- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: VPN Tunnel Transfer Speed Issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VPN Tunnel Transfer Speed Issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2019 10:50 PM
Hi all,
We have 3 VPN tunnels running between 3 sites, two with an ASA-5506, one with an ASA-5505 (although the problem is similar between the different models). Despite our internet connections maxing at 400Mbps, and interoffice transfers at reasonable (Windows) speeds, intersite transfers max out at 20Mbps.
I have read a lot on these community boards in my attempts to fix the issue. My attempts have involved:
- Changing the MTU on the Interface (values from 1400-1500)
- Chainging the IKEv2 Fragmentation settings
- Enable & Disable Fragmentation
- Setting Fragmentation MTU (values between 1380-1460)
- Changing the IPSec Prefragmentation Policies settings:
- Enable/Disabling Pre-Fragmentation
- Changing the DF-Bit Policy between Clear & Copy
No combination of these has resulted in a speed increase. I'm happy to provide more configs. I mainly use the ASDM to configure these but I can do some CLI if needed.
I'm sure I'm missing something, please help me to find out what!
Cheers,
David
- Labels:
-
Routing Protocols
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2019 12:18 AM
Hello,
post the full running configurations of both your ASAs, maybe we can spot something...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2019 12:38 AM
: Hardware: ASA5506, 4096 MB RAM, CPU Atom C2000 series 1250 MHz, 1 CPU (4 cores)
ASA Version 9.7(1)4
hostname gateway
domain-name mydomain.com
enable password XXXX encrypted
ip local pool VPNv4 192.168.192.2-192.168.192.254 mask 255.255.255.0
ipv6 local pool VPNv6 2406:3400:b:43e6::1/123 30
interface GigabitEthernet1/1
nameif outside
security-level 0
ip address XXX.XXX.XXX.XXX (Local) 255.255.255.252
!
interface GigabitEthernet1/2
nameif inside
security-level 100
ip address 192.168.77.2 255.255.255.240
ipv6 address 2406:3400:b:430e::2/64
ipv6 nd suppress-ra
!
interface GigabitEthernet1/3
nameif UserWiFi
security-level 100
ip address 192.168.67.1 255.255.255.0
!
interface GigabitEthernet1/4
nameif GuestWiFi
security-level 90
ip address 192.168.65.1 255.255.255.0
!
interface GigabitEthernet1/5
nameif DMZ
security-level 50
ip address XXX.XXX.XXX.XXX (DMZ) 255.255.255.248
ipv6 nd suppress-ra
!
interface GigabitEthernet1/6
nameif BNETest
security-level 100
ip address 10.0.0.1 255.255.255.0
!
interface GigabitEthernet1/7
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/8
no nameif
no security-level
no ip address
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
ftp mode passive
clock timezone EST 10
clock summer-time EDT recurring last Sun Oct 2:00 last Sun Mar 3:00
dns domain-lookup inside
dns server-group DefaultDNS
mtu outside 1500
mtu inside 1500
mtu UserWiFi 1500
mtu GuestWiFi 1500
mtu DMZ 1500
mtu BNETest 1500
ip verify reverse-path interface outside
ip verify reverse-path interface GuestWiFi
ip verify reverse-path interface DMZ
icmp unreachable rate-limit 100 burst-size 10
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 16384
nat (inside,outside) source static AllSydInside AllSydInside destination static DM_INLINE_NETWORK_5 DM_INLINE_NETWORK_5 no-proxy-arp route-lookup description Exemption rule for inside traffic to the BNE and HBA L2L tunnels
nat (DMZ,outside) source static SydDMZ SydDMZ destination static DM_INLINE_NETWORK_6 DM_INLINE_NETWORK_6 no-proxy-arp route-lookup description Exemption rule for DMZ traffic to the BNE and HBA L2L tunnels
nat (UserWiFi,outside) source static UserWiFiV4 UserWiFiV4 destination static DM_INLINE_NETWORK_7 DM_INLINE_NETWORK_7 no-proxy-arp route-lookup description Exemption rule for UserWiFi Traffic to the BNE and HBA L2L tunnels
nat (outside,outside) source static VPNSubnetSYD VPNSubnetSYD destination static DM_INLINE_NETWORK_4 DM_INLINE_NETWORK_4 no-proxy-arp route-lookup description Exemption hairpin rule for SydVPN to L2L Tunnels to BNE and HBA
nat (inside,outside) source static DM_INLINE_NETWORK_3 DM_INLINE_NETWORK_3 destination static VPNSubnetSYD VPNSubnetSYD no-proxy-arp route-lookup description This is the translation rule for the inside networks over the VPN it must be before hairpin rules.
nat (outside,outside) source dynamic VPNSubnetSYD interface description This is a hairpin rule so the full tunnel routes traffic back out to the real world that we have not already intercepted
nat (inside,outside) source static any any destination static NETWORK_OBJ_192.168.192.0_24 NETWORK_OBJ_192.168.192.0_24 no-proxy-arp route-lookup
nat (UserWiFi,outside) source static any any destination static NETWORK_OBJ_192.168.192.0_24 NETWORK_OBJ_192.168.192.0_24 no-proxy-arp route-lookup
!
object network obj_any
nat (any,outside) dynamic interface
object network DMZNetV4_in
nat (DMZ,outside) static DMZNetV4_out
access-group outside_access_in in interface outside
access-group inside_access_in in interface inside
access-group UserWiFi_access_in in interface UserWiFi
access-group GuestWiFi_access_in in interface GuestWiFi
access-group DMZ_access_in in interface DMZ
access-group BNETest_access_in in interface BNETest
access-group global_access global
ipv6 dhcprelay server 2406:3400:b:4300::250 inside
ipv6 dhcprelay enable UserWiFi
ipv6 dhcprelay enable GuestWiFi
route outside 0.0.0.0 0.0.0.0 XXX.XXX.XXX.XXX (Next hop) 1
route BNETest 192.168.32.0 255.255.240.0 10.0.0.2 1
route inside 192.168.37.0 255.255.255.0 192.168.77.1 3
route inside 192.168.50.0 255.255.255.0 192.168.77.1 3
route inside 192.168.60.0 255.255.255.0 192.168.77.1 3
route inside 192.168.64.0 255.255.240.0 192.168.77.1 2
route inside 192.168.80.0 255.255.255.0 192.168.77.1 3
route inside 192.168.90.0 255.255.255.0 192.168.77.1 3
route inside 192.168.100.0 255.255.255.0 192.168.77.1 3
route inside 192.168.120.0 255.255.255.0 192.168.77.1 3
route inside 192.168.130.0 255.255.255.0 192.168.77.1 3
route inside 192.168.140.0 255.255.255.0 192.168.77.1 3
route inside 192.168.150.0 255.255.255.0 192.168.77.1 3
route inside 192.168.160.0 255.255.255.0 192.168.77.1 3
route BNETest 192.168.194.0 255.255.255.0 10.0.0.2 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
timeout igp stale-route 0:01:10
aaa-server RomulusAndRemus protocol ldap
aaa-server RomulusAndRemus (inside) host 192.168.70.17
server-port 636
ldap-base-dn ou=People,dc=mydomain,dc=com,dc=au
ldap-naming-attribute uid
ldap-login-password *****
ldap-login-dn cn=Directory Manager
ldap-over-ssl enable
server-type auto-detect
aaa-server RomulusAndRemus (inside) host 192.168.70.18
server-port 636
ldap-base-dn ou=People,dc=mydomain,dc=com,dc=au
ldap-naming-attribute uid
ldap-login-password *****
ldap-login-dn cn=Directory Manager
ldap-over-ssl enable
server-type auto-detect
aaa-server RomulusAndRemus (inside) host ldap0.mydomain.com
server-port 636
ldap-base-dn ou=People,dc=mydomain,dc=com,dc=au
ldap-naming-attribute uid
ldap-login-password *****
ldap-login-dn cn=Directory Manager
ldap-over-ssl enable
server-type auto-detect
aaa-server RomulusAndRemus (inside) host ldap1.mydomain.com
server-port 636
ldap-base-dn ou=People,dc=mydomain,dc=com,dc=au
ldap-naming-attribute uid
ldap-login-password *****
ldap-login-dn cn=Directory Manager
ldap-over-ssl enable
server-type auto-detect
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
aaa authentication http console LOCAL
http server enable
http 192.168.100.0 255.255.255.0 inside
http 192.168.64.0 255.255.240.0 inside
http 192.168.110.0 255.255.255.0 inside
http 192.168.192.0 255.255.255.0 inside
snmp-server host DMZ XXX.XXX.XXX.XXX poll community ***** version 2c
snmp-server host inside 192.168.100.253 poll community ***** version 2c
snmp-server host inside 192.168.70.249 poll community ***** version 2c
snmp-server location Sydney
snmp-server contact ***** ******
snmp-server community *****
sysopt connection tcpmss 1300
sysopt connection preserve-vpn-flows
service sw-reset-button
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS mode transport
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal 3DES
protocol esp encryption 3des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal DES
protocol esp encryption des
protocol esp integrity sha-1 md5
crypto ipsec security-association pmtu-aging infinite
crypto ipsec fragmentation after-encryption outside
crypto ipsec df-bit clear-df outside
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 1 match address outside_cryptomap_65535.1
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 1 set pfs
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 1 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set pfs group5
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
crypto dynamic-map geelong_dynamic 3 match address outside_cryptomap_2
crypto dynamic-map geelong_dynamic 3 set pfs
crypto dynamic-map geelong_dynamic 3 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 1 match address outside_cryptomap
crypto map outside_map 1 set peer XXX.XXX.XXX.XXX (Alt Remote)
crypto map outside_map 1 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 2 match address outside_cryptomap_1
crypto map outside_map 2 set peer XXX.XXX.XXX.XXX (Remote)
crypto map outside_map 2 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 2 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
crypto map outside_map 3 ipsec-isakmp dynamic geelong_dynamic
crypto map outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map outside_map interface outside
crypto ca trustpoint _SmartCallHome_ServerCA
no validation-usage
crl configure
crypto ca trustpoint ASDM_TrustPoint0
enrollment terminal
crl configure
crypto ca trustpoint ASDM_TrustPoint1
enrollment terminal
crl configure
crypto ca trustpoint XXXX
enrollment terminal
subject-name CN=gateway.mydomain.com
crl configure
crypto ca trustpoint ASDM_Launcher_Access_TrustPoint_0
enrollment self
fqdn none
subject-name CN=192.168.77.2,CN=gateway
crl configure
crypto ca trustpoint ASDM_Launcher_Access_TrustPoint_1
enrollment self
fqdn none
subject-name CN=192.168.77.2,CN=gateway
crl configure
crypto ca trustpoint ASDM_Launcher_Access_TrustPoint_2
enrollment self
fqdn none
subject-name CN=192.168.77.2,CN=gateway
crl configure
crypto ca trustpoint ASDM_Launcher_Access_TrustPoint_3
enrollment self
fqdn none
subject-name CN=192.168.77.2,CN=gateway
crl configure
crypto ca trustpoint ASDM_TrustPoint2
enrollment terminal
crl configure
crypto ca trustpoint ASDM_TrustPoint3
crl configure
crypto ca trustpoint ASDM_TrustPoint4
enrollment terminal
crl configure
crypto ca trustpoint ASDM_TrustPoint5
enrollment terminal
fqdn vpn.mydomain.com
subject-name XXXX
keypair VPN-2018
crl configure
crypto ca trustpoint ASDM_TrustPoint6
enrollment terminal
crl configure
crypto ca trustpoint ASDM_TrustPoint8
enrollment terminal
crl configure
crypto ca trustpoint ASDM_TrustPoint9
enrollment terminal
no validation-usage
crl configure
crypto ca trustpoint ASDM_TrustPoint10
enrollment terminal
fqdn vpn.mydomain.com
subject-name XXXX
keypair syd-asdm.key
no validation-usage
crl configure
crypto ca trustpool policy
crypto ca certificate chain _SmartCallHome_ServerCA
certificate ca 6ecc7aa5a7032009b8cebcf4e952d491
XXXX
quit
crypto ca certificate chain ASDM_TrustPoint0
certificate ca 01fda3eb6eca75c888438b724bcfbc91
XXXX
quit
crypto ca certificate chain ASDM_TrustPoint1
certificate ca 083be056904246b1a1756ac95991c74a
XXXX
quit
crypto ca certificate chain ASDM_TrustPoint5
certificate 079992f6d6a4b6d5f770f0cca02be1d6
XXXX
quit
crypto ca certificate chain ASDM_TrustPoint9
certificate ca 01fda3eb6eca75c888438b724bcfbc91
XXXX
quit
crypto ca certificate chain ASDM_TrustPoint10
certificate 0ed637ed96cd9eac13e0bf319a9d338b
XXXX
quit
certificate ca
XXXX
quit
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 10
encryption aes-192
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 30
encryption 3des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 40
encryption des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 enable outside client-services port 443
crypto ikev2 remote-access trustpoint ASDM_TrustPoint10
crypto ikev1 enable outside
crypto ikev1 policy 20
authentication rsa-sig
encryption aes-256
hash sha
group 2
lifetime 86400
crypto ikev1 policy 30
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 86400
crypto ikev1 policy 50
authentication rsa-sig
encryption aes-192
hash sha
group 2
lifetime 86400
crypto ikev1 policy 60
authentication pre-share
encryption aes-192
hash sha
group 2
lifetime 86400
crypto ikev1 policy 80
authentication rsa-sig
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 policy 90
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 policy 110
authentication rsa-sig
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 120
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 140
authentication rsa-sig
encryption des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 150
authentication pre-share
encryption des
hash sha
group 2
lifetime 86400
telnet timeout 5
ssh stricthostkeycheck
ssh 192.168.100.0 255.255.255.0 inside
ssh 192.168.64.0 255.255.240.0 inside
ssh 192.168.110.0 255.255.255.0 inside
ssh 192.168.192.0 255.255.255.0 inside
ssh timeout 60
ssh key-exchange group dh-group14-sha1
console timeout 0
management-access inside
dhcpd auto_config outside
!
dhcpd address 192.168.77.6-192.168.77.14 inside
!
dhcprelay server 192.168.70.17 inside
dhcprelay server 192.168.70.18 inside
dhcprelay enable UserWiFi
dhcprelay enable GuestWiFi
dhcprelay timeout 60
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
wccp web-cache redirect-list wccp-traffic group-list wccp-servers
wccp interface inside web-cache redirect in
ntp server 192.168.70.18 source inside
ntp server 192.168.70.17 source inside
ssl trust-point ASDM_TrustPoint10 outside
ssl trust-point ASDM_TrustPoint10 inside
ssl trust-point ASDM_TrustPoint10 UserWiFi
ssl trust-point ASDM_TrustPoint10 GuestWiFi
ssl trust-point ASDM_TrustPoint10 DMZ
ssl trust-point ASDM_TrustPoint10 BNETest
ssl trust-point ASDM_Launcher_Access_TrustPoint_3 inside vpnlb-ip
webvpn
enable outside
anyconnect profiles SplitTunnel_client_profile disk0:/SplitTunnel_client_profile.xml
anyconnect profiles Tunnel_client_profile disk0:/Tunnel_client_profile.xml
anyconnect enable
tunnel-group-list enable
cache
disable
error-recovery disable
group-policy GroupPolicy_SplitTunnel internal
group-policy GroupPolicy_SplitTunnel attributes
wins-server value 192.168.70.18 192.168.70.17
dns-server value 192.168.70.18 192.168.70.17
vpn-tunnel-protocol ikev2 ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value SydVPNTunnelNets
default-domain value mydomain.com
split-dns value mydomain.com
split-tunnel-all-dns disable
webvpn
anyconnect profiles value SplitTunnel_client_profile type user
group-policy GroupPolicy_Tunnel internal
group-policy GroupPolicy_Tunnel attributes
wins-server value 192.168.70.18 192.168.70.17
dns-server value 192.168.70.18 192.168.70.17
vpn-tunnel-protocol ikev2 ssl-client
default-domain value mydomain.com
webvpn
anyconnect profiles value Tunnel_client_profile type user
always-on-vpn profile-setting
group-policy GroupPolicy_XXX.XXX.XXX.XXX (Remote) internal
group-policy GroupPolicy_XXX.XXX.XXX.XXX (Remote) attributes
vpn-tunnel-protocol ikev1 ikev2
group-policy GroupPolicy_dynamic internal
group-policy GroupPolicy_dynamic attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy_XXX.XXX.XXX.XXX (Alt Remote) internal
group-policy GroupPolicy_XXX.XXX.XXX.XXX (Alt Remote) attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy1 internal
group-policy GroupPolicy1 attributes
vpn-tunnel-protocol ikev1
group-policy IPSecFullTunnel internal
group-policy IPSecFullTunnel attributes
wins-server value 192.168.70.18 192.168.70.17
dns-server value 192.168.70.18 192.168.70.17
vpn-tunnel-protocol l2tp-ipsec
default-domain value mydomain.com
group-policy IPSecSplitTunnel internal
group-policy IPSecSplitTunnel attributes
wins-server value 192.168.70.18 192.168.70.17
dns-server value 192.168.70.18 192.168.70.17
vpn-tunnel-protocol l2tp-ipsec
split-tunnel-policy tunnelspecified
split-tunnel-network-list value SydVPNTunnelNets
default-domain value mydomain.com
dynamic-access-policy-record deny_users
user-message "Denied"
action terminate
dynamic-access-policy-record DfltAccessPolicy
username local_root password XXXX encrypted privilege 15
username local_root attributes
ssh authentication publickey fb:e4:59:7c:30:6c:8d:55:a7:f7:58:65:46:24:b1:04:44:ef:c9:de:20:59:88:f6:b4:8e:f1:a1:ad:d2:f3:83 hashed
tunnel-group SplitTunnel type remote-access
tunnel-group SplitTunnel general-attributes
address-pool VPNv4
ipv6-address-pool VPNv6
authentication-server-group RomulusAndRemus
default-group-policy GroupPolicy_SplitTunnel
tunnel-group SplitTunnel webvpn-attributes
group-alias SplitTunnel enable
tunnel-group SplitTunnel ipsec-attributes
ikev1 pre-shared-key *****
ikev1 trust-point XXXX
tunnel-group Tunnel type remote-access
tunnel-group Tunnel general-attributes
address-pool VPNv4
ipv6-address-pool VPNv6
authentication-server-group RomulusAndRemus
default-group-policy GroupPolicy_Tunnel
tunnel-group Tunnel webvpn-attributes
group-alias Tunnel enable
tunnel-group Tunnel ipsec-attributes
ikev1 pre-shared-key *****
ikev1 trust-point XXXX
tunnel-group XXX.XXX.XXX.XXX (Alt Remote) type ipsec-l2l
tunnel-group XXX.XXX.XXX.XXX (Alt Remote) general-attributes
default-group-policy GroupPolicy_XXX.XXX.XXX.XXX (Alt Remote)
tunnel-group XXX.XXX.XXX.XXX (Alt Remote) ipsec-attributes
ikev1 pre-shared-key *****
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
tunnel-group IPSecFullTunnel type remote-access
tunnel-group IPSecFullTunnel general-attributes
address-pool VPNv4
authentication-server-group RomulusAndRemus
default-group-policy IPSecFullTunnel
tunnel-group IPSecFullTunnel ipsec-attributes
ikev1 pre-shared-key *****
ikev1 trust-point ASDM_TrustPoint10
tunnel-group IPSecSplitTunnel type remote-access
tunnel-group IPSecSplitTunnel general-attributes
address-pool VPNv4
authentication-server-group RomulusAndRemus
default-group-policy IPSecSplitTunnel
tunnel-group IPSecSplitTunnel ipsec-attributes
ikev1 pre-shared-key *****
tunnel-group XXX.XXX.XXX.XXX (Remote) type ipsec-l2l
tunnel-group XXX.XXX.XXX.XXX (Remote) general-attributes
default-group-policy GroupPolicy_XXX.XXX.XXX.XXX (Remote)
tunnel-group XXX.XXX.XXX.XXX (Remote) ipsec-attributes
ikev1 pre-shared-key *****
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
tunnel-group geelong_dynamic type ipsec-l2l
tunnel-group geelong_dynamic general-attributes
default-group-policy GroupPolicy_dynamic
tunnel-group geelong_dynamic ipsec-attributes
ikev1 pre-shared-key *****
!
class-map SFR
match access-list SFR
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
no tcp-inspection
policy-map global_policy
class inspection_default
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect dns preset_dns_map
inspect ip-options
class SFR
sfr fail-open
class class-default
user-statistics accounting
!
hpm topN enable
Cryptochecksum:2168345798d1453e75380609510699f7
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2019 01:46 AM
Hello,
at first glance, it looks like ikev2 is enabled on the outside for (AnyConnect or whatever clients you use) client access only ?
Try and configure just:
crypto ikev2 enable outside
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2019 02:23 AM
Hi Georg,
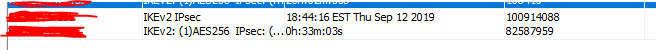
Thanks for having a look. I will run that command on both ASAs. However I believe it is already enabled. Please see the attached image which indicates that the tunnel is connected via IKE2.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2019 12:51 AM
: Hardware: ASA5506, 4096 MB RAM, CPU Atom C2000 series 1250 MHz, 1 CPU (4 cores)
ASA Version 9.6(1)
hostname gateway
domain-name mydomain.com
names
ip local pool BNEVPNIPv4Pool 192.168.194.1-192.168.194.254 mask 255.255.255.0
interface GigabitEthernet1/1
nameif outside
security-level 0
ip address XXX.XXX.XXX.XXX (Local) 255.255.255.252
!
interface GigabitEthernet1/2
nameif inside
security-level 100
ip address 192.168.36.1 255.255.255.0
!
interface GigabitEthernet1/3
nameif Management
security-level 100
ip address 192.168.32.1 255.255.255.0
!
interface GigabitEthernet1/4
nameif UserWireless
security-level 100
ip address 192.168.35.1 255.255.255.0
!
interface GigabitEthernet1/5
nameif GuestWireless
security-level 50
ip address 192.168.33.1 255.255.255.0
!
interface GigabitEthernet1/6
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/7
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/8
shutdown
no nameif
no security-level
no ip address
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
ftp mode passive
clock timezone EST 10
dns domain-lookup outside
dns domain-lookup inside
dns server-group DefaultDNS
name-server 192.168.70.18 outside
name-server 192.168.70.17 outside
domain-name mydomain.com
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
mtu outside 1500
mtu inside 1500
mtu Management 1500
mtu UserWireless 1500
mtu GuestWireless 1500
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-761.bin
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
nat (inside,outside) source static AllBehindInside AllBehindInside destination static DM_INLINE_NETWORK_2 DM_INLINE_NETWORK_2 no-proxy-arp route-lookup description Exemption rule for the inside interface to the SYD L2L
nat (Management,outside) source static MGMTNetv4 MGMTNetv4 destination static DM_INLINE_NETWORK_4 DM_INLINE_NETWORK_4 no-proxy-arp route-lookup description Exemption rule for the MGMT interface to the SYD L2L
nat (UserWireless,outside) source static UserWiFiv4 UserWiFiv4 destination static DM_INLINE_NETWORK_5 DM_INLINE_NETWORK_5 no-proxy-arp route-lookup description Exemption rule for the UserWiFi interface to the SYD L2L
nat (inside,outside) source static BNENetsV4 BNENetsV4 destination static BNEVPNv4 BNEVPNv4 no-proxy-arp route-lookup description Translation rule for inside nets to VPN subnet
nat (outside,outside) source static BNEVPNv4 BNEVPNv4 destination static DM_INLINE_NETWORK_3 DM_INLINE_NETWORK_3 no-proxy-arp route-lookup description Hairpin rule for traffic coming in from Anyconnect VPN to the L2L tunnels
nat (outside,outside) source dynamic BNEVPNv4 interface description Hairpin rule for the full Anyconnect VPN Tunnel to the internet
!
object network allInternalObjects
nat (any,outside) dynamic interface
access-group outside_access_in in interface outside
access-group inside_access_in in interface inside
access-group Management_access_in in interface Management
access-group UserWireless_access_in in interface UserWireless
access-group GuestWireless_access_in in interface GuestWireless
access-group global_access global
route outside 0.0.0.0 0.0.0.0 XXX.XXX.XXX.XXX (Next hop) 1
route Management 192.168.32.0 255.255.240.0 192.168.36.2 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
aaa-server mydom_ldap protocol ldap
aaa-server mydom_ldap (inside) host 192.168.70.18
server-port 636
ldap-base-dn ou=People,dc=mydomain,dc=com,dc=au
ldap-naming-attribute uid
ldap-login-password *****
ldap-login-dn cn=Directory Manager
ldap-over-ssl enable
server-type auto-detect
aaa-server mydom_ldap (inside) host 192.168.70.17
server-port 636
ldap-base-dn ou=People,dc=mydomain,dc=com,dc=au
ldap-naming-attribute uid
ldap-login-password *****
ldap-login-dn cn=Directory Manager
ldap-over-ssl enable
server-type auto-detect
user-identity default-domain LOCAL
aaa authentication http console LOCAL
aaa authentication ssh console LOCAL
http server enable
http 192.168.0.0 255.255.0.0 Management
http 192.168.0.0 255.255.0.0 inside
no snmp-server location
no snmp-server contact
sysopt connection tcpmss 1300
sysopt connection preserve-vpn-flows
service sw-reset-button
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS mode transport
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal 3DES
protocol esp encryption 3des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal DES
protocol esp encryption des
protocol esp integrity sha-1 md5
crypto ipsec security-association pmtu-aging infinite
crypto ipsec fragmentation after-encryption outside
crypto ipsec df-bit clear-df outside
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
crypto map outside_map 1 match address outside_cryptomap_1
crypto map outside_map 1 set peer XXX.XXX.XXX.XXX (Remote Alt)
crypto map outside_map 1 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 1 set ikev2 ipsec-proposal DES 3DES AES AES192 AES256
crypto map outside_map 3 match address outside_cryptomap
crypto map outside_map 3 set peer XXX.XXX.XXX.XXX (Remote)
crypto map outside_map 3 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 3 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
crypto map outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map outside_map interface outside
crypto ca trustpoint _SmartCallHome_ServerCA
no validation-usage
crl configure
crypto ca trustpoint mydom_wildcard
enrollment terminal
subject-name CN=gateway.mydomain.com,OU=IT,O=mydomain,C=AU,St=New South Wales,L=Sydney,EA=network@mydomain.com
keypair mydom_ssl
crl configure
crypto ca trustpoint ASDM_TrustPoint0
enrollment terminal
crl configure
crypto ca trustpoint ASDM_Launcher_Access_TrustPoint_0
enrollment self
fqdn none
subject-name CN=10.0.0.2,CN=gateway
keypair ASDM_LAUNCHER
crl configure
crypto ca trustpoint ASDM_TrustPoint1
enrollment terminal
subject-name CN=gateway
keypair <Default-ECDSA-Key>
crl configure
crypto ca trustpoint ASDM_TrustPoint2
enrollment terminal
fqdn bne-vpn.mydomain.com
subject-name CN=bne-vpn,O=mydom ain,C=AU,St=New South Wales,L=Sydney,EA=network@mydomain.com
keypair VPN_2018
no validation-usage
crl configure
crypto ca trustpool policy
crypto ca certificate chain _SmartCallHome_ServerCA
certificate ca XXX
quit
crypto ca certificate chain mydom_wildcard
certificate XXXX
quit
crypto ca certificate chain ASDM_TrustPoint0
certificate ca XXXX
quit
crypto ca certificate chain ASDM_Launcher_Access_TrustPoint_0
certificate XXXX
quit
crypto ca certificate chain ASDM_TrustPoint2
certificate XXXX
quit
certificate ca XXXX
quit
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 10
encryption aes-192
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 30
encryption 3des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 40
encryption des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 enable outside client-services port 443
crypto ikev2 fragmentation mtu 1380
crypto ikev2 remote-access trustpoint mydom_wildcard
crypto ikev1 enable outside
crypto ikev1 policy 20
authentication rsa-sig
encryption aes-256
hash sha
group 2
lifetime 86400
crypto ikev1 policy 30
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 86400
crypto ikev1 policy 50
authentication rsa-sig
encryption aes-192
hash sha
group 2
lifetime 86400
crypto ikev1 policy 60
authentication pre-share
encryption aes-192
hash sha
group 2
lifetime 86400
crypto ikev1 policy 80
authentication rsa-sig
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 policy 90
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 policy 110
authentication rsa-sig
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 120
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 140
authentication rsa-sig
encryption des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 150
authentication pre-share
encryption des
hash sha
group 2
lifetime 86400
telnet timeout 5
ssh stricthostkeycheck
ssh 192.168.0.0 255.255.0.0 inside
ssh timeout 5
ssh version 2
ssh key-exchange group dh-group14-sha1
console timeout 0
management-access inside
dhcpd auto_config outside
!
dhcprelay server 192.168.70.17 outside
dhcprelay server 192.168.70.18 outside
dhcprelay enable inside
dhcprelay enable Management
dhcprelay enable UserWireless
dhcprelay enable GuestWireless
dhcprelay timeout 60
ntp server 203.114.73.24 source outside
ntp server 103.76.40.155 source outside
ntp server 192.168.70.18 source outside
ntp server 192.168.70.17 source outside
ntp server 129.250.35.251 source outside
ssl trust-point ASDM_TrustPoint2 outside
ssl trust-point ASDM_TrustPoint2 inside
ssl trust-point ASDM_TrustPoint2 Management
ssl trust-point ASDM_TrustPoint2 UserWireless
ssl trust-point ASDM_TrustPoint2 GuestWireless
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 outside vpnlb-ip
webvpn
enable outside
anyconnect profiles FullTunnel_client_profile disk0:/FullTunnel_client_profile.xml
anyconnect profiles SplitTunnel_client_profile disk0:/SplitTunnel_client_profile.xml
anyconnect enable
tunnel-group-list enable
cache
disable
error-recovery disable
group-policy GroupPolicy_SplitTunnel internal
group-policy GroupPolicy_SplitTunnel attributes
wins-server value 192.168.70.17 192.168.70.18
dns-server value 192.168.70.17 192.168.70.18
vpn-tunnel-protocol ikev2 ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value AllSubnetsForVPN
default-domain value mydomain.com
split-dns value mydomain.com
split-tunnel-all-dns disable
webvpn
anyconnect profiles value SplitTunnel_client_profile type user
group-policy GroupPolicy_FullTunnel internal
group-policy GroupPolicy_FullTunnel attributes
wins-server value 192.168.70.18 192.168.70.17
dns-server value 192.168.70.18 192.168.70.17
vpn-tunnel-protocol ikev2 ssl-client
default-domain value mydomain.com
webvpn
anyconnect profiles value FullTunnel_client_profile type user
group-policy GroupPolicy_XXX.XXX.XXX.XXX (Remote) internal
group-policy GroupPolicy_XXX.XXX.XXX.XXX (Remote) attributes
vpn-tunnel-protocol ikev1 ikev2
group-policy GroupPolicy_XXX.XXX.XXX.XXX (Remote Alt) internal
group-policy GroupPolicy_XXX.XXX.XXX.XXX (Remote Alt) attributes
vpn-tunnel-protocol ikev1 ikev2
dynamic-access-policy-record deny_users
action terminate
dynamic-access-policy-record DfltAccessPolicy
username local_root password XXXX encrypted privilege 15
username local_root attributes
ssh authentication publickey fb:e4:59:7c:30:6c:8d:55:a7:f7:58:65:46:24:b1:04:44:ef:c9:de:20:59:88:f6:b4:8e:f1:a1:ad:d2:f3:83 hashed
username local_pbrady password XXXX encrypted privilege 15
tunnel-group SplitTunnel type remote-access
tunnel-group SplitTunnel general-attributes
address-pool BNEVPNIPv4Pool
authentication-server-group mydom_ldap
default-group-policy GroupPolicy_SplitTunnel
tunnel-group SplitTunnel webvpn-attributes
group-alias SplitTunnel enable
tunnel-group FullTunnel type remote-access
tunnel-group FullTunnel general-attributes
address-pool BNEVPNIPv4Pool
authentication-server-group mydom_ldap
default-group-policy GroupPolicy_FullTunnel
tunnel-group FullTunnel webvpn-attributes
group-alias FullTunnel enable
tunnel-group XXX.XXX.XXX.XXX (Remote) type ipsec-l2l
tunnel-group XXX.XXX.XXX.XXX (Remote) general-attributes
default-group-policy GroupPolicy_XXX.XXX.XXX.XXX (Remote)
tunnel-group XXX.XXX.XXX.XXX (Remote) ipsec-attributes
ikev1 pre-shared-key *****
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
tunnel-group XXX.XXX.XXX.XXX (Remote Alt) type ipsec-l2l
tunnel-group XXX.XXX.XXX.XXX (Remote Alt) general-attributes
default-group-policy GroupPolicy_XXX.XXX.XXX.XXX (Remote Alt)
tunnel-group XXX.XXX.XXX.XXX (Remote Alt) ipsec-attributes
ikev1 pre-shared-key *****
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
Cryptochecksum:7e7472d205b76c8ba06fc0f8e20b272d
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2019 11:37 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2019 06:05 PM
Hi Joseph thanks for your reply.
I'd never heard of this issue before, but based on some quick research I got the following numbers:
- RTT (based on pinging the remote file server, plus a little extra as my understanding is that Windows ping won't account for the full network congestion etc.)
- 20ms
- Bandwidth (based on on running LAN Speed Test against the remote file server, 200 packets randomly varying between 2-8Mb)
- 28/13Mbps Up/Down
- BDP using this calculator: https://www.speedguide.net/bdp.php
- 0.03-0.06 Mbps = 30,000 - 60,000 bits
My understanding is that anything over 12,500, so it would appear that this is the case. I will investigate further these CTCP features and try activating them.
Thanks!
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: