- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Need help configuring site-to-site VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2019 09:18 PM
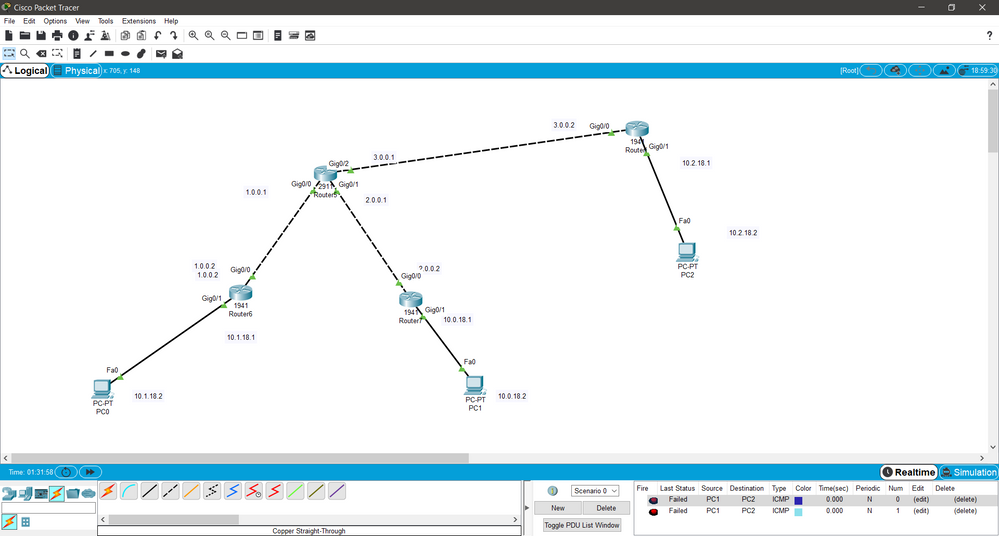
I'm trying to connect 2 sites to the main office in the middle using VPN I already configured the left side and It works fine but I can't seem to connect the right side to the middle network, here are all the configuration commands i used,
!on router 6 (left)
hostname S
interface g0/1 ip address 10.1.18.1 255.255.255.224
no shut
interface g0/0 ip address 1.0.0.2 255.255.255.224
no shut
exit ip route 0.0.0.0 0.0.0.0 1.0.0.1
!
!on router 7(middle)
hostname B
interface g0/1
ip address 10.0.18.1 255.255.255.224
no shut
interface g0/0
ip address 2.0.0.2 255.255.255.224
no shut
exit
ip route 0.0.0.0 0.0.0.0 2.0.0.1
!
!router 8 (right)
hostname M
interface g0/1
ip address 10.2.18.1
no shut
interface g0/0
ip address 3.0.0.2
no shut
exit
ip route 0.0.0.0 0.0.0.0 3.0.0.1
!
!on router 5 (ISP, top)
hostname ISP
interface g0/0
ip address 1.0.0.1 255.255.255.224
no shut
interface g0/1
ip address 2.0.0.1 255.255.255.224
no shut
interface g0/2
ip address 3.0.0.1 255.255.255.224
no shut
exit
!
!on router M , B, S
license boot module c1900 technology-package securityk9
!
!on router 6
crypto isakmp policy 10
encryption aes 256
authentication pre-share
group 5
!
crypto isakmp key secretkey address 2.0.0.2
!
crypto ipsec transform-set S-B esp-aes 256 esp-sha-hmac
!
crypto map IPSEC-MAP 10 ipsec-isakmp
set peer 2.0.0.2
set pfs group5
set security-association lifetime seconds 86400
set transform-set S-B
match address 100
!
interface GigabitEthernet0/0
crypto map IPSEC-MAP
!
access-list 100 permit ip 10.1.18.0 0.0.0.31 10.0.18.0 0.0.0.31
!
!on router 7(middle)
!for the 1st tunnel
crypto isakmp policy 10
encryption aes 256
authentication pre-share
group 5
!
crypto isakmp key secretkey address 1.0.0.2
!
crypto ipsec transform-set B-S esp-aes 256 esp-sha-hmac
!
crypto map IPSEC-MAP 10 ipsec-isakmp
set peer 1.0.0.2
set pfs group5
set security-association lifetime seconds 86400
set transform-set B-S
match address 100
!
interface GigabitEthernet0/0
crypto map IPSEC-MAP
!
access-list 100 permit ip 10.0.18.0 0.0.0.31 10.1.18.0 0.0.0.31
!
!for the 2st tunnel
crypto isakmp policy 11
encryption aes 256
authentication pre-share
group 5
!
crypto isakmp key secretkey address 3.0.0.2
!
crypto ipsec transform-set B-M esp-aes 256 esp-sha-hmac
!
crypto map IPSEC-MAP 11 ipsec-isakmp
set peer 3.0.0.2
set pfs group5
set security-association lifetime seconds 86400
set transform-set B-M
match address 110
!
interface GigabitEthernet0/0
crypto map IPSEC-MAP
!
access-list 110 permit ip 10.0.18.0 0.0.0.31 10.2.18.0 0.0.0.31
!
!on router 8(left)
crypto isakmp policy 11
encryption aes 256
authentication pre-share
group 5
!
crypto isakmp key secretkey address 2.0.0.2
!
crypto ipsec transform-set M-B esp-aes 256 esp-sha-hmac
!
crypto map IPSEC-MAP 11 ipsec-isakmp
set peer 2.0.0.2
set pfs group5
set security-association lifetime seconds 86400
set transform-set M-B
match address 110
!
interface GigabitEthernet0/0
crypto map IPSEC-MAP
!
access-list 110 permit ip 10.2.18.0 0.0.0.31 10.0.18.0 0.0.0.31
Solved! Go to Solution.
- Labels:
-
LAN Switching
-
Other Routing
-
WAN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2019 04:27 AM - edited 09-15-2019 04:27 AM
Hello,
I opened the file and both VPNs are working. What exactly can you NOT do ? If I ping 10.0.18.2 from both VPN endpoints, I get a proper response, and if you check the encrypted packets on R7 with 'show crypto ipsec sa', the encrypted packet count is increasing.
I have taken out all the redundant stuff and cleaned up the configs, revised project file is attached...(use the lateste version of Packet Tracer, 7.2.2).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2019 12:43 AM
Hello,
post the Packet Tracer project (.pkt) file, zip it first, otherwise the system won't let you upload it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2019 02:56 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2019 04:27 AM - edited 09-15-2019 04:27 AM
Hello,
I opened the file and both VPNs are working. What exactly can you NOT do ? If I ping 10.0.18.2 from both VPN endpoints, I get a proper response, and if you check the encrypted packets on R7 with 'show crypto ipsec sa', the encrypted packet count is increasing.
I have taken out all the redundant stuff and cleaned up the configs, revised project file is attached...(use the lateste version of Packet Tracer, 7.2.2).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2019 04:40 AM
thank you for your reply, it seems to be working on your revised lab, could it be an issue with the packt tracer version? or did you change any configurations?
thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2019 04:46 AM
I just restarted the application and it seems to be working fine, thank you very much for your time, good sir.
and if you have time could you please explain how can I add a remote user to connect to the 10.0.18.0 network through IP Sec VPN, thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2019 07:45 AM
Hello,
if you add the lines in bold to the configuration of Router7, the router will function as PPTP VPN server for remote access users:
Current configuration : 1554 bytes
!
version 15.1
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname B
!
username vpnuser password 0 vpnpassword
!
aaa new-model
!
aaa authentication ppp default local
!
vpdn enable
!
ip cef
no ipv6 cef
!
license udi pid CISCO1941/K9 sn FTX15245NGO-
license boot module c1900 technology-package securityk9
!
vpdn-group REMOTE-VPN
accept-dialin
protocol pptp
virtual-template 1
!
crypto isakmp policy 10
encr aes 256
authentication pre-share
group 5
!
crypto isakmp policy 11
encr aes 256
authentication pre-share
group 5
!
crypto isakmp key secretkey address 1.0.0.2
crypto isakmp key secretkey1 address 3.0.0.2
!
crypto ipsec transform-set B-S esp-aes 256 esp-sha-hmac
crypto ipsec transform-set B-M esp-aes 256 esp-sha-hmac
!
crypto map IPSEC-MAP 10 ipsec-isakmp
set peer 1.0.0.2
set pfs group5
set security-association lifetime seconds 86400
set transform-set B-S
match address 100
!
crypto map IPSEC-MAP 11 ipsec-isakmp
set peer 3.0.0.2
set pfs group5
set security-association lifetime seconds 86400
set transform-set B-M
match address 101
!
spanning-tree mode pvst
!
interface GigabitEthernet0/0
ip address 2.0.0.2 255.255.255.224
duplex auto
speed auto
crypto map IPSEC-MAP
!
interface GigabitEthernet0/1
ip address 10.0.18.1 255.255.255.224
duplex auto
speed auto
!
interface Virtual-Template1
ip unnumbered GigabitEthernet0/1
peer default ip address pool VPNPOOL
ppp encrypt mppe auto required
ppp authentication ms-chap ms-chap-v2
!
interface Vlan1
no ip address
shutdown
!
ip local pool VPNPOOL 10.0.18.20 10.0.18.30
!
ip classless
ip route 0.0.0.0 0.0.0.0 2.0.0.1
!
ip flow-export version 9
!
!
access-list 100 permit ip 10.0.18.0 0.0.0.31 10.1.18.0 0.0.0.31
access-list 101 permit ip 10.0.18.0 0.0.0.31 10.2.18.0 0.0.0.31
!
line con 0
!
line aux 0
!
line vty 0 4
login
!
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2019 12:38 PM - edited 09-15-2019 12:54 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
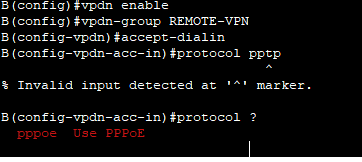
09-15-2019 01:09 PM
Hello,
the only option available as protocol appears to be pppoe, but that is not supported in Packet Tracer. EZVPN is not supported either. What is the exact requirement for the remote access ?
Keep in mind that Packet Tracer devices are not fully featured, real IOS devices. Only a subset of the commands available in IOS are available.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2019 01:24 PM
thank you for your reply,
the requirement is that the remote users should be able to access their work from the company site (10.1.18.0 network and 10.2.18.0 network) while traveling.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2019 02:17 PM
Hello,
have a look at the video below. As said, you can only do a few things with Packet Tracer, the below might work for you:
Packet Tracer Lab 6 - Remote Access VPN
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide