- Cisco Community
- Technology and Support
- Networking
- Routing
- simulating ICMP redirecting attack on laboratory network
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2012 02:37 AM - edited 03-04-2019 05:51 PM
Hello,
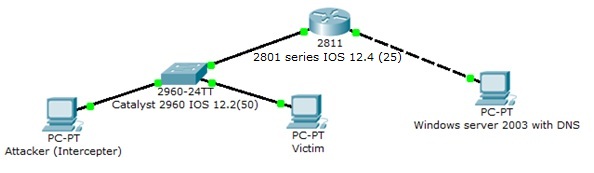
I study at University of Ostrava and currently I am working on my master thesis. Its content is realization of few attacks on network. Now I am trying to implement ICMP redirecting attack by using Intercepter program. Diagram of my netwok you can see on enclosed picture (Schema.jpg). Through Intercepter program I generate packets ICMP redirect (ICMP type 5), which are successfully sent from PC Attacker, but these packets do not arrive to PC Victim and Warshark shows me messages „ Destination Unreachable (Host Unrecheable).“ When I use instead of Cisco switch non Cisco switch (for example: Edimax) or hub, ICMP redirects packets arrive to PC Victim and I can continue in the attack.
As I could not find out the reason of unsuccessfulness of the attacks, I would like to ask you if you could not recommend some literature (or web link), which describe this type of problematics. Or if you would be so kind and help me to clarify, what cause this problem.
SW:
Switch is in the defautl setting
Cisco Catalyst 2960 IOS: c2960-lanbasek9-mz.122-50.SE3.bin
Router:
Set only IP address on FastEthernet interfaces
Cisco 2801 IOS: 2801-ipbasek9-mz 124.25f.bin
Solved! Go to Solution.
- Labels:
-
Other Routing
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2012 01:53 PM
Hello Rene,
It seems that your ICMP Redirect packets are sourced from an illegal source MAC address. Currently, you are using 01:02:03:04:05:06. However, this is wrong: if the first octet of a MAC address is an odd number (i.e. the lowmost bit of the first octet in the MAC address is set to 1), this MAC address is considered a group address. Group addresses are illegal as source MAC addresses - they can be correctly used only as destination MAC addresses. Cisco Catalyst switches check the validity of source MAC addresses and may drop frames sourced from illegal MAC addresses. Thus, the ICMP Redirect packets never make it to the victim. That may be the cause of your problems.
If you want to use your own MAC address then I suggest setting the first MAC address octet to 0x02. The second lowmost bit of the first octet in the address is the so-called U/L (Universal/Local) bit. If set to 1, it declares that this MAC address has been locally assigned and is not an official IEEE OUI-based address - ideal for your needs, so e.g. 02:11:12:13:14:15.
Give it a try please.
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2012 08:42 AM
Hi Rene,
You've got a nice thesis at your hand. Good luck with it.
Regarding the ICMP Redirect message, it actually surprises me that the Cisco switch should in any way interfere with the ICMP message that is not destined to it. Can you describe how is the Cisco switch configured? Ideally, post its configuration here. In addition, please also describe the entire IP settings of the Interceptor and the Victim PC. Also, please try to attach the stored capture file from the Wireshark that shows the unexpected ICMP messages.
Thanks!
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2012 02:39 PM
Hi Peter,
thak you very much for your reply.
Switch was in default setting, bellow you can see running configuration:
Current configuration : 1244 bytes ! version 12.2 no service pad service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname Switch ! boot-start-marker boot-end-marker ! ! no aaa new-model system mtu routing 1500 ! ! ! spanning-tree mode pvst spanning-tree extend system-id ! vlan internal allocation policy ascending ! ! interface FastEthernet0/1 ! interface FastEthernet0/2 ! interface FastEthernet0/3 ! interface FastEthernet0/4 ! interface FastEthernet0/5 ! interface FastEthernet0/6 ! interface FastEthernet0/7 ! interface FastEthernet0/8 ! interface FastEthernet0/9 ! interface FastEthernet0/10 ! interface FastEthernet0/11 ! interface FastEthernet0/12 ! interface FastEthernet0/13 ! interface FastEthernet0/14 ! interface FastEthernet0/15 ! interface FastEthernet0/16 ! interface FastEthernet0/17 ! interface FastEthernet0/18 ! interface FastEthernet0/19 ! interface FastEthernet0/20 ! interface FastEthernet0/21 ! interface FastEthernet0/22 ! interface FastEthernet0/23 ! interface FastEthernet0/24 ! interface GigabitEthernet0/1 ! interface GigabitEthernet0/2 ! interface Vlan1 no ip address ! ip http server ip http secure-server ip sla enable reaction-alerts ! line con 0 line vty 5 15 ! end
Interceptor setting you can see on enclosed picture bellow: (original gateway is IP adress of router, Target IP is IP address of PC Victim, new record is IP address of DNS/web server on Windows 2003 server and New gateway is IP address of PC attacker).

Victim PC setting :
IP address is 192.168.10.2
Mask is 255.255.255.0
Gateway is 192.168.10.254
DNS is 192.168.100.254
I think, problem is not on PC Victim, because when in network was different switch or hub ICMP redirects packets arrive to PC Victim.
Wireshark log of successful arrive ICMP redirect packet and Wireshark log of unsuccessful arrive ICMP redirect packet you can download here from my Dropbox :
https://www.dropbox.com/sh/81fp3zs316a3fi4/2-1pu7HBQd
On first log you can see arp packets and following ICMP redirect packet.
On second log you can see arp packets (5 and 6) but missing ICMP redirect packet behind arp packets.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2012 01:53 PM
Hello Rene,
It seems that your ICMP Redirect packets are sourced from an illegal source MAC address. Currently, you are using 01:02:03:04:05:06. However, this is wrong: if the first octet of a MAC address is an odd number (i.e. the lowmost bit of the first octet in the MAC address is set to 1), this MAC address is considered a group address. Group addresses are illegal as source MAC addresses - they can be correctly used only as destination MAC addresses. Cisco Catalyst switches check the validity of source MAC addresses and may drop frames sourced from illegal MAC addresses. Thus, the ICMP Redirect packets never make it to the victim. That may be the cause of your problems.
If you want to use your own MAC address then I suggest setting the first MAC address octet to 0x02. The second lowmost bit of the first octet in the address is the so-called U/L (Universal/Local) bit. If set to 1, it declares that this MAC address has been locally assigned and is not an official IEEE OUI-based address - ideal for your needs, so e.g. 02:11:12:13:14:15.
Give it a try please.
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2012 12:58 AM
Hi Peter,
Thank you very much for clarifying my problem.
I'll try implement the attack again this week and then I write the result.
Best regards, René
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2012 05:11 AM
Hello Peter,
I changed the MAC address and ICMP redirecting packet arrived on PC victim, so the attack was succesful.
Thank you very much for your help.
Best regards,
René
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2012 05:36 AM
Hello Rene,
Wonderful! Thanks for letting me know Take care, and good luck with your thesis!
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2012 06:26 AM
Hello Peter,
I have another problem with the ICMP redirecting attack
ICMP redirect pakets are successfully sent to computer with Windows 7. This computer receive these packets successfully (verified by Wireshark), but does not change its routing table according to the information contained in the ICMP redirect packet.
PC with Windows XP change its routing table after receive ICMP redirect paket.
I could not find out the reason of unsuccessfulness why routing table is not change in Windows 7. If you would be so kind and help me to clarify, what cause this problem.
Best regards,
René
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2012 07:23 AM
Hi
It is mostly becasue ICMP Redirect is diabled on Windows 7
You can Chnage it from Registery
Start - Run- Regedit
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters
EnableICMPRedirect
Checkif it is 0. 0 means it is disabled. You can change it to 1 if you want to enable this feature
Recommneded Value is 0.
http://msdn.microsoft.com/en-us/library/ff648853.aspx
Thank you
Raju
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2012 07:38 AM
Thak you for your reply.
I am sorry, I forgot to write that I have a value in the registry set to 1.
This is not a solution to this problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2012 07:58 AM
Hi,
maybe a stupid question, but couldn't it be a firewall problem ?
Regards.
Alain
Don't forget to rate helpful posts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2012 08:29 AM
Hi, thank you for your reply.
Theoretically it is possible, but I could not find the Windows firewall settings which allow. I tried to create a new rule that permit ICMP type 5 code 1, but nothing helped.
Best regard, René
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
