- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: shaping traffic
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2010 03:55 AM - edited 03-04-2019 10:05 AM
Hello all
Please help me to write configuraion for my cisco router (Cisco 2811, c2800nm-ipbase-mz.124-3i.bin) for shaping traffic incoming from Internet, but set best bandwidth between local networks (VLANed networks - VLAN1-servers VLAN and VLAN30-other users VLAN)
My network configuration:
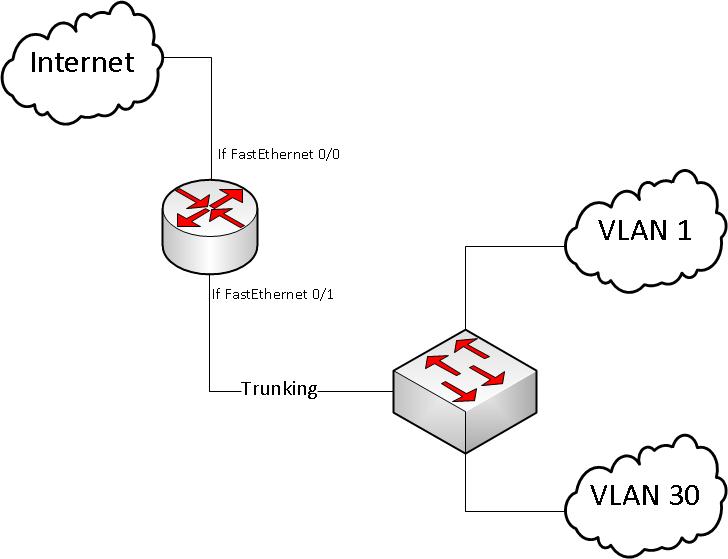
Configuration of my router:
Cisco-R1#show running-config
Building configuration...
Current configuration : 3695 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Cisco-R1
!
boot-start-marker
boot-end-marker
!
enable secret 5 XXXXXXXXXXXXXXXXXXXXXXXXX
!
no aaa new-model
!
resource policy
!
ip subnet-zero
!
!
ip cef
no ip dhcp use vrf connected
ip dhcp excluded-address 10.0.0.78
!
ip dhcp pool ***OTHER's***
network 10.0.0.64 255.255.255.240
dns-server 192.232.0.1
default-router 10.0.0.78
domain-name others.iwt.local
lease 8
!
!
username cisco secret 5 XXXXXXXXXXXXXXXXXXX
!
!
class-map match-all admin2
match access-group 101
class-map match-all admin
match access-group 140
!
!
policy-map admins
class admin
shape average 128000
class admin2
set precedence 5
!
!
!
interface FastEthernet0/0
ip address 192.232.0.1 255.255.255.224
ip nat outside
duplex auto
speed auto
traffic-shape group 140 512000 12800 12800 1000
!
interface FastEthernet0/1
no ip address
ip nat inside
duplex auto
speed auto
!
interface FastEthernet0/1.1
description *** Server's VLAN1 ***
encapsulation dot1Q 1 native
ip address 10.0.0.3 255.255.255.240
ip nat inside
no snmp trap link-status
no cdp enable
!
interface FastEthernet0/1.2
description *** Sales Users VLAN2 ***
encapsulation dot1Q 2
ip address 10.0.0.30 255.255.255.240
ip nat inside
no snmp trap link-status
no cdp enable
!
interface FastEthernet0/1.10
description *** Tech Users VLAN10 ***
encapsulation dot1Q 10
ip address 10.0.0.46 255.255.255.240
ip nat inside
no snmp trap link-status
no cdp enable
!
interface FastEthernet0/1.20
description *** Service Users VLAN20 ***
encapsulation dot1Q 20
ip address 10.0.0.54 255.255.255.248
ip nat inside
no snmp trap link-status
no cdp enable
!
interface FastEthernet0/1.30
description *** Other Users VLAN30 ***
encapsulation dot1Q 30
ip address 10.0.0.78 255.255.255.240
ip access-group other's in
ip nat inside
no snmp trap link-status
no cdp enable
!
interface FastEthernet0/1.40
description *** Admin's ***
encapsulation dot1Q 40
ip address 10.0.0.102 255.255.255.248
ip access-group admin's in
ip nat inside
no snmp trap link-status
no cdp enable
!
ip classless
ip route 0.0.0.0 0.0.0.0 192.232.0.30
!
no ip http server
ip nat inside source list 10 interface FastEthernet0/0 overload
!
ip access-list extended admin's
permit tcp any any eq ftp-data
permit tcp any any eq ftp
permit tcp any any eq 22
permit tcp any any eq telnet
permit tcp any any eq www
permit tcp any any eq domain
permit udp any any eq domain
permit tcp any any eq 443
permit tcp any any eq 3389
permit tcp any any eq 13389
permit tcp any 10.0.0.0 0.0.0.255
permit udp any 10.0.0.0 0.0.0.255
permit tcp any host 192.232.0.1 eq smtp
permit tcp any host 192.232.0.1 eq pop3
permit icmp any any
ip access-list extended other's
permit tcp any any eq ftp-data
permit tcp any any eq ftp
permit tcp any any eq 22
permit tcp any any eq telnet
permit tcp any any eq www
permit tcp any any eq domain
permit udp any any eq domain
permit tcp any any eq 443
permit tcp any any eq 3389
permit tcp any any eq 13389
permit tcp any 10.0.0.0 0.0.0.255
permit udp any 10.0.0.0 0.0.0.255
permit tcp any host 192.232.0.1 eq smtp
permit tcp any host 192.232.0.1 eq pop3
permit icmp any any
!
access-list 10 permit 10.0.0.0 0.0.0.255
access-list 101 permit ip 10.0.0.0 0.0.0.255 any
access-list 101 permit ip 10.0.0.0 0.0.0.255 10.0.0.96 0.0.0.7
access-list 140 permit ip any 10.0.0.96 0.0.0.7
no cdp run
!
control-plane
!
!
line con 0
login local
line aux 0
login local
line vty 0 4
login local
!
scheduler allocate 20000 1000
!
end
Solved! Go to Solution.
- Labels:
-
Other Routing
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2010 03:34 AM
Hi Osman,
shaping is not the perfect tool to "limit the bandwidth to the users", because it just delays the traffic in internal buffers before sending it.
Use a policer instead and that should do the job.
Can you also clarify what you mean with "Today, this configuration works, but the truth is I do not know whether I made that used..."?
Regards,
Antonio
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2010 05:30 AM
Osman,
If you have the techs in a subnet, you can police the web traffic or the p2p traffic to say 512Kbps.
i.e just the internet traffic.
For mails and business critical applications, you can use the extended access list to match on the port numbers and give a better bandwidth to them.
You can control and utilize the 10Mbps BW well enough to meet all of your requirement.
HTH,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2010 06:12 AM
Hello!
Inbound traffic shaping has is not a good behavior unless you want to have different bandwith for different traffic. As an example let's say you have 10Mbps total bandwidth from your provider and you want 5Mbps for business traffic, 3Mbps for e-mail, ftp and 2Mbps for http and other kind of traffic.
In other cases inbound traffic shaping shaping in not recommend as you will cut your own bandwidth.
To be able to help you, we need more detail. What do you have (details like bandwidth) and what do you want to achieve (traffic shaping, traffic prioritization...) in clear objectives.
Cheers,
Calin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2010 07:14 AM
Hi Osman,
as far as I know shaping is always used outbound, never inbound (what arrived is already arrived, so why shaping it?).
If you look at the documentation of the "traffic-shape group" command:
http://www.cisco.com/en/US/partner/docs/ios/12_2/qos/command/reference/qrfcmd11.html#wp1019905
it's indeed stated very clearly:
"To enable traffic shaping based on a specific access list for outbound traffic on an interface"
^^^^^^^^^^^^^^^^^^^^^^
Moreover it's not clear to me what's your goal: to limit the bandwidth toward the users or to optimize the usage of the Internet bandwidth?
Regards,
Antonio
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2010 08:31 AM
Main task - to limit the bandwidth toward the users
I solve my task using policy-map
My final configuration the router next:
Cisco-R1#show run
Building configuration...
Current configuration : 5527 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Cisco-R1
!
boot-start-marker
boot-end-marker
!
enable secret 5 XXXXXXXXXXXXXXXXXXXXXX
!
no aaa new-model
!
resource policy
!
ip subnet-zero
!
ip cef
no ip dhcp use vrf connected
ip dhcp excluded-address 10.0.0.78
ip dhcp excluded-address 10.0.0.33 10.0.0.37
ip dhcp excluded-address 10.0.0.46
ip dhcp excluded-address 10.0.0.45
!
ip dhcp pool ***OTHER's***
network 10.0.0.64 255.255.255.240
dns-server 192.232.0.1
default-router 10.0.0.78
domain-name others.local
lease 8
!
username Cisco secret 5 XXXXXXXXXXXXXXXXXX
!
!Here i define classes usin for the classification traffic based on ACL
!ACL 101 define packets from Local server (VLAN 1)
!and specific ALC for users network who will be shaped (VLAN 10, VLAN 20)
class-map match-any service's
match access-group 130
class-map match-any tech's
match access-group 110
class-map match-any local
match access-group 101
!
!My Policy-map that used shaping traffic for the corresponding classes
policy-map service's
class local
shape average 154400000 154400000 154400000
class service's
shape average 524288 524288 524288
policy-map tech's
class local
shape average 154400000 154400000 154400000
class tech's
shape average 524288 524288 524288
!
interface FastEthernet0/0
ip address 192.232.0.1 255.255.255.224
ip nat outside
duplex full
speed auto
!
interface FastEthernet0/0.30
no cdp enable
!
interface FastEthernet0/0.40
no cdp enable
!
interface FastEthernet0/1
no ip address
ip nat inside
duplex auto
speed auto
!
interface FastEthernet0/1.1
description *** Server's VLAN1 ***
encapsulation dot1Q 1 native
ip address 10.0.0.3 255.255.255.240
ip nat inside
no snmp trap link-status
no cdp enable
!
interface FastEthernet0/1.2
description *** Sales Users VLAN2 ***
encapsulation dot1Q 2
ip address 10.0.0.30 255.255.255.240
ip nat inside
no snmp trap link-status
no cdp enable
!
interface FastEthernet0/1.10
description *** Tech Users VLAN10 ***
encapsulation dot1Q 10
ip address 10.0.0.46 255.255.255.240
ip access-group tech's in
ip nat inside
no snmp trap link-status
! In this configuration i use the policy-map for outgoing way
no cdp enable
service-policy output tech's
!
interface FastEthernet0/1.20
description *** Service Users VLAN20 ***
encapsulation dot1Q 20
ip address 10.0.0.54 255.255.255.248
ip access-group service's in
ip nat inside
no snmp trap link-status
no cdp enable
service-policy output service's
!
interface FastEthernet0/1.30
description *** Other Users VLAN30 ***
encapsulation dot1Q 30
ip address 10.0.0.78 255.255.255.240
ip access-group other's in
ip nat inside
no snmp trap link-status
no cdp enable
!
interface FastEthernet0/1.40
description *** Admin's ***
encapsulation dot1Q 40
ip address 10.0.0.102 255.255.255.248
ip access-group admin's in
ip nat inside
no snmp trap link-status
no cdp enable
!
ip classless
ip route 0.0.0.0 0.0.0.0 192.232.0.30
!
no ip http server
ip nat inside source list 10 interface FastEthernet0/0 overload
!
ip access-list extended admin's
permit tcp any any eq ftp-data
permit tcp any any eq ftp
permit tcp any any eq 22
permit tcp any any eq telnet
permit tcp any any eq www
permit tcp any any eq domain
permit udp any any eq domain
permit tcp any any eq 443
permit tcp any any eq 2802
permit tcp any any eq 3389
permit tcp any any eq 5190
permit tcp any any eq 13389
permit tcp any any eq 44567
permit tcp any 10.0.0.0 0.0.0.255
permit udp any 10.0.0.0 0.0.0.255
permit tcp any host 192.232.5.1 eq smtp
permit tcp any host 192.232.5.1 eq pop3
permit icmp any any
ip access-list extended other's
permit tcp any any eq ftp-data
permit tcp any any eq ftp
permit tcp any any eq 22
permit tcp any any eq telnet
permit tcp any eq 68 any eq 67
permit tcp any any eq www
permit tcp any any eq domain
permit udp any any eq domain
permit tcp any any eq 443
permit tcp any any eq 3389
permit tcp any any eq 13389
permit tcp any 10.0.0.0 0.0.0.255
permit udp any 10.0.0.0 0.0.0.255
permit tcp any host 192.232.5.1 eq smtp
permit tcp any host 192.232.5.1 eq pop3
permit icmp any any
!
access-list 10 permit 10.0.0.0 0.0.0.255
access-list 101 permit ip 10.0.0.0 0.0.0.255 any
access-list 101 permit ip 10.0.0.0 0.0.0.255 10.0.0.96 0.0.0.7
access-list 110 permit ip any 10.0.0.32 0.0.0.15
access-list 130 permit ip any 10.0.0.48 0.0.0.7
access-list 140 permit ip any 10.0.0.96 0.0.0.7
no cdp run
!
control-plane
!
!
line con 0
login local
line aux 0
login local
line vty 0 4
login local
!
scheduler allocate 20000 1000
!
end
Today, this configuration works, but the truth is I do not know whether I made that used...![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2010 03:34 AM
Hi Osman,
shaping is not the perfect tool to "limit the bandwidth to the users", because it just delays the traffic in internal buffers before sending it.
Use a policer instead and that should do the job.
Can you also clarify what you mean with "Today, this configuration works, but the truth is I do not know whether I made that used..."?
Regards,
Antonio
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2010 04:59 AM
Hi
Okay, since you gave me an answer. I use policer.
Thanks for all. ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2010 08:12 AM
Osman,
We wish you have a better configuration.
Where did you apply the service policy ? As output to the users ?
Why do you want to slow down packets to the users from the internet ?
Or do you really intend to slow down the burst to the Servers ?
Why did you apply the policy towards the tech's ?
How much is the speed/BW of your Internet ?
i know its all questions, but we wish to help you out get the best config up there.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2010 10:34 AM
Ok.
First, I apply my policy at output interface of my router, as output to the users
Second, I want to slow down for some users who use the torrent applications. And many users of the sales department, management department can't work with business-critical applications
Third, I have only 10 Mbps Internet bandwidth for all users of the company and the main server (application server, Web, DNS, MAIL, FTP - servers). And now, I need a form of movement for better control of the technical department, where some guys hinder work by downloading the Internet channe
Today in our region (Russian Federation, Daghestan Republic), 1 Megabit Internet channel is 312.5 $. For our company, the total cost of $ 3,125 per month
Thank you for your interest
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2010 05:30 AM
Osman,
If you have the techs in a subnet, you can police the web traffic or the p2p traffic to say 512Kbps.
i.e just the internet traffic.
For mails and business critical applications, you can use the extended access list to match on the port numbers and give a better bandwidth to them.
You can control and utilize the 10Mbps BW well enough to meet all of your requirement.
HTH,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2010 08:17 AM
Thank you all for your support ![]()
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
