- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Layer 3 routing
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2019 02:29 AM
Hi Hoping someone can advise me.
I have a sonicwall TZ400. Im migrating our network to vlan managed network.
At the moment all devices expect CCTV are on default vlan1.
I have a routing port setup 192.168.120.80 255.255.255.0 Which is connect to port X3 on the sonicwall.
X3 has a ip address of 192.168.120.254 which i can ping form the core switch and from the sonicwall but i cannot can out to the internet through the CCTV vlan. any advice.
The default Sonicwall LAN IP is 192.168.16.254 (X1) i have to keep this for VLAN1.
here are my static routes:
cctv-vlan 192.168.20.0
L3 Switch 192.168.120.80
Core Switch config
no aaa new-model
clock timezone gmt 1
switch 1 provision ws-c3750g-24ps
system mtu routing 1500
ip subnet-zero
ip routing
ip domain-name *****.local
ip name-server 8.8.8.8
no ip dhcp use vrf connected
!
ip dhcp pool Voice
network 192.168.30.0 255.255.255.0
default-router 192.168.30.1
dns-server 8.8.8.8 8.8.4.4
!
!
!
!
crypto pki trustpoint TP-self-signed-1562173568
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-1562173568
revocation-check none
rsakeypair TP-self-signed-1562173568
!
!
crypto pki certificate chain TP-self-signed-1562173568
certificate self-signed 01
3082024D 308201B6 A0030201 02020101 300D0609 2A864886 F70D0101 04050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 31353632 31373335 3638301E 170D3933 30333031 30303034
30325A17 0D323030 31303130 30303030 305A3031 312F302D 06035504 03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D31 35363231
37333536 3830819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281
8100A476 DA036124 20128049 28B4D1E7 607FAC0B 772389D0 A437DA1F 1BB1801A
1807FB3D 7AB1C838 D498724E 16D5C9E1 27549732 E25FEF98 BE773D29 DE622F18
F0CDAD27 2C7FA223 1E549829 158090DE FCAB8A2B 1A5F0C12 94BD29BC 1980C84E
BE330F03 43DD70C1 2C60800C EA1402D0 A487ADF3 4BA34158 C8251FF8 654775B2
C7210203 010001A3 75307330 0F060355 1D130101 FF040530 030101FF 30200603
551D1104 19301782 154F542D 53572D30 352E6F73 74656368 2E6C6F63 616C301F
0603551D 23041830 16801482 7C73A7E6 F7B88868 5BD2C751 E534D7CA 6E5FD930
1D060355 1D0E0416 0414827C 73A7E6F7 B888685B D2C751E5 34D7CA6E 5FD9300D
06092A86 4886F70D 01010405 00038181 000CF7D5 0EE12C41 197D448D BA320CB2
BE2BBEE4 96439390 C28912CD D69641DC 1529C87A 7C06A5E2 16029409 EF503FEB
D74931AD 34949966 C2F2652D 46D376AA 9CCA70FC 32159276 81695E88 D8183FC6
27F3FF30 5C9E652D FB33FF20 1CB6F6C9 30B02F52 F5583A98 479D9FBB D2413863
CE7024E4 CC76BB15 BED39FC7 54E2EFC0 25
quit
!
!
!
!
!
spanning-tree mode pvst
spanning-tree portfast default
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
!
!
!
interface GigabitEthernet1/0/1
switchport access vlan 99
!
interface GigabitEthernet1/0/2
!
interface GigabitEthernet1/0/3
spanning-tree portfast trunk
!
interface GigabitEthernet1/0/4
!
interface GigabitEthernet1/0/5
!
interface GigabitEthernet1/0/6
!
interface GigabitEthernet1/0/7
!
interface GigabitEthernet1/0/8
!
interface GigabitEthernet1/0/9
!
interface GigabitEthernet1/0/10
!
interface GigabitEthernet1/0/11
switchport access vlan 20
!
interface GigabitEthernet1/0/12
!
interface GigabitEthernet1/0/13
switchport access vlan 20
!
interface GigabitEthernet1/0/14
!
interface GigabitEthernet1/0/15
!
interface GigabitEthernet1/0/16
switchport access vlan 20
!
interface GigabitEthernet1/0/17
switchport access vlan 20
!
interface GigabitEthernet1/0/18
switchport access vlan 20
!
interface GigabitEthernet1/0/19
!
interface GigabitEthernet1/0/20
switchport access vlan 20
!
interface GigabitEthernet1/0/21
switchport access vlan 20
!
interface GigabitEthernet1/0/22
switchport access vlan 20
!
interface GigabitEthernet1/0/23
!
interface GigabitEthernet1/0/24
no switchport
ip address 192.168.120.80 255.255.255.0
!
interface GigabitEthernet1/0/25
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 1,10,19-21,30,50,99,100
switchport mode trunk
!
interface GigabitEthernet1/0/26
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 1,10,19-21,30,50,99,100
switchport mode trunk
!
interface GigabitEthernet1/0/27
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 1,10,19-21,30,50,99,100
switchport mode trunk
!
interface GigabitEthernet1/0/28
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 1,10,19-21,30,50,99,100
switchport mode trunk
!
interface Vlan1
ip address 10.1.1.50 255.255.255.0
ip access-group 10 out
no ip route-cache cef
no ip route-cache
no ip mroute-cache
!
interface Vlan20
ip address 192.168.20.1 255.255.255.0
ip access-group 20 out
!
interface Vlan30
ip address 192.168.30.1 255.255.255.0
ip access-group 30 out
!
interface Vlan50
no ip address
!
interface Vlan99
ip address 192.168.99.1 255.255.255.0
ip access-group 99 out
!
interface Vlan100
ip address 192.168.100.1 255.255.255.0
ip access-group 10 out
!
ip default-gateway 192.168.16.254
ip classless
ip route 0.0.0.0 0.0.0.0 192.168.16.254
ip http server
ip http secure-server
!
!
access-list 1 deny 192.168.10.0 0.0.0.255
access-list 20 permit 192.168.18.104
access-list 20 permit 192.168.16.190
access-list 20 permit 192.168.17.190
access-list 20 deny 192.168.16.0 0.0.3.255
access-list 21 deny 192.168.16.0 0.0.3.254
access-list 30 deny 192.168.16.0 0.0.3.255
access-list 30 permit any
access-list 30 deny 192.168.100.0 0.0.0.255
access-list 99 deny 192.168.16.0 0.0.3.254
!
control-plane
!
!
line con 0
exec-timeout 0 0
logging synchronous
login
line vty 0 4
exec-timeout 0 0
password Pa55word
logging synchronous
login local
transport input ssh
line vty 5 15
exec-timeout 0 0
password Pa55word
logging synchronous
login local
transport input ssh
!
end
Core#ping 192.168.120.254
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.120.254, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/8 ms
I
Solved! Go to Solution.
- Labels:
-
LAN Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2019 08:44 AM - edited 04-25-2019 01:03 AM
Hello
So just to confirm you don’t want any other vlans accessing the new cctv vlan but wish the cctv vlan to access internet?
Example:
vlan x 10.10.10.0/24
vlan x 11.11.11.0/24
ip access-list extended cctv-acl
deny ip 10.10.10.0 0.0.0.255 any
deny ip 11.11.11.0 0.0.0.255 any
permit ip any any
in vlan x < cctv vlan>
ip access-group cctv-acl OUT
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2019 02:42 AM
Hi there,
Confirm that the sonicwall is configured to NAT 192.168.20.0/24 to its 'outside' X1 interface (on the 192.168.16.0/24 subnet)
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2019 03:13 AM
If i set the routing port ip address to 192.168.16.80 (which what is was originally) i am able to get internet net access and ping this gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2019 02:53 AM - edited 04-24-2019 02:56 AM
Hello
@Dav1787 wrote:
here are my static routes:
cctv-vlan 192.168.20.0
L3 Switch 192.168.120.80
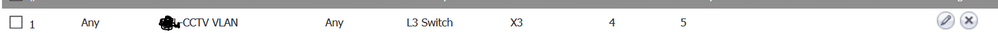
Looks like your ACL applied to vlan 20 is negating access remove it and test connectivity , Can you explain what is the nature of this acl what are you trying to achieve
Lastly - 192.168.120.80 ? I dont see any reference to this subnet anywhere on your core
interface Vlan20
ip address 192.168.20.1 255.255.255.0
ip access-group 20 out
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2019 03:08 AM
Hi Paul
What should i be referncing on my core for the 192.168.120.80 subnet?
The ACL prevents access form the 192.168.16.0/22 Ip range to the VLAN. Only certain users are allowed access to the CCTV VLAN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2019 03:37 AM - edited 04-24-2019 03:38 AM
Hello
@Dav1787 wrote:
Hi Paul
What should i be referncing on my core for the 192.168.120.80 subnet?
The ACL prevents access form the 192.168.16.0/22 Ip range to the VLAN. Only certain users are allowed access to the CCTV VLAN.
Fw
192.168.120.80 255.255.255.0 X3
192.168.16.254 X1
Core
interface GigabitEthernet1/0/24
no switchport
ip address 192.168.120.80 255.255.255.0
interface Vlan20 <---- CCTV
ip address 192.168.20.1 255.255.255.0
ip access-group 20 out
ip route 0.0.0.0 0.0.0.0 192.168.16.254
If you want all vlan 20 traffic to be routed towards X3 interface on the sonicwall then you will need to policy route towards it otherwise vlan 20 will go via the default route, however it looks like the ip address assigned to routed port gig1/0/24 has the same ip address as the sonicwall X3 port?
Policy Base Routing example:
ip access-list extended CCTV_acl
permit ip 192.168.20.0 0.0.0.255 any
route-map CCTV_rm
match ip address CCTV_acl
set ip next-hop 192.168.120.x <---sonicwall ip address
int vlan 20
ip policy route-map CCTV_rm
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2019 03:41 AM
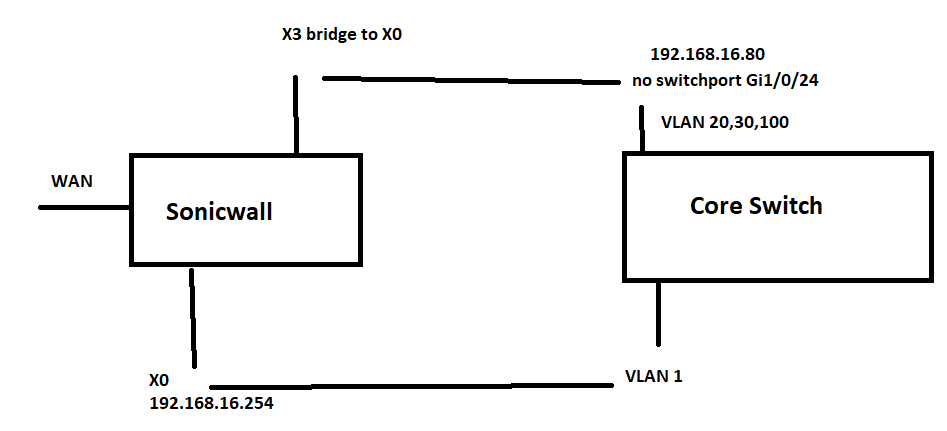
No the Ip address of the X3 port is ont he same subnet as the X3 port its not the same IP address. Maybe this diagram might help explain it. This is the current setup that is working but i need to move all device for vlan1 to a new vlan.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
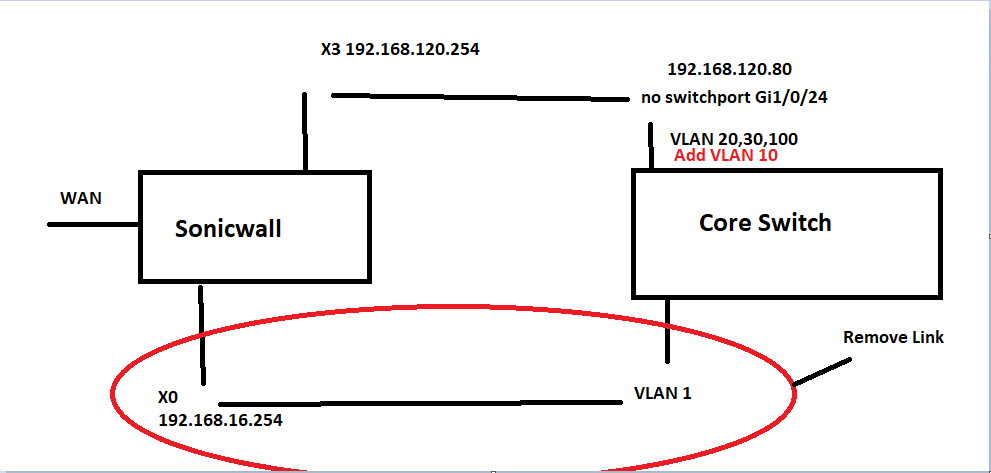
04-24-2019 03:45 AM
Desired solution
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2019 03:54 AM - edited 04-24-2019 03:58 AM
Hello
Okay then you wont need PBR , you just need to create a additional SVI on the core and change the routed port to an access port and default route.
Example:
int vlan 10
description Sonicwall
ip address 192.168.120.x 255.255.255.0
vlan 10
exit
interface GigabitEthernet1/0/24
Description link to SonicWall FW
no ip address 192.168.120.80 255.255.255.0
switchport host
switchport access vlan 10
no ip route 0.0.0.0 0.0.0.0 192.168.16.254
ip route 0.0.0.0 0.0.0.0 vlan 10 192.168.120.80
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2019 04:15 AM
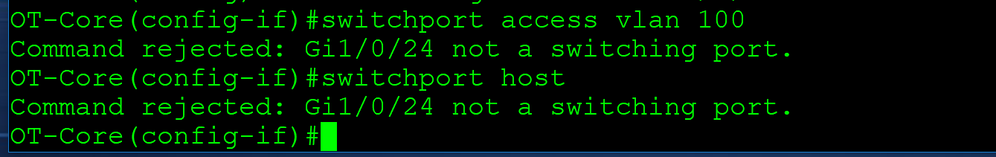
hasnt worked that mate.
Added static route for Vlan 20 to 192.168.120.254 (gateway)
change static routes to match the new routing port Ip address.
also some commands didnt work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2019 04:46 AM - edited 04-24-2019 04:47 AM
Hello
What model of switch is being used for the core?
int gigx/x/x
switchport
switchport host
switchport acess vlan 10
if that doesn't work you may need to select another port that is L2 capable
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2019 04:49 AM
its a C3750G.
Its fine now i realised you put to use 192.168.120.80 as the ip route. i changed it to 192.168.120.254 and now its working so great stuff thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2019 06:07 AM - edited 04-24-2019 06:14 AM
sorry this didnt work but i now know why.
Its releated to my access lists. If i remove them all together i can access the internet.
Can anyone explain how i can correct the access list to disallow the vlans accessing the main network?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2019 06:20 AM
Hello
what didn’t work ?
Just to conform - you have now removed the routed port and disconnected its physical link to the Fw and it’s now an access port on vlan 10
On the Fw any static routes that you may have now need pointing to the vlan 10 of the switch and if your performing nat vlan 10 needs to be included in any access list if you not already doing so
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2019 06:37 AM
sorry my bad i should be clear.
The reason i couldnt get internet access from any of my vlans was because of two things.
When i change the X3 port to a static address of 192.168.120.254 i had no static route for that network on my core switch. After doing some testing some of my vlans were abel to access the internet (gateway) and some couldnt.
after invesitgiating this futher i have realised that some have access lists and some dont. So its a ACL issue.
VLAN 100 was able to access the internet as it has no ACL assigned to it.
VLAN 20 was not able to access the internet because it has a ACL assigned to it.
Now its kind of working. My question is:
How do i create a access list that allows access for internet access but denies any other vlan accessed any devices in it?
at the moment anythign ont he default vlan can access the cameras.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: