- Cisco Community
- Technology and Support
- Networking
- SD-WAN and Cloud Networking
- Unable to ping inside networks between site to site VPN of ASA 5506W to MX84
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2020 12:39 AM - edited 03-05-2020 12:40 AM
Hi,
I'd like to ask for some help regarding the network that I have right now.
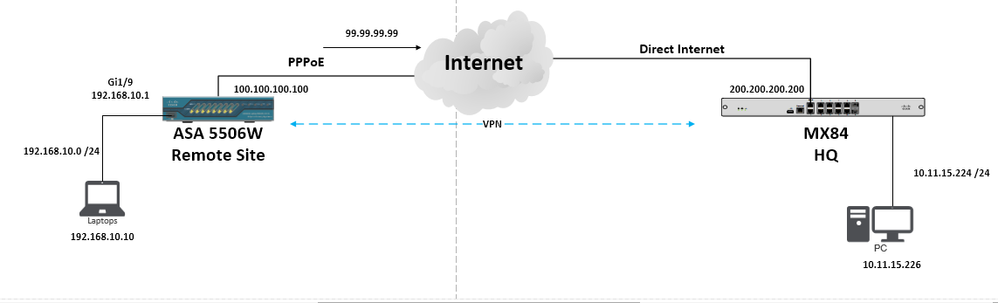
We have a remote site that has a ASA 5506W that has a PPPoE as its Internet connection. Its currently peered at our main site towards MX84. Setup looks like below
Even though I see the VPN connection up and running between the 2 sites, I can't seem to reach any of the end devices from HQ to Remote and vice versa. I think it has probably to do with routing or firewall rules although I'm not really sure since I allowed the icmp in the management of ASDM for the wifi interface (HQ to Remote Site ping). In the reverse side of that, I also cannot ping from the Gi1/9 interface towards the HQ Subnet as well (Remote Site to HQ ping)
Log results Ping from HQ to Remote site
From ASA (no logs from Meraki since its log are crap)
10.11.15.226 44679 Failed to locate egress interface for ICMP from outside:10.11.15.226/44679 to 192.168.10.1/0
Log results from Remote Site to HQ
From ASA again
ASA# ping
TCP Ping [n]:
Interface: outside
Target IP address: 10.11.15.226
Repeat count: [5]
Datagram size: [100]
Timeout in seconds: [2]
Extended commands [n]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.11.15.226, timeout is 2 seconds:
?????
Success rate is 0 percent (0/5)
ASA#
100.100.100.100 32781 10.11.15.226 0 Built outbound ICMP connection for faddr 10.11.15.226/0 gaddr 100.100.100.100/32781 laddr 100.100.100.100/32781(any)
I'm not sure if this is a routing issue but I did add a static route for peer ip of HQ to outside by the provided next hop ip from the PPPoE interface.
S* 0.0.0.0 0.0.0.0 [1/0] via 99.99.99.99, outside
S 200.200.200.200 255.255.255.255 [1/0] via 99.99.99.99, outside
Here's the ASA config
interface GigabitEthernet1/1
nameif outside
security-level 0
pppoe client vpdn group ISP
ip address pppoe setroute
interface GigabitEthernet1/9
nameif wifi
security-level 100
ip address 192.168.10.1 255.255.255.0
!
dns domain-lookup outside
dns server-group DEFAULTDNS
name-server 8.8.8.8
name-server 8.8.4.4
dns server-group DefaultDNS
domain-name STARK
same-security-traffic permit inter-interface
object network obj_any
subnet 0.0.0.0 0.0.0.0
object network Net_10.11.15.224_27
subnet 10.11.15.224 255.255.255.224
object network Net_192.168.10.0_24
subnet 192.168.10.0 255.255.255.0
object-group network Group_Remote_Subnets
network-object 192.168.10.0 255.255.255.0
access-list 100 extended permit icmp any any
access-list outside_cryptomap extended permit ip object-group Group_Remote_Subnets 10.11.15.224 255.255.255.224
icmp permit any wifi
nat (inside,outside) source static Group_Remote_Subnets Group_Remote_Subnets destination static Net_10.11.15.224_27 Net_10.11.15.224_27 no-proxy-arp route-lookup
!
object network obj_any
nat (any,outside) dynamic interface
!
nat (inside,outside) after-auto source dynamic any interface
route outside 200.200.200.200 255.255.255.255 10.228.205.30 1
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map outside_map 1 match address outside_cryptomap
crypto map outside_map 1 set peer 200.200.200.200
crypto map outside_map 1 set ikev1 transform-set REMOTE_HQ ESP-3DES-SHA
crypto map outside_map 1 set security-association lifetime kilobytes unlimited
crypto map outside_map interface outside
crypto ca trustpool policy
crypto ikev1 enable outside
crypto ikev1 enable inside
crypto ikev1 policy 10
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 28800
group-policy DfltGrpPolicy attributes
vpn-tunnel-protocol ikev1 ssl-client ssl-clientless
group-policy GroupPolicy_200.200.200.200 internal
group-policy GroupPolicy_200.200.200.200 attributes
vpn-tunnel-protocol ikev1
dynamic-access-policy-record DfltAccessPolicy
tunnel-group 200.200.200.200 type ipsec-l2l
tunnel-group 200.200.200.200 general-attributes
default-group-policy GroupPolicy_200.200.200.200
tunnel-group 200.200.200.200 ipsec-attributes
ikev1 pre-shared-key *****
!
Basically, I want the 192.168.10.0 /24 network to be able to ping 10.11.15.224 /27 and vice versa.
Thanks
Solved! Go to Solution.
- Labels:
-
Other SD-WAN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2020 08:49 PM
added in the global command of
crypto map outside_map 1 set reverse-route
and
management-access wifi and finable to ping
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2020 10:48 PM
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2020 08:49 PM
added in the global command of
crypto map outside_map 1 set reverse-route
and
management-access wifi and finable to ping
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide