- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Routing between two LAN interfaces on ISR 4431 router
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2019 10:40 AM
Hi, am a newb with IOS routers, so I think I have a simple mistake somewhere in my routing config. Have two LAN interfaces and one WAN. LAN interface routes to internet with no issues. It is connected to Core Switch via an access vlan. DMZ interface is also connected to core switch via an isolated private vlan (no gateway on core switch). DMZ interface also routes to internet, no problem. PCs on DMZ can also ping PCs on LAN interface. PCs on LAN cannot ping anything on DMZ interface. I do have Zone-Based Firewall turned on, but when I do debugs it shows that packet as being forwared and no drops. Here is the related config info. What am I missing?
--Router Config-- interface GigabitEthernet0/0/0 description WAN Interface ip address 7.7.7.7 255.255.255.224 ip nat outside zone-member security OUTSIDE negotiation auto interface GigabitEthernet0/0/2 ip address 192.168.8.5 255.255.255.248 description LAN Interface ip nat inside zone-member security INSIDE negotiation auto spanning-tree portfast disable interface GigabitEthernet0/0/3 description DMZ Interface ip address 192.168.15.1 255.255.255.0 ip nat inside zone-member security DMZ negotiation auto spanning-tree portfast disable ip route 0.0.0.0 0.0.0.0 7.7.7.1 permanent ip route 172.16.200.0 255.255.252.0 192.168.8.1 permanent ip nat inside source route-map nat_traffic interface GigabitEthernet0/0/0 overload ip forward-protocol nd route-map nat_traffic permit 10 match ip address NAT_ACL ip access-list NAT_ACL deny ip 172.16.200.0 0.0.3.255 192.168.15.0 0.0.0255 permit ip 192.168.15.0 0.0.0.255 any ---Core Switch Config --- interface GigabitEthernet4/0/41 description Uplink to ISR Router LAN switchport access vlan 8 switchport mode access spanning-tree portfast spanning-tree bpduguard enable interface Vlan8 ip address 192.168.8.1 255.255.255.248 interface GigabitEthernet4/0/40 description Uplink to ISR Router DMZ switchport access vlan 15 switchport mode access spanning-tree portfast spanning-tree bpduguard enable (NOTE: No interface for vlan 15, router will act as gateway for DMZ) ip route 0.0.0.0 0.0.0.0 192.168.8.2 permanent (Note: This is an ASA on the nework that currently has most Internet traffic going through it) ip route 192.168.15.0 255.255.255.0 192.168.8.5 permanent
So routing from DMZ to LAN seems to work with no issues. Routing from LAN to DMZ is not working. I did not include configs for ZoneBased Firewall as I don't think that is the issue. If I do a traceroute from PC on LAN to DMZ it does show that the packet is being routed to 192.168.8.5 as it should be. I can also ping PCs on both LAN and DMZ from the router. Also 172.16.200.0/22 network has it's gateway on the core switch, and routes to the internet through the ASA. I CAN ping gateway of 192.168.15.1 from PCs on 172.16.200.0/22 network.
Solved! Go to Solution.
- Labels:
-
ISR 4000 Series
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2019 07:23 PM
Well, after four hours on the phone with TAC and two different engineers, we have a solution. Nothing wrong at all with my config. Am embarrassed to admit this, but the problem turned out to be a Windows 10 firewall on the laptop I was using to test with. I had previously turned the firewall off, and assumed it was still off being I was able to ping the laptop from the router.
Two things I did not know. When you reboot Windows 10, it likes to turn the firewall back on. I had to modify a windows group policy to make the firewall stay off between reboots. Also, apparently windows firewall rules allow pings from devices on it's own subnet, but not from devices outside it's subnet, unless you add or modify it's rules.
In my defense, I am a Linux guy, and seldom use Windows : - ). Hopefully someone will read this and learn from my stupidity.
Thank you Paul and others for your attempts to help me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2019 12:09 PM
Hello,
I am not clear on your topology: you have two LAN interfaces, and how many switches ? If you have several Vlans on one switch and want to connect that switch to a router, you need to configure the port on the switch as a trunk, and configure subinterfaces on the router interface.
Post a schematic drawing showing your devices, and how they are connected...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2019 02:40 PM
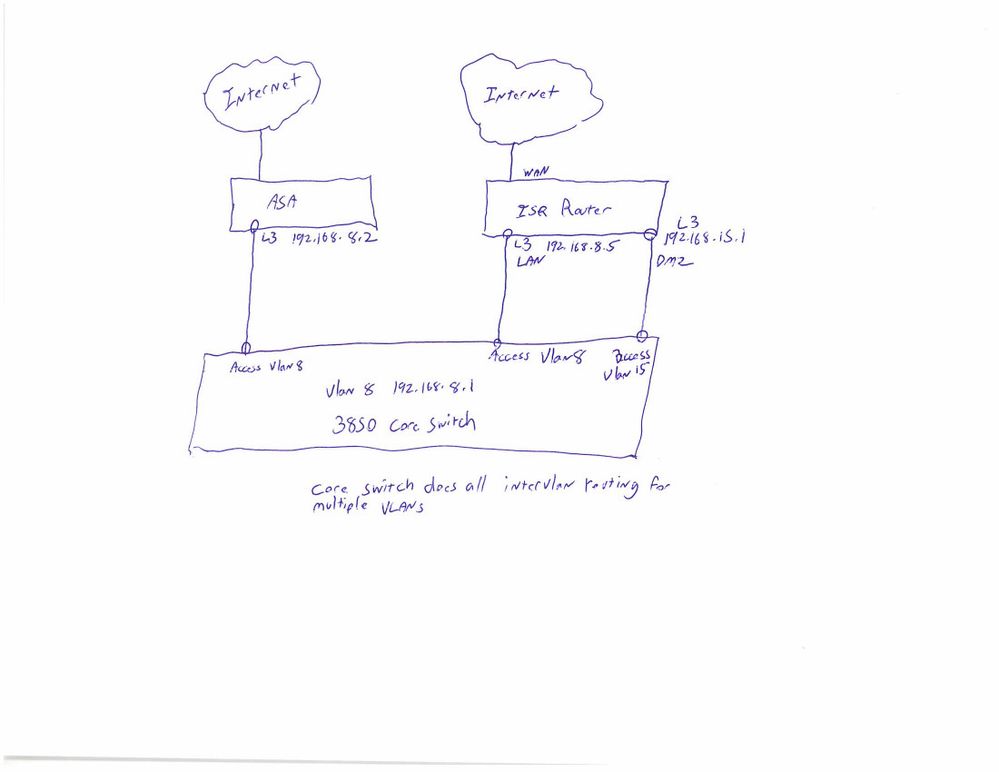
Hi Georg, hope this diagram helps. So there are multiple switches and vlans on my network. The 3850 does all intervlan routing and has all other gateways for all the vlans. Switchport connections to ASA and ISR are all vlan access. Vlan 8 for LAN and for ASA. Vlan 15 for DMZ. Gateway for DMZ is on Router and not 3850. I have done this kind of setup before with no issues and have not had to do trunked ports. Reason being is that the interfaces on the ASA and router are L3 interfaces, which allows me to do static routes on the 3850 to point to them. Is that not possible on ISR router?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2019 03:22 PM
Hello,
I don't see how your LAN can access the Internet through the ISR, since you are not even NATting the LAN range.
Either create a Vlan 15 interface with an IP address on the 3850, or use a subinterface for the DMZ on the ISR:
interface GigabitEthernet0/0/3.15
encapsulation dot1q 15
description DMZ Interface
ip address 192.168.15.1 255.255.255.0
ip nat inside
zone-member security DMZ
negotiation auto
spanning-tree portfast disable
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2019 03:37 PM
I believe the LAN accesses Internet through the ASA, not through the ISR.
One thing I could suggest is to modify the ACL as follows:-
ip access-list NAT_ACL
deny ip 172.16.200.0 0.0.3.255 192.168.15.0 0.0.0.255 ! Not needed for now
deny ip 192.168.15.0 0.0.0.255 172.16.200.0 0.0.3.255
permit ip 192.168.15.0 0.0.0.255 any
HTH,
Meheretab
Meheretab
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2019 04:15 PM
Correct. 172.16.200.0/22 accesses the internet through the ASA. The 192.168.8.0 network is basically for routers, firewalls, etc. I did try removing the entry on the NAT_ACL, but that did not make a difference. Originally put it there because I thought perhaps the packets were hitting the route map to the internet. I could try and do the subinterfaces and vlans as suggested, just don't understand why my config is not working. I have done this type of setup with non cisco routers as well as the ASA. Gotta be something I am overlooking.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2019 02:00 PM - edited 09-17-2019 02:01 PM
Hello
@CW7 wrote:So routing from DMZ to LAN seems to work with no issues. Routing from LAN to DMZ is not working. I did not include configs for ZoneBased Firewall as I don't think that is the issue. If I do a traceroute from PC on LAN to DMZ it does show that the packet is being routed to 192.168.8.5 as it should be. I can also ping PCs on both LAN and DMZ from the router. Also 172.16.200.0/22 network has it's gateway on the core switch, and routes to the internet through the ASA. I CAN ping gateway of 192.168.15.1 from PCs on 172.16.200.0/22 network.
So to confirm -
172.16.200.0/22 hangs off GigabitEthernet0/0/2
192.168.15.0 can initiate ping (echo) to 192.168.8.0/29 and replies ( icmp echo-reply)
However 192.168.8.0/29 can initiate ping (echo) to 192.168.15.0 cannot reply ( icmp echo-reply)
Have you tried removing this static route ip route 192.168.15.0 255.255.255.0 192.168.8.5 permanent ?
As looking at your config -
ip route 0.0.0.0 0.0.0.0 7.7.7.1 permanent <----via gig0/0/0
ip route 172.16.200.0 255.255.252.0 192.168.8.1 permanent <----GigabitEthernet0/0/2
ip route 192.168.15.0 255.255.255.0 192.168.8.5 permanent <----GigabitEthernet0/0/2 - However you have connected interface for this subnet already (GigabitEthernet0/0/3) so this static isn't really going to work.
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2019 03:49 PM
Correct, 172.16.200.0/22 (vlan 200) has its gateway on 3850 and is indirectly connected to ISR via ISR gi 0/0/2. It should be able to reach the ISR via static routing over vlan 8. Yes I can ping 8.0 network from ISR router. As I understand it, my static routing should work. On the core switch the default route is:
ip route 0.0.0.0 0.0.0.0 192.168.8.2 permanent
So, anything that switch does not know what do to with is routed to the ASA (192.168.8.2) and out to the internet.
The route:
ip route 172.16.200.0 255.255.252.0 192.168.8.1 permanent
is there to tell other vlans on the core switch how to reach devices on that vlan.
The Router gi 0/0/2 192.168.8.5 (LAN interface) gives me my connection to main switch and all other vlans.
The Router DMZ interface 192.168.15.1 connects to the router via vlan 15 on the core switch. Vlan 15 on the core switch has no ip address assigned to it, because I want all routing to be done on the ISR router. It is a private vlan. All routing to it will be done on ISR router and not on ASA or Core Switch.
So if I am on PC 172.16.200.2 and ping 192.168.15.5, the packet routes to gateway 172.16.200.1 on core switch, and should be routed to 192.168.8.5 via the static route:
ip route 192.168.15.0 255.255.255.0 192.168.8.5 permanent
on the core switch. Device should respond to ping and be routed back out gi 0/0/2 to core switch and vlan 200.
If I do a trace route from 172.16.200.2 pc it does show packet going to 192.168.8.5, but it times out after that.
I know this is a wonky setup. It is not permanent. I am replacing the ASA with router, but want to test everything to be sure it works as expected, before I do the cutover.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2019 05:34 PM - edited 09-18-2019 12:18 AM
Hello
Apologies maybe i am missing something here but...-
@CW7 wrote:
ip route 172.16.200.0 255.255.252.0 192.168.8.1 permanent
is there to tell other vlans on the core switch how to reach devices on that vlan
I would say this static route is on the asr so the asr plus the dmz can reach 172.16.200.0/22 L3 interface residing on the core switch and I would expect the core to have a static pointing to the ASR lan interface 192.168.8.5 to reach the DMZ subnet on the ASR
However ---
@CW7 wrote:
The Router DMZ interface 192.168.15.1 connects to the router via vlan 15 on the core switch. Vlan 15 on the core switch has no ip address assigned to it, because I want all routing to be done on the ISR router. It is a private vlan. All routing to it will be done on ISR router and not on ASA or Core Switch
ip route 192.168.15.0 255.255.255.0 192.168.8.5 permanent
As this subnet 192.168.15.0/24 resides on the ASR via its L3 interface gig0/0/3 and not on the core then this static isnt required , in fact you dont even need a vlan 15 interface on the core with no ip address.
I am also wondering if that gigi0/0/3 on the asr needs to be a sub-interface with encapsulation for vlan 15 for tagging of its host traffic- I think this was already mentioned in another post , so you could try the following?.
ASR
conf t
int gig0/0/3
no ip address
int gig0/0/3.15
encapsulation dot1q 15
ip address 192.168.15.1 255.255.255.0
exit
no ip route 192.168.15.0 255.255.255.0 192.168.8.5 permanent
Would it be possible to post the config of your core switch?
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2019 08:33 AM
Hi Paul,
I did post part of the config of my core switch in my first post. I think you have been thinking some of the static routes on my core switch were on my ISR router. Here it is the relevant portion of config on my core switch. I will try your suggestions about sub interface and removing the static route, and let you know. Thanks.
---Core Switch Config --- interface GigabitEthernet4/0/41 description Uplink to ISR Router LAN switchport access vlan 8 switchport mode access spanning-tree portfast spanning-tree bpduguard enable interface Vlan8 ip address 192.168.8.1 255.255.255.248 interface vlan 200 ip address 172.16.200.1 255.255.252.0 interface GigabitEthernet4/0/40 description Uplink to ISR Router DMZ switchport access vlan 15 switchport mode access spanning-tree portfast spanning-tree bpduguard enable (NOTE: No interface for vlan 15, router will act as gateway for DMZ) ip route 0.0.0.0 0.0.0.0 192.168.8.2 permanent ip route 192.168.15.0 255.255.255.0 192.168.8.5 permanent
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2019 08:42 AM - edited 09-18-2019 08:43 AM
Hello
okay the static route for the DMZ is indeed applied on the core so have a go at the suggested config for the ASR and let us know the outcome?
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2019 09:18 AM
Well, unfortuneately that did not work. I understand your thinking though. I think the issue is definitely a layer 2, layer 3 confusion thing. If I put a gateway on the core switch for vlan 15, it would work. However if I do that all Vlans will be able to access the DMZ via the Core Switch. Would defeat the purpose of a DMZ. I could do vlan filtering on Core Switch to restrict access, but speaking from experience vlan filtering is a poor solution. I had a situaltion once where I temporarily had to do a bunch of vlan filters and the performance hit on the switch was significant. Unless you have any other ideas, I am going to open a case with TAC and see if they have a solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2019 07:23 PM
Well, after four hours on the phone with TAC and two different engineers, we have a solution. Nothing wrong at all with my config. Am embarrassed to admit this, but the problem turned out to be a Windows 10 firewall on the laptop I was using to test with. I had previously turned the firewall off, and assumed it was still off being I was able to ping the laptop from the router.
Two things I did not know. When you reboot Windows 10, it likes to turn the firewall back on. I had to modify a windows group policy to make the firewall stay off between reboots. Also, apparently windows firewall rules allow pings from devices on it's own subnet, but not from devices outside it's subnet, unless you add or modify it's rules.
In my defense, I am a Linux guy, and seldom use Windows : - ). Hopefully someone will read this and learn from my stupidity.
Thank you Paul and others for your attempts to help me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2019 02:55 AM
Hello
Sometimes the solution is as simile as a software FW - I think what was cause for confusion was the ability to be able to ping and then your not being able to, and not knowing your pc automatically turning back on its fw.
So glad you got it sorted.
On a side note though i would suggest for clarity you still look at your setup regards that static route on the ASR and having its interface as subinterface
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: