_DH_SECRET_RESP
*May 23 05:27:12.314: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):Action: Action_Null
*May 23 05:27:12.314: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 0 CurState: R_BLD_INIT Event: EV_GEN_SKEYID
*May 23 05:27:12.314: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):Generate skeyid
*May 23 05:27:12.314: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 0 CurState: R_BLD_INIT Event: EV_GET_CONFIG_MODE
*May 23 05:27:12.314: IKEv2-INTERNAL:No config data to send to toolkit:
*May 23 05:27:12.314: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 0 CurState: R_BLD_INIT Event: EV_BLD_MSG
*May 23 05:27:12.314: IKEv2-INTERNAL:Construct Vendor Specific Payload: DELETE-REASON
*May 23 05:27:12.314: IKEv2-INTERNAL:Construct Vendor Specific Payload: (CUSTOM)
*May 23 05:27:12.314: IKEv2-INTERNAL:Construct Notify Payload: NAT_DETECTION_SOURCE_IP
*May 23 05:27:12.314: IKEv2-INTERNAL:Construct Notify Payload: NAT_DETECTION_DESTINATION_IP
*May 23 05:27:12.314: IKEv2-PAK:(SESSION ID = 6,SA ID = 2):Next payload: SA, version: 2.0 Exchange type: IKE_SA_INIT, flags: RESPONDER MSG-RESPONSE Message id: 0, length: 437
Payload contents:
SA Next payload: KE, reserved: 0x0, length: 48
last proposal: 0x0, reserved: 0x0, length: 44
Proposal: 1, Protocol id: IKE, SPI size: 0, #trans: 4 last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA1
last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA96
last transform: 0x0, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_1536_MODP/Group 5
KE Next payload: N, reserved: 0x0, length: 200
DH group: 5, Reserved: 0x0
N Next payload: VID, reserved: 0x0, length: 36
VID Next payload: VID, reserved: 0x0, length: 23
VID Next payload: NOTIFY, reserved: 0x0, length: 21
NOTIFY(NAT_DETECTION_SOURCE_IP) Next payload: NOTIFY, reserved: 0x0, length: 28
Security protocol id: Unknown - 0, spi size: 0, type: NAT_DETECTION_SOURCE_IP
NOTIFY(NAT_DETECTION_DESTINATION_IP) Next payload: CERTREQ, reserved: 0x0, length: 28
Security protocol id: Unknown - 0, spi size: 0, type: NAT_DETECTION_DESTINATION_IP
CERTREQ Next payload: NONE, reserved: 0x0, length: 25
Cert encoding X.509 Certificate - signature
*May 23 05:27:12.315: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 0 CurState: INIT_DONE Event: EV_DONE
*May 23 05:27:12.315: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 0 CurState: INIT_DONE Event: EV_CHK4_ROLE
*May 23 05:27:12.315: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 0 CurState: INIT_DONE Event: EV_START_TMR
*May 23 05:27:12.315: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 0 CurState: R_WAIT_AUTH Event: EV_NO_EVENT
*May 23 05:27:12.485: IKEv2-INTERNAL:Got a packet from dispatcher
*May 23 05:27:12.485: IKEv2-INTERNAL:Processing an item off the pak queue
*May 23 05:27:12.485: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):Request has mess_id 1; expected 1 through 1
*May 23 05:27:12.485: IKEv2-PAK:(SESSION ID = 6,SA ID = 2):Next payload: ENCR, version: 2.0 Exchange type: IKE_AUTH, flags: INITIATOR Message id: 1, length: 1324
Payload contents:
IDi Next payload: CERT, reserved: 0x0, length: 67
Id type: DER ASN1 DN, Reserved: 0x0 0x0
CERT Next payload: CERTREQ, reserved: 0x0, length: 771
Cert encoding X.509 Certificate - signature
CERTREQ Next payload: IDr, reserved: 0x0, length: 25
Cert encoding X.509 Certificate - signature
IDr Next payload: AUTH, reserved: 0x0, length: 34
Id type: DER ASN1 DN, Reserved: 0x0 0x0
AUTH Next payload: SA, reserved: 0x0, length: 264
Auth method RSA, reserved: 0x0, reserved 0x0
SA Next payload: TSi, reserved: 0x0, length: 44
last proposal: 0x0, reserved: 0x0, length: 40
Proposal: 1, Protocol id: ESP, SPI size: 4, #trans: 3 last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA96
last transform: 0x0, reserved: 0x0: length: 8
type: 5, reserved: 0x0, id: Don't use ESN
TSi Next payload: TSr, reserved: 0x0, length: 24
Num of TSs: 1, reserved 0x0, reserved 0x0
TS type: TS_IPV4_ADDR_RANGE, proto id: 0, length: 16
start port: 0, end port: 65535
start addr: 192.168.34.0, end addr: 192.168.34.15
TSr Next payload: NOTIFY, reserved: 0x0, length: 24
Num of TSs: 1, reserved 0x0, reserved 0x0
TS type: TS_IPV4_ADDR_RANGE, proto id: 0, length: 16
start port: 0, end port: 65535
start addr: 192.168.211.0, end addr: 192.168.211.15
*May 23 05:27:12.486: IKEv2-INTERNAL:Parse Notify Payload: Unknown - 16417 NOTIFY(Unknown - 16417) Next payload: NONE, reserved: 0x0, length: 8
Security protocol id: Unknown - 0, spi size: 0, type: Unknown - 0
*May 23 05:27:12.486: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 1 CurState: R_WAIT_AUTH Event: EV_RECV_AUTH
*May 23 05:27:12.486: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 1 CurState: R_WAIT_AUTH Event: EV_CHK_NAT_T
*May 23 05:27:12.486: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 1 CurState: R_WAIT_AUTH Event: EV_PROC_ID
*May 23 05:27:12.486: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):Received valid parameteres in process id
*May 23 05:27:12.491: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 1 CurState: AUTH_DONE Event: EV_FAIL
*May 23 05:27:12.491: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 1 CurState: EXIT Event: EV_ABORT
*May 23 05:27:12.491: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 1 CurState: EXIT Event: EV_CHK_PENDING_ABORT
*May 23 05:27:12.491: IKEv2-INTERNAL:Negotiating SA request deleted
*May 23 05:27:12.491: IKEv2-INTERNAL:Decrement count for incoming negotiating
*May 23 05:27:12.492: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 1 CurState: EXIT Event: EV_CHK_GKM
*May 23 05:27:12.492: IKEv2-INTERNAL:(SESSION ID = 6,SA ID = 2):SM Trace-> SA: I_SPI=0E4072C2DD4A6542 R_SPI=7F99B96F1A6D2949 (R) MsgID = 1 CurState: EXIT Event: EV_UPDATE_CAC_STATS
*May 23 05:27:12.492: CRYPTO_PKI: Rcvd request to end PKI session 9000F.
*May 23 05:27:12.492: CRYPTO_PKI: PKI session 9000F has ended. Freeing all resources.
*May 23 05:27:14.201: [] -> [ACL VPN_340]: message ACL notify RP
*May 23 05:27:14.201: [ACL VPN_340]: message = ACL notify RP
*May 23 05:27:14.201: [ACL VPN_340]: state = ACL notify RP action
*May 23 05:27:14.201: IPSEC:(SESSION ID = 1) (MESSAGE) crypto_ipsec_construct_sa_request request already in progress
*May 23 05:27:15.477: IKEv2-INTERNAL:Got a packet from dispatcher
*May 23 05:27:15.478: IKEv2-INTERNAL:Processing an item off the pak queue
*May 23 05:27:15.480: IKEv2-INTERNAL:Couldn't find matching SA
*May 23 05:27:15.480: IKEv2-PAK:(SESSION ID = 0,SA ID = 0):Next payload: ENCR, version: 2.0 Exchange type: INFORMATIONAL, flags: RESPONDER Message id: 0, length: 76
*May 23 05:27:16.487: IKEv2-INTERNAL:Got a packet from dispatcher
*May 23 05:27:16.488: IKEv2-INTERNAL:Processing an item off the pak queue
*May 23 05:27:16.490: IKEv2-INTERNAL:Couldn't find matching SA
*May 23 05:27:16.490: IKEv2-PAK:(SESSION ID = 0,SA ID = 0):Next payload: ENCR, version: 2.0 Exchange type: IKE_AUTH, flags: INITIATOR Message id: 1, length: 1324This log output, besides being horrendously unreadable, shows no useful information as to why the tunnel is failing. In fact, the only failure I see is the line "CurState: AUTH_DONE Event: EV_FAIL", which tells me nothing as to why it failed.
What is going on here?
- Labels:
-
ISR 4000 Series
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2019 12:34 AM
Hello,
assuming that you are running router firmware version 1.0.02.16 (which was released in January, and which is the first to support ikev2), and that obviously the encryption, decryption, and authentication parameters on the RV340 match what you have configured on the ISR, you might want to try a second policy, separate from the policy for the ASA, and use the parameters outlined in the document below:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2019 07:55 PM
@Georg Pauwen wrote:Hello,
assuming that you are running router firmware version 1.0.02.16 (which was released in January, and which is the first to support ikev2), and that obviously the encryption, decryption, and authentication parameters on the RV340 match what you have configured on the ISR, you might want to try a second policy, separate from the policy for the ASA, and use the parameters outlined in the document below:
I am actually running the newest firmware on the RV340 (1.0.03.15). Are you saying that I specifically need to use those encr/hash/DH settings in that document? Or are you just providing that for reference? I can assure you that all settings are duplicated on the RV340 (with obvious mirroring of the subnets on each side).
And when you say "second policy", do you mean a second profile? As in, "crypto ikev2 profile RV340W"? I am intending to use the same policy & proposal for both the ASA and the RV340..... surely this can be done?
Also, when I try to create a new "crypto ikev2 profile" for the RV340, I find that I am also not allowed to use the same certmap.... I would have to duplicate the certmap already in use and name it "CERTMAP2", or something. That doesn't seem right..... All devices are using certs signed by the same CA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2019 12:36 AM - edited 05-24-2019 12:44 AM
Hello train_wreck,
From the log messages of your first post we see:
that there are NAT issues.
Is the RV340 router behind NAT ?
Edit:
your firmware version on RV340 is newer so you should be fine. I don't think you need to downgrade.
About the document provided by Georg.
It may be wise to implement a second IKEv2 profile dedicated to the RV340 and the use of the Phase I and Phase II IKE options reported in the document as to be seen as something tested and validated for interoperability by Cisco.
IF you need to build a second certmap you should give it a try.
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2019 01:11 AM
@Giuseppe Larosa wrote:From the log messages of your first post we see:
that there are NAT issues.
Is the RV340 router behind NAT ?
No, it is not. Both WAN IPs of both devices are within the same /29 (e.g., the ISR is at 50.x.x.3/29 and the RV340 is at 50.x.x.4/29) and are connected to the same VLAN on the same switch.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2019 01:45 AM
Also, I tried adding a second ikev2 profile, with a second certmap and a second ipsec profile linked to the ikev2 profile. This changed nothing. The problem is still there, and the error is still the same ("EV_FAIL").
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-25-2019 12:10 AM - edited 05-25-2019 12:12 AM
I have narrowed this down to a problem with the RV340 router. I have since added 2 more additional crypto map sites to different devices (a Fortigate 30E and a ZyXel USG40), and both work flawlessly, in addition to the original ASA that has remained working the whole time. Only the RV340 has this problem. All devices use certificates that were signed with my internal CA.
My original configuration was mostly correct; I did not have to use IPsec profiles or multiple IKEv2 profiles to accomplish this, and in fact because I was using crypto maps, the ipsec profile was unnecessary. Only 1 IKEv2 profile is used in multiple crypto map entries, and all are configured the same and are working fine (except the RV340).
This will not be the first problem I have had with the RV340, VPN-related or otherwise. Cisco really needs to get out of the "Small Business" VPN router business, it's obvious they don't really care about it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-25-2019 01:55 AM
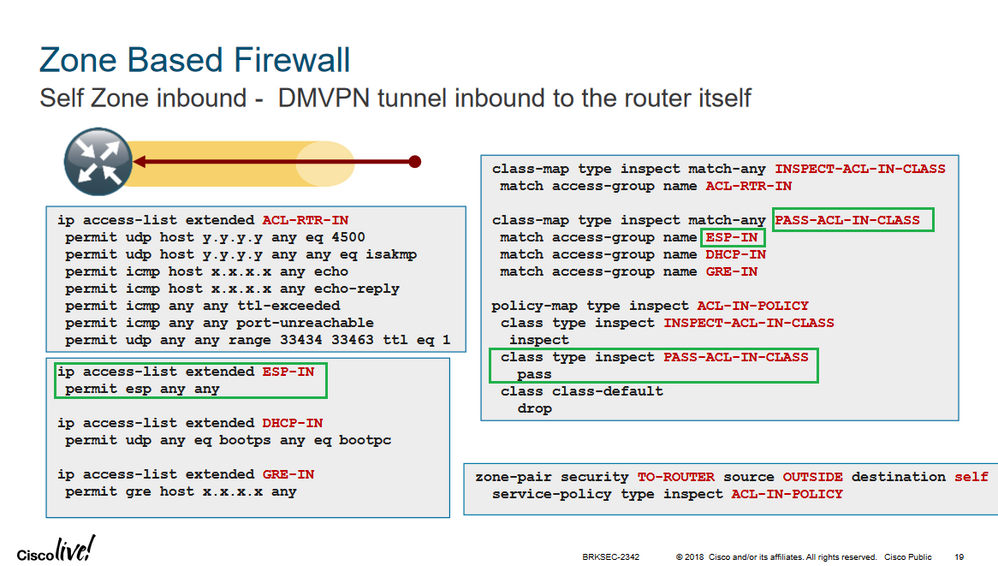
Hi,
ZBFW does not inspect ESP, you need to change the policy-map to "pass".
policy-map type inspect OUT_SELF_POL
class type inspect EXPOSED
pass
HTH
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide