- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: What is the best practice to access devices through management ports?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2019 09:40 PM
Hi everyone!
I have devices enabled with management ports to access. Those are placed in DMZ zone specially like DMZ SW, VM servers, SAN SW etc.
Now I have queries need to be answered:
1. What will be the best practice to connect to manage them through management ports? Using a common management SW?
2. Is it wise to keep them accessible from LAN side configuring the management port using the same IP subset that i got in my LAN side as management traffics are not allowed to travel to a default router? If no, than how to access them remotely through management IP from different network?
Thanks in advance :)
Solved! Go to Solution.
- Labels:
-
Catalyst Switch
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2019 11:04 PM
Hi,
Another method may that you will connect Magamenet Switch to the Core switch and restrict Management VLAN access using the VACL or use a sperate VRF and route leak as required so your IT team can access the Management switch without having dual NIC or switching himself from to Management network.
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2019 12:36 AM
Hello,
in general, it is recommended to separate management and production/user traffic, and to use a separate Vlan for management. If your management traffic cannot be routed outside of your network, there is obviously no way to access your devices remotely, at least not using the management IP addresses.
It might be useful to post a brief schematic drawing showing your topology, as well as what devices you actually have, in order to give you a more specific answer...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2019 02:34 AM - edited 06-22-2019 02:38 AM
Hello Georg,
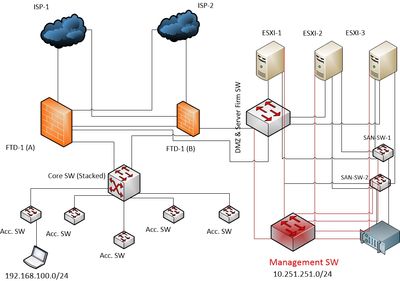
Thanks for the replay. The diagram has been attached. Where I have a management SW that connects all management ports form devices from DMZ zone (Colored RED). What will be best way to access network 10.251.251.0/24 to that management network from a particular user VLAN having network of 192.168.100.0/24 in a effective way where security is not compromised.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2019 04:13 AM - edited 06-22-2019 04:14 AM
Hello
If the dmz subnet resides on the FW then the best way is to advertise that dmz subnet via a static route into you production network then restrict access to on the FW for mgt services (snmp/ntp/ssh,tacacs etc.) to/from that dmz subnet
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2019 05:11 AM - edited 06-22-2019 05:12 AM
Dear Paul Driver
To do so, default route is needed from management ports and I afraid there is no gateway setting on the management port for it. Than how can I route the traffic to my production network?
Please correct me if i'm wrong.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2019 06:00 AM
You keep mentioning your management network cannot or is not allowed to reach a default router. If this is company policy rather than technical constraint of sorts you could have a dedicated jump host with two NiCs, one LAN side and one in the management network. Select users could then use the jump host as the point of entry to the management network and no GW would be required as the 2nd NIC will be on same L2 subnet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2019 08:22 PM
That seems helpful. Apart from this will it be harmful to keep the management ports in a common VLAN where the IT administrators resides without setting up a default gateway in the management interfaces so that the traffic can't travel outside of that broadcast domain?
BR,
GM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2019 11:04 PM
Hi,
Another method may that you will connect Magamenet Switch to the Core switch and restrict Management VLAN access using the VACL or use a sperate VRF and route leak as required so your IT team can access the Management switch without having dual NIC or switching himself from to Management network.
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2019 08:43 PM
It sounds great. Thanks for your suggestion.
BR
Mostofa
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2019 12:49 AM
These these things are usually setup based on the company security policy of some sort, or more common, you have come in and inherited it the way it is and want to make some changes.
How many devices are you planning putting on this L2 network? That alone may dictate whether you should look at using multiple networks rather than one L2. Everyone here has suggested various different ways to achieve connectivity with secured isolation so it really just depends on what you want to achieve. I have seen all the methods suggested here in place across different companies. Utilizing your existing hardware/setup without the need to buy/configure anything else, Deepaks solution should be easy enough to put in place with no interruptions or reconfiguration of end management devices.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2019 08:44 PM
I will follow Deepak's one. Thanks a lot for the discussions.
BR
Mostofa
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: