- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Remote User Connectivity issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Remote User Connectivity issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2020 03:45 AM
This is my first post, please forgive me if I am posting in the wrong discussion board or using wrong labels.
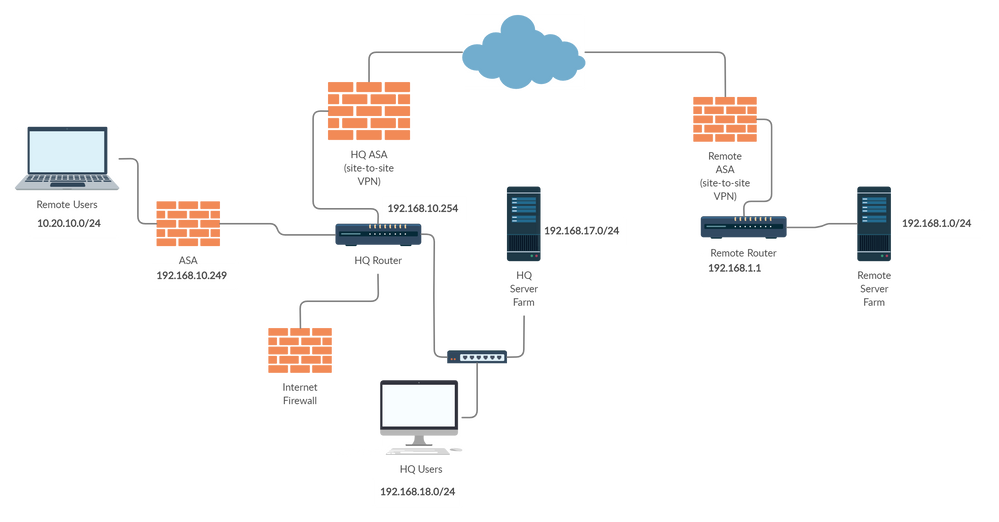
Please assist me in solving this remote user error. I have the current scenario with a graphical representation below.
Current Scenario -
- HQ Users can access remote server resources via site-to-site VPN
- Remote Users can access HQ server resources via Remote access VPN
- Remote Users cannot access remote server resources
- HQ router has a route for RA VPN users
- Added entry for RA users in both HQ & Remote ASA
- Added a route in remote router to point 10.20.10.0/24 towards remote ASA
- Labels:
-
LAN Switching
-
Routing Protocols
-
WAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2020 04:21 AM
Hello,
post the full running configs of all ASAs and routers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2020 04:29 AM
Ok I will post those soon.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2020 11:01 PM
The configs are as follow -
Config of ASA (192.168.17.249)
!
hostname ASA
!
interface Ethernet0/0
nameif outside
security-level 0
ip address *.*.*.* 255.255.255.248
!
interface Ethernet0/1
nameif inside
security-level 100
ip address 192.168.17.249 255.255.252.0
!
access-list remote_splitTunnelAcl standard permit 192.168.16.0 255.255.252.0
access-list inside_nat0_outbound extended permit ip 192.168.16.0 255.255.252.0 10.20.10.0 255.255.255.0
access-list vpn extended permit tcp 10.20.10.0 255.255.255.0 interface inside
pager lines 24
mtu outside 1500
mtu inside 1500
ip local pool vpnPool 10.20.10.1-10.20.10.250 mask 255.255.255.0
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
global (outside) 1 interface
nat (inside) 0 access-list inside_nat0_outbound
nat (inside) 1 192.168.16.0 255.255.252.0
route outside 0.0.0.0 0.0.0.0 *.*.*.* 1
route inside 192.168.1.0 255.255.255.0 192.168.17.254 1
dynamic-access-policy-record DfltAccessPolicy
aaa-server RADIUS protocol radius
aaa-server RADIUS (inside) host 192.168.17.4
timeout 5
aaa authentication enable console LOCAL
aaa authentication ssh console LOCAL
aaa authentication http console LOCAL
http server enable
http 192.168.17.0 255.255.255.0 inside
crypto ipsec transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set pfs
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map outside_map interface outside
crypto isakmp enable outside
crypto isakmp policy 10
authentication crack
encryption aes-256
hash sha
group 2
lifetime 86400
telnet timeout 5
ntp server 192.168.17.4
tftp-server inside 192.168.17.253 ASA-confg
webvpn
group-policy remote internal
group-policy remote attributes
dns-server value 192.168.17.4 192.168.17.2
vpn-tunnel-protocol IPSec
split-tunnel-policy tunnelspecified
split-tunnel-network-list value remote_splitTunnelAcl
default-domain value data-path.net
tunnel-group remote type remote-access
tunnel-group remote general-attributes
address-pool vpnPool
authentication-server-group RADIUS
default-group-policy remote
tunnel-group remote ipsec-attributes
pre-shared-key ******
!
: end
Config of HQ Router
ip route 0.0.0.0 0.0.0.0 192.168.17.251
ip route 10.20.10.0 255.255.255.0 192.168.17.249
ip route 192.168.1.0 255.255.255.0 192.168.17.252
ip route 192.168.6.0 255.255.255.0 192.168.17.252
!
!
access-list 100 permit ip 192.168.16.0 0.0.3.255 any
access-list 100 permit tcp any any eq smtp
access-list 100 permit tcp any any eq 143
access-list 100 permit tcp any any eq 443
access-list 100 permit icmp any any
access-list 100 permit ip 10.20.10.0 0.0.0.255 any
!
end
Config of HQ ASA
hostname HQASA
names
!
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address *.*.*.* 255.255.255.252
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.17.252 255.255.252.0
!
ftp mode passive
clock timezone GMT 6
object network A
subnet 192.168.1.0 255.255.255.0
object network A-IP-Phone
subnet 192.168.6.0 255.255.255.0
object network NETWORK_OBJ_192.168.16.0_22
subnet 192.168.16.0 255.255.252.0
object network Wireless_A
subnet 192.168.4.0 255.255.255.0
object network RemoteVPN
subnet 10.20.10.0 255.255.255.0
object-group network DM_INLINE_NETWORK_1
network-object object A
network-object object A-IP-Phone
network-object object Wireless_A
object-group network DM_INLINE_NETWORK_2
network-object object July
network-object object July-IP-Phone
network-object object Wireless_JULY
access-list Riverbed_TCP_Option_76 extended permit tcp any any log
access-list Riverbed_TCP_Option_78 extended permit tcp any any log
access-list riverbed_tcp extended permit tcp any any
access-list outside_cryptomap extended permit ip 192.168.16.0 255.255.252.0 object-group DM_INLINE_NETWORK_1
access-list outside_cryptomap extended permit ip object RemoteVPN object-group DM_INLINE_NETWORK_2
!
tcp-map Riverbed_TCP__Option_76_Tmap
tcp-options range 76 76 allow
!
tcp-map Riverbed_TCP__Option_78_Tmap
tcp-options range 78 78 allow
!
tcp-map allow-probes
tcp-options range 76 78 allow
!
pager lines 24
nat (inside,outside) source static NETWORK_OBJ_192.168.16.0_22 NETWORK_OBJ_192.168.16.0_22 destination static DM_INLINE_NETWORK_1 DM_INLINE_NETWORK_1 no-proxy-arp route-lookup
route outside 0.0.0.0 0.0.0.0 *.*.*.* 1
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
aaa authentication serial console LOCAL
aaa authentication http console LOCAL
aaa authentication enable console LOCAL
aaa authentication login-history duration 365
http server enable
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS mode transport
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal 3DES
protocol esp encryption 3des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal DES
protocol esp encryption des
protocol esp integrity sha-1 md5
crypto ipsec security-association pmtu-aging infinite
crypto map outside_map 1 match address outside_cryptomap
crypto map outside_map 1 set peer *.*.*.*
crypto map outside_map 1 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 1 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
crypto map outside_map interface outside
crypto ca trustpool policy
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 10
crypto ikev2 policy 20
crypto ikev2 policy 30
crypto ikev2 policy 40
crypto ikev2 enable outside
tftp-server inside 192.168.17.253 HQASA-confg
group-policy GroupPolicy_*.*.*.* internal
group-policy GroupPolicy_*.*.*.* attributes
vpn-tunnel-protocol ikev1 ikev2
dynamic-access-policy-record DfltAccessPolicy
quota management-session 3
tunnel-group *.*.*.* type ipsec-l2l
tunnel-group *.*.*.* general-attributes
default-group-policy GroupPolicy_*.*.*.*
tunnel-group *.*.*.* ipsec-attributes
ikev1 pre-shared-key *****
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
!
: end
Config of Remote ASA (192.168.1.201)
hostname Remote-ASA
names
name 192.168.16.0 NET
name 192.168.6.0 IP-PHONE
name 192.168.14.0 VPN
ip local pool VPN-POOL 192.168.14.10-192.168.14.250 mask 255.255.255.0
!
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address *.*.*.* 255.255.255.192
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.1.201 255.255.255.0
!
ftp mode passive
object network NET
subnet 192.168.16.0 255.255.252.0
object network NETWORK_OBJ_192.168.1.0_24
subnet 192.168.1.0 255.255.255.0
object network NETWORK_OBJ_192.168.14.0_24
subnet 192.168.14.0 255.255.255.0
object network Wireless_network
subnet 192.168.4.0 255.255.255.0
object network Workstations
subnet 192.168.2.0 255.255.255.0
object network Printers
subnet 192.168.3.0 255.255.255.0
object network RemoteVPN
subnet 10.20.10.0 255.255.255.0
object-group network DM_INLINE_NETWORK_1
network-object 192.168.1.0 255.255.255.0
network-object object Wireless_network
network-object object Workstations
access-list outside_cryptomap extended permit ip object Workstations object NET
access-list outside_cryptomap extended permit ip object Wireless_network object NET
access-list outside_cryptomap extended permit ip 192.168.1.0 255.255.255.0 object NET
access-list outside_cryptomap extended permit ip 192.168.6.0 255.255.255.0 object NET
access-list outside_cryptomap extended permit ip object-group DM_INLINE_NETWORK_1 object RemoteVPN
access-list remote_splitTunnelAcl standard permit 192.168.1.0 255.255.255.0
access-list outside_cryptomap_65535.65535 extended permit ip any any
access-list riverbed_tcp extended permit tcp any any
!
tcp-map allow-probes
tcp-options range 76 78 allow
!
nat (inside,outside) source static NETWORK_OBJ_192.168.1.0_24 NETWORK_OBJ_192.168.1.0_24 destination static NETWORK_OBJ_192.168.14.0_24 NETWORK_OBJ_192.168.14.0_24 no-proxy-arp route-lookup
route outside 0.0.0.0 0.0.0.0 68.93.159.194 1
route inside 192.168.2.0 255.255.255.0 192.168.1.1 1
route inside 192.168.4.0 255.255.255.0 192.168.1.1 1
route inside IP-PHONE 255.255.255.0 192.168.1.1 1
aaa-server RADIUSSERVERS protocol radius
aaa-server RADIUSSERVERS (inside) host 192.168.1.245
timeout 5
key *****
user-identity default-domain LOCAL
snmp-server host-group inside NETWORK_OBJ_192.168.1.0_24 poll community ***** version 2c
no snmp-server location
no snmp-server contact
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
!—output omitted--!
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 match address outside_cryptomap_65535.65535
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set pfs
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 1 match address outside_cryptomap
crypto map outside_map 1 set peer *.*.*.*
crypto map outside_map 1 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map outside_map interface outside
crypto ca trustpool policy
group-policy GroupPolicy_*.*.*.*internal
group-policy GroupPolicy_*.*.*.*attributes
vpn-tunnel-protocol ikev1 ikev2
group-policy remote internal
group-policy remote attributes
dns-server value 192.168.1.245 192.168.1.49
vpn-tunnel-protocol ikev1
split-tunnel-policy tunnelspecified
split-tunnel-network-list value remote_splitTunnelAcl
default-domain value *.*.*.*.local
dynamic-access-policy-record DfltAccessPolicy
tunnel-group *.*.*.* type ipsec-l2l
tunnel-group *.*.*.*general-attributes
default-group-policy GroupPolicy_*.*.*.*
tunnel-group *.*.*.* ipsec-attributes
ikev1 pre-shared-key *****
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
tunnel-group remote type remote-access
tunnel-group remote general-attributes
address-pool VPN-POOL
authentication-server-group RADIUSSERVERS
default-group-policy remote
tunnel-group remote ipsec-attributes
ikev1 pre-shared-key *****
!
class-map tcp-traffic
!—output omitted--!
: end
Config of Remote Router (L3 Switch)
interface Vlan1
description Servers
ip address 192.168.1.1 255.255.255.0
no ip unreachables
ip route 10.20.10.0 255.255.255.0 192.168.1.201
ip route 192.168.14.0 255.255.255.0 192.168.1.201
ip route 192.168.16.0 255.255.252.0 192.168.1.201
ip access-list standard 10
80 permit 192.168.16.0 0.0.3.255
90 permit 192.168.14.0 0.0.0.255
140 permit 10.20.10.0 0.0.0.255
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2020 12:54 AM
Hello,
where is network 192.168.16.0, the one specified in the split tunnel ACL ?
Either way, make the changes/additions marked in bold to the ASA (the one on the left):
--> access-list remote_splitTunnelAcl standard permit 192.168.0.0 255.255.0.0
ip local pool vpnPool 10.20.10.1-10.20.10.250 mask 255.255.255.0
--> object network OBJ-VPN-POOL
--> subnet 10.20.10.0 255.255.255.0
webvpn
--> enable outside
group-policy remote internal
group-policy remote attributes
dns-server value 192.168.17.4 192.168.17.2
vpn-tunnel-protocol IPSec
split-tunnel-policy tunnelspecified
split-tunnel-network-list value remote_splitTunnelAcl
default-domain value data-path.net
tunnel-group remote type remote-access
tunnel-group remote general-attributes
address-pool vpnPool
authentication-server-group RADIUS
default-group-policy remote
tunnel-group remote ipsec-attributes
pre-shared-key ******
--> nat (inside,outside) 2 source static any any destination static OBJ-VPN-POOL OBJ-VPN-POOL no-proxy-arp route-lookup
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2020 01:32 AM
Hello,
The network 192.168.16.0/22 is the HQ network
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2020 01:43 AM
Hello,
The command are not working for the ASA, the version is Cisco Adaptive Security Appliance Software Version 8.2(5) can you please provide the commands that will work on this version?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2020 10:36 PM
Can anyone help please? Still stuck with this!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide