- Cisco Community
- Technology and Support
- Networking
- Routing
- Redistributing Routes between OSPF and EIGRP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2013 01:12 PM - edited 03-04-2019 08:04 PM
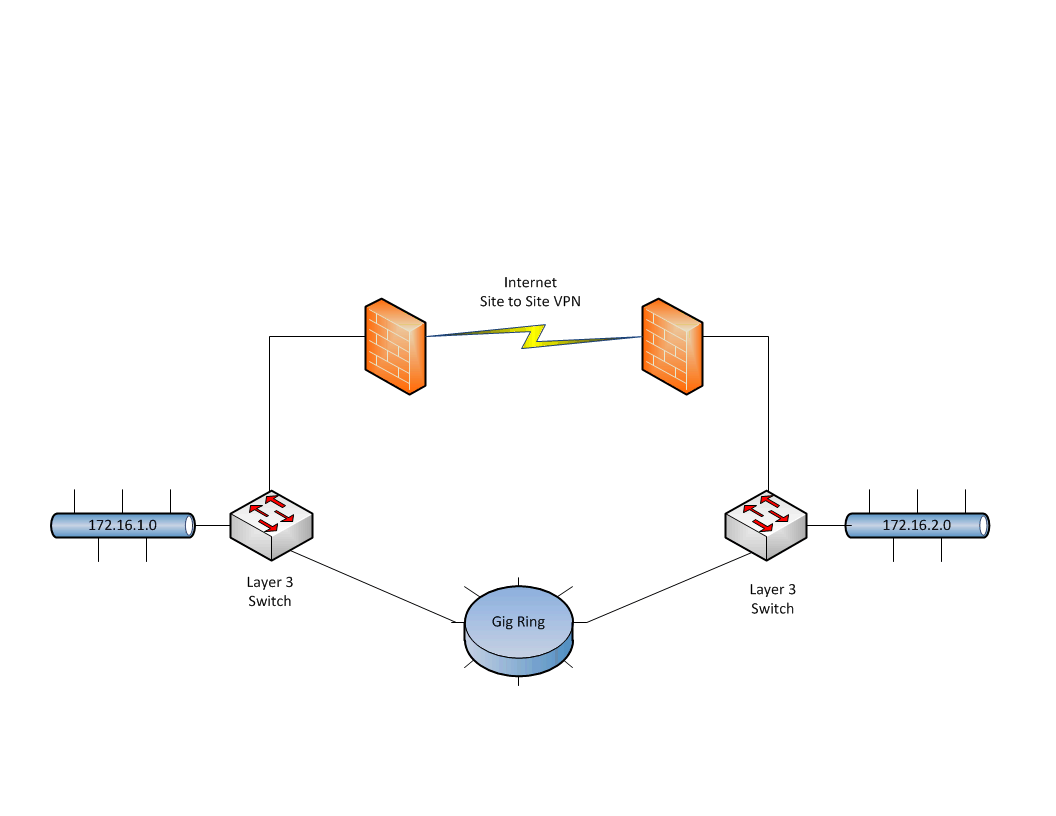
We have a test network with the below topology. We have two networks each connected to a L3 switch. Both have networks have an ASA firewall with a site to site tunnel between them. They also have a gig connection between them. We want to setup a scenerio where the gig connection is the primary route but if that route fails then it fails over to the routethat is over the site to site tunnel. We have eigrp running on both core switches so the routes over the gig connection are working correctly. However the networks are not learning about the second route that goes over the vpn tunnel. We have ospf running on the asa's and we are redistrubuting the routes into eigrp. Does that sound correct? The ASA's look like they are learning routes over ospf correctly however when we go to the core switches and do show ip eigrp topology we do not see the feasible successor routes. Any ideas on how to make this work?
Solved! Go to Solution.
- Labels:
-
Routing Protocols
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2013 09:04 AM
Hello
From the initial config looks like you have auto summarisation enabled on the core switches, also in the asa eigrp process your redistribution metrics dont seem correct regards the delay /load/reliability- whats the reasoning behind this? Could you try the following:
Core Switch 1 & 2
router eigrp 100
no auto-summary
Asa 1& 2
Router eigrp 100
Redistribute ospf 1 metric 100000 1 255 1 1500
Could you also post the out from - show ip eigrp topology all-links
Res
Paul
Please don't forget to rate any posts that have been helpful.
Thanks.
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2013 01:17 PM
Mitchell
We could tell more about the problem if you would provide more detail, in particular it would help if you would post the configuration.
Based on my experience I would say that a very common problem with redistribution into EIGRP is configuring the redistribution but not configuring a default metric for the redistribution. So my first suggestion would be to check and see if a default metric is provided for the redistribution.
If that is not the problem then please post the configuration.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2013 01:31 PM
Here is what we have configured on the asa and switches in respect to routing. The 192.168.100 is the vlan for the gig connection:
ASA 1:
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 10.10.10.1 255.255.255.0
interface GigabitEthernet0/5
nameif inside
security-level 100
ip address 172.16.1.20 255.255.255.0
router eigrp 100
no auto-summary
network 172.16.1.0 255.255.255.0
redistribute ospf 100 metric 1000 1000 245 245 1500
router ospf 100
network 10.10.10.0 255.255.255.0 area 10.10.10.0
log-adj-changes
redistribute eigrp 100 subnets
Core Switch 1:
interface Vlan2
ip address 172.16.1.1 255.255.255.0
router eigrp 100
network 172.16.1.0 0.0.0.255
network 192.168.100.0
eigrp router-id 172.16.1.1
ASA 2:
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 10.10.10.2 255.255.255.0
interface GigabitEthernet0/5
nameif inside
security-level 100
ip address 172.16.2.20 255.255.255.0
router eigrp 100
no auto-summary
network 172.16.2.0 255.255.255.0
redistribute ospf 100 metric 1000 1000 245 245 1500
router ospf 100
network 10.10.10.0 255.255.255.0 area 10.10.10.0
log-adj-changes
redistribute eigrp 100 subnets
Core Switch 2:
interface Vlan2
ip address 172.16.2.1 255.255.255.0
router eigrp 100
network 172.16.2.0 0.0.0.255
network 192.168.100.0
eigrp router-id 172.16.2.1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2013 01:51 PM
Mitchell
Thank you for the additional information. I am glad to see that a default metric is supplied for the redistribution into EIGRP. So we must look for some other explanation for why the routes do not seem to be redistributed. As a first step in figuring this out would you post the output of show ip eigrp neighbor and the output of show ip eigrp topology from the switches? Also I would like to see what the ASAs say about neighbor relationship of both EIGRP and OSPF.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2013 10:48 AM
Deleted config will repost.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2013 11:42 AM
Hello Mitchell, the output provided may be helpful, though i'd just like to point out an observation... your latest post seems to contradict your second post (with regards to ip addressing in particular) which could potentially make things a bit more difficult for members to assist
Please rate useful posts & remember to mark any solved questions as answered. Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2013 12:20 PM
Mitchell
Bilal is quite right. There are some details in this post that are reversed from what you gave in an earlier post. For example in the earlier post 172.16.1.0 was on switch 1 and fw1 but this post shows it on switch2 and fw2. And there appears to be another network here since sw1 has a neighbor at 192.168.1.6. And firewall 2 has two EIGRP neighbors
fw2# sh eigrp neighbors
EIGRP-IPv4 neighbors for process 100
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
1 172.16.1.3 Gi0/5 13 00:33:06 80 480 0 19
0 172.16.1.2 Gi0/5 10 00:33:07 87 522 0 30
where the earlier post shows only one device connected to the firewall inside.
So there are details of the config that you have not shared with us and it makes us wonder what else we do not know about the environment that might turn out to be important.
Besides clarifying information about the topology and configuration, I have one other request. On the firewall would you post the output of show ip eigrp topology all
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2013 12:43 PM
I will repost on Monday. I cut and paste then did some editing to clean up the post and made a few mistakes. Sorry about that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-11-2016 12:05 AM
Redistribution
The Process of exchanging routing information between Routing Protocols.
To Configure Redistribution
- Router must be running both protocols
- Change Metric
- RIPV2:Hop Counts
- OSPF:cost
- EIGRP:BW+DELAY+LOAD+RELIABILITY+MTU
Refer to the config and snapshot for redistribution of EIGRP and OSPF
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2013 04:24 PM
On the asa set reverse route on the crypto map, redistribute static subnets into eigrp. Then check the eigrp topology table on cores.
Sent from Cisco Technical Support Android App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2013 06:13 AM
Here are the additional show outputs. The 192.168.100.0 network is the primary gig link network. Also, On the sw1 side we added another layer3 switch to test redundant gateways. The ip addresses for the #1 side switches are now 172.16.1.2 and 172.16.1.3. Once thing I have notice is in the routes for the firewall, fw1 shows an ospf learned route while fw2 does not show that. The vpn tunnel works between the firewalls.
Core Switch 1:
sw1#show ip eigrp nei
EIGRP-IPv4 Neighbors for AS(100)
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
2 192.168.100.5 Vl192 11 00:29:23 1988 5000 0 8
1 172.16.1.3 Vl100 10 00:29:23 1755 5000 0 6
0 172.16.1.20 Vl100 10 00:29:23 3 450 0 8
sw1#sh ip eigrp top
EIGRP-IPv4 Topology Table for AS(100)/ID(192.168.100.6)
Codes: P - Passive, A - Active, U - Update, Q - Query, R - Reply,
r - reply Status, s - sia Status
P 192.168.100.0/24, 1 successors, FD is 2816
via Connected, Vlan192
P 172.16.1.0/24, 1 successors, FD is 2816
via Connected, Vlan100
P 172.16.2.0/24, 1 successors, FD is 3072
via 192.168.100.5 (3072/2816), Vlan192
P 10.10.10.0/24, 1 successors, FD is 2816256
via 172.16.1.20 (2816256/2816000), Vlan100
ASA 1:
fw1# show eigrp nei
EIGRP-IPv4 neighbors for process 100
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
1 172.16.1.2 Gi0/5 13 00:35:09 1 200 0 3
0 172.16.1.3 Gi0/5 11 00:35:27 2 200 0 1
fw1# show ospf nei
Neighbor ID Pri State Dead Time Address Interface
172.16.2.20 1 FULL/DR 0:00:34 10.10.10.1 outside
fw1# show eigrp top
EIGRP-IPv4 Topology Table for AS(100)/ID(172.16.1.20)
Codes: P - Passive, A - Active, U - Update, Q - Query, R - Reply,
r - reply Status, s - sia Status
P 10.10.10.0 255.255.255.0, 1 successors, FD is 2816000
via Redistributed (2816000/0)
P 192.168.100.0 255.255.255.0, 1 successors, FD is 3072
via 172.16.100.2 (3072/2816), GigabitEthernet0/5
P 172.16.1.0 255.255.255.0, 1 successors, FD is 2816
via Connected, GigabitEthernet0/5
fw1# show route
Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default, U - per-user static route, o - ODR
P - periodic downloaded static route
Gateway of last resort is 10.10.10.1 to network 0.0.0.0
O E2 172.16.2.0 255.255.255.0 [110/20] via 10.10.10.1, 0:38:29, outside
C 172.16.1.0 255.255.255.0 is directly connected, inside
C 10.10.10.0 255.255.255.0 is directly connected, outside
D 192.168.100.0 255.255.255.0 [90/3072] via 172.16.1.2, 0:38:15, inside
S* 0.0.0.0 0.0.0.0 [1/0] via 10.10.10.1, outside
Core Switch 2:
sw2#show ip eigrp nei
EIGRP-IPv4 Neighbors for AS(100)
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
1 192.168.100.6 Vl192 14 00:39:44 6 200 0 7
0 172.16.2.20 Vl200 12 00:40:11 1021 5000 0 4
sw2#show ip eigrp top
EIGRP-IPv4 Topology Table for AS(100)/ID(172.16.2.1)
Codes: P - Passive, A - Active, U - Update, Q - Query, R - Reply,
r - reply Status, s - sia Status
P 192.168.100.0/24, 1 successors, FD is 2816
via Connected, Vlan192
P 172.16.1.0/24, 1 successors, FD is 3072
via 192.168.100.6 (3072/2816), Vlan192
P 172.16.2.0/24, 1 successors, FD is 2816
via Connected, Vlan200
P 10.10.10.0/24, 1 successors, FD is 2816256
via 172.16.2.20 (2816256/2816000), Vlan200
ASA 2:
fw2# show eigrp nei
EIGRP-IPv4 neighbors for process 100
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 172.16.2.1 Gi0/5 11 00:43:20 8 200 0 7
fw2# show ospf nei
Neighbor ID Pri State Dead Time Address Interface
172.16.1.20 1 FULL/BDR 0:00:37 10.10.10.2 outside
fw2# show eigrp top
EIGRP-IPv4 Topology Table for AS(100)/ID(192.168.1.1)
Codes: P - Passive, A - Active, U - Update, Q - Query, R - Reply,
r - reply Status, s - sia Status
P 10.10.10.0 255.255.255.0, 1 successors, FD is 2816000
via Redistributed (2816000/0)
P 192.168.100.0 255.255.255.0, 1 successors, FD is 3072
via 172.16.200.1 (3072/2816), GigabitEthernet0/5
P 172.16.2.0 255.255.255.0, 1 successors, FD is 2816
via Connected, GigabitEthernet0/5
P 172.16.1.0 255.255.255.0, 1 successors, FD is 3328
via 172.16.200.1 (3328/3072), GigabitEthernet0/5
fw2# show route
Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default, U - per-user static route, o - ODR
P - periodic downloaded static route
Gateway of last resort is 10.10.10.2 to network 0.0.0.0
C 172.16.2.0 255.255.255.0 is directly connected, inside
D 172.16.1.0 255.255.255.0 [90/3328] via 172.16.2.1, 0:45:26, inside
C 10.10.10.0 255.255.255.0 is directly connected, outside
D 192.168.100.0 255.255.255.0 [90/3072] via 172.16.2.1, 0:45:30, inside
S* 0.0.0.0 0.0.0.0 [1/0] via 10.10.10.2, outside
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2013 07:51 AM
Mitchell
I am trying to figure out the relationships and I find this in the output
P 172.16.1.0 255.255.255.0, 1 successors, FD is 3328
via 172.16.200.1 (3328/3072), GigabitEthernet0/5
So what can you tell us about the next hop of 172.16.200.1? Where is this network?
In reviewing this thread I believe that part of the problem may be that you are doing mutual redistribution between EIGRP and OSPF on both sides. Mutual redistribution at multiple points is a very common cause of network problems. So I would suggest that you change your design.
If I am understanding correctly what you want to achieve it is that OSPF should run over the VPN connection and should advertise the 172.16 subnets over the VPN so that each side will learn the other side's subnet via OSPF as a backup. If that is the case then I suggest that you make these changes:
- remove the redistribution of EIGRP into OSPF.
- add a network statement for the local 172.16 subnet for OSPF on each fw.
- keep the redistribution of OSPF into EIGRP.
This would allow OSPF to learn and advertise the 172.16 subnets and allow EIGRP to learn the other sides 172.16 subnet as an EIGRP external backup and keep the 172.16 learned via EIGRP internal over the Gig as the primary.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2013 08:28 AM
In the above config that is 172.16.2.1 not 172.16.200.1. I may have made a typo there. We did your suggestions but still not seeing a feasible successor router on the switches. Here is the ospf configs we have now. We tried a few other things from different posts:
ASA 1:
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 10.10.10.1 255.255.255.0
ospf network point-to-point non-broadcast
router ospf 100
router-id 10.10.10.1
network 10.10.10.0 255.255.255.0 area 10.10.10.0
network 172.16.1.0 255.255.255.0 area 10.10.10.0
neighbor 10.10.10.2 interface outside
log-adj-changes
!
router eigrp 100
no auto-summary
eigrp router-id 172.16.1.20
network 172.16.1.0 255.255.255.0
redistribute ospf 100 metric 1000 1000 245 245 1500 match internal
ASA 2:
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 10.10.10.2 255.255.255.0
ospf network point-to-point non-broadcast
router eigrp 100
no auto-summary
eigrp router-id 172.16.2.20
network 172.16.2.0 255.255.255.0
redistribute ospf 100 metric 1000 1000 245 245 1500 match internal
!
router ospf 100
router-id 10.10.10.2
network 10.10.10.0 255.255.255.0 area 10.10.10.0
network 172.16.2.0 255.255.255.0 area 10.10.10.0
neighbor 10.10.10.1 interface outside
We still show an ospf route learned on ASA 1 but there is not one for ASA 2.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2013 09:04 AM
Hello
From the initial config looks like you have auto summarisation enabled on the core switches, also in the asa eigrp process your redistribution metrics dont seem correct regards the delay /load/reliability- whats the reasoning behind this? Could you try the following:
Core Switch 1 & 2
router eigrp 100
no auto-summary
Asa 1& 2
Router eigrp 100
Redistribute ospf 1 metric 100000 1 255 1 1500
Could you also post the out from - show ip eigrp topology all-links
Res
Paul
Please don't forget to rate any posts that have been helpful.
Thanks.
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2013 09:12 AM
I agree with Paul that it may be helpful if you post the output of show ip eigrp topology all, and have asked for that a couple of times already. It is likely that it will have entries that do not show up in show ip eigrp topology which only shows entries that EIGRP believes are currently useable.
Also I would like to see the output of show ip route from both firewalls.
HTH
Rick
Rick
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
