- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Point to point connection
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2023 12:14 PM
Hi,
I have 2 locations and they are connected to connected through VPN connection and it works fine but I am just adding a new point to point connection.
On both ends Fortinet Firewalls interface have been configured with ip address 172.16.30.1 and 172.16.30.2 respectively.
On both cisco SW we have int vlan 65 with ip address 172.16.0.5 on Cisco Sw site 1 and 172.16.30.6 on Cisco SW site 2.
Interface Connecting the 2 sites were configured as truck allowing vlan 65
Int GigabitEthernet1/0/22 and int GigabitEthernet 1/0/23 were configured as access allowing vlan 65.
Fortinet 1 cannot ping Fortinet 2
I tried putting an ip address on the interfaces connecting the 2 sites (
GigabitEthernet1/0/24 and Te2/1/1) and both sites can ping each other but still cannot get Fortinet 1 to ping Fortinet 2.
What will be the simplest setup to have Fortinet 1 ping Fortinet 2? i cannot change anything on Fortinet side
Thanks
Tazio
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2023 06:58 AM
Hi ,
Yes you are absolutely right. I did a shut on Te2/1/1 and int GigabitEthernet1/0/24 still stays up up.
Please see the output yopu requested
!!!!!!!!!!!!!!
COLOSW_STACKED#sh ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is 10.30.0.1 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 10.30.0.1
10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 10.30.0.0/21 is directly connected, Vlan2
L 10.30.0.2/32 is directly connected, Vlan2
172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks
C 172.16.30.0/29 is directly connected, Vlan65
L 172.16.30.6/32 is directly connected, Vlan65
!!!!!!!!!!!!!!!!!!!!!!
BGP1#sh ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks
C 172.16.30.0/29 is directly connected, Vlan65
L 172.16.30.3/32 is directly connected, Vlan65
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!1
COLOSW_STACKED#sh run | i routing
ip routing
class-map match-any system-cpp-police-routing-control
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
BGP1#sh run | i routing
ip routing
class-map match-any system-cpp-police-routing-control
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
I did a ping to 10.16.30.6 with laptop connected to media converter and Ip set to 172.16.30.3 and int te2/1/1 set as access for vlan 65 and ping works
C:\Users\Tazio.SMIDOMAIN>ping 172.16.30.6
Pinging 172.16.30.6 with 32 bytes of data:
Reply from 172.16.30.6: bytes=32 time=6ms TTL=254
Reply from 172.16.30.6: bytes=32 time=4ms TTL=254
Reply from 172.16.30.6: bytes=32 time=5ms TTL=254
Reply from 172.16.30.6: bytes=32 time=5ms TTL=254
Ping statistics for 172.16.30.6:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 4ms, Maximum = 6ms, Average = 5ms
Thanks
Tazio
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2023 09:48 AM
SW to Sw cannot ping <<- this need more clarification? how it L2 VPN and can not ping each other?
please share spanning tree for interface
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2023 11:51 AM
FW1-SW1-Router1-l2vpn-Router2-SW2-FW2
the l2vpn is mpls or l2tpv3 is vlan aware? check the router do the l2vpn I think the issue is there.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2023 12:49 PM
https://www.letsconfig.com/how-to-configure-q-in-q-tunneling-in-cisco/
I think this is your config, the SP need to know the VLAN you add to make Q-in-Q map.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2023 12:54 PM
Hello,
I have not followed the entire thread, but can you post the full running configurations (sh run) of both switches ? Since this is a layer 2 network, make sure you don't have 'ip routing' enabled on any of the switches.
That said, the Fortinets do not need a default gateway, as both Fortinets and both switches are in the same subnet...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2023 07:14 AM
Hi,
Please see running config for both Sw.
I know you said the ip routing should not be on any of those Sw but I can see they are there. I can remove them if need be.
The Fortinet Engineer told me that he should not have the default Gateway but Fortinet was not even able to ping trhe Ciusco Sw without the GW.
Please see sh run attached for both Sw.
Thanks
Tazio
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2023 06:10 AM
Hi,
Anything you can suggest please
Thanks
Tazio
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2023 06:19 AM
are you check what I mention before??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2023 06:42 AM
Hi,
I have spoken with ISP and asked them to allow VLAN 65 but did not hear back. But they told me that I need to put an ip add on both cisco sw and make it point to point
Thanks
Tazio
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2023 03:07 AM
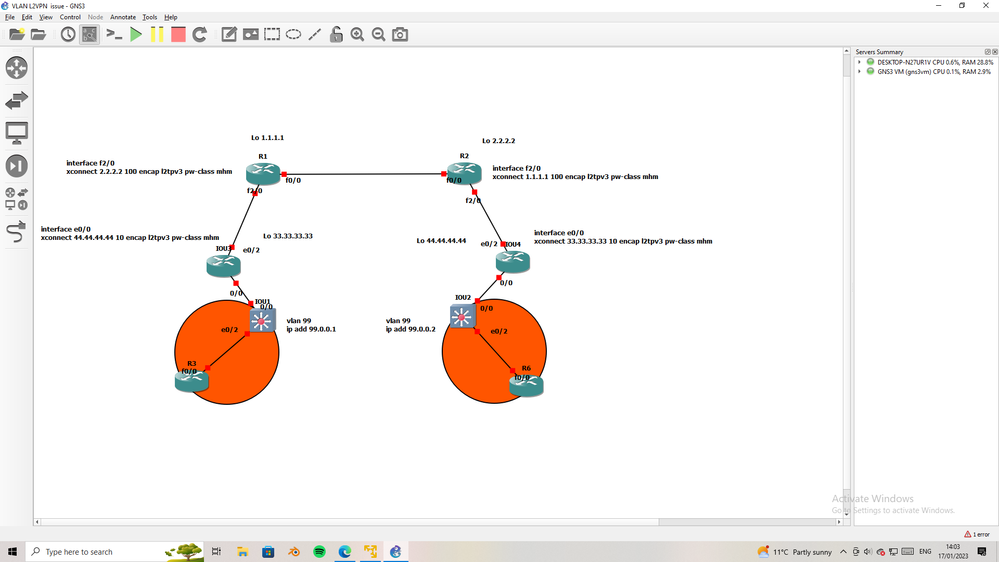
this is simple topology, I want to clear points here,
R1 & R2 is ISP router
IOU3 and IOU3 is your edge router,
IOU1 & IOU2 is L3SW
if we want to L2 between two SW, the two edge router must config with xconnect,
the issue is not solve in SW it solve in edge router that connect to ISP.
this solution will be L2 over ISP L2VPN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2023 06:10 AM
Hello,
Thank you everyone for your help.
My issue has been resolved,
I set the interfaces connecting the 2 Cisco Sws on both sites as access ,instead of trunk and set all other interfaces connecting to the Firewall as Trunk.
Both sites can ping each other
Still could not understand why when the point to point interfaces (cisco Sw) were configures as Trunk it did not work.
Thanks
Tazio
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2023 06:16 AM
you are so welcome
- « Previous
-
- 1
- 2
- Next »
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: