- Cisco Community
- Technology and Support
- Networking
- Routing
- NAT hairpinning with multiple NAT outside WAN links, port forwards, static NAT and source route-maps...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
NAT hairpinning with multiple NAT outside WAN links, port forwards, static NAT and source route-maps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-15-2020 03:28 AM
Hi all,
This one has stumped me for quite some time - long enough for me to go to the effort of actually doing some documentation!
In a pinch, I need to do hairpin NAT from the internal VLAN 1 hosts, to the external NAT addresses on two of the links. This gets complex, because there's policy routing in the way and a few other limitations that seem to break anything I try.
Diagram below:
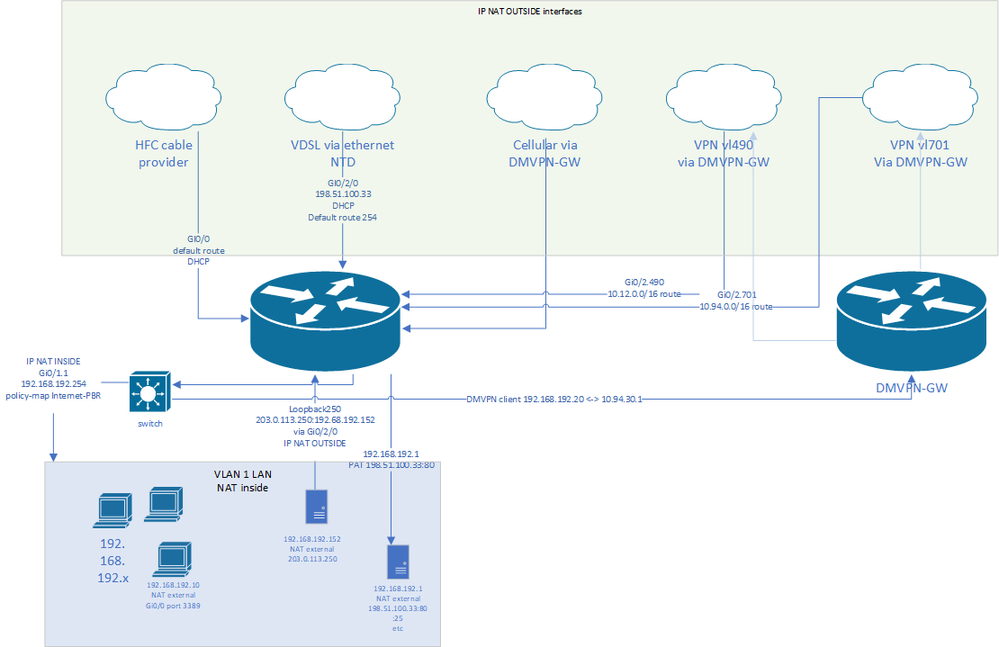
I have two VPN paths, Gi0/2.490, Gi0/2.701. These go to the DMVPN router. The DMVPN router is just a source of traffic in this instance and is not part of the actual problem but is included for visibility.
Gi0/0 is the default route.
Gi0/2/0 is policy routed based on source address (VDSL via ethernet NTD)
Gi0/2.761 is a cellular connection I use for failover if the primary link or links go down.
The ISP on Gi0/2/0 has an address presented as a framed route. This lands on Loopback250 and is used for static NAT to a server.
The primary address on Gi0/2/0 is PAT with PAT translations pointing to various servers and client that have specific port forward requirements.
Same with Gi0/0.
NAT runs on all of the above as a NAT outside.
LAN path is Gi0/1.1.
Route table entries are simplified as follows:
ip route 0.0.0.0 0.0.0.0 GigabitEthernet0/0 dhcp
ip route 0.0.0.0 0.0.0.0 GigabitEthernet0/2.761 dhcp 255
ip route 10.94.0.0 255.255.0.0 110.94.172.142 (work DMVPN path 1 via Gi0/2.701)
ip route 10.12.0.0 255.255.0.0 10.12.81.30 ! (work DMVPN path 2 via Gi0/2.490)
ip route 10.94.30.1 255.255.255.255 GigabitEthernet0/0 dhcp ! Exclude the DMVPN headend or else traffic will try to go over the DMVON tunnel to its own headend
ip route 0.0.0.0 0.0.0.0 GigabitEthernet0/2/0 dhcp 254
In order to run NAT on all these interfaces, I use policy maps:
ip nat inside source route-map NATLIST interface GigabitEthernet0/2/0 overload
ip nat inside source route-map NATLIST-LTE interface GigabitEthernet0/2.761 overload
ip nat inside source route-map NATLIST-mw interface Tunnel8 overload
ip nat inside source route-map NATLIST-work-1 interface GigabitEthernet0/2.490 overload
ip nat inside source route-map NATLIST-work-2 interface GigabitEthernet0/2.701 overload
ip nat inside source route-map NATLIST-HFC interface GigabitEthernet0/0 overload
All of these look the same:
route-map NATLIST permit 1
match ip address 102 ! ACL of IP ranges of my internal network
match interface GigabitEthernet0/2/0 ! Relevant external facing interface
I have a policy map:
==
! Set any traffic to the DMVPN headend to go out the primary WAN. The DMVPN headends for this box reside on the /16 that routes via the DMVPN interior, so I need to ensure traffic goes around it or else the DMVPN tunnel won't come up.
route-map Internet-PBR permit 9
match ip address work-headend
set interface GigabitEthernet0/0
!
! If these are work VPN addresses, cease processing PBR in case we want a host to still see the work vlans but not be policy routed by rule 12.
There are multiple interfaces, so a "set interface" will not work.
route-map Internet-PBR permit 11
match ip address work-vlans
!
! If the traffic should go out the secondary WAN, send it out here using the Internet-PBR ACL:
route-map Internet-PBR permit 12
match ip address Internet-PBR
set ip next-hop dynamic dhcp
set interface GigabitEthernet0/2/0
!
! LTE tertiary WAN path. Force hosts out this link by adding them to the LTE-Bypass ACL.
route-map Internet-PBR permit 13
match ip address LTE-Bypass
set ip next-hop 172.21.17.254
set interface GigabitEthernet0/2.761
==
ACL for traffic going over the second link:
ip access-list extended Internet-PBR ! Hosts that go out the secondary
deny ip any 192.168.0.0 0.0.255.255 ! traffic to other internal hosts need to route to other internal hosts, not get policy routed out to the Internet.
permit ip host 192.168.192.1 any
permit ip host 192.168.192.177 any
permit ip host 192.168.192.12 any
permit ip host 192.168.192.167 any
permit ip host 192.168.192.131 any
permit ip host 192.168.192.152 any
! NAT for these addresses:
ip access-list extended 102
permit ip 192.168.0.0 0.0.255.255 any
Problems (in order of pain):
1. I can't get NAT hairpin to work. I've attempted using policy maps and a loopback interface with NAT outside configured but this doesn't seem to take effect. I've also attempted NVI NAT, but this broke my ability to NAT in from the outside using multiple interfaces at once (couldn't figure that out). NVIs also don't seem to be supported with IOS-XE, so I can't migrate to a 4000 series in the near future without getting this right.
- The important one is the 1:1 NAT on Loop250, but also need Gi0/2/0 and Gi0/0's overloaded NAT to work in this manner.
2. I can't ping the Gi0/2/0 (VDSL via Ethernet) interface from the outside. If I add a "permit ip any any" on access list 102 (for the NAT rules), I see a response from Gi0/0's IP address.
1a. If I ping Loop250, I get two responses (one duplicate). If I ping from the box behind that NAT translation, I see two responses, too.
3. The policy map to Gi0/2/0 gets the wrong next-hop (from the Gi0/0 interface) whenever that DHCP lease renews.
route-map Internet-PBR permit 12
match ip address Internet-PBR
set ip next-hop dynamic dhcp
set interface GigabitEthernet0/2/0
It gets the IP address of the last interface that requested a DHCP address, even though I have specified the interface. Is this by design or a bug?
Thanks all!
- Labels:
-
ISR G2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-15-2020 03:54 AM - edited 08-15-2020 03:54 AM
Hello
I can see you have NAT and PBR on multiple interfaces but tbh it isn't clear on what your trying to hairpin?
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2020 01:58 AM
Hi Paul,
I'm attempting to hairpin (access from internal 192.168.192.0/24 locations) the outside NAT addresses on Gi0/2/0 and Loop250. It would be preferable if I could hairpin translations on Gi0/0 as well.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
